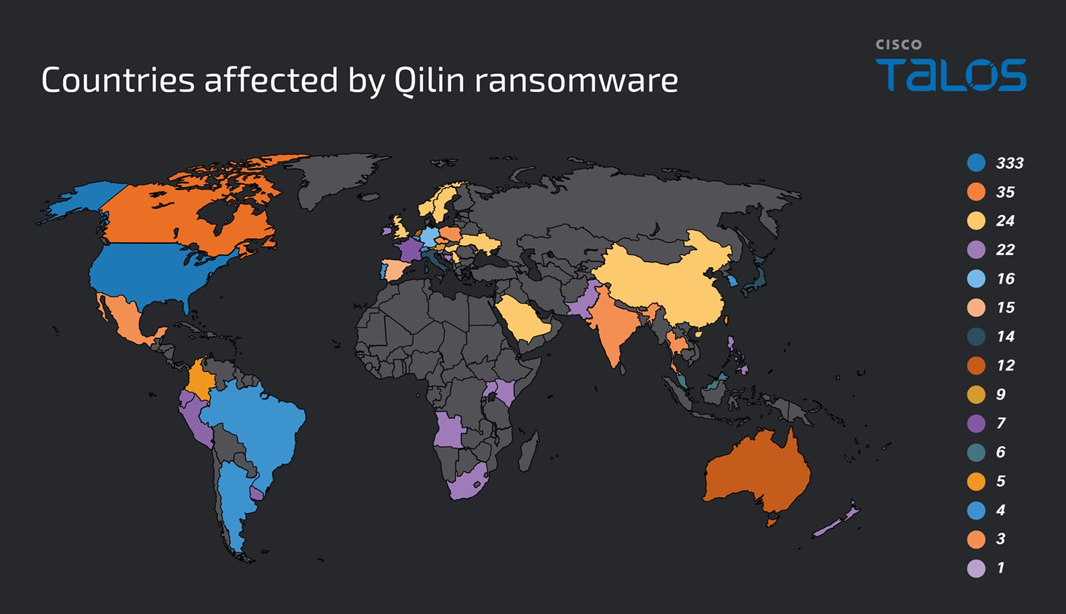
Qilin ransomware activity is surging, with 100 victims listed in August
A major Swedish power supplier was hit by Everest gang, Some top tech companies relent on Australia's age ban, Google denies it suffered a 183m Gmail accounts breach, Western Sydney University hit with fifth cyber incident in two years, Afghan data breach killed 49 people, much more