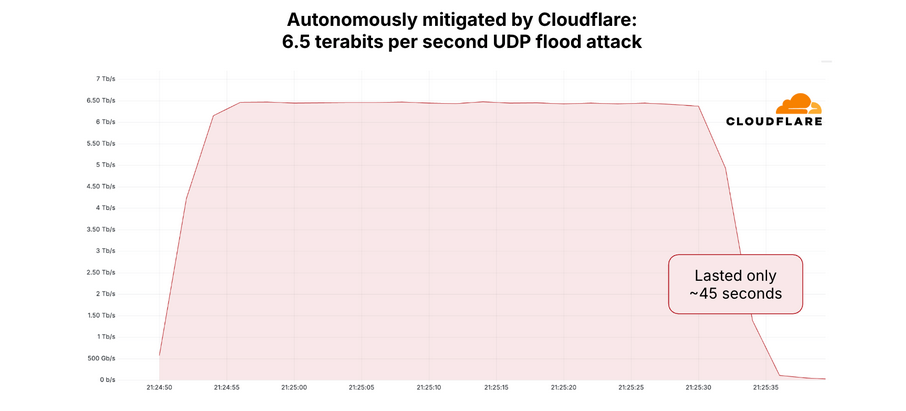
Krebs on Security hit by 'test run' DDoS attack that peaked at 6.3 terabits of data per second
TeleMessage hack leaked broader swathe of US officials' messages than reported, Nineteen-year-old pleads guilty to PowerSchool hack, M&S to take $403m profit hit, Ohio health giant hit by Interlock ransomware, NSO Group gets cold shoulder in DC, Patel shutters FISA watchdog office, much more