Very young engineers with no government or infosec experience are rifling through critical US government systems
Spyware maker Paragon Solutions targeted 100 people on WhatsApp, Texas governor bans Chinese AI and social media apps, Researchers show DeepSeek's R1 produces toxic content, Anom sellers plead guilty, Keir Starmer's email was hacked by Russia, Wedding invites distributed malware, much more


Please consider supporting Metacurity with an upgraded subscription so that you can continue receiving our daily missives, packed with the top infosec developments you should know.
If you can't commit to a subscription today, consider tipping or donating to help keep Metacurity going.
Six young engineers, all under age 24 and one just out of high school, with no government or cybersecurity experience, are now playing critical roles in Musk’s Department of Government Efficiency (DOGE) project, gaining unrestricted access to computer systems at the Office of Personnel Management (OPM), General Services Administration (GSA), Treasury Department, US AID and possibly elsewhere.
The engineers are Akash Bobba, Edward Coristine, Luke Farritor, Gautier Cole Killian, Gavin Kliger, and Ethan Shaotran.
One source says Bobba, Coristine, Farritor, and Shaotran all currently have working GSA emails and A-suite-level clearance at the GSA. This means they work out of the agency’s top floor and have access to all physical spaces and IT systems.
The source says they worry that the new teams could bypass the regular security clearance protocols to access the agency’s sensitive compartmented information facility, as the Trump administration has already granted temporary security clearances to unvetted people.
One Treasury official, David A. Lebryk, the highest-ranking career official at the department, left the agency after a clash with allies of billionaire Elon Musk over access to sensitive payment systems.
Sources say officials affiliated with Musk’s “Department of Government Efficiency” have been asking for access to the system since after the election, requests reiterated more recently, including after Trump’s inauguration. Tom Krause, a Silicon Valley executive who has now been detailed to Treasury, is among those involved.
After gaining access to the Treasury Department systems, Musk claims he has stopped paying federal contractors, saying, "The corruption and waste is being rooted out in real time."
Musk also announced that he shut down USAID and ordered agency personnel not to attend work today. (Vittoria Elliott / Wired and Gregory Korte and Viktoria Dendrinou / Bloomberg and John Hudson, Ellen Nakashima, Missy Ryan, Mariana Alfaro and Faiz Siddiqui / Washington Post)
Related: Reuters, Washington Post, Ars Technica, ABC News, New York Times, Wired, New York Magazine, CNN, New York Times, TechCrunch, Fortune, Forbes, Palo Alto Online, Digby's Hullabaloo, TweakTown, Mashable, The Guardian, SiliconANGLE, The Indian Express, Feminist Space, New Republic, Gwen Tolios, Associated Press, Hacker News (ycombinator), r/technology, r/politics, r/news, Fortune, r/enoughMuskspam
Meta said that nearly 100 journalists and other members of civil society using WhatsApp were targeted by spyware owned by Paragon Solutions, an Israeli maker of hacking software.
The journalists and other civil society members were alerted of a possible breach of their devices. WhatsApp said it had “high confidence” that the 90 users in question had been targeted and “possibly compromised.”
It is not clear who was behind the attack. Like other spyware makers, Paragon’s hacking software is used by government clients, and WhatsApp said it has not been able to identify the clients who ordered the alleged attacks.
Experts said the targeting was a “zero-click” attack, meaning targets would not have had to click on malicious links to be infected.
Chantilly, VA-based Paragon has recently been scrutinized after Wired magazine reported that it had entered into a $2m contract with the US Immigration and Customs Enforcement’s homeland security investigations division.
The division reportedly issued a stop-work order for the contract to verify whether it complied with a Biden administration executive order restricting the federal government's use of spyware. In its first two weeks in office, the Trump administration has revoked dozens of the Biden administration’s executive orders, but the 2023 order, which prohibited the use of spyware that posed a risk to national security, remains in effect.
WhatsApp said it had sent Paragon a “cease and desist” letter and was exploring its legal options. It said the alleged attacks had been disrupted in December and that it was not clear how long the targets may have been under threat. (Stephanie Kirchgaessner / Wired)
Related: Reuters, The Independent, Middle East Monitor, Palestine Chronicle, Engadget, Firstpost, WION, TechCrunch, Bloomberg, The Record, Forbes, Wired, Syrian Arab News Agency, Hackread, Techreport, Türkiye Today, Cyber Security News, Business Standard, Neowin, The Nation, The Guardian, PCMag, Al Jazeera, Anadolu Ajansı, Engadget, Shafaq News, Moneycontrol, The Verge, Irish Independent, Reuters, r/cybersecurit, r/worldnews, r/InternationalNews, r/technology, Slashdot, Cyberdaily.au, Security Affairs, iTnews - Security, Globes
Texas Governor Gov. Greg Abbott issued a ban on the use of Chinese-backed artificial intelligence and social media apps, including DeepSeek, Lemon8, Moomoo, RedNote, Tiger Brokers, and Webull, on Texas government-issued devices.
His proclamation orders the Texas Department of Public Safety and the Department of Information Resources to add the six technologies to the state's prohibited technologies list. The list bans state employees and contractors from downloading and using the apps on personal and state-owned devices.
In December 2022, Abbott banned the short-form video social media app TikTok. A few months later, he signed Senate Bill 1893, granting him the authority to ban any social media applications or services that pose potential security risks to Texas, including "successor applications" to TikTok or those developed by its parent company, ByteDance Limited. Abbott's most recent proclamation includes RedNote and Lemon8 as two of these applications. (Karoline Leonard / Austin-American Statesman)
Related: Associated Press, Office of the Texas Governor, The Information, KEYE, KCEN-TV, KWTX-TV, FOX 7 Austin
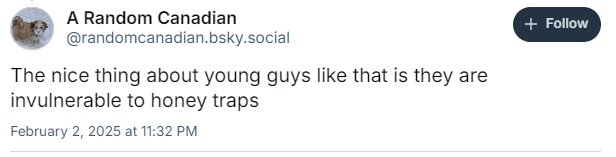
Security researchers from Cisco and the University of Pennsylvania are publishing findings showing that, when tested with 50 malicious prompts designed to elicit toxic content, DeepSeek’s R1 AI model did not detect or block a single one.
The researchers say they were shocked to achieve a “100 percent attack success rate.”
The Cisco researchers drew 50 randomly selected prompts to test DeepSeek’s R1 from HarmBench, a well-known library of standardized evaluation prompts. They tested prompts from six HarmBench categories: general harm, cybercrime, misinformation, and illegal activities. They probed the model running locally on machines rather than through DeepSeek’s website or app, which sends data to China.
Beyond this, the researchers say they have also seen potentially concerning results from testing R1 with more involved, non-linguistic attacks that use Cyrillic characters and tailored scripts to achieve code execution. But for their initial tests, Sampath says his team wanted to focus on findings that stemmed from a generally recognized benchmark.
The findings are part of growing evidence that DeepSeek’s safety and security measures may not match those of other tech companies developing LLMs. DeepSeek’s censorship of subjects deemed sensitive by China’s government has also been easily bypassed. (Lily Hay Newman and Matt Burgess / Wired)
Related: Cisco, PCMag, Forbes, Dark Reading, Unit 42, Wallarm, Futurism, PaymentSecurity.io, WinBuzzer, ZDNET, Wired, r/technews, Enkrypt AI
Aurangzeb Ayub, Shane Ngakuru, Seyyed Hossein Hosseini, and Alexander Dmintrienko pleaded guilty this month in San Diego to selling Anom devices, the encrypted phone secretly backdoored by the FBI that led to the largest sting operation in history.
The defendants were set to go to trial, and the government was preparing to reveal the real identity of the confidential human source who had provided the FBI with the Anom company.
The court records released as part of the plea deals also provide new insight into how some of the phone sellers discussed drug trafficking on their Anom devices as well.
Anom became a popular tool for serious criminals in Australia, Europe, South America, and South East Asia. Customers used the phones to coordinate massive, multi-ton shipments of drugs. In June 2021, authorities launched a global relay race of raids, with more than nine thousand law enforcement officials acting across a single day. (Joseph Cox / 404 Media)
Related: Mobile ID World
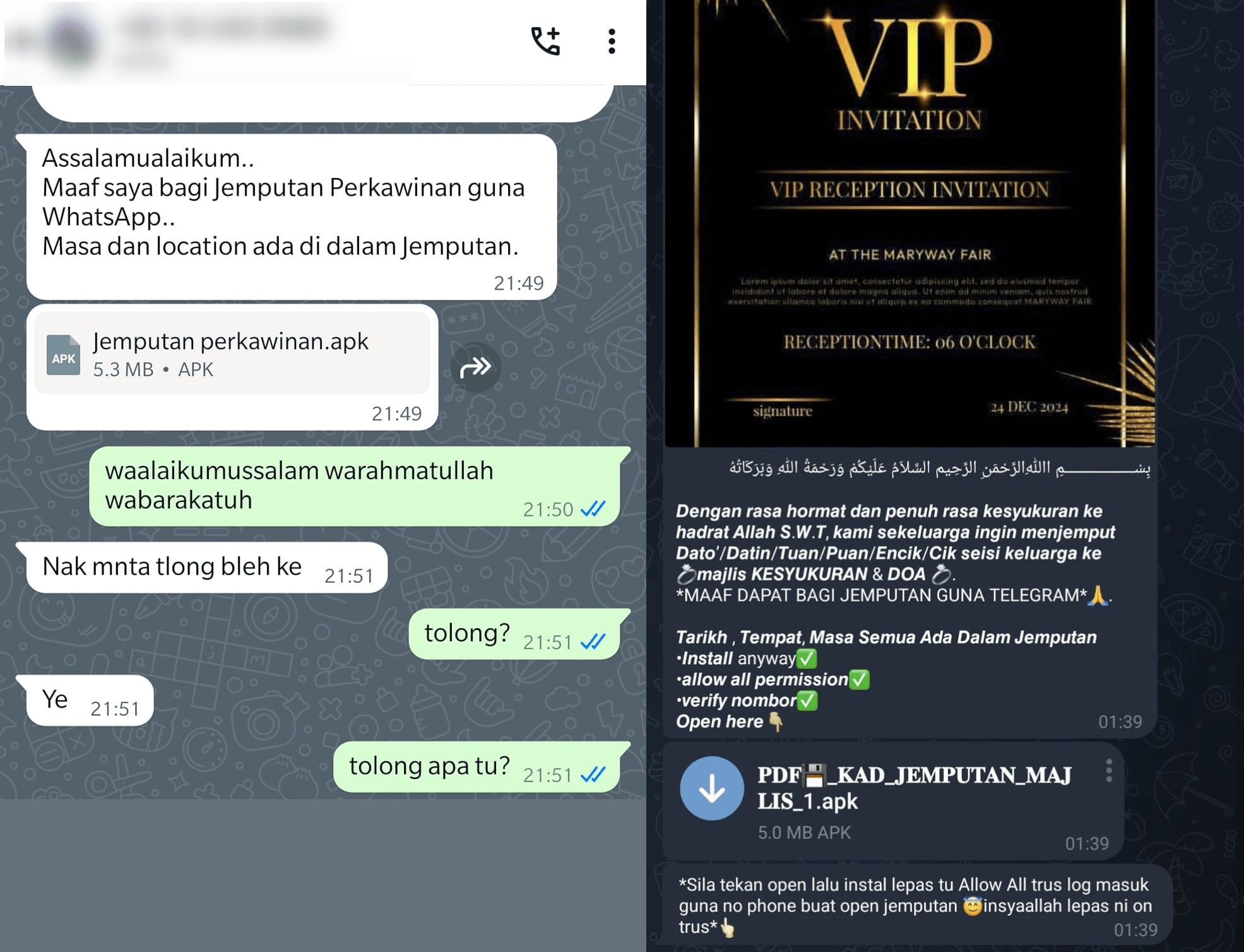
Researchers at Kaspersky report that cybercriminals are using fake wedding invitations targeting users in Malaysia and Brunei to distribute a newly discovered Android malware called Tria.
Since mid-2024, the attackers have been spreading the malware through private and group chats on Telegram and WhatsApp, inviting users to weddings and prompting them to install a mobile app to receive the invitation.
The researchers warn that the stolen information could be used to access online banking, reset passwords, or hijack accounts that rely on email and messaging app authentication.
The attackers' primary goal appears to be gaining complete control of victims’ WhatsApp and Telegram accounts, allowing them to spread malware further or send fraudulent money requests to contacts. (Daryna Antoniuk / The Record)
India has eased restrictions on its Aadhaar authentication service, a digital identity verification framework linked to the biometrics of over 1.4 billion people, to let businesses, including those offering services such as e-commerce, travel, hospitality, and healthcare, use the verification system to authenticate their customers.
The update has raised privacy concerns as New Delhi has yet to define the guardrails it would consider to avoid misuse of individuals’ biometric IDs. (Jagmeet Singh / TechCrunch)
Related: pib.gov.in, Scroll.in, Inc42 Media.
Australian privacy commissioner Karly Kind recently awarded $10,000 in compensation to a complainant whose healthcare records became “intertwined” with those of a person, a doppelganger who shared the same name and date of birth.
“Intertwinement primarily occurs when staff incorrectly add personal information to the wrong account, or a third-party provider submits a claim for the wrong customer,” she wrote.
Kind suggested that hundreds of Australians share the same name and date of birth and that when their government records become intertwined, they “may suffer not only inconvenience but real harm.” She mentioned the possibility of health practitioners being denied access to accurate records and difficulties accessing “financial aspects of health and government services.”
“Although only a small subset of Australians may be affected, the potential harm is significant,” she wrote.
For one such person, identified as “ATQ” in a complaint about intertwined data, their medical records included info about three people who shared their name and birthday after four mistakes by government workers. (Simon Sharwood / The Register)
Related: Australian Information Commissioner, Carly Kind on LinkedIn
In their new book "Get In," Patrick Maguire and Gabriel Pogrund report that in his rise to power, labor leader Keir Starmer was forced to abandon his personal email account after the security services investigated a suspected Russian hack.
In 2022, Jill Cuthbertson, his head of office, circulated a note without explanation instructing staff not to email Starmer under any circumstances.
Starmer subsequently changed his email address, which a source said had been “dangerously obvious,” and added two-factor authentication, a fail-safe under which users can access an account only after passing two security checks. (Patrick Maguire and Gabriel Pogrund / The Times)
Related: The Telegraph, Daily Mail, The Sun
Seraphic Security, an Israeli startup competing in the enterprise browser space, announced it had raised $29 million in a Series A venture funding round.
GreatPoint Ventures led the round, with CrowdStrike Falcon Fund, Planven, Cota Capital, and Storm Ventures also participating. (Ryan Naraine / Security Week)
Related: FinTech Global, Seraphic Cyber Security, FinSMEs
Invary, a pioneer in runtime integrity solutions, announced it had raised $3.5 million in a venture funding seed round.
SineWave Ventures, Flyover Capital, Hyperlink Ventures, and KCRise Fund participated in the round. (Invary)
Frenos, a startup that has developed an autonomous operational technology (OT) security assessment platform, announced it had raised $3.88 million in a venture funding seed round.
DataTribe led the round. (Eduard Kovacs / Security Week)
Related: Pulse 2.0, Business Wire, The Business Journals, The Paypers, FinSMEs
Best Thing of the Day: A Bright Spot in a Dismal Situation
Cybersecurity and Infrastructure Security Agency (CISA) employees were told they are not eligible for the federal government-wide deferred resignation program being pushed by Elon Musk via the US Office of Personnel Management.
Bonus Best Thing of the Day: Please, No AI at Anthropic
AI company Anthropic is telling its job applicants not to use AI when filling out applications.
Worst Thing of the Day: Please, No Politics Over Here at r/cybersecurity
Over at r/cybersecurity, the mods want to ban discussion of politics because cybersecurity is a pure technology discipline that rises above the fray of dictators and autocrats attempting to seize control over and jeopardize the security of critical infrastructure.




