France accuses Russia's APT28 of a string of serious cyberattacks going back to 2021
Kristi Noem urges "back-to-basics" for CISA, WhatsApp to roll out private processing for new AI features, Indian court blocks Proton Mail, Nova Scotia Power copes with a cyber breach, Israeli hacker-for-hire PI loses extradition fight, Scammers use snail mail for Ledger wallet theft, much more


Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
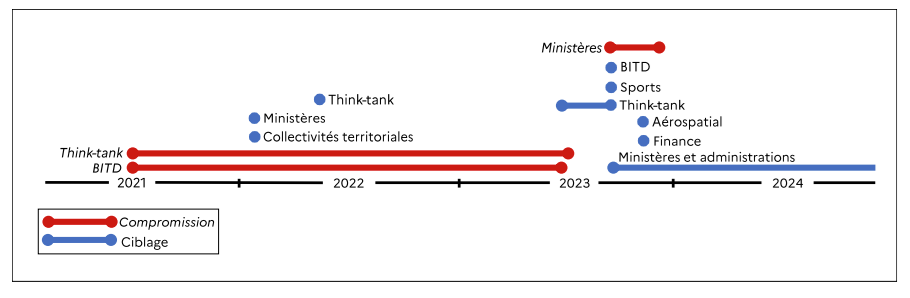
France's foreign ministry explicitly accused Russia's GRU military intelligence agency of mounting cyber attacks on a dozen entities, including ministries, defense firms, and think tanks, since 2021, in an attempt to destabilise France.
The accusations, levelled at GRU unit APT28, which officials said was based in Rostov-on-Don in southern Russia, are not the first by a Western power, but it is the first time Paris has blamed the Russian state based on its own intelligence.
The ministry said in a statement that APT28's attacks on France go as far back as 2015, when the TV5 Monde station was taken off air in a hack claimed by purported Islamic State militants.
France said APT28 had been behind the attack, and another in the 2017 presidential election when emails linked to the party and campaign of the eventual winner, Emmanuel Macron, were leaked and mixed with disinformation.
According to a report by France's National Cybersecurity Agency (ANSSI), APT28 has sought to obtain strategic intelligence from entities across Europe and North America. Officials said the government had decided to go public to keep the public informed at a time of uncertainty in domestic politics and over Russia's war in Ukraine.
ANSSI said there had been a jump last year in the number of attacks on French ministries, local administrations, defence companies, aerospace firms, think tanks, and entities in the financial and economic sector. They said APT28's most recent attack was in December, and that some 4,000 cyber attacks had been ascribed to Russian actors in 2024, an increase of 15% on 2023. (John Irish / Reuters)
Related: Diplomatie.gouv.fr, ANSSI, ANSSI, The Guardian, Ukrinform, Bleeping Computer, Politico EU, BleepingComputer, The Record, The Kyiv Independent, Daily Sabah, r/worldnews, ABC News, Infosecurity Magazine, Wall Street Journal, France24
Speaking at this year's RSA conference, Homeland Security Secretary Kristi Noem outlined her plans to refocus the Cybersecurity and Infrastructure Security Agency (CISA) on protecting critical infrastructure from increasingly sophisticated threats, particularly from China, while distancing the agency from what she characterized as mission drift under previous leadership.
Noem provided the most detailed vision yet of how the current administration is pushing CISA to a “back-to-basics” approach aimed at hardening defenses against adversaries who have demonstrated capabilities to infiltrate critical systems.
“We’re going to make sure that we need to put CISA back to focusing on its core mission,” Noem said. “They were deciding what was truth and what was not. And it’s not the job of CISA to be the ‘Ministry of Truth.’ It’s to be a cybersecurity agency that works to protect this country.”
The “Ministry of Truth” comment is a reference to CISA’s misinformation and election security efforts, which have been inflamed in recent weeks after President Donald Trump signed an executive order stripping former CISA leader Chris Krebs of his security clearance and calling for a review of Krebs’ actions as a government employee.
Noem called that work “inappropriate” in an accompanying on-stage interview with José-Marie Griffiths, the president of Dakota State University. (Greg Otto / Cyberscoop)
Related: The Record, The Register, KTVU, The Register, NextGov/FCW
Communication app WhatsApp, used by roughly 3 billion people around the world, will roll out cloud-based AI capabilities in the coming weeks that are designed to preserve WhatsApp’s defining security and privacy guarantees while offering users access to message summarization and composition tools.
Meta has been incorporating generative AI features across its services that are built on its open source large language model, Llama. And WhatsApp already includes a light blue circle that gives users access to the Meta AI assistant. But many users have balked at this addition, given that interactions with the AI assistant aren’t shielded from Meta the way end-to-end encrypted WhatsApp chats are.
The new feature, dubbed Private Processing, is meant to address these concerns with what the company says is a carefully architected and purpose-built platform devoted to processing data for AI tasks without the information being accessible to Meta, WhatsApp, or any other party. (Lily Hay Newman / Wired)
Related: Engineering at Meta, WhatsApp, Social Media Today, WABetaInfo, Engadget, The Hacker News, iPhone in Canada Blog
Marks & Spencer has admitted that some products are running short in its stores as it continues to deal with the fallout from a ransomware attack.
The retailer said there were “pockets of limited availability” in some shops, as more than a week of disruption to its IT systems affects its stores.
The company has decided to “take some of our systems temporarily offline” as part of its “proactive management of the incident”. “We are working hard to get availability back to normal across the estate,” it said on Wednesday.
The Metropolitan police confirmed that its cybercrime unit was investigating the attack, which has been linked to hacking collective Scattered Spider. A spokesperson for the force said inquiries were continuing.
M&S was forced to stop taking orders on its website, which accounts for about £3.8m (around $5 million) in sales a day, after days of disruption in stores caused by a cyber-attack. M&S has also had to pause deliveries of some packaged food items to Ocado, the online grocery specialist it co-owns.
The disruption caused by the hack, and uncertainty over when it will end, has wiped more than £600m (around $800 million) off the stock market value of M&S in just over a week. (Sarah Butler / The Guardian)
Related: Hong Kong Free Press, Financial Times, Reuters, The Guardian, Sky News, The Independent, Computer Weekly, ITV News
The Karnataka High Court in India ordered the blocking of encrypted email provider Proton Mail across the country after a local firm alleged that its employees had received emails containing obscene and vulgar content sent via Proton Mail.
Justice M Nagaprasanna ordered the Indian government to “block Proton Mail, bearing in mind the observations made in the course of the order,” under the Information Technology Act 2008.
In its complaint filed in January, the New Delhi-based firm called for the regulation or blocking of Proton Mail in India, as the email service reportedly refused to share details about the sender of the allegedly offensive emails, despite a police complaint. (Jagmeet Singh / TechCrunch)
Related: Live Law, Bar and Bench, CyberInsider, The Indian Express, Moneycontrol, Inc42 Media, Cointelegraph, The Hacker News, The Hindu
Canada's Nova Scotia Power and its parent company, Emera, said someone gained unauthorized access to parts of their Canadian network and servers supporting their business applications, a breach that was discovered on April 25.
Nova Scotia Power said there is no impact on the utility's ability to serve customers in Nova Scotia, and there has been no disruption to any Canadian physical operations such as Nova Scotia Power's generation, transmission, and distribution facilities, the Maritime Link, or the Brunswick Pipeline.
However, Nova Scotia Power posted to its social media channels Sunday night that it was having a "technical issue" with its phone line and customers' ability to access their accounts.
In response to customers asking about the breach on Facebook, the company said it is "currently open to support our customers for emergencies and outages only."
The utility's website saithe security breach caused the issues the issues were caused by the security breach. Customers can still report emergencies or outages through Nova Scotia's outage line, though they may face a longer wait. (CBC News)
Related: Business Wire, Industrial Cyber, Rigzone, Cybernews, Daily Energy Insider, The Globe and Mail, The Chronicle Herald, The Hawk, Cyber Insider
Amit Forlit, an Israeli private investigator wanted by the US for allegedly carrying out a "hacking for hire" campaign at the behest of an ExxonMobil lobbyist, lost his fight against extradition from Britain.
He is facing charges of wire fraud, conspiracy to commit wire fraud, and computer hacking relating to his alleged targeting of environmental activists, his lawyers said in January, confirming Reuters' earlier reporting.
His objections to extradition were rejected by Judge John McGarva, who said in his written ruling that US prosecutors alleged that Forlit was a "hired gun".
"The highest he can put his case is that he is collateral damage in the climate change litigation," McGarva said. He added that Forlit's prosecution "may be dropped by the new administration" of President Donald Trump. (Sam Tobin / Reuters)
According to a letter received by tech commentator Jacob Canfield, scammers are mailing physical letters to the owners of Ledger crypto hardware wallets asking them to validate their private seed phrases in a bid to access the wallets to clean them out.
A seed phrase, or recovery phrase, is a string of up to 24 words that unlocks access to a crypto wallet. A scammer with the phrase can access and control the associated wallet to transfer its holdings elsewhere.
Canfied received a letter that appeared to be from Ledger claiming he needed to immediately perform a “critical security update” on his device.
The letter, which uses Ledger’s logo, business address, and a reference number to feign legitimacy, asks to scan a QR code and enter the wallet’s private recovery phrase under the guise of validating the device.
The letter threatens that “failure to complete this mandatory validation process may result in restricted access to your wallet and funds.”
Ledger said the letter is a scam and cautioned its device users to stay vigilant against phishing attempts. (Brayden Lindrea / Cointelegraph)
Related: crypto.news, The Block, The Daily Hodl
South Korea’s leading mobile carrier, SK Telecom, is facing mounting fallout from a recent hacking incident, with more than 70,000 users switching to rival providers in just two days after the company began offering free USIM card replacements.
Amid growing concerns that the data breach could spill over into the financial sector, South Korean financial authorities on Wednesday launched an emergency response team and tightened security protocols.
According to industry sources, 35,902 SK Telecom users switched to other major carriers on Tuesday, following 34,132 users who switched on Monday. During the same period, SKT gained only 11,991 new users. (Jo He-rim / The Korea Herald)
Related: Yonhap News, Korea JoongAng Daily, ChosunBiz
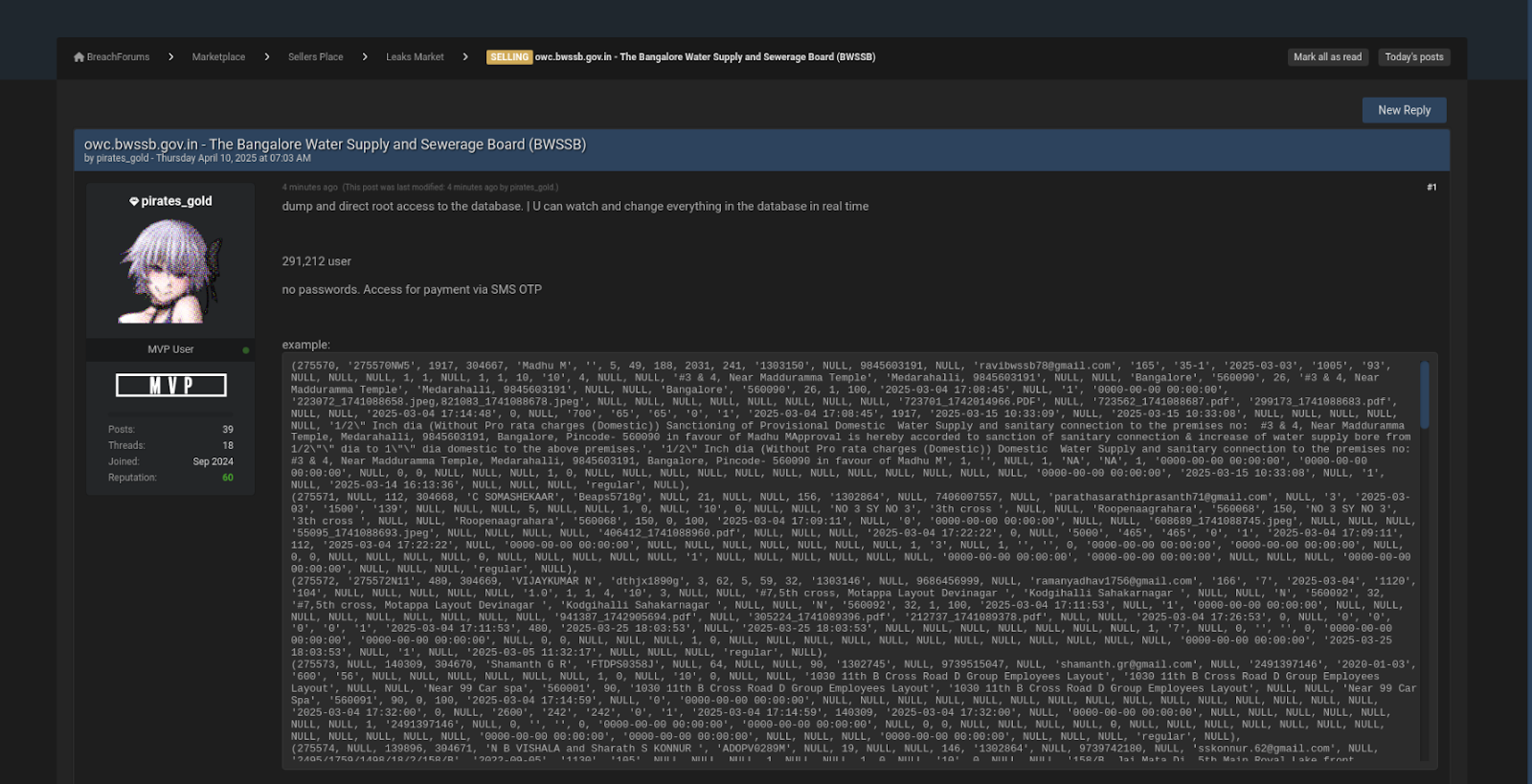
Researchers at CloudSEK revealed a critical breach in the infrastructure of the Bangalore Water Supply and Sewerage Board (BWSSB) that left sensitive personal data of over 290,000 Bangalore residents vulnerable, after direct root access to BWSSB’s database was found being sold by a cybercriminal for just $500 on underground forums.
On April 10, 2025, CloudSEK’s proprietary digital risk monitoring platform XVigil flagged a post by a threat actor identified as pirates_gold, offering unrestricted access to BWSSB’s database. What makes this incident particularly disturbing is how easily this access was obtained through exposed credentials and a publicly accessible admin login portal.
CloudSEK’s STRIKE Team traced the breach back to a publicly accessible .env file, containing plaintext MySQL credentials, alongside an internet-facing Adminer interface, commonly used for managing databases. These misconfigurations gave the attacker full administrative control, without any need for advanced hacking tools. (India CRN)
Related: CloudSEK, NDTV, Vartha Bharati, The420, OneIndia, Deccan Herald
The US Embassy in Guatemala said it found that China-based espionage groups had hacked the Central American nation's foreign ministry's computer system, but the Guatemalan government said this was an old case.
The embassy said in a post on X that the hacking was discovered during a safety revision conducted by the Guatemalan government and the US Southern Command, a military branch.
Guatemala's foreign ministry dismissed the US embassy's report of a hack into its systems as old. "They are referring to an old case from September 2022. There has been no recent hack," it said in a statement. (Sofia Menchu / Reuters)
According to a report by the Government Accountability Office (GAO), some state and local government agencies are unsure how they will continue to fund their cybersecurity initiatives in the absence of federal support.
The office examined the $1 billion, 4-year State and Local Cybersecurity Grant Program by randomly sampling state and territorial government agencies that have received funding.
It found that most agencies had positive things to say about the program, and some agency representatives selected for interviews by the federal office reported concerns with how they’ll continue their cybersecurity initiatives after the program’s one-time funding runs out, or if it’s prematurely ended. (Colin Wood / StateScoop)
Related: GAO

Acting DARPA Director Rob McHenry told an audience at the RSAC 2025 Conference that a combination of formal software development methods with large language models (LLMs) could “virtually eliminate software vulnerabilities” across foundational system infrastructures, a departure from the traditionally accepted risks of software flaws.
Formal methods, a way of using math to prove that software works as intended, have for decades been regarded as effective but laborious and expensive, suited only for the most critical systems and requiring expert staff. McHenry noted that combining LLMs with formal methods enables automatic generation and validation of correctness proofs, drastically lowering the labor and cost barriers.
His statements came in the context of the AI Cyber Challenge, a public-private collaboration involving industry leaders such as Google, Microsoft, Anthropic, and OpenAI. The initiative tests whether advanced AI systems can identify and patch vulnerabilities in open-source software components vital to the electric grid, health care, and transportation. (Greg Otto / Cyberscoop)
Related: NextGov/FCW
Microsoft previewed hotpatching for on-prem Windows Server 2025, which will become a paid subscription service in July.
Hotpatching allows software updates to be applied without requiring a reboot. It’s a common approach that’s available for the Linux kernel, VMware products, and the Xen hypervisor, among others. Admins like it because it allows security updates to be implemented without requiring reboots – and therefore without having to find a change window or a convenient moment for an outage.
Microsoft already offers hotpatching for Windows Server: Azure Edition and version 2022 running in its Azure cloud. The MS-DOS titan says its Xbox team is a big user.
Last August, Microsoft teased a preview of hotpatching for Windows Server 2025 implementations controlled by its Arc hybrid-and-multicloud management tool.
Microsoft said the preview will end on June 30 and be replaced by a subscription service that costs $1.50/core/month. Non-hotpatch updates will still be available as usual for free. (Simon Sharwood / The Register)
Related: Microsoft, Bleeping Computer, Forbes
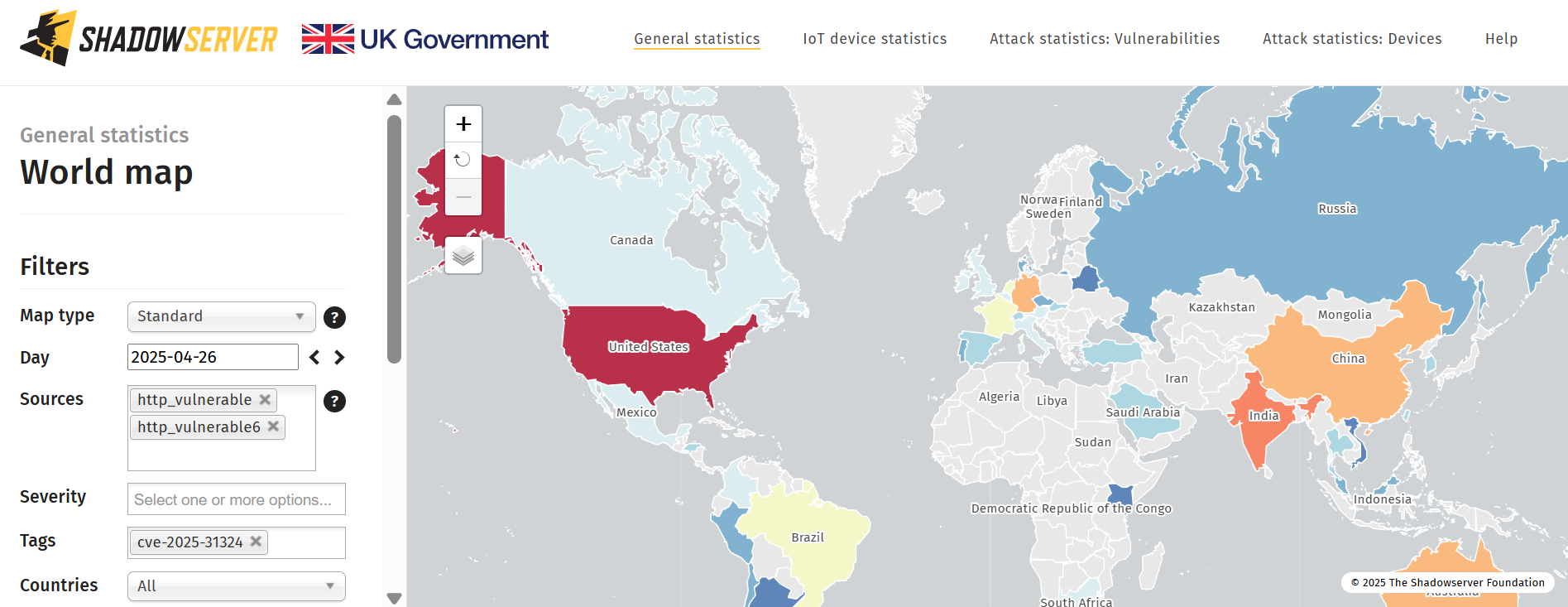
Attackers are actively exploiting a recently patched zero-day vulnerability in SAP's NetWeaver Visual Composer Web-based software modeling tool.
CVE-2025-31324 is a critical vulnerability with a maximum CVSS score of 10 that affects all SAP NetWeaver 7.xx versions. It allows unauthenticated remote attackers to upload arbitrary files to internet-exposed systems without any restrictions.
SAP issued an emergency patch for the vulnerability on April 25, three days after ReliaQuest reported exploitation activity targeting NetWeaver systems. ReliaQuest initially suspected that attackers were either exploiting an older SAP vulnerability, tracked as CVE-2017-9844, or a new, undisclosed remote file inclusion vulnerability in NetWeaver.
But SAP's later analysis revealed the issue was actually tied to an improper authentication and authorization check in NetWeaver Visual Composer's Metadata Uploader component.
The Shadowserver Foundation, which monitors the internet for threat activity, on April 27 reported finding 454 internet-exposed SAP NetWeaver instances that are vulnerable to attack via the new bug. Most of the vulnerable instances are in the US (149), followed by India with 50 and Australia with 37, Shadowserver said.
Organizations that are unable to update immediately should consider disabling Visual Composer and restricting access to the affected endpoint, as Rapid7 recommends. (Jai Vijayan / Dark Reading)
Related: SC World, MSSP Alert, Rapid7, The Register, The Center for Internet Security, Cyberscoop, Onapsis
The Removing Our Unsecure Technologies to Ensure Reliability and Security (ROUTERS) Act, a bill requiring the Department of Commerce to study national security issues posed by routers and modems controlled by US adversaries, passed the House of Representatives.
The House moved quickly on the bill, which was introduced by Reps. Bob Latta (R-OH) and Robin Kelly (D-IL) in March, and advanced out of the chamber’s Energy and Commerce Committee three weeks ago.
The bill, which calls on Commerce’s assistant secretary for communications and information to lead a study into devices that are “designed, developed, manufactured, or supplied” by or subject to the influence of a “covered country,” takes particular aim at China and the state-sponsored hacking campaigns that have plagued US networks. (Matt Bracken / Cyberscoop)
Related: docs.house.gov, Infosecurity Magazine, SC Media
Best Thing of the Day: Malicious Deepfakes Can Land You in Jail
A former high school athletics director accused of using artificial intelligence to create a racist and antisemitic deepfake of a principal in Pikesville, Maryland, has been sentenced to four months in jail as part of a plea deal.
Worst Thing of the Day: Buy Some Real Artwork, It Lasts Longer
Thousands of NFTs that had once sold collectively for millions of dollars briefly vanished from the internet and were replaced with the phrase “This content has been restricted. Using Cloudflare’s basic service in this manner is a violation of the Terms of Service," underscoring the ephemeral nature of crypto-backed pictures that dominated the internet for a few years.
Bonus Worst Thing of the Day: Keep Your Stuff Off the Internet
Thousands of automatic tank gauge (ATG) devices in automobiles are accessible over the internet and are just "a packet away" from compromise.
Closing Thought
@bbcnews The images of women shown here appear to be AI and not real - however one company is using photos of celebrities. #Apple #Deepfake #AI #ArtificialIntelligence #GameOfThrones #LenaHeadey #MaisieWilliams #Tech #Technology #BBCNews
♬ original sound - BBC News - BBC News
,




