A database with 149 million usernames and passwords was exposed on the internet
Venezuelan nationals who stole cash from ATMs using malware will be deported from US, FBI asked Microsoft to unlock encrypted laptops, Under Armour is investigating massive data breach, Tech investors want the US government to probe S. Korea's treatment of Coupang following data breach, much more


A database containing 149 million account usernames and passwords—including 48 million for Gmail, 17 million for Facebook, and 420,000 for the cryptocurrency platform Binance—has been removed after security researcher Jeremiah Fowler reported the exposure to the hosting provider.
Fowler could not find indications of who owned or operated it, so he worked to notify the host, which took down the trove because it violated the terms of service agreement.
In addition to email and social media logins for several platforms, Fowler also observed credentials for government systems from multiple countries, as well as consumer banking and credit card logins and media streaming platforms. Fowler suspects that the database had been assembled by infostealing malware that infects devices and then uses techniques like keylogging to record information that victims type into websites.
While attempting to contact the hosting service over the course of about a month, Fowler says the database continued to grow, accumulating additional logins for an array of services. He is not naming the provider, because the company is a global host that contracts with independent regional companies to expand its reach. The database was hosted by one of these affiliates in Canada.
In addition to the 48 million Gmail credentials, the trove also contained about four million for Yahoo accounts, 1.5 million for Microsoft Outlook, 900,000 for Apple’s iCloud, and 1.4 million for “.edu” academic and institutional accounts. There were also, among others, about 780,000 logins for TikTok, 100,000 for OnlyFans, and 3.4 million for Netflix. The data was publicly accessible and searchable using just a web browser. (Lily Hay Newman / Wired)
Related: ExpressVPN, Techzine
The US Justice Department announced that 34-year-old Luz Granados and 40-year-old Johan Gonzalez-Jimenez, two Venezuelan nationals convicted of using malware to steal cash from ATMs, will be deported.
They conducted ATM jackpotting, removing the targeted ATM’s outer casing and connecting a laptop to the machine to install malware. The malware then enabled them to instruct the ATM to dispense all its cash.
Granados, sentenced to time served, must pay $126,340 in restitution, while Gonzalez-Jimenez, sentenced to 18 months in prison, was ordered to pay $285,100.
Both defendants face deportation, with Granados currently in custody awaiting removal and Gonzalez-Jimenez set to be deported following his prison sentence.
This announcement came less than two weeks after the DoJ announced that a group of five Venezuelan nationals had pleaded guilty or been sentenced for their role in a multi-state ATM jackpotting ring. They also faced deportation. (Eduard Kovacs / Security Week)
Related: Justice Department, COLA Daily, WIS10, WACH
Early last year, the FBI served Microsoft with a search warrant, asking it to provide recovery keys to unlock encrypted data stored on three laptops in the first known instance where the Redmond, Washington company has provided any encryption key to law enforcement.
Federal investigators in Guam believed the devices held evidence that would help prove individuals handling the island’s Covid unemployment assistance program were part of a plot to steal funds.
The data was protected with BitLocker, software that’s automatically enabled on many modern Windows PCs to safeguard all the data on the computer’s hard drive. BitLocker scrambles the data so that only those with a key can decode it.
It’s possible for users to store those keys on a device they own, but Microsoft also recommends BitLocker users store their keys on its servers for convenience. While that means someone can access their data if they forget their password, or if repeated failed attempts to log in lock the device, it also makes them vulnerable to law enforcement subpoenas and warrants.
In the Guam case, it handed over the encryption keys to investigators.
Microsoft confirmed to Forbes that it does provide BitLocker recovery keys if it receives a valid legal order. “While key recovery offers convenience, it also carries a risk of unwanted access, so Microsoft believes customers are in the best position to decide... how to manage their keys,” said Microsoft spokesperson Charles Chamberlayne.
He said the company receives around 20 requests for BitLocker keys per year, and in many cases, the user has not stored their key in the cloud, making it impossible for Microsoft to assist. (Thomas Brewster / Forbes)
Related: Hacker News (ycombinator)
Clothing retailer Under Armour is investigating a recent data breach that purloined customers’ email addresses and other personal information, but so far, there are no signs that the hackers stole any passwords or financial information.
The breach is believed to have happened late last year and affected 72 million email addresses, according to information cited by the cybersecurity website Have I Been Pwned. Some of the records taken also included personal information that included names, genders, birthdates, and ZIP codes.
In an Under Armour statement acknowledging its investigation into the claims of a data breach, the Baltimore-based company said: “We have no evidence to suggest this issue has affected UA.com or systems used to process payments or store customer passwords. Any implication that sensitive personal information of tens of millions of customers has been compromised is unfounded.” (Associated Press)
Related: The Register, Security Magazine, PC Mag, Security Affairs, MarketWatch, The Business Journals, TechCrunch
US-based tech investors Greenoaks and Altimeter said they have petitioned the US government to investigate the South Korean government and potentially impose trade remedies over what they describe as discriminatory treatment of e-commerce company Coupang following a consumer data breach that has caused billions of dollars in losses for investors.
The move comes after Coupang reported in November that personal data for some 33 million customers in South Korea were compromised, triggering a backlash from lawmakers and the public, which prompted a wide-ranging investigation as well as lawsuits from investors and consumers.
The investors said they have asked the US Trade Representative (USTR) to investigate South Korea’s actions and impose "appropriate trade remedies, potentially including tariffs and other sanctions," arguing that the response to the breach has gone far beyond normal regulatory enforcement.
The moves could escalate a corporate dispute into a potential government-to-government trade issue, invoking U.S. trade law and an international treaty to challenge the actions of South Korean authorities. (Hyunjoo Jin and Krystal Hu / Reuters)
Related: Korea JoongAng Daily, Axios, The Chosun Daily, Maeil Business Newspaper, Yonhap News Agency, The Korea Herald, Tech in Asia
The Trump administration pushed out two officials focused on neutralizing technological threats from China, people familiar with the matter said, in the latest dismissals of key personnel working on national-security issues tied to Beijing.
The departures, from an office within the Commerce Department’s Bureau of Industry and Security, alarmed some US officials and security hawks already concerned with what they described as the Trump administration’s softening stance toward China as trade talks between the two sides continue.
The latest losses were within the bureau’s Office of Information and Communications Technology and Services. Set up by the first Trump administration, it has been described by many Republicans and Democrats as showing promise in limiting China’s technological and economic advances that could harm US national security. The OICTS is broadly charged with securing US technology supply chains and communications infrastructure, and protecting Americans’ data from adversaries.
Liz Cannon, the executive director of the OICTS, submitted her resignation, the culmination of a pressure campaign by senior officials to get her to leave, people familiar with the matter said. Her announced departure follows the exit of one of her deputies, who was put on administrative leave last week, the people said.
Cannon was appointed under the Biden administration, which implemented a range of punitive actions on China and technology issues, including tough export controls on American semiconductors and restrictions on Chinese companies doing business in the US.
Both OICTS officials were integral in establishing a rule last year that widely restricts the import and sale of internet-connected passenger vehicles and related hardware and software with links to China or Russia. The rule was enacted after the office had established that the potential to share data from the cars posed a national security risk. (Heather Somerville and Amrith Ramkumar / Wall Street Journal)
Spain's High Court closed its investigation into the use of Israeli cyber-intelligence firm NSO Group's "Pegasus" software to spy on Spanish politicians, citing a lack of cooperation from Israeli authorities.
The investigation was launched after the Spanish government disclosed in 2022 that NSO's spyware had been used to spy on members of the Spanish cabinet, sparking a political crisis that led to the resignation of the country's spy chief.
Officials did not clarify whether domestic or foreign entities were linked to the espionage, whose targets included Prime Minister Pedro Sanchez and several ministers.
Investigating judge Jose Luis Calama said he was unable to advance the probe into the alleged spying on politicians because a lack of response to requests for information from Israel meant there was no identifiable suspect.
NSO has always denied wrongdoing, saying the software, which it licenses to governments after Israeli government approval, is intended to fight crime and protect national security and that it cannot monitor how it is used. Israel says its role is limited to export licences rather than day-to-day operations. (Emma Pinedo / Reuters)
Related: The Guardian, The Record, El País
Paid subscribers receive full access to Metacurity’s archives and selected analytical deep dives
Don't miss out on the full range of what Metacurity has to offer. Upgrade to a paid subscription, gain access to our archives and special content, and stay current while helping to keep independent media alive.
If you can't afford a paid subscription, donate what you can to keep this vital resource going.
The Irish government is planning to bolster its police's ability to intercept communications, including encrypted messages, and provide a legal basis for spyware use.
The Communications (Interception and Lawful Access) Bill is being framed as a replacement for the current legislation that governs digital communication interception.
The Department of Justice, Home Affairs, and Migration said in an announcement this week that the existing Postal Packets and Telecommunications Messages (Regulation) Act 1993 "predates the telecoms revolution of the last 20 years."
As well as updating laws passed more than two decades ago, the government was keen to emphasize that a key ambition for the Bill is to empower law enforcement to intercept all forms of communications.
The Bill will bring communications from IoT devices, email services, and electronic messaging platforms into scope, "whether encrypted or not."
In a similar way to how certain other governments want to compel encrypted messaging services to unscramble packets of interest, Ireland's announcement also failed to explain precisely how it plans to do this.
However, it promised to implement a robust legal framework, alongside all necessary privacy and security safeguards, if these proposals do ultimately become law. It also vowed to establish structures to ensure "the maximum possible degree of technical cooperation between state agencies and communication service providers." (Connor Jones / The Register)
Related: Gov.ie, The Record, TechCrunch, SC Media, Boing Boing, WebProNews, Cyber Insider, Extra
Researchers at Citizen Lab accused Israeli digital forensics company Cellebrite of enabling human rights violations after authorities in Jordan allegedly used its technology to break into the mobile phones of activists.
Citizen Lab said equipment manufactured by Cellebrite had been used in at least seven cases to extract data from mobile phones seized from several people between late 2023 and mid 2025.
Those people, including several activists and a journalist, were detained for involvement in protests or criticism of authorities and didn’t consent to the searches of their devices, researchers said.
Victor Cooper, a Cellebrite spokesman, said in an emailed statement that the company vets customers against internal human rights parameters and has previously ceased doing business in jurisdictions where risks were deemed “incompatible with our corporate values.” (Ryan Gallagher / Bloomberg)
Related: Citizen Lab, The Times of Israel, The Guardian, Cyberscoop, The Record, OCCRP

Greek police have taken down a mobile scam operation that used a fake cell tower hidden inside a car to send phishing messages to unsuspecting phone users across the Athens metropolitan area, authorities said last week.
According to a statement from the Hellenic Police, the suspects are accused of forging identity documents, carrying out fraud, and illegally accessing information systems as part of an organized criminal group.
Officers stopped the suspects for a check in the Spata area east of Athens following reports of suspicious behavior. During the inspection, the suspects allegedly presented forged identity documents. A subsequent search of their vehicle uncovered a mobile computing system hidden in the trunk and connected to a roof-mounted transmitter disguised as a shark-fin antenna.
Authorities said the setup functioned as a rogue mobile base station — often called an SMS blaster — allowing it to mimic legitimate telecom infrastructure and send mass scam messages. The device forced nearby mobile phones to connect to the suspects’ system and downgraded them from 4G to the less-secure 2G network, exploiting long-known vulnerabilities.
Once connected, the attackers were able to harvest identifying data such as phone numbers and then send scam text messages posing as banks or courier companies. The messages contained phishing links that lured victims into entering payment card details and other sensitive information, which were later used to carry out unauthorized transactions, police said.
So far, investigators have linked the group to at least three fraud cases in Maroussi, Spata, and Athens, but authorities said the investigation is ongoing and the full scope of the operation remains unclear. The suspects have been brought before a public prosecutor.
Police have not disclosed the suspects’ identities, but local media reported that they are Chinese nationals. (Daryna Antoniuk / The Record)
Related: Hellenic Police, Data Center Dynamics, Greek City Times, ProtoThema
Vietnam regulators fined ByteDance Ltd.’s TikTok 880 million dong ($33,516) for misleading consumers about their relationship with businesses and violating consumer protection and data consent rules.
The Vietnam Competition Commission said TikTok has no mechanism that allows consumers to opt out of having their information used for commercial activities, such as advertising, according to a statement on the Vietnam Competition Commission’s website. The social media app also failed to provide processes to certain types of users, allowing them to file complaints or resolve disputes, it said.
TikTok Vietnam, in a statement, said the company has “begun implementing adjustments” in line with the authority’s recommendations. “TikTok is committed to fostering a transparent business and shopping environment, in compliance with local laws and with consumer interests at the core.”
The regulator also slapped an 810 million dong fine on tech firm VNG Group, the operator of Vietnam’s popular messaging app Zalo.
The commission said VNG did not provide consumers the ability to refuse the use of their information by businesses or determine how much could be used. In late December, the commission asked VNG to provide information related to Zalo’s policies in collecting and using users’ data after complaints from its users, according to a posting on the government’s website. (Linh Vu Nguyen and Nguyen Xuan Quynh / Bloomberg)
Related: Tuoi Tre News, The Business Times, Cryptopolitan, Coincentral, Tech in Asia, Viet Nam News, The Investor, VN Express, Money and Banking
Kazakhstan's data breach law reforms are moving ahead, with plans to criminalise mass personal data leaks and lift the maximum fine to about AUD $42,500 or around USD $29,150.
For Australian investors and companies active in Central Asia, this signals stricter oversight, closer to EU-style enforcement. Banks, fintechs, and large data handlers face higher compliance costs and legal exposure. (Danny Kontos / Meyka)
Related: The Times of Central Asia
Ilya Lichtenstein, who was at the center of a massive 2016 crypto heist worth billions at the time, wrote online that he is now out of prison and has changed his ways.
“Ten years ago, I decided that I would hack the largest cryptocurrency exchange in the world,” Lichtenstein wrote on LinkedIn, detailing a time when his startup was barely making money and he decided to steal some instead.
“This was a terrible idea. It was the worst thing I had ever done,” he added. “It upended my life, the lives of people close to me, and affected thousands of users of the exchange. I know I disappointed a lot of people who believed in me and grossly misused my talents.”
In 2023, Lichtenstein and his wife, Heather Morgan, pleaded guilty to money laundering conspiracy in a wild 2016 scheme to steal 120,000 bitcoins (worth over $10 billion today) from Bitfinex, a cryptocurrency exchange. The pair was arrested at their Manhattan home in 2022.
Lichtenstein quickly flipped, helping the government recover the assets he had stolen and then helping the feds “on a variety of crypto cases.” He says that he enjoyed working with the government.
“When I was a black hat hacker, I was isolated and paranoid,” he wrote. “Working with the good guys, being part of a team solving a bigger problem felt surprisingly good. I realized that I could use my technical skills to make a difference.” (Cyrus Farivar / Ars Technica)
Related: LinkedIn
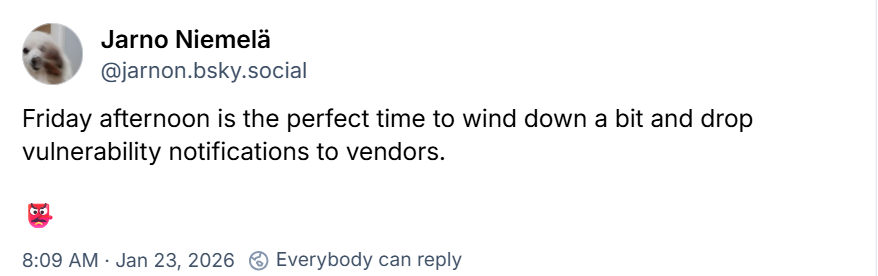
Researchers at Okta are warning about custom phishing kits explicitly built for voice-based social engineering (vishing) attacks, which are being used in active attacks to steal Okta SSO credentials for data theft.
They explain that the phishing kits are sold as part of an "as a service" model and are actively being used by multiple hacking groups to target identity providers, including Google, Microsoft, and Okta, and cryptocurrency platforms.
Unlike typical static phishing pages, these adversary-in-the-middle platforms are designed for live interaction via voice calls, allowing attackers to change content and display dialogs in real time as a call progresses.
The core features of these phishing kits are real-time manipulation of targets through scripts that give the caller direct control over the victim's authentication process.
As the victim enters credentials into the phishing page, those credentials are forwarded to the attacker, who then attempts to log in to the service while still on the call.
Okta recommends that customers use phishing-resistant MFA such as Okta FastPass, FIDO2 security keys, or passkeys.
This advisory comes after BleepingComputer learned that Okta privately warned its customers' CISOs earlier this week about the ongoing social engineering attacks.
BleepingComputer contacted Okta after learning that threat actors were calling targeted companies' employees to steal their Okta SSO credentials. (Lawrence Abrams / Bleeping Computer)
Related: Okta, The Register, Help Net Security, The Cyber Express
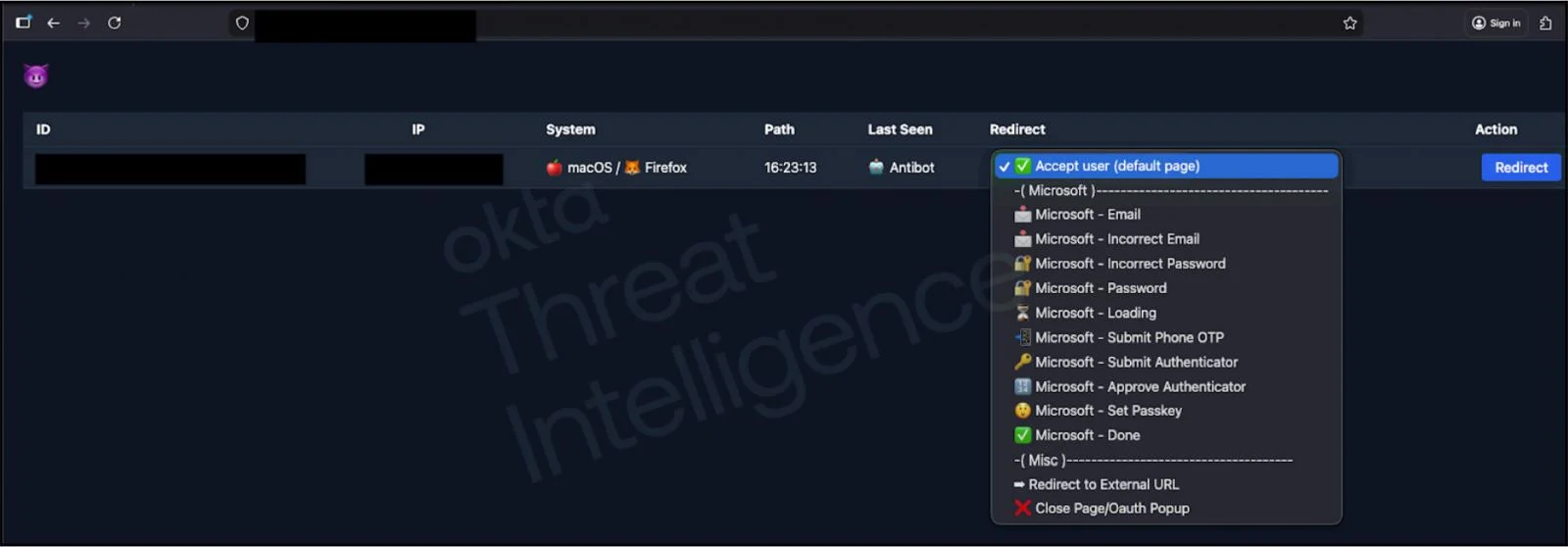
Researchers at Greynoise say that a recently disclosed critical vulnerability in the GNU InetUtils telnet daemon (telnetd) is "trivial" to exploit.
The bug, which had gone unnoticed for nearly 11 years, was disclosed on January 20 and is tracked as CVE-2026-24061 (9.8).
It was introduced in a May 2015 update, and if you're one of the few to be still running telnetd, patch up, because attacks are already underway.
GreyNoise data shows that in the past 24 hours, 15 unique IPs were trying to execute a remote authentication bypass attack by using the vulnerability.
The bug allows attackers to gain root access to a target system easily.
"The telnetd server invokes /usr/bin/login (normally running as root) passing the value of the USER environment variable received from the client as the last parameter," wrote GNU contributor Simon Josefsson.
"If the client supply [sic] a carefully crafted USER environment value being the string '-f root', and passes the telnet(1) -a or --login parameter to send this USER environment to the server, the client will be automatically logged in as root bypassing normal authentication processes."
The researchers say users should at the very least update to the latest version of telnetd and close it off from the web, but better still, upgrade to a more secure alternative, such as SSH. (Connor Jones / The Register)
Related: Greynoise, Seclists, CSO Online
Researchers at digital forensics and incident response company Cyber Centaurs found that an operational security failure allowed researchers to recover data that the INC ransomware gang stole from a dozen US organizations.
A deep forensic examination of the artifacts left behind uncovered tooling that had not been used in the investigated attack, but exposed attacker infrastructure that stored data exfiltrated from multiple victims.
The Cyber Centaurs investigation began after a client U.S. organization detected ransomware encryption activity on a production SQL Server.
The payload, a RainINC ransomware variant, was executed from the PerfLogs directory, which is typically created by Windows. However, ransomware actors have begun to use it more frequently for staging.
The researchers also noticed the presence of artifacts from the legitimate backup tool Restic, although data exfiltration had occurred during the lateral movement stage and the threat actor had not used the utility in this attack.
This caused a shift in the researchers' investigation "from incident response to infrastructure analysis."
The traces that INC ransomware left behind included renamed binaries (like ‘winupdate.exe’), PowerShell scripts to execute Restic, hardcoded repository configuration variables, and backup commands. (Bill Toulas / Bleeping Computer)
Related: Cyber Centaurs, CSO Online, Tech Nadu
Researchers at mobile security company Dr.Web discovered a new family of Android click-fraud trojans that leverages TensorFlow machine learning models to detect and interact with specific advertisement elements automatically.
The mechanism relies on visual analysis based on machine learning instead of predefined JavaScript click routines, and does not involve script-based DOM-level interaction like classic click-fraud trojans.
The threat actor is using TensorFlow.js, an open-source library developed by Google for training and deploying machine learning models in JavaScript. It permits running AI models in browsers or on servers using Node.js.
The new family of Android trojans is distributed through GetApps, the official app store for Xiaomi devices. (Bill Toulas / Bleeping Computer)
Related: Android Authority, Dr. Web, Security Affairs, SC Media, Cyber Security News, GBHackers
Researchers at cybersecurity company watchTowr report that hackers began exploiting an authentication bypass vulnerability in SmarterTools' SmarterMail email server and collaboration tool that allows resetting admin passwords.
Hackers began exploiting an authentication bypass vulnerability in SmarterTools' SmarterMail email server and collaboration tool that allows resetting admin passwords.
watchTowr reported the issue on January 8, and SmarterMail released a fix on January 15 without an identifier being assigned.
After the issue was addressed, the researchers found evidence that threat actors started to exploit it just two days later. This suggests that hackers reverse-engineered the patch and found a way to leverage the flaw. (Bill Toulas / Bleeping Computer)
Related: WatchTwr, Cyber Daily, Cyber Press
The State Art Collections Dresden (Staatliche Kunstsammlungen Dresden – SKD), Germany, became the target of a deliberate cyberattack
Large parts of the digital infrastructure have been affected. However, the security network remains unaffected and fully operational. Structural and technical safety is also fully guaranteed. The museums remain open to visitors.
At present, accessibility to the SKD via telephone and digital channels is severely limited. The online shop and visitor services are currently unavailable. It is not yet possible to predict when all affected systems will be restored.
The museum association is in close coordination with the Dresden Police Department and the Saxon State Office of Criminal Investigation. The Prosecutor General’s Office in Dresden is considering taking over the investigation. (Art Dependence Magazine)
Related: Die Sachsen, Kunst Mag
Best Thing of the Day: White Supremacists Still Can't Date
Twenty-five days after a hacktivist dressed as Pink Ranger from the Power Rangers wiped three white supremacist websites, including the WhiteDate dating site, on stage at the end of a talk at a hacker conference, WhiteDate is still down.
Bonus Best Thing of the Day: Along With All That ICE Funding, At Least Cyber Gets Funded
The US House of Representatives approved a three-bill minibus appropriations package that approves funding for the US Cybersecurity and Infrastructure Agency for 2026, including efforts to provide legal liability protections for sharing cyber threat information as well as state and local government cyber grants.
Worst Thing of the Day: Destroying the FBI
Forty-five current and former FBI employees say the changes the agency has made under Donald Trump have left America less safe.
Closing Thought