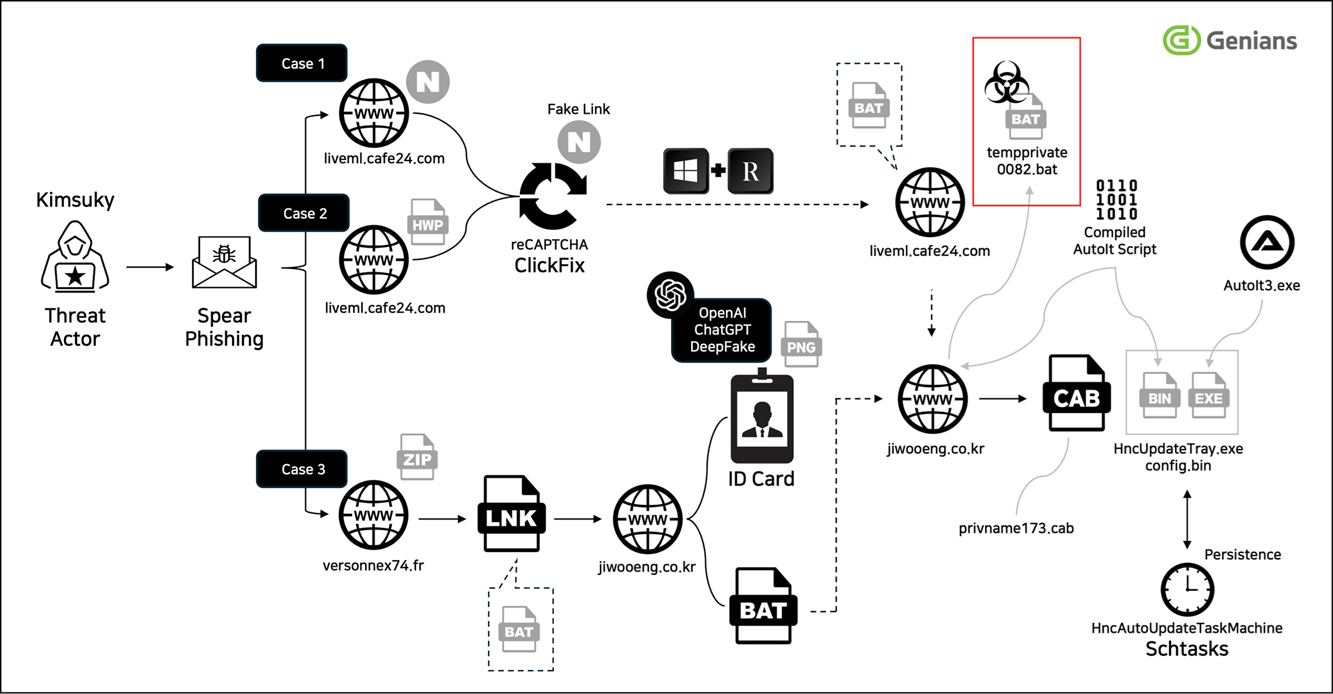
DPRK's Kimsuky forged a deepfake military ID using ChatGPT for S. Korean attack
Vastaamo hacker who released psychotherapy center records is set free, FBI issues warning of UNC6040 and UNC6395 targeting Salesforce users, Shiba Inu stopped damage from attack, DC AG charges Athena ATM operator for ignoring elderly scams, much more