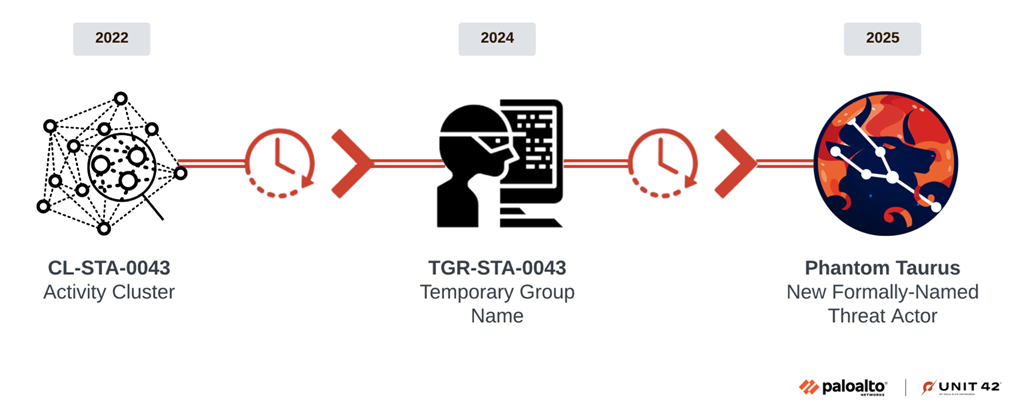
Chinese hackers breached diplomats' email servers in a years-long campaign
China sentences 11 people to death for gambling and Myanmar scam operations, DOJ settles with Georgia Tech over fake cyber assessment score, Google launches new ransomware protection, Microsoft launches a security store, BNB Chain X account hacked, Imgur blocked in UK, much more