The White House fired 176 CISA employees on Friday, with more layoffs feared
Scattered Lapsus$ Hunters leaked 5m Qantas, 23m Vietnam Air customers' records, Spanish cops dismantle GXC Team, Dutch gov't warns of China's Nexperia security risks, Breach of crypto betting platform Shuffle exposes user data, FCC chair says sites have removed barred Chinese electronics, much more


Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
The Trump administration on Friday began laying off more than 4,000 federal workers as the government remains shut down, a reduction in force (RIF) that includes the firing of 176 employees at the Cybersecurity and Infrastructure Security Agency (CISA).
Those 176 cut jobs are likely the beginning of further mass layoffs at CISA during the government shutdown, sources close to the situation tell Metacurity. In a statement sent to Metacurity, a Department of Homeland Security spokesperson seemed to suggest that further firings are in the offing for the nation's cybersecurity agency.
“RIFs will be occurring at CISA," the spokesperson said. "During the last administration, CISA was focused on censorship, branding, and electioneering. This is part of getting CISA back on mission.”
It's worth noting that CISA engaged in very little work on disinformation, or what Trump calls "censorship," during the last administration, particularly in comparison to its core mission of securing federal infrastructure. Most of the employees at CISA who worked in this area have already been fired or left the government.
The disdain for "censorship" mirrors that of Project 2025, the Heritage Foundation's blueprint for how Trump should run his second term. Project 2025 was spearheaded by Russell Vought, who is now the director of OMB and is overseeing the firings of US government employees. Project 2025 envisions dismantling CISA altogether and putting the remnants of the agency in the Department of Transportation.
According to Project 2025, “The Cybersecurity and Infrastructure Security Agency (CISA) is a DHS component that the Left has weaponized to censor speech and affect elections at the expense of securing the cyber domain and critical infrastructure, which are threatened daily. A conservative Administration should return CISA to its statutory and important but narrow mission.”
News of this latest round of CISA layoffs follows reporting by Bloomberg that the Trump administration has reassigned some CISA professionals to work on immigration issues. The Trump administration also fired 130 CISA workers earlier this year and released a FY2026 budget that calls for cutting 1,000 jobs at the agency. Trump's 2026 budget calls for an unprecedented $1.23 billion cut in spending on cybersecurity across all government agencies.
This latest round of CISA firings further comes amid a government shutdown during which CISA is functioning with only 889 employees out of its former 2,540 employees. (Sahil Kapur, Yamiche Alcindor, Monica Alba, Laura Strickler, and Zoë Richards / NBC News and Cynthia Brumfield / Metacurity)
Related: New York Post, Federal News Network. The Hill, Bloomberg Government, r/cybersecurity, The Hill, GovExec, NBC News, Court Listener, Databreach Today
The hacker collective Scattered Lapsus$ Hunters has leaked the personal records of 5 million Qantas customers on the dark web, after a ransom deadline set by the cybercriminals passed.
The airline is one of more than 40 firms globally caught up in the hack, reported to contain up to 1bn customer records.
The hackers released an extortion note on a data leaks site on the dark web last week, demanding payment in return for preventing the stolen data from being shared.
The Qantas data, which was stolen from a Salesforce database in a major cyber-attack in June, included customers’ email addresses, phone numbers, birth dates, and frequent flyer numbers. It did not contain credit card details, financial information, or passport details.
On Saturday, the group marked the data as “leaked”, writing: “Don’t be the next headline, should have paid the ransom.”
The big threat now for Qantas customers is a wave of cybercrims facilitated by the release of their personal data. RMIT cyber security professor Matthew Warren said the data leak would lead to a "second wave of scams.:
Australian Home Affairs and Cyber Security Minister Tony Burke insists Qantas will be held accountable after the personal information of 5.7 million of its customers was released onto the dark web by hackers. (Cait Kelly / The Guardian, AAP, and Patrick Brischetto / 9News)
Related: ABC.net.au, PYOK, Aviation A2Z, News.com, Reuters, Bloomberg, RTL Today, Have I Been Pwned, Travel And Tour World, 9News, AFP, Sydney Morning Herald, WebProNews, News.com, ABC.net.au, SBC News, Australian Cybersecurity Magazine, Skift, News.com, Information Age, Simple Flying, Security News | Tech Times, The Cyber Express, Cyberdaily.au, CSO Online, Silicon Republic
According to several hacker forums, Scattered Lapsus$ Hunters has released over 23 million records containing personal data of Vietnam Airlines customers.
ShinyHunters was previously responsible for leaking data from Vietnam’s National Credit Information Center (CIC), which is also mentioned on the site that released the Vietnam Airlines data.
Hackers claim they gained access to Salesforce accounts of 39 companies, including major names like Vietnam Airlines, Google, Cisco, Disney, and FedEx.
Salesforce provides customer relationship management (CRM) solutions to Vietnam Airlines. This indicates that the attackers did not hack Vietnam Airlines’ own systems directly but infiltrated its Salesforce account to extract customer data.
After failing to extort Salesforce, the hackers began publishing and selling data from several companies, including Vietnam Airlines, Qantas, and GAP Inc.
According to posts on hacker forums, the group is offering data from 7.3 million Vietnam Airlines customers for sale.
On the morning of October 13, a representative from VNCERT (under A05 - Ministry of Public Security) confirmed to VietNamNet that Vietnam Airlines’ customer data is indeed being listed for sale on hacker forums. VNCERT is actively investigating the incident. (Vietnamnet Global)
Related: HaveIBeenPwned
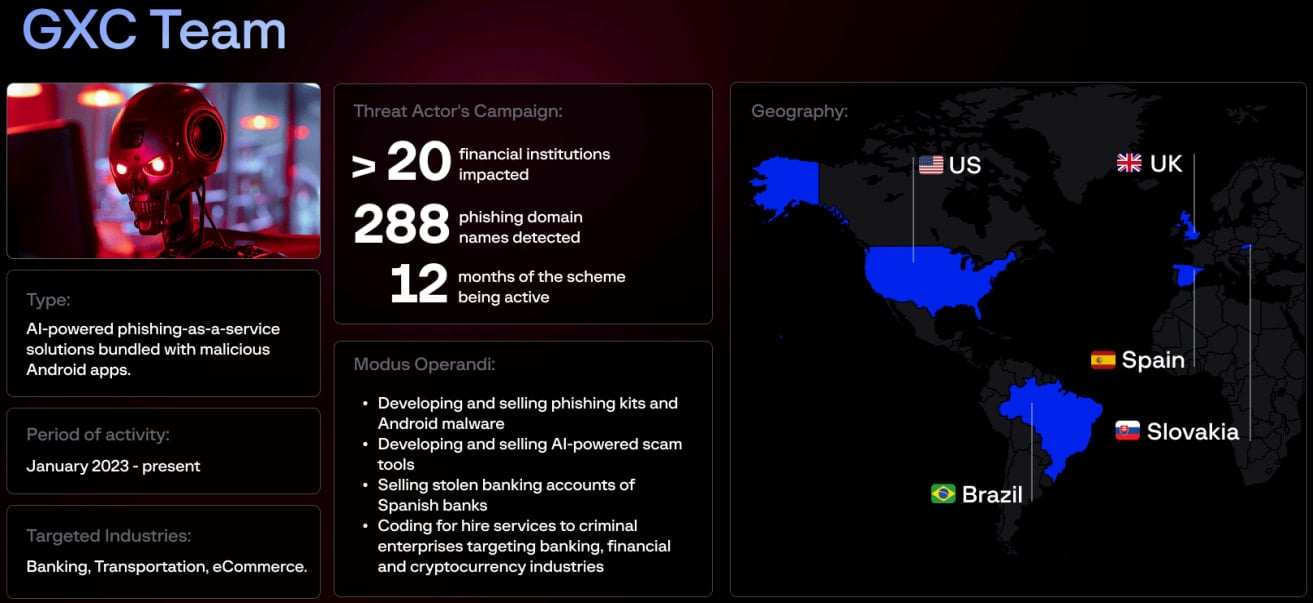
Spanish Guardia Civil have dismantled the “GXC Team” cybercrime operation and arrested its alleged leader, a 25-year-old Brazilian known as “GoogleXcoder.”
The GXC Team operated a crime-as-a-service (CaaS) platform offering AI-powered phishing kits, Android malware, and voice-scam tools via Telegram and a Russian-speaking hacker forum.
“The Civil Guard has dismantled one of the most active criminal organizations in the field of phishing in Spain, with the arrest of a 25-year-old Brazilian young man considered the main provider of tools for the massive theft of credentials in the Spanish-speaking environment,” announced Guardia Civil.
Group-IB has been tracking the operation and says that GXC Team was targeting banks, transport, and e-commerce entities in Spain, Slovakia, the UK, the US, and Brazil. (Bill Toulas / Bleeping Computer)
Related: Guardia Civil, Security Affairs, Group-IB, The 420
The Dutch government has taken control of Chinese-owned semiconductor maker Nexperia, warning of risks to Europe’s economic security after alleging “serious governance shortcomings” at the company.
In a statement, the Dutch Ministry of Economic Affairs said it acted because of “a threat to the continuity and safeguarding of crucial technological knowledge and capabilities” on Dutch and European soil.
The move escalates frictions between Western countries and China over access to high-end technology such as advanced semiconductors and critical raw materials. On Thursday, China placed sweeping restrictions on the exports of rare earths used in products from cars to wind turbines.
The Dutch ministry statement said it invoked the country’s Goods Availability Act because of “recent and acute serious governance shortcomings and actions” at Nexperia, which is based in the Netherlands and has been majority-owned by Chinese technology group Wingtech since 2019.
“The decision aims to prevent a situation in which the goods produced by Nexperia (finished and semi-finished products) would become unavailable in an emergency,” it added. (Andy Bounds, Ryan McMorrow, and Demetri Sevastopulo / Financial Times)
Related: Government.nl, Silicon Republic, The Economic Times, CNBC, BBC, Reuters, Techzine, South China Morning Post, Pekingnology, Morningstar, Inc., DigiTimes, r/europer, r/technology
Shuffle, a leading crypto betting platform, suffered a data breach after its third-party customer service provider was compromised, exposing the data of most of its users.
According to Shuffle founder Noa Dummett, the company’s customer relationship management (CRM) service provider, Fast Track, suffered a data breach that exposed its users’ data. Shuffle used the service in question for “programmatic email sending and various communications with users,” suggesting that those messages and email addresses were likely among the exposed data.
“Unfortunately, it seems that their breach has impacted the majority of our users,” Dummett wrote. He said that the company was investigating how the breach took place and “where this data ended up.”
The amount of data is likely to be significant. According to SimilarWeb, Shuffle was the 12,064th most-visited website in the world at the time of writing. Dummett also noted that the company will be looking for alternatives to Fast Track. (Adrian Zmudzinski / Cointelegraph)
Related: Brave New Coin, Gambling Insider, Crypto Economy
Brendan Carr, the chair of the US Federal Communications Commission, said that major US online retail websites have removed several million listings for prohibited Chinese electronics as part of a crackdown by the agency.
Carr said that the items removed are either on a US list of barred equipment or were not authorized by the agency, including items like home security cameras and smart watches from companies including Huawei, Hangzhou Hikvision, ZTE, and Dahua Technology Company.
The FCC issued a new national security notice reminding companies of prohibited items, including video surveillance equipment. Carr said the items could allow China to "surveil Americans, disrupt communications networks and otherwise threaten US national security." (David Shepardson / Reuters)
Related: Chris Krebs on LinkedIn, The Chosun
Analysts at KELA report that the scale and scope of North Korean fraudulent job schemes likely extend beyond most people’s understanding, with new material showing that at least one group has been working outside the IT realm and in the very different field of architecture and civil engineering.
Files linked to the alleged North Korean operatives show 2D architectural drawings and some 3D CAD files for properties in the United States, Kela researchers say. In addition to the plans, the scammers were also seen claiming to advertise a range of architectural services and using, or creating, architectural stamps or seals, which can act as legal certification that drawings follow local building regulations.
“These operatives are active not only in technology and cybersecurity but also in industrial design, architecture, and interior design, accessing sensitive infrastructure and client projects under fabricated identities,” Kela writes in a blog post.
Kela’s security researchers focused on a GitHub account linked to one suspected North Korean IT network before analyzing further accounts and profiles. The GitHub profile, plus some connected personas and some architectural work, was first identified earlier this year.
The GitHub account publicly listed a series of Google Drive files that could be downloaded by anyone and contained a treasure trove of information linked to the potential scammers. The files included details of work being pursued by the DPRK-linked accounts, duplicate and false CVs, images that could be used as profile pictures, and details of the personas used to find work. (Matt Burgess / Wired)

The Korean Ministry of Science and ICT said it has asked the police to investigate allegations that telco giant KT Corp. obstructed a government probe into the company's unauthorized mobile payment breaches.
In late August, unauthorized mobile payments worth a combined 240 million won (US$168,000) were reported in Seoul and nearby areas after the personal data of hundreds of KT users were compromised through illegal micro base stations.
The government subsequently formed a joint public-private investigation team to scrutinize the incident. However, the ministry said KT failed to cooperate with the probe fully and interfered with the team's activities.
"KT submitted false information regarding the timing of the server disposal and did not report backup logs for the disposed servers to the investigation team until Oct. 18," the ministry said in a statement submitted to the National Assembly's Science, ICT, Broadcasting and Communications Committee for an annual parliamentary audit.
"We determined there was intentional misconduct to obstruct the government investigation, including submitting false materials and concealing evidence," it added. (Yonhap News Agency)
Related: The Korea Times, Chosun Biz
An over-the-air (OTA) update to the infotainment system in some Jeeps appears to be causing certain models to go into a limp mode or otherwise fail to operate.
It’s not clear what the most recent update from Jeep was supposed to do, though owners are referring to it as a “U-Connect update,” which is to say that it’s possibly related to the infotainment system.
How that results in the vehicle’s powertrain failing is not yet obvious, though this happened before with at least one other automaker.
Back in 2023, Rivian pushed out an update for its electric trucks that failed. The vehicles would get to 90% and then not complete the installation. While this was an annoyance, we reported at the time that the cars could still be driven. Rivian blamed the incident on a “fat finger” coding mistake. In 2023, some Lucid owners also reported that an update caused their cars to “brick,” which is to say the vehicle stopped functioning. (Matt Hardigree / The Autopian)
Related: The Stack
Andrea Orcel, CEO of UniCredit bank, received a notification on April 29 from Apple, which had worked with Citizen Lab, that he was targeted with Graphite spyware from the Israeli company Paragon Solutions.
Orcel received the notification of potential compromise between 2 and 6 pm on April 29, 2025: "Threat notification. Apple has detected a targeted mercenary spyware attack against your iPhone." Along with him, an unspecified number of users around the world, including Fanpage journalist Ciro Pellegrino.
A few months earlier, Citizen Lab had collaborated with WhatsApp to identify a vulnerability: what both cases have in common is that both Apple and WhatsApp were exposed to several flaws exploited by Paragon to install its spyware on the targets' phones, without their knowledge. (Raffaele Angius / IRPI Media)
Related: La Stampa
United Imaging, a corporation with deep ties to the Chinese Communist Party and a history of industrial espionage, produces hardware used for sensitive medical research funded by the National Institutes of Health.
United Imaging is a multinational medical technology company based in Shanghai that has conducted research alongside the Chinese military and cooperates with the state-backed Chinese Academy of Sciences. In addition to its government links, three United Imaging employees were charged in 2013 with transferring “nonpublic information” generated at an NIH-funded lab to both the company and the Chinese Academy of Sciences in exchange for payments.
Despite United Imaging’s history and despite evidence that some Chinese hardware has backdoors allowing data to be remotely downloaded, public records show that the company’s hardware is present at NIH-funded labs and central research installations across the country.
The Center for Quantitative Cancer Imaging at the University of Utah, for instance, had multiple United Imaging PET scanners installed in its clinical research lab as of September 2023, per a press release. Mass General Brigham, a Harvard-affiliated hospital that serves as one of the nation’s leading biomedical research organizations, similarly, used an NIH grant to purchase hardware manufactured by United Imaging. (Robert Schmad / Washington Examiner)
President Donald Trump decided not to nominate Army Lt. Gen. William Hartman to be the next leader of US Cyber Command and the National Security Agency, according to four people familiar with the matter.
Hartman, who has been leading both entities in an acting capacity since April, was recently informed of the decision and submitted his retirement paperwork this week, according to these individuals, who were granted anonymity because they were not authorized to speak publicly about the situation.
Two of the people said the choice was made, in part, after Hartman failed to impress key Defense Department leaders — despite having the backing of Defense Secretary Pete Hegseth and Director of National Intelligence Tulsi Gabbard. The nomination has been expected for weeks, but was never formally submitted to the Senate.
One of the four people said that the nomination could have run into additional resistance from people within the Trump administration who want to end the “dual-hat” leadership arrangement at Cyber Command and the NSA. The idea is that putting a leader with dual-hat experience permanently in the job would make it more difficult to sever the relationship, the source said. The administration’s internal stance is that the dual-hat should remain in place. (Martin Matishak / The Record)
Related: Cipher Brief
Criminals in the UK are cashing in on would-be drivers’ frustration over test delays by claiming they can help them skip queues and obtain licenses without the need to do exams.
Fraudsters are asking for hundreds of pounds for what they say are legitimate licenses, claiming they have staff inside the government testing and licensing bodies working for them.
In one example, the fraudster asked for £850 for a driving license, payable in installments, claiming that a “team of DVSA-certified instructors” would process the buyer’s details.
They claim the driver is enrolled in a test center but will not have to sit the theory or practical test. Instead, they claim their staff submits test results through the system, which leads to the license being issued.
However, the Driver and Vehicle Licensing Agency (DVLA), which issues licenses, and the Driver and Vehicle Standards Agency (DVSA), which carries out tests, have warned that the promised shortcuts are scams designed to gather victims’ money and personal details. (Shane Hickey / The Guardian)
Related: Daily Mail, Inkl
Aisuru, the world’s largest and most disruptive botnet, is now drawing a majority of its firepower from compromised Internet-of-Things (IoT) devices hosted on US internet providers like AT&T, Comcast, and Verizon, new evidence suggests.
Experts say the heavy concentration of infected devices at US providers is complicating efforts to limit collateral damage from the botnet’s attacks, which shattered previous records this week with a brief traffic flood that clocked in at nearly 30 trillion bits of data per second.
The hacked systems that get subsumed into the botnet are mostly consumer-grade routers, security cameras, digital video recorders, and other devices operating with insecure and outdated firmware, and/or factory-default settings. Aisuru’s owners are continuously scanning the internet for these vulnerable devices and enslaving them for use in distributed denial-of-service (DDoS) attacks that can overwhelm targeted servers with crippling amounts of junk traffic. (Brian Krebs / Krebs on Security)
Related: Slashdot
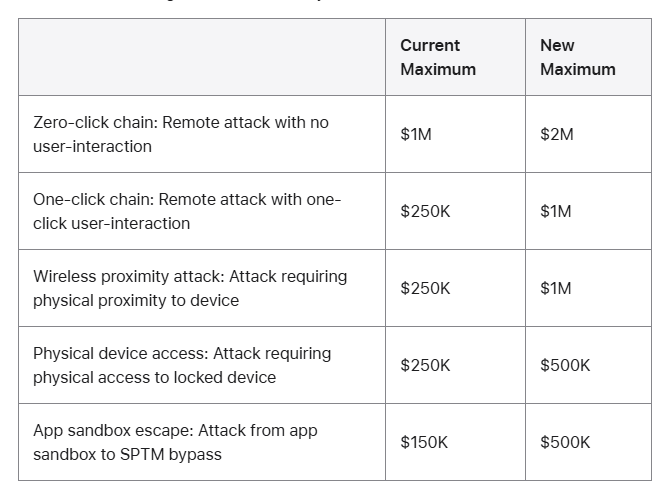
At the Hexacon offensive security conference in Paris, Apple vice president of security engineering and architecture Ivan Krstić announced a new maximum payout of $2 million for a chain of software exploits that could be abused for spyware.
In addition to individual payouts, the company's bug bounty also includes a bonus structure, adding additional awards for exploits that can bypass its extra secure Lockdown Mode as well as those discovered while Apple software is still in its beta testing phase.
Taken together, the maximum award for what would otherwise be a potentially catastrophic exploit chain will now be $5 million. The changes take effect next month. (Lily Hay Newman / Wired)
Related: Apple Security Research, CSO Online, The Verge, Appleosophy, Engadget, AppleInsider, Computerworld, Michael Tsai, BleepingComputer, iThinkDifferent, MacRumors, iPhone in Canada, Neowin, CyberInsider, Macworld, Moneycontrol, Help Net Security, iClarified, 9to5Mac, PCMag, Axios, PhoneArena, SecurityWeek, MacDailyNews, MacTech.com, r/apple, Slashdot
The personal information of thousands of Bectu, or the Broadcasting, Entertainment, Communications and Theatre Union, members has been breached in an “IT security incident” at its parent trade union Prospect.
Union members were emailed with information about the nature of the breach, which Prospect experienced in June.
In the email, Prospect general secretary Mike Clancy said member information accessed included bank details, contact details, and “personal identifiers” like birth dates and protected characteristics.
A person familiar with the incident said some personal case files, containing highly sensitive information, were also breached, and the members affected are being informed.
It is not clear how many people have been impacted, but sources said that it is likely to be the majority of Bectu’s 40,000 members. Bectu is one of the largest UK screen industry unions, with notable members including British filmmaker Ken Loach. (Jake Kanter / Deadline)
Related: The Register
Research suggests that a cyber incident at Banco Hipotecario del Uruguay (BHU) was likely a sophisticated ransomware attack by the group Crypto24, involving the theft of approximately 700GB of sensitive data, including client personal information, legal contracts, and financial records.
The event started around September 30, 2025, disrupting online services and payments, but with in-person operations continuing. Recovery is ongoing, with some services like installment payments resuming by October 7, 2025. (Alberto Daniel Hill / Cyber Midnight)
Related: El Observador, El País Uruguay, Montevideo Portal, Ambito, Telenoche
The city of Sugar Land, TX, is working to restore phone lines, internet service and its online payment system Friday, following a cyber breach.
Local officials said a "cyber event" affected Sugar Land's "internal network infrastructure" and sparked an investigation involving federal, state, and local authorities. The city reported the breach Thursday night and said it affected some online services, such as bill pay.
As of Friday night, officials said they would halt utility disconnections and would not charge late fees until the payment system was back online.
Sugar Land's utilities were working Sunday, but officials were still working to "fully restore" some services, according to city spokesperson Alicia Alaniz. She said officials were still trying to identify the source of the breach. (Jarrod Wardwell / Houston Chronicle)
Related: ABC13, KHOU, The Record, Click2Houston
Michigan City, Indiana, officials are working to restore their systems after a ransomware incident on September 23.
The city said part of their data was impacted, along with municipal employees' internet and telephone access.
An investigation is underway into the full impact of the event. (WSBT)
Related: Hometown News, WIMS, WNDU

Resistant.AI, a provider of native artificial intelligence models for financial crime and fraud prevention, announced it had raised $25 million in a Series B venture funding round.
DTCP led the round, with strong participation from existing investors, including GV and Notion Capital, who are doubling down on their investment. (Cate Lawrence / Tech.eu)
Related: Tech Funding News, Silicon Canals, FinSMEs
1Password founders have agreed to sell a $75 million stake to a fund established earlier this year by Utah Jazz owner Ryan Smith and Accel partner Ryan Sweeney.
The Halo Fund, founded by Smith and Sweeney, contributed the largest investment in a $100 million secondary sale in which investors, including Flume Ventures, bought stakes from 1Password founders, according to the company.
Under the terms of the transaction, the implied value of the password manager and digital security firm remains consistent with its last primary funding round that valued it at $6.8 billion, the company said. (Jeff Stone / Bloomberg)
Related: BetaKit
Best Thing of the Day: Better Late Than Never
Google’s Open Source Vulnerabilities (OSV) database recently added 500–600 new advisories, not because of a sudden flood of new vulnerabilities, but because of a simple policy change that formerly treated disputed OSVs as withdrawn.
Worst Thing of the Day: If the Malware Doesn't Get You, the Pathogens Might
AI pioneer Yoshua Bengio is less concerned about AI creating destructive malware than he is about AI creating a deadly pathogen that could kill humanity.
Closing Thought