MI5 warns that China uses LinkedIn to recruit and compromise lawmakers
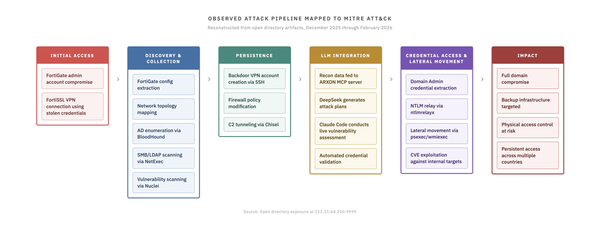
WhatsApp feature can extract 3.5B users' phone numbers, Police raid KT for allegedly hiding breach evidence, Beijing rumors cost TP-Link $1B, LG Energy Solution was hit by a cyberattack, Airlines won't sell passenger data to the US, Toronto schools weren't prepared for PowerSchool breach, much more