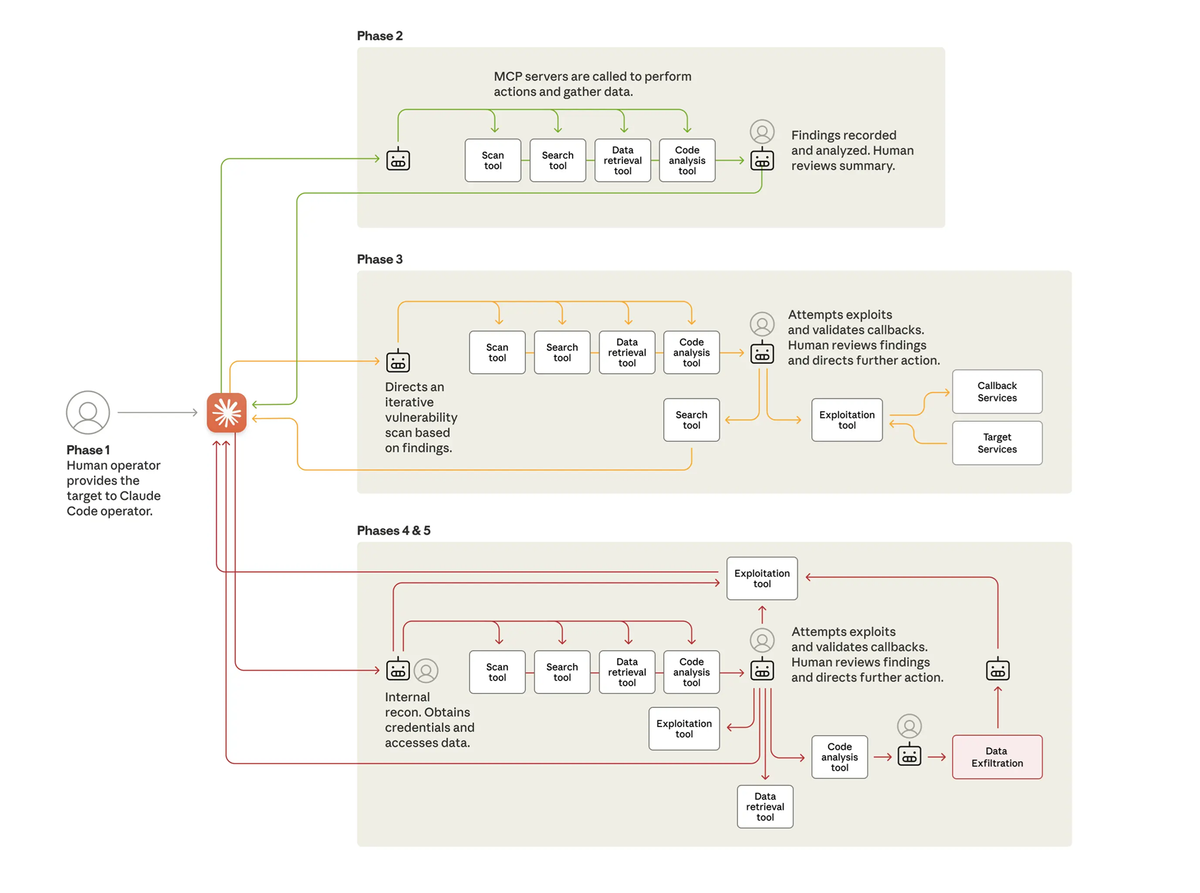
Chinese state hackers used Anthropic to automate cyber intrusions
UK MoD knew of Excel's security risks before Afghan data leak, NHS investigates Clop's attack claims, ASUS patches DSL router critical flaws, DoorDash reveals October security incident, US feds warn of Akira's expanded encryption capabilities, Kraken is testing how fast it can encrypt, much more