China-aligned hackers hijack servers to game Google rankings
Salt Typhoon may have stolen data from nearly every American, N. Korea has crypto workers under siege, House panel approves measure to renew cornerstone cyber law, Stealerium malware takes screenshots of users watching porn, M&S hackers claim Jaguar attack, much more
Please consider supporting Metacurity
Metacurity has been a labor of love for years, and I’m so grateful for your readership. Your support can help ensure I can continue delivering the carefully curated weekly long-reads and daily digests of the most critical developments in cybersecurity.
If you find value in what Metacurity offers, please consider upgrading to a paid subscription. We also provide corporate subscription options, and soon we’ll be introducing affordable sponsorship opportunities—perfect for promoting your events or products to a highly engaged audience.
To learn more, feel free to reach out at cynthia@metacurity.com.
Thank you so much for being part of the Metacurity community.
If you can't commit to a subscription, please consider donating what you can afford to help keep Metacurity free to all.
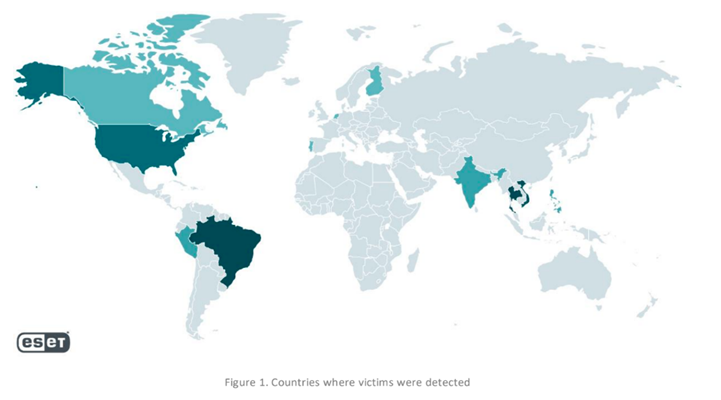
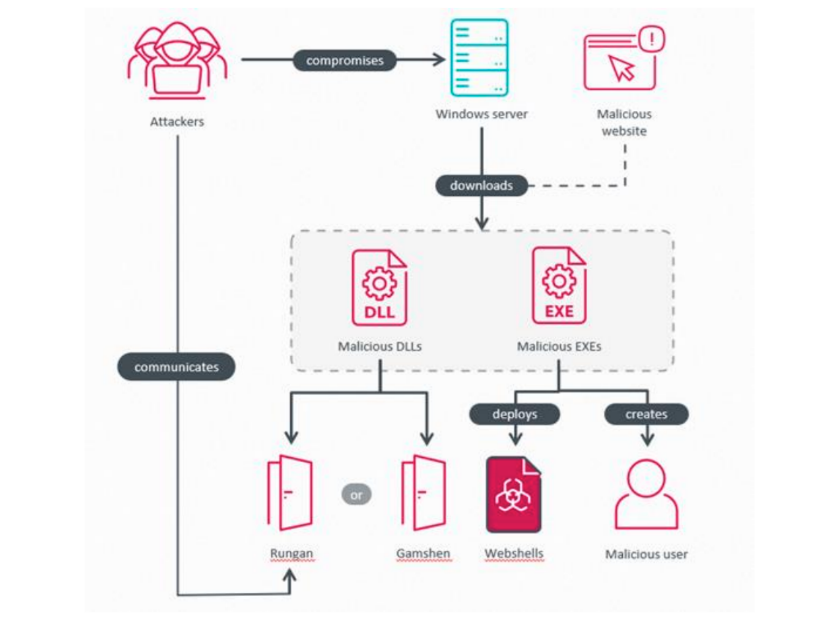
Researchers at ESET identified a new China-aligned threat actor they call GhostRedirector that is targeting Windows servers mainly in Brazil, Thailand, and Vietnam with a passive C++ backdoor and a malicious Internet Information Services (IIS) that manipulates Google search results in an SEO manipulation scheme.
GhostRedirector uses two previously undocumented, custom tools: a passive C++ backdoor that ESET calls Rungan, and an IIS module that it calls Gamshen.
While Rungan has the capability of executing commands on a compromised server, Gamshen appears to provide SEO fraud as-a-service to manipulate search engine results by modifying responses to Googlebots visiting the sites to boost the page ranking of targeted sites, which ESET discovered were 65 gaming sites.
GhostRedirector also uses a series of other custom tools, as well as the publicly known exploits EfsPotato and BadPotato, to create a privileged user on the server that can be used to download and execute other malicious components with higher privileges, or used as a fallback in case the Rungan backdoor or other malicious tools are removed from the compromised server.
“The malware delivers different information to the Googlebot than it should be,” Tony Anscombe, Chief Security Evangelist at ESET, told Metacurity. “It controls what that server is then sending back to the Googlebot. It promotes certain other sites. In effect, it hijacks that server's reputation with the Googlebot and then feeds it inaccurate information that elevates your content or the content that's on another server.”
One interesting angle on GhostRedirector is that some of the infected servers targeting Brazil, Thailand, and Vietnam were in the US. The organizations in those targeted countries essentially rented server space in the US. “If you look at those servers, they're primarily hosting for those other victim countries,” Anscombe said.