Hackers who stole trove of sensitive UPenn data deride 'dog**** elitist institution'
LLM giants are trying to stop indirect prompt injection attacks, Oz government warns of Cisco IOS XE flaws, Polish authorities probe cyberattack on online loan platform, Chinese President Xi Jinping joked about smartphone backdoors, Shiba Inu implements massive security upgrade, much more


Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
A hacker has taken responsibility for last week's University of Pennsylvania "We got hacked" email incident, saying it was a far more extensive breach that exposed data on 1.2 million donors and internal documents.
On Friday, University of Pennsylvania alums and students began receiving multiple offensive emails from Penn.edu addresses claiming the university had been hacked and data stolen.
"The University of Pennsylvania is a dog**** elitist institution full of woke retards. We have terrible security practices and are completely unmeritocratic," reads the email sent to Penn alumni and students.
"We hire and admit morons because we love legacies, donors, and unqualified affirmative action admits. We love breaking federal laws like FERPA (all your data will be leaked) and Supreme Court rulings like SFFA."
The emails originated from connect.upenn.edu, a Penn mailing list platform hosted on Salesforce Marketing Cloud. The university downplayed the incident, describing the messages as "fraudulent emails" that were "obviously fake."
The threat actor behind the attack contacted BleepingComputer, claiming the intrusion was far broader and that they had gained access to multiple university systems.
The hacker said their group "gained full access" to an employee's PennKey SSO account, allowing access to Penn's VPN, Salesforce data, Qlik analytics platform, SAP business intelligence system, and SharePoint files.
They said they exfiltrated data for roughly 1.2 million students, alumni, and donors, including names, dates of birth, addresses, phone numbers, estimated net worth, donation history, and demographic details such as religion, race, and sexual orientation.
The attackers told BleepingComputer they breached Penn's systems on October 30th and completed data downloads by October 31st, when the compromised employee account was locked and access was lost.
After discovering their access had been revoked, the hacker said they still had access to Salesforce Marketing Cloud and used it to send the offensive mass email to roughly 700,000 recipients. (Lawrence Abrams / Bleeping Computer)
Related: The Daily Pennsylvanian, Philly Voice, TechCrunch
Google DeepMind, Anthropic, OpenAI, and Microsoft are among those trying to prevent so-called indirect prompt injection attacks, where a third party hides commands in websites or emails designed to trick the AI model into revealing unauthorized information, such as confidential data.
“AI is being used by cyber actors at every chain of the attack right now,” said Jacob Klein, who leads the threat intelligence team at AI start-up Anthropic.
AI groups are using a variety of techniques, including hiring external testers and using AI-powered tools, to detect and reduce malicious uses of their powerful technologies. But experts warned the industry had not yet solved how to stop indirect prompt injection attacks.
“When we find a malicious use, depending on confidence levels, we may automatically trigger some intervention, or we may send it to human review,” he added.
Google DeepMind uses a technique called automated red teaming, where the company’s internal researchers constantly attack its Gemini model in a realistic way to uncover potential security weaknesses. (Melissa Heikkilä / Financial Times)
Related: Business Standard, PYMNTS, Fudzilla
Patients from Genea, one of Australia's largest IVF clinics, are seeking compensation after their sensitive medical information was published on the dark web earlier this year.
The representative complaint, a type of complaint lodged by an individual on behalf of two or more people, was sent to the Office of the Australian Information Commissioner on 20 October. Melbourne law firm Phi Finney McDonald is acting on behalf of affected patients.
The complaint alleges the company failed to take reasonable steps to protect information from misuse, interference, loss, and unauthorized access.
It also alleges Genea failed to destroy or remove information once it was no longer needed, and that it breached its obligations under the Privacy Act 1988 by not informing affected individuals sooner.
In February, Genea Fertility informed clients via email that personal data had been breached by cybercriminals and posted to the dark web.
The exposed data includes the medical histories, diagnoses, treatments, and prescription medications of those clients, as well as pathology and diagnostic test results. (Cheyne Anderson, Cameron Carr / SBS News)
Related: Cyber Daily
The Australian government is warning about ongoing cyberattacks against unpatched Cisco IOS XE devices in the country to infect routers with the BadCandy webshell.
The vulnerability exploited in these attacks is CVE-2023-20198, a max-severity flaw that allows remote unauthenticated threat actors to create a local admin user via the web user interface and take over the devices.
Cisco fixed the flaw in October 2023, which was then marked as an actively exploited issue. A public exploit became available two weeks later, fueling mass exploitation for backdoor planting on internet-exposed devices.
The Australian authorities have warned that variants of the same Lua-based BadCandy web shells are still used in attacks throughout 2024 and 2025, indicating that many Cisco devices remain unpatched.
Once installed, BadCandy allows remote attackers to execute commands with root privileges on compromised devices. (Bill Toulas / Bleeping Computer)
Related: ASD, Cyber Daily, Security Affairs, The Register
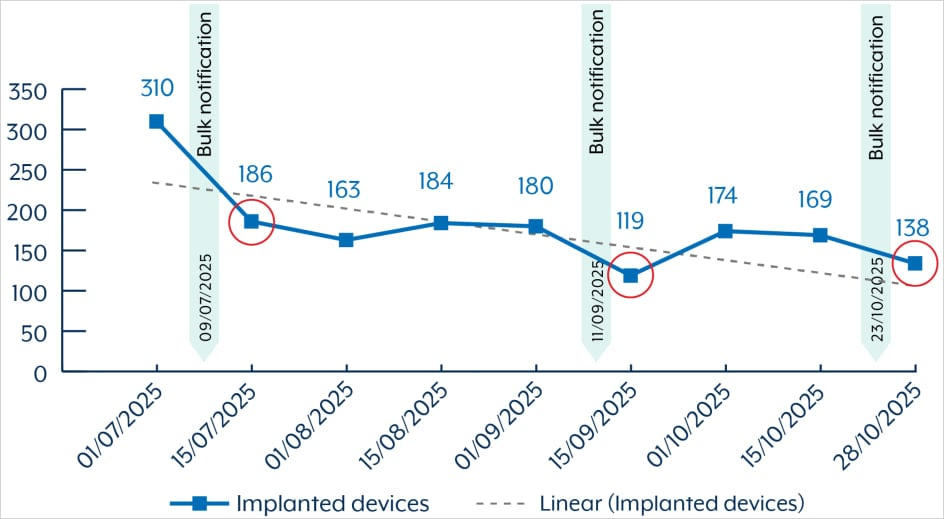
Sources close to the investigation say Yuriy Igorevich Rybtsov, a 41-year-old from the Russia-controlled city of Donetsk, Ukraine, was previously referenced in US federal charging documents only by his online handle “MrICQ.”
According to a 13-year-old indictment (PDF) filed by prosecutors in Nebraska, MrICQ was a developer for a cybercrime group known as “Jabber Zeus.”
Two sources familiar with the Jabber Zeus investigation said Rybtsov was arrested in Italy, although the exact date and circumstances of his arrest remain unclear. A summary of recent decisions (PDF) published by the Italian Supreme Court states that in April 2025, Rybtsov lost a final appeal to avoid extradition to the United States.
According to the mugshot website lockedup[.]wtf, Rybtsov arrived in Nebraska on October 9, and was being held under an arrest warrant from the US Federal Bureau of Investigation (FBI).
The data breach tracking service Constella Intelligence found breached records from the business profiling site bvdinfo[.]com showing that a 41-year-old Yuriy Igorevich Rybtsov worked in a building at 59 Barnaulska St. in Donetsk. Further searching on this address in Constella finds the same apartment building shared by a business registered to Vyacheslav “Tank” Penchukov, the leader of the Jabber Zeus crew in Ukraine. (Brian Krebs / KrebsonSecurity)
Polish Deputy Prime Minister and Minister for Digital Affairs Krzysztof Gawkowski confirmed that Polish authorities are investigating a large-scale cyberattack that compromised personal data belonging to clients of SuperGrosz, an online loan platform operated by AIQLABS.
Gawkowski described the incident as “very serious,” warning that criminals had gained access to sensitive personal information, including names, national identification numbers (PESEL), ID card details, email and home addresses, phone numbers, nationality, marital status, number of children, employment details, employer contact information, declared income, bank account numbers, and Facebook identifiers.
The minister said that Poland's national cybersecurity teams - CSIRT KNF (responsible for financial institutions) and CSIRT NASK (the national research network) - are already investigating the breach and that the Polish Personal Data Protection Office has been notified. “State services are working to identify the convictions,” he wrote. (Polskie Radio)
Related: Safedane.gov.pl
Chinese President Xi Jinping joked about security backdoors while presenting a pair of Xiaomi Corp. smartphones to his South Korean counterpart, a rare moment of spontaneous levity captured during a week of tense trade negotiations with Donald Trump.
Xi, in South Korea to meet Trump on the sidelines of the Asia-Pacific Economic Cooperation summit, presented the pair of devices to Korean President Lee Jae Myung. In a video circulated on social media, Lee asked: “Is the line secure?” Xi chuckled, pointed at the gadgets, and replied through an interpreter: “You can check if there’s a backdoor.” The two leaders burst into laughter.
The exchange was striking because the issue of security and alleged espionage is a sensitive one and a major thorn in US-Chinese relations. American lawmakers have raised the possibility that tech companies such as Huawei Technologies Co. build backdoors — ways to gain access to sensitive data — into their equipment or services, something the firms have repeatedly denied. Washington officials have, in turn, broached the idea of working similar access points or tracking technology into products such as Nvidia Corp. chips, which the US company has publicly opposed. (Yuan Gao and Yoolim Lee / Bloomberg)
Related: France 24, XiaomiTime, Forbes Middle East, The Korea Herald, The Indian Express
The Shiba Inu development team has implemented a substantial security upgrade for the Shibarium network as the network works to restore confidence following a security incident that threatened its operations.
Shibarium's legacy public RPC endpoint will be deactivated over the next two weeks. The Remote Procedure Call serves as the essential link between user wallets, decentralized applications, and the blockchain. Without functional RPC endpoints, users cannot execute transactions, interact with smart contracts, or view their account balances.
A critical incident in September forced network operators to pause Shibarium to prevent data corruption. An attacker compromised a validator key and leveraged a temporary delegation of 4.6 million BONE tokens. The malicious actor attempted to gain control over the network consensus.
Developers clarified that the breach did not expose fundamental flaws in the core protocol of Shibarium. The vulnerability stemmed from external access to validator credentials rather than code-level weaknesses. The team responded by implementing multiple security layers.
New protective measures include a validator denylisting system that can quickly isolate compromised nodes. The Plasma Bridge now requires a seven-day withdrawal delay, giving the team time to detect and respond to suspicious activity. These changes aim to prevent similar incidents in the future. (Newton Gitonga / Coinpaper)
Related: The Shib, CryptoRank
Thai police arrested 24 suspected members of an international scam network who were hiding in a luxury villa near Bangkok, officials said. Most of the suspects were Filipino nationals who had fled Myanmar following a major crackdown on scam centers there earlier this month.
Police Lt. Gen. Natsak Chaowana, commander of the Central Investigation Bureau, said the operation stemmed from data analysis showing scam networks relocating from Myanmar into Thailand. The suspects were detained during an October 29 raid on a villa in Samut Prakan province, just south of Bangkok.
Authorities found 22 foreigners, mostly Filipinos aged 23 to 38, living at the property. Immigration checks revealed that two were in Thailand illegally and 17 had overstayed their visas. Three others, a Singaporean man and two Filipinos, had valid visas but faced revocation due to their alleged involvement in the group.
All suspects admitted that they had worked as scammers in Myawaddy, a border town in Myanmar notorious for criminal syndicates. They told police they fled the area after fighting broke out around October 21. Their manager arranged for their escape to Thailand and rented the villa for about 200,000 baht ($5,400) from October 27–31 while they prepared to move on to Cambodia to resume their operations. (Khaosod English)
Related: The Straits Times
The first test cases in an action against the Police Service of Northern Ireland following a significant data breach are to get underway at Belfast High Court.
The breach happened in August 2023 when a spreadsheet released as part of a freedom of information request held hidden data with the initials, surname, rank, and role of PSNI officers and staff.
Police later said the information had gotten into the hands of dissident republicans.
In the aftermath of the leak, some officers chose to move house and change their daily routines.
A group action is being taken by police officers and staff over the breach.
Belfast legal firm Edwards Solicitors, which represents the majority of plaintiffs in the action, said the outcomes for the test cases will guide thousands of other cases.
It said that even though the PSNI accepted liability for the data breach, and a business case has been approved to make a “universal offer” to those bringing claims, the employer has said it cannot make the offer as it is not affordable within its current funding.
Partner and head of litigation at Edwards Solicitors, Philip Gordon, said: “The outcome of these initial cases in the High Court will provide some direction and guidance for the parties.
“It remains hugely disappointing that the PSNI have not resolved their budget issues to allow for a universal offer to be made, but these test cases are the next step in pursuing compensation for our clients who had their personal details revealed in the 2023 data breach. (Rebecca Black / The Independent)
Related: Irish News
Thai police arrested members of a hacking and phishing crime ring that stole data from massage parlor owner phones to scam their clients out of millions of won by threatening to release nonexistent “massage videos” if they didn't pay.
The Gyeonggi Nambu Provincial Police Agency said that it referred four suspects — a hacker in his 30s and three accomplices in their 20s responsible for gathering and exploiting information — to the prosecution.
The hacker and the other suspects, who were local acquaintances, are accused of forming an organized crime ring. Police applied Article 114 of the Criminal Act, which covers the organization of criminal groups.
According to police, the hacker began collecting contact information from massage parlors in Seoul, Gyeonggi, and Daegu in January 2022, tricking nine owners into installing a malicious app by claiming it was for business purposes. The app secretly stole client data, including contacts, messages, and call records.
The accomplices allegedly set up shop in an officetel in Nam District, Busan, and used the stolen data to blackmail 62 victims, extorting around 500 million won ($351,000) in total. (SON SUNG-BAE / Korea JoongAng Daily)
Related: The Chosun
Cybersecurity experts from multiple federal agencies released guidance to help organizations bolster their defenses against attacks on on-premises Microsoft Exchange Servers, resurfacing and building upon previously shared advice that generally applies to most technology.
The Cybersecurity and Infrastructure Security Agency said the security blueprint for Microsoft Exchange Server is a follow-up effort to an emergency directive the agency released in August for CVE-2025-53786, a high-severity defect affecting on-premises Microsoft Exchange servers. CISA jointly issued the guide with the National Security Agency and cyber agencies in Australia and Canada.
Related: NSA.gov, The HIPAA Journal, Industrial Cyber, Forbes, Bank Info Security
CISA confirmed that a high-severity privilege escalation flaw in the Linux kernel is now being exploited in ransomware attacks.
While the vulnerability (tracked as CVE-2024-1086) was disclosed on January 31, 2024, as a use-after-free weakness in the netfilter: nf_tables kernel component and was fixed via a commit submitted in January 2024, it was first introduced by a decade-old commit in February 2014.
Successful exploitation enables attackers with local access to escalate privileges on the target system, potentially resulting in root-level access to compromised devices.
As Immersive Labs explains, potential impact includes system takeover once root access is gained (allowing attackers to disable defenses, modify files, or install malware), lateral movement through the network, and data theft.
"These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise," CISA said. "Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable." (Sergiu Gatlan / Bleeping Computer)
Related: CISA, Security Affairs, Immersive Labs
Best Thing of the Day: Vox Populi Hates Flock Cameras
A growing number of Americans have gotten involved in local politics to dispute the use of Flock license plate scanning equipment in their towns.
Worst Thing of the Day: Waiting for Godot, But With Computers
The Foreign Affairs Ministry of Mauritius says Vanita Mirpuri is prohibited, from leaving the country because of a five-year-old “computer misuse” charge against her based on a complaint by her former husband that has now been withdrawn, but Canada won't return her passport.
Bonus Worst Thing of the Day: ICE Implements Mandatory Facial Scans
Immigration and Customs Enforcement (ICE) does not let people decline to be scanned by its new facial recognition app, which the agency uses to verify a person’s identity and their immigration status.
Closing Thought
alums




