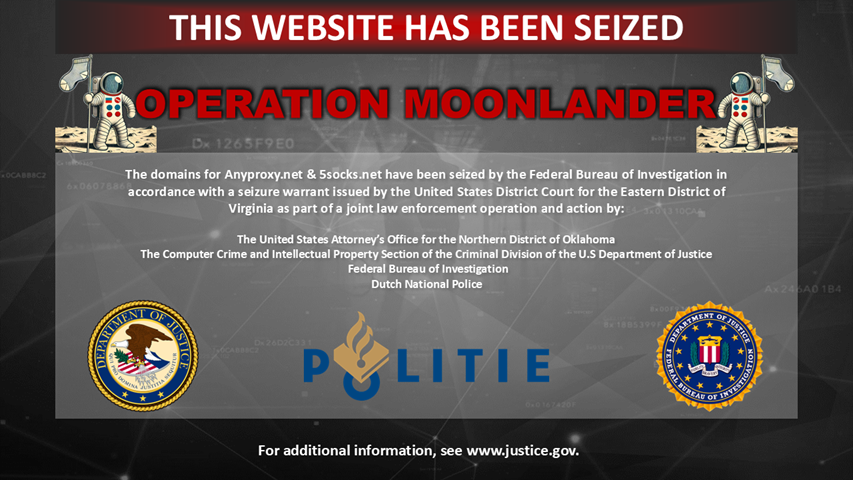
US feds seize two top botnet sites in Operation Moonlander
Florida encryption backdoor bill fails, Suspect in ransomware attack on Dutch research institute detained, College website iClicker was compromised, Google to pay Texas $1.4b for privacy violations, Wikimedia challenges UK Online Safety Act, Ledger Discord server was hacked, so much more