CISA warns US infrastructure owners following Russian attack on Poland's power grid
Russia throttles Telegram accusing it of failing to protect personal data or combat crime, N. Korean hackers targeted crypto company with unique malware and multiple scams, Israel claims it foiled hundreds of Iranian cyberattacks, Microsoft issued fixes for six zero day flaws, much more


The total number of new vulnerabilities discovered could top 100,000 in 2026, according to the latest forecast by FIRST. But that doesn't necessarily mean more cyberattacks. Check out my latest CSO piece on how CISOs might have to up their efforts to separate signal from noise as CVE volume soars.
Metacurity has been following cybersecurity, surveillance, and power as they unfold day by day—tracking patterns, context, and connections that most other sources miss. We go beyond the usual infosec news echo chamber, highlighting what’s real, overlooked, and often missed by traditional outlets. Please consider supporting our work by upgrading your subscription. Thank you!
Following a Jan. 30 report from Poland’s Computer Emergency Response Team that concluded a December attack on the country's power grid overlapped significantly with infrastructure used by a Russian government-linked hacking group, the US Cybersecurity and Infrastructure Security Agency published a warning for US critical infrastructure owners and operators.
CISA said its warning was meant to “amplify” that Polish report. In particular, CISA said the attack highlighted the threats to operational technology and industrial control systems, most commonly used in the energy and manufacturing sectors.
And CISA’s alert continues a recent agency focus on securing edge devices like routers or firewalls, after a binding operational directive last week to federal agencies to strip unsupported products from their systems.
“The malicious cyber activity highlights the need for critical infrastructure entities with vulnerable edge devices to act now to strengthen their cybersecurity posture against cyber threat activities targeting OT and ICS,” the alert reads.
“A malicious cyber actor(s) gained initial access in this incident through vulnerable internet-facing edge devices, subsequently deploying wiper malware and causing damage to remote terminal units (RTUs),” it states. “The malicious cyber activity caused loss of view and control between facilities and distribution system operators, destroyed data on human machine interfaces (HMIs), and corrupted system firmware on OT devices. While the affected renewable energy systems continued production, the system operator could not control or monitor them by their intended design.”
CISA urged owners and operators to review the Polish report, as well as security guidance from other US agencies. (Tim Starks / CyberScoop)
Related: CISA, Cybersecurity Dive
Russia tightened its step-by-step throttling of the ubiquitous communication app Telegram, escalating a crackdown on what remains of the free Russian internet amid President Vladimir V. Putin’s war against Ukraine.
New disruptions to the app’s service in multiple regions of the country rattled many of the more than 100 million Russians who turn to Telegram each month as a source of news, commentary, and entertainment, and as a tool to make calls and send messages.
The Russian communications regulator, Roskomnadzor, said in a statement on Tuesday that it would continue to impose successive restrictions on Telegram until the app ceased violating Russian law. The agency has accused Telegram of failing to protect personal data, combat fraud, and prevent its use by terrorists and criminals, according to the statement, which was released to the state news agency Tass.
The regulator’s actions come after Russia barred and impeded various messaging and social media platforms, and as it pushes its own state-controlled messaging app, MAX, as a safe alternative to competitors like Telegram and WhatsApp. The moves are broadly seen as an attempt to extend Kremlin control over what Russians are able to see, do, and say online. Many analysts compared MAX to China’s WeChat, a state-controlled “super app” that dominates the Chinese internet.
Telegram’s founder, Pavel Durov, said in a statement posted Tuesday on Telegram, “Russia is restricting access to Telegram in an attempt to force its citizens to switch to a state-controlled app built for surveillance and political censorship.” (Paul Sonne and Oleg Matsnev / New York Times)
Related: Reuters, Euronews, The Japan Times, France24, StratNews, TVP World, TRT World
According to researchers at Google-owned Mandiant, North Korean hackers in a group dubbed UNC1069 targeted an official at a cryptocurrency company with several unique pieces of malware deployed alongside multiple scams, including a fake Zoom meeting, according to a new report from incident responders.
The hackers initially contacted the victim through Telegram using the compromised account of another cryptocurrency executive. The victim was sent a Calendly link for a 30-minute meeting that contained a Zoom meeting link.
“The victim reported that during the call, they were presented with a video of a CEO from another cryptocurrency company that appeared to be a deepfake,” Mandiant explained.
“While Mandiant was unable to recover forensic evidence to independently verify the use of AI models in this specific instance, the reported ruse is similar to a previously publicly reported incident with similar characteristics, where deepfakes were also allegedly used.”
When the victim was in the meeting, the hackers claimed there were audio issues — prompting them to ask the victim to take several actions on their device to resolve them, allegedly. The issues were a ruse to cover for a ClickFix attack — a technique where hackers install malware on a device by having the victim try to resolve fictitious technical issues.
In this case, the victim was directed to a web page with troubleshooting directions for both macOS systems and Windows systems. Embedded in the string of commands was one line that kicked off the infection chain.
The victim followed the troubleshooting commands, and their macOS device was infected. (Jonathan Greig / The Record)
Related: Google Cloud, Cyber Security News, GBHackers, CyberPress, BeInCrypto
Israel's Shin Bet security agency and National Cyber Directorate issued a joint statement saying they detected and foiled hundreds of Iranian cyberattacks targeting Israelis — including senior government and defense officials, academics, and journalists.
There has been a noted rise in attempts by Iranian intelligence agents to hack the private Google accounts of Israelis since June 2025’s 12-day war with Iran.
“The purpose of these attempts is to collect personal and professional information that could be used to advance terrorist activity, espionage, and influence operations in the form of ‘targeted phishing,'” the Shin Bet and Cyber Directorate say.
They say the method includes “personalized approaches tailored to the target’s fields of interest, impersonating a familiar figure and inviting them to a meeting or to download files via a link, as well as ‘phishing impersonation’ messages aimed at obtaining the target’s login details, with emphasis on the password and even the additional verification code for the Google, Telegram or WhatsApp account, thus granting the attacker full access to these accounts.” (Emanuel Fabian / The Times of Israel)
Microsoft issued its February Patch Tuesday updates to fix more than 50 security holes in its Windows operating systems and other software, including patches for a whopping six “zero-day” vulnerabilities that attackers are already exploiting in the wild.
Zero-day #1 this month is CVE-2026-21510, a security feature bypass vulnerability in Windows Shell wherein a single click on a malicious link can quietly bypass Windows protections and run attacker-controlled content without warning or consent dialogs. CVE-2026-21510 affects all currently supported versions of Windows.
The zero-day flaw CVE-2026-21513 is a security bypass bug targeting MSHTML, the proprietary engine of the default Web browser in Windows. CVE-2026-21514 is a related security feature bypass in Microsoft Word.
The zero-day CVE-2026-21533 allows local attackers to elevate their user privileges to “SYSTEM” level access in Windows Remote Desktop Services. CVE-2026-21519 is a zero-day elevation of privilege flaw in the Desktop Window Manager (DWM), a key component of Windows that organizes windows on a user’s screen. Microsoft fixed a different zero-day in DWM just last month.
The sixth zero-day is CVE-2026-21525, a potentially disruptive denial-of-service vulnerability in the Windows Remote Access Connection Manager, the service responsible for maintaining VPN connections to corporate networks. (Brian Krebs / Krebs on Security)
Related: Bleeping Computer, Tenable Blog, Qualys Blog, Cyber Security News, SANS Internet Storm Center, The Stack, iTnews - Security, PCMag.com, reddit TECH NEWS, Bleeping Computer, AskWoody, Rapid7, Infosecurity Magazine, Security Week, Techzine, Neowin, CyberScoop, Zero Day Initiative, CSO Online, CRN, The Register - Security, CyberInsider
Microsoft has begun rolling out updated Secure Boot certificates through monthly Windows updates to replace the original 2011 certificates that will expire in late June 2026.
Introduced in 2011, Secure Boot ensures that only trusted bootloaders can load on computers with UEFI firmware, helping block malicious software, such as rootkits, from executing during system startup by verifying its digital signature against a set of trusted digital certificates stored in the firmware.
Microsoft first revealed plans to refresh expiring Secure Boot certificates on eligible Windows 11 24H2 and 25H2 systems in January, following a November alert warning IT admins to update the security certificates used to validate UEFI firmware before they expire.
"After more than 15 years of continuous service, the original Secure Boot certificates are reaching the end of their planned lifecycle and begin expiring in late June 2026," said Windows Servicing and Delivery partner director Nuno Costa.
The new Secure Boot certificates will be installed automatically via regular monthly updates for customers who allow Microsoft to manage Windows updates on their systems. Additionally, many PCs manufactured since 2024, and the vast majority shipped last year, already include updated certificates. (Sergiu Gatlan / Bleeping Computer)
Related: The Verge, Windows Blog, PCWorld, iTnews, Thurrott, Ars Technica, Cybersecurity Dive, Notebookcheck, PCMag, ZDNET, XDA Developers, Windows Central, Engadget, Neowin
At Sunday’s Super Bowl, Ring advertised “Search Party,” a cute, horrifyingly dystopian feature that is nominally designed to turn all of the Ring cameras in a neighborhood into a dragnet that uses AI to look for a lost dog.
It does not take an imagination of any sort to envision this being tweaked to work against suspected criminals, undocumented immigrants, or others deemed ‘suspicious’ by people in the neighborhood. Many of these use cases are how Ring has been used by people on its dystopian “Neighbors” app for years.
Chris Gilliard, a privacy expert and author of the upcoming book Luxury Surveillance, told 404 Media these features and their Super Bowl ad are “a clumsy attempt by Ring to put a cuddly face on a rather dystopian reality: widespread networked surveillance by a company that has cozy relationships with law enforcement and other equally invasive surveillance companies.”
With Ring’s recent partnership with Flock, which will further facilitate the sharing of video footage with police, and its new Search Party feature, the message is clear: Ring is still, again, and always will be in the business of leveraging its network of luxury surveillance consumers as a law enforcement tool. (Jason Koebler / 404 Media,)
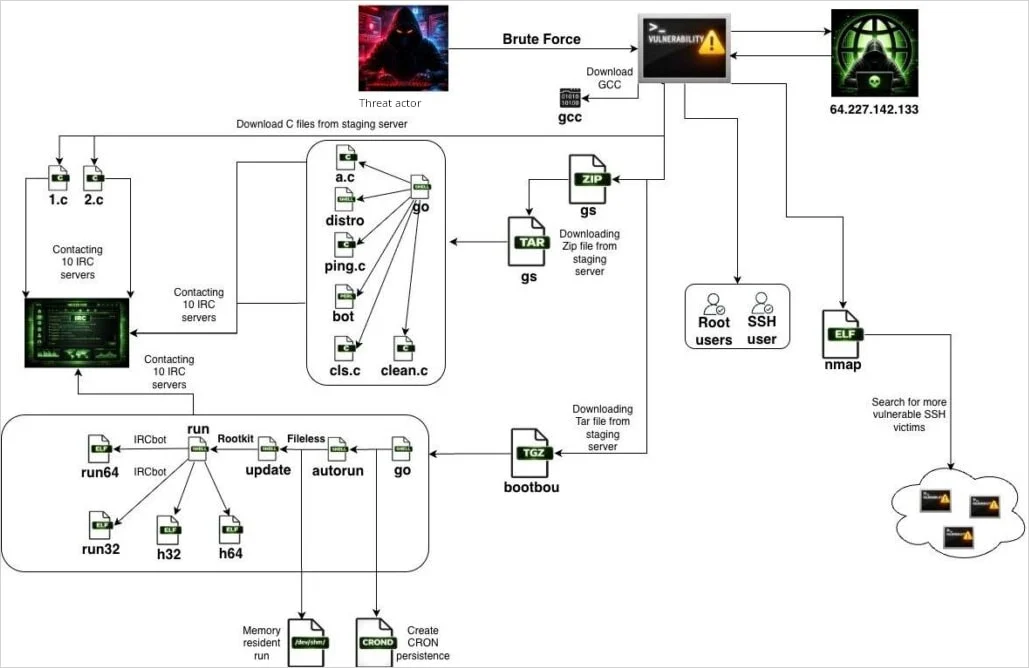
Researchers at Flare report that a newly documented Linux botnet named SSHStalker is using the IRC (Internet Relay Chat) communication protocol for command-and-control (C2) operations.
The protocol was invented in 1988, and its adoption peaked during the 1990s, becoming the main text-based instant messaging solution for group and private communication.
Technical communities still appreciate it for its implementation simplicity, interoperability, low bandwidth requirements, and no need for a GUI.
The SSHStalker botnet relies on classic IRC mechanics such as multiple C-based bots and multi-server/channel redundancy instead of modern C2 frameworks, prioritizing resilience, scale, and low cost over stealth and technical novelty.
According to Flare, this approach extends to other characteristics of SSHStalker’s operation, like using noisy SSH scans, one-minute cron jobs, and a large backlog of 15-year-old CVEs.
The botnet also contains exploits for 16 CVEs targeting Linux kernel versions from the 2009-2010 era. This is used to escalate privileges after the earlier brute-forcing step grants access to a low-privileged user.
Distributed denial-of-service (DDoS) capabilities are also present, though the researchers noted they have not yet observed any such attacks. In fact, SSHStalker’s bots currently connect to the C2 and then enter an idle state, suggesting testing or access hoarding for now.
Flare has not attributed SSHStalker to a particular threat group, though it noted similarities with the Outlaw/Maxlas botnet ecosystem and various Romanian indicators. (Bill Toulas / Bleeping Computer)
Related: Flare, Security Affairs, GBHackers, Security Week, SC Media
US Immigration and Customs Enforcement’s top official rejected claims from lawmakers Tuesday that the Department of Homeland Security component is building a database for protesters.
The alleged detractor database has been referenced in several reports by think tanks, letters to DHS officials from lawmakers, and in interviews with border czar Tom Homan. During Tuesday’s House Homeland Security Committee hearing, Rep. Lou Correa, D-Calif., cited a well-circulated clip of an ICE agent in Portland, Maine, telling a person videotaping that she would be added to a “nice little database.”
“I can’t speak for that individual,” said Todd Lyons, who serves as acting director of ICE. “But I can assure you that there is no database that’s tracking United States citizens.”
Despite Lyons’ pushback on the database claims, skepticism is persistent as stakeholders point to reports to the contrary.
“He either 1) perjured himself or 2) has no idea what’s going on in his own agency, because all those facial recognition shots they’re taking of people on the streets of this country are going somewhere besides the agents’ smartphone,” Patrick Eddington, senior fellow in homeland security and civil liberties at the Cato Institute, said in a post on BlueSky.
FedScoop reached out to DHS for clarification. Tricia McLaughlin, the agency’s assistant security for public affairs, reaffirmed that there is no database of domestic terrorists run by DHS.
“We do, of course, monitor and investigate and refer all threats, assaults, and obstruction of our officers to the appropriate law enforcement,” McLaughlin said in an email. “Obstructing and assaulting law enforcement is a felony and a federal crime.” (Lindsay Wilkinson / FedScoop)
Karim Toubba, the Chief Executive Officer of LastPass, said that the significant security incident that has dogged the firm's footsteps since 2022 became "a forcing function to drive a lot of changes."
In August of 2022, an "unauthorized party" gained access to portions of the LastPass development environment via a compromised developer account and stole some of LastPass's source code and technical data.
It didn't end there. Information stolen during this attack led to further compromise, including the theft of basic customer account information and related metadata – such as names, billing addresses, email addresses, telephone numbers, and IP addresses. Furthermore, a backup copy of the customer vault data was accessed. Although encrypted, it was still accessed by an intruder who managed to steal a master password from a senior engineer's home computer.
"We significantly changed the technology stack of all of our employees, [such as] the security capabilities that are on their devices, and then issued new devices to all employees in the form of laptops that were completely locked down," Toubba commented. "I'm a Mac user, and as an example, I can't even go to the App Store with my Mac -- I can only use corporate-sanctioned applications, which are focused and validated."
Hardware authentication measures were rolled out across the board, such as YubiKey dongles. LastPass also overhauled its employee training program, formed a dedicated security team, and engaged third parties for ongoing security audits, including penetration testing. (Charlie Osborne / ZDNet)
AI cybersecurity startup Vega Security announced it had raised $120 million in a Series B venture funding round.
Accel led the round with participation from Cyberstarts, Redpoint, and CRV. (Rebecca Bellan / TechCrunch)
Related: Access Newswire, CTech, Silicon Angle, PYMNTS
Best Thing of the Day: He Never Banked on Investigative Journalists
to resolve them, allegedly, who swindled a Romanian woman of $2 million right to his doorstep at a newly purchased mansion in Abuja, Nigeria.
Worst Thing of the Day: Look at What Google Gave to ICE About a Student Journalist
Google fulfilled an Immigration and Customs Enforcement subpoena that demanded a wide array of personal data on a student activist and journalist, including usernames, addresses, an itemized list of services, including any IP masking services, telephone or instrument numbers, subscriber numbers or identities, and credit card and bank account numbers.
Closing Thought