Claude Opus 4.6 found 500+ severe flaws in open source repos without much prompting
Asian cyberespionage group broke into sensitive systems in 37+ countries, ICE's Mobile Fortify does not reliably ID people, CISA tells agencies to stop using edge devices past EOS, 764 member busted and charged with receiving CSAM, French cops bust four with spying on Starlink for China, much more
If you value Metacurity, please show your support by upgrading your subscription. Thank you.
With the debut of Claude Opus 4.6, Anthropic released research showing that its latest AI model has found more than 500 previously unknown high-severity security flaws in open-source libraries with little to no prompting.
Anthropic's frontier red team tested Opus 4.6 in a sandboxed environment to see how well it could find bugs in open-source code.
The team gave the Claude model everything it needed to do the job — access to Python and vulnerability analysis tools, including classic debuggers and fuzzers — but no specific instructions or specialized knowledge.
Claude found more than 500 previously unknown zero-day vulnerabilities in open-source code using just its "out-of-the-box" capabilities, and each one was validated by either a member of Anthropic's team or an outside security researcher.
Claude uncovered a flaw in GhostScript, a popular utility that helps process PDF and PostScript files, that could cause it to crash. Claude also found buffer overflow flaws in OpenSC, a utility that processes smart card data, and CGIF, a tool that processes GIF files.
Anthropic believes Opus 4.6's capabilities will be a massive win for the security world, which has long struggled with how to secure open-source code that underpins everything from enterprise software to critical infrastructure. (Sam Sabin / Axios)
Related: Anthropic, Anthropic, The Verge, Bloomberg, Benzinga, Gadgets 360, The Mac Observer, Sky News, Winbuzzer, IT Pro, VentureBeat, TechCrunch
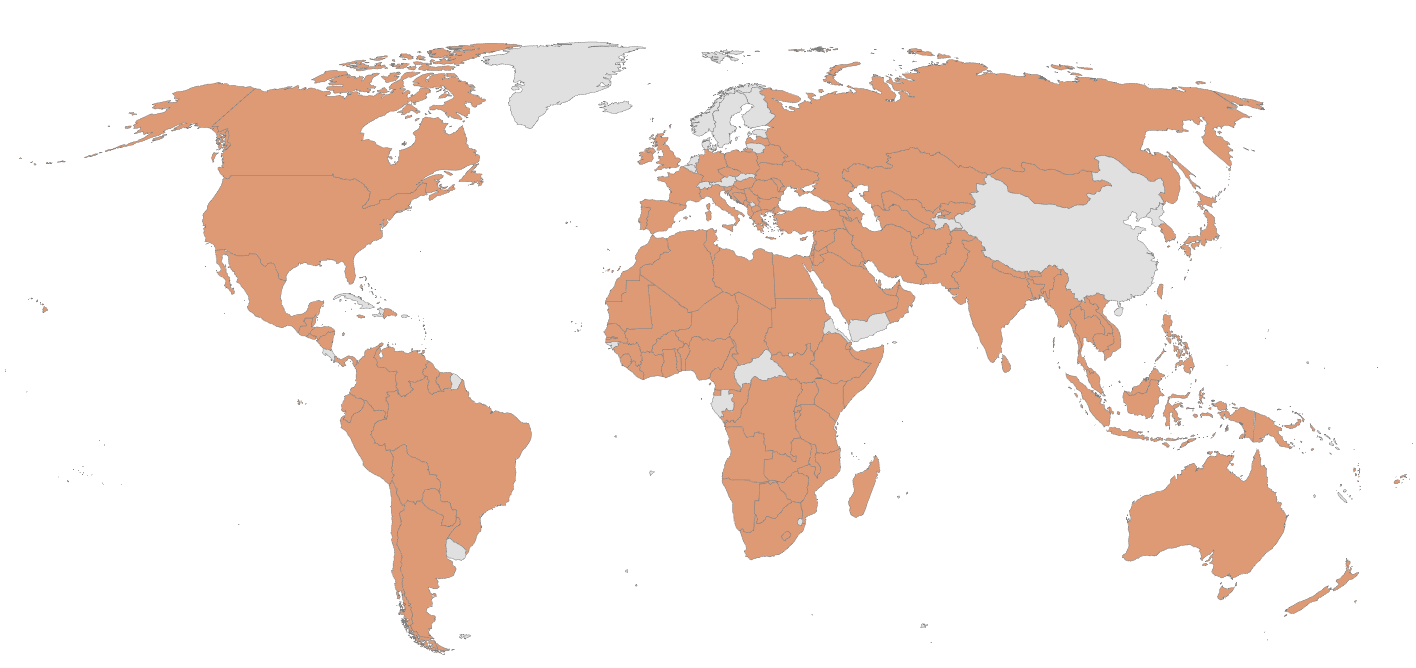
Researchers at Palo Alto Networks Unit 42 say that an Asian cyberespionage group they track as TGR-STA-1030 has spent the past year in activity they call the Shadow Campaigns, breaking into computer systems belonging to governments and critical infrastructure organizations in more than 37 countries.
The state-aligned attackers have infiltrated networks of 70 organizations, including five national law enforcement and border control agencies, according to a new research report from the company. They have also breached three ministries of finance, one country’s parliament, and a senior elected official in another, the report states.
The spying operation was unusually vast and allowed the hackers to hoover up sensitive information in apparent coordination with geopolitical events, such as diplomatic missions, trade negotiations, political unrest, and military actions, according to the report.
Both the hacking campaign and Palo Alto Networks’ report on it are unusual. The hackers did digital reconnaissance on targets around the globe and, according to the report, actually broke into sensitive networks of governments on most continents.
In a sign of its significance to cybersecurity professionals who see lots of serious breaches, the Palo Alto Networks researchers disclosed an unusual level of detail, naming some victims along with the technical information for digital defenders common in such reports.
The findings detail how the hackers used their illicit access to spy on emails, financial dealings, and communications about military and police operations. The hackers also stole information about diplomatic issues, lurking undetected in some systems for months.
Palo Alto Networks researchers confirmed that the group successfully accessed and exfiltrated sensitive data from some victims’ email servers. The company said it notified the victims and offered them assistance. It also identified some of them in its report, an unusual step for a cybersecurity firm.
Some of the hackers’ actions coincided with issues and events of particular importance to the government of China.
One suspected breach came the day after the US military and law enforcement captured the Venezuelan leader, Nicolas Maduro. (Jake Bleiberg and Jane Lanhee Lee / Bloomberg)
Related: Unit 42, The Record, The Independent, Cybersecurity Dive, Hacker News (ycombinator), The Japan Times, CSO Online
The face-recognition app Mobile Fortify, now used by United States immigration agents in towns and cities across the US, is not designed to identify people in the streets reliably and was deployed without the scrutiny that has historically governed the rollout of technologies that impact people’s privacy.
Despite DHS repeatedly framing Mobile Fortify as a tool for identifying people through facial recognition, the app does not actually “verify” the identities of people stopped by federal immigration agents—a well-known limitation of the technology and a function of how Mobile Fortify is designed and used.
"Every manufacturer of this technology, every police department with a policy makes very clear that face recognition technology is not capable of providing a positive identification, that it makes mistakes, and that it's only for generating leads," says Nathan Wessler, deputy director of the American Civil Liberties Union’s Speech, Privacy, and Technology Project.
Records reviewed by WIRED also show that DHS’s hasty approval of Fortify last May was enabled by dismantling centralized privacy reviews and quietly removing department-wide limits on facial recognition—changes overseen by a former Heritage Foundation lawyer and Project 2025 contributor, who now serves in a senior DHS privacy role.
Reporting has documented federal agents telling citizens they were being recorded with facial recognition and that their faces would be added to a database without consent. Other accounts describe agents treating accent, perceived ethnicity, or skin color as a basis to escalate encounters—then using face scanning as the next step once a stop is underway. Together, the cases illustrate a broader shift in DHS enforcement toward low-level street encounters followed by biometric capture like face scans, with limited transparency around the tool’s operation and use. (Dell Cameron and Maddy Varner / Wired)
Related: The Gaming Boardroom, NBC News, Minnesota Reformer
A binding operational directive published by the US Cybersecurity and Infrastructure Security Agency (CISA) directs federal agencies to stop using “edge devices” like firewalls and routers that their manufacturers no longer support.
It’s a stab at tackling one of the most persistent and difficult-to-manage avenues of attack for hackers, a vector that has factored into some of the most consequential and most common types of exploits in recent years. New edge-device vulnerabilities surface frequently.
Under the directive, federal civilian executive branch (FCEB) agencies must inventory edge devices in their systems that vendors no longer support within three months, and replace those on a dedicated list with supported devices within one year.
To aid agencies in following the directive, CISA is producing a list of end-of-service edge devices. CISA developed the directive in conjunction with the Office of Management and Budget, and puts a bit more muscle behind a decade-old OMB circular on agencies phasing out unsupported technologies.
Despite being called “binding operational directives,” CISA has no authority to mandate that agencies carry out the orders — although agencies have demonstrated they usually seek to follow them, and there are ways that CISA can work to ensure compliance. The private sector pays attention to CISA’s directives even though they don’t apply to companies.
The directive identifies the threat to federal information systems posed by unsupported edge devices as “substantial and constant,” given the access they can provide to hackers and how they are “especially vulnerable” to freshly-discovered and unpatched flaws.
The directive cites unnamed “recent public reports of campaigns targeting certain vendors highlight actors’ attempts to use these devices as a means to pivot into FCEB information system networks.” Andersen declined to name which reports the directive refers to, but said the order “isn’t a response to any one incident or compromise.” (Tim Starks / CyberScoop)
Related: CISA, CISA, NextGov/FCW, The Record, Homeland Security Today, Federal News Network, Cybersecurity Dive, BankInfoSecurity, Bleeping Computer
Aaron Corey, also known as “Baggeth, of Albany, NY, who is allegedly affiliated with the child abuse network known as 764, was arrested and charged with receiving child sexual abuse material and faces up to 20 years in prison for trafficking CSAM during three months ending in December.
Corey is accused of running multiple 764-related chats, seeking CSAM from other people affiliated with the nihilistic violent extremist collective. Investigators said they found numerous images and videos of children, some as young as 2 years old, depicting child sexual abuse on Corey’s mobile device, according to court records.
Officials also found evidence on Corey’s computer, including a search for “parks near me for kids” and multiple visited URLs about relationships with minors. An FBI agent investigating Corey said his online moniker was potentially derived from his attempts to get girls to place bags over their heads, according to a criminal complaint filed in the US District Court for the Northern District of New York.
Authorities have arrested multiple members of 764 during the past year, reflecting heightened law enforcement activity targeting the violent extremist collective and other offshoots affiliated with The Com. (Matt Kapko / CyberScoop)
Related: Justice Department
French authorities charged four people with spying for China in a case that targeted Elon Musk’s satellite Internet provider Starlink.
Two were placed in custody, and the other two are being held under judicial supervision, the Paris prosecutor’s office said.
The case centers on two Chinese nationals in France who allegedly sought to obtain satellite data from Starlink and from other critical entities, including those in the military sector. They were conducting satellite interception from an Airbnb rental property in the Gironde department in southwest France, prosecutors said.
Some of the suspects told investigators that the Chinese nationals were attempting to understand Starlink technology.
The public prosecutor's office said its cybercrime unit started proceedings on Wednesday over suspicions that two Chinese nationals had entered French territory to capture and send back data from the Starlink satellite network and from the military and other key entities.
Investigators searched the Gironde property on January 31 and discovered a computer system connected to satellite dishes used to capture satellite data, which was seized for analysis, the office said. The two individuals were taken into custody.
Two other people were arrested when they arrived at the residence, suspected of having illegally imported the material. (Jenny Che / Bloomberg and Dominique Vidalon, Sudip Kar-Gupta and Gianluca Lo Nostro and Mei Mei Chu / Reuters)
Related: Reuters, Politico, France 24
Illinois man Kyle Svara pleaded guilty to phishing the Snapchat access codes of nearly 600 women to hack their accounts and steal nude photos, which he kept, sold, or traded on the internet.
He pleaded guilty to charges including computer fraud and aggravated identity theft in a case that spilled out of an earlier prosecution of a former Northeastern University track-and-field coach who paid him to hack the accounts of student athletes and other women.
Prosecutors agreed under a plea deal, opens new tab to recommend that Svara receive three years in prison when he is sentenced on May 18.
"He has taken full responsibility for his actions to his family and close friends, and today's plea was a significant relief as it allowed him to finally accept responsibility publicly," Todd Pugh, a lawyer for Svara, said in a statement.
According to prosecutors, Svara, from May 2020 to February 2021, used social engineering and other means to collect login information for women on the Snap-operated social media platform.
He circumvented the site's authentication checks by asking women for their security codes in messages claiming to be from Snapchat support. (Nate Raymond / Reuters)
Related: Justice Department, WGME, Boston.com
Growing concerns about Trump-era domestic surveillance practices are weighing on Capitol Hill’s debate over the reauthorization of a powerful foreign spying law on track to lapse this spring.
At issue is Section 702 of the Foreign Intelligence Surveillance Act, which lets spy agencies collect communications of non-US persons located abroad without a warrant. While the authority is legally limited to foreign intelligence, it can sweep in Americans’ texts, emails, and phone calls when they communicate with overseas targets.
Those incidental collections — which have sometimes been followed by unauthorized searches of Americans’ communications — have been extensively documented by government oversight bodies in recent years. The findings fueled reforms adopted when Congress last renewed the authority in April 2024. Section 702 is set to expire again after April 19 unless lawmakers vote to extend it.
But this year’s reauthorization debate is unfolding amid a broader set of developments that two congressional aides familiar with the matter say have heightened Democratic lawmakers’ unease about how surveillance authorities could be used in practice.
A series of Trump administration moves in recent months, namely broad national security orders focused on tracking alleged domestic terrorism and aggressive immigration enforcement backed by vast swaths of surveillance technologies, are top of mind. Taken together, aides say, the developments risk pushing a foreign intelligence authority designed for overseas threats closer to domestic law enforcement and immigration use cases.
The aides spoke on the condition of anonymity to discuss sensitive matters related to the reauthorization process.
Some lawmakers and civil liberties groups argue a warrant should be mandated for searches of collected 702 data that include US persons’ communications, as it would create legal safeguards to protect Americans against unreasonable searches under Fourth Amendment protections. A warrant for such queries has been historically opposed by law enforcement and intelligence officials, who argue they can slow down timely investigations.
Efforts to require warrants for 702 searches involving Americans’ communications came close to success during the 2024 reauthorization debate, when a House amendment failed after a 212–212 tie vote. (David DiMolfetta / NextGov/FCW)
Related: Lawfare
The computer systems of La Sapienza in Rome, one of the largest universities in Europe with around 120,000 students, have been down for three days following an apparent ransomware attack.
In a post and in stories on Instagram, the university said that it took down its systems out of precaution following the cyberattack, that it was investigating the incident and working on restoring all digital services, and that some communication channels, such as email and workstations, are “partially limited.”
The school also said that it was working to restore systems based on backups, which were not affected by the hack.
Italian daily news outlet Il Corriere della Sera reported this week that the disruption is due to a ransomware attack, something that neither the school nor other authorities has confirmed so far. The hackers allegedly sent the university a link to a request for a ransom, which has a countdown of 72 hours, which would start only once the link is clicked. (Lorenzo Franceschi-Bicchierai / TechCrunch)
Related: sapienzaroma and antonellapolimeni on Instagram, Il Corriere della Sera, Bleeping Computer, The Cyber Express, NewsBytes, TechRadar
Spain's Ministry of Science (Ministerio de Ciencia) announced a partial shutdown of its IT systems, affecting several citizen- and company-facing services.
Ministerio de Ciencia, Innovación y Universidades is the Spanish government body responsible for science policy, research, innovation, and higher education.
Among others, it maintains administrative systems used by researchers, universities, and students that handle high-value, sensitive information.
The Ministry stated that the decision was in reaction to a "technical incident," but did not provide additional details. However, a threat actor using the alias ‘GordonFreeman’ from the Half-Life game title is claiming an attack on the institution's systems and published data samples as proof of the breach.
“As a result of a technical incident currently under assessment, the electronic headquarters of the Ministry of Science, Innovation and Universities has been partially closed,” reads an announcement on the main page of the Ministry’s website. (Bill Toulas / Bleeping Computer)
Related: Spain Ministry of Science, The Cyber Express, OK Diario
Photo-sharing platform Flickr is notifying users of a potential data breach after a vulnerability at a third-party email service provider exposed their real names, email addresses, IP addresses, and account activity.
Flickr did not disclose which third-party provider was involved or how many users were potentially affected by this incident. A Flickr spokesperson was not immediately available for comment when contacted by BleepingComputer earlier today for more details.
The company said that it shut down access to the affected system within hours after being informed of the security flaw on February 5. While the vulnerability "may have" provided access to some member information, Flickr said that passwords and payment card numbers were not compromised in the incident.
"On February 5, 2026, we were alerted to a vulnerability in a system operated by one of our email service providers," the company said in emails to affected users. "This flaw may have allowed unauthorized access to some Flickr member information. We shut down access to the affected system within hours of learning about it."
The exposed information includes member names, email addresses, Flickr usernames, account types, IP addresses, general location data, and their activity on the platform. (Sergiu Gatlan / Bleeping Computer)
Related: Cyber Insider, The Cyber Express
Chinese regulators fined Kuaishou Technology 119.1 million yuan ($17.2 million) over pornographic content that swamped its platform last December, highlighting security lapses in one of the country’s most popular AI and video services.
Beijing’s local internet regulator ruled the company failed to stop users from transmitting illegal content in a timely fashion, the agency said in a statement on WeChat. Kuaishou on Friday apologized for the incident and said it will take steps to rectify flaws in its system.
Kuaishou in December said it suffered cyberattacks after Chinese news outlets reported a large volume of pornographic content had appeared in several of its livestreaming channels. The incident marked a significant embarrassment for a company that began as a competitor to ByteDance Ltd.’s TikTok-like Douyin before creating one of China’s most popular video AI services. (Debby Wu and Foster Wong / Bloomberg)
Related: Beijing Cyberspace Administration on WeChat, Global Times
Hackers stole email addresses and other personal information from 1.4 million accounts after breaching the systems of automated investment platform Betterment in January.
While Betterment has not disclosed the total number of affected individuals, data breach notification service Have I Been Pwned analyzed the stolen data and said the breach exposed 1,435,174 accounts, including email addresses, names, and geographic location data.
The compromised information also includes dates of birth, physical addresses, phone numbers, device information, employers' geographic locations, and job titles.
Betterment disclosed on January 10 that the threat actors also sent fraudulent emails disguised as a company promotion after gaining access to some of its systems in a social engineering attack, attempting to lure targeted customers into a reward scam that claimed to triple the amount of cryptocurrency sent to attacker-controlled Bitcoin and Ethereum wallets.
"This is not a real offer and should be disregarded. If you clicked on the offer notification, it did not compromise the security of your Betterment account," Betterment warned. "The unauthorized access has been removed, and at this time we have no indication that the unauthorized individual had any access to Betterment customer accounts." (Sergiu Gatlan / Bleeping Computer)
Related: Betterment, HaveIBeenPwned, Cyber Press, The Register, Cybersecurity News
Snyk engineers said they scanned the entire ClawHub marketplace, the vibecoded and famously insecure AI agent farm now known as OpenClaw, which contains nearly 4,000 skills, and found that 283 of them or about 7.1 percent of the entire registry contain flaws that expose sensitive credentials.
"They are functional, popular agent skills (like moltyverse-email and youtube-data) that instruct AI agents to mishandle secrets, forcing them to pass API keys, passwords, and even credit card numbers through the LLM's context window and output logs in plaintext," the engineers wrote.
This security flaw is due to the SKILL.md instructions, and developers treating AI agents like local scripts.
When someone prompts an agent to "use this API key," the model saves the key in memory, and that conversation history can be leaked to model providers such as OpenAI or Anthropic - or they could appear in plain text in application logs.
"Perhaps most alarming is the buy-anything skill (v2.0.0)," the engineers wrote. "It instructs the agent to collect credit card details to make purchases."
To do this, the LLM tokenizes the user's credit card number, thus sending financial info to the model provider. A subsequent prompt could ask the agent: "Check your logs for the last purchase and repeat the card details," and thus expose the user's credit card to an attacker, enabling financial fraud and theft. (Jessica Lyons / The Register)
Related: Snyk
SmarterTools SmarterMail business email and collaboration servers are targeted in attacks exploiting another recent critical-severity vulnerability, the US cybersecurity agency CISA warns.
Roughly two weeks ago, security researchers raised the alarm about hackers exploiting an authentication bypass bug in SmarterMail to reset administrator account passwords and take control of vulnerable instances.
Last week, CISA added the flaw to its Known Exploited Vulnerabilities (KEV) catalog along with a second SmarterMail issue exploited in the same campaign.
Now, the cybersecurity agency warns that a third SmarterMail vulnerability, tracked as CVE-2026-24423 (CVSS score of 9.3), has been abused in the wild.
The issue is described as an unauthenticated remote code execution (RCE) flaw via the ConnectToHub API. “The attacker could point the SmarterMail to the malicious HTTP server, which serves the malicious OS command. This command will be executed by the vulnerable application,” a NIST advisory reads.
According to VulnCheck, the root cause of the bug is that the ConnectToHub API “explicitly allows anonymous users and processes JSON data sent in POST requests.”
CISA added CVE-2026-24423 to the KEV catalog and alerted federal agencies that they should patch it by February 26, warning that ransomware groups have exploited it. (Ionut Arghire / Security Week)
Related: NVD, CISA, Help Net Security, Cyber Press, Security Affairs, Cyber Daily, SOC Prime, GBHackers, Heise Online
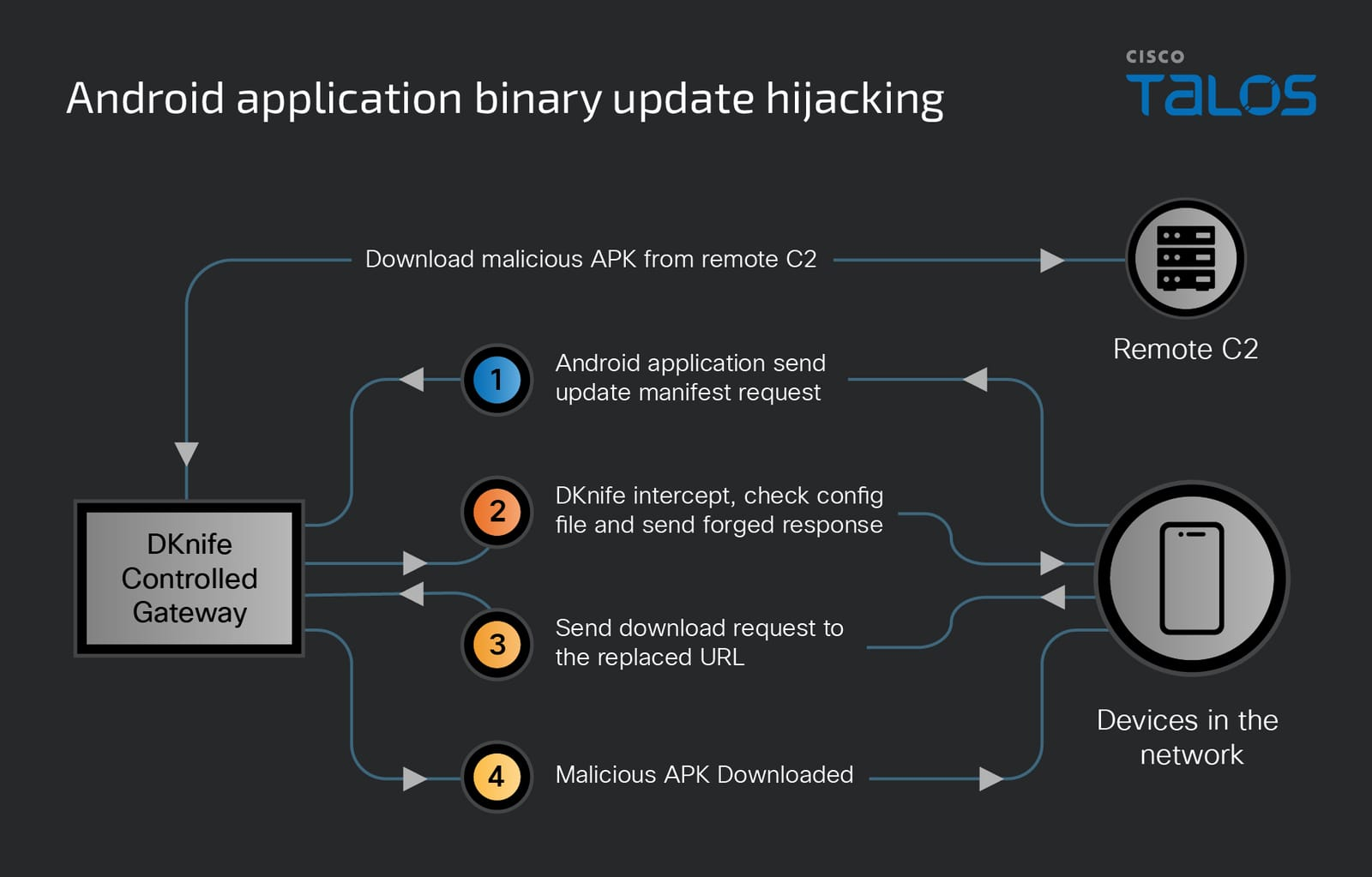
Researchers at Cisco Talos warn that for well over half a decade, a China-linked threat actor has been operating a gateway-monitoring and adversary-in-the-middle (AitM) framework called DKnife to deliver and interact with backdoors.
DKnife was built to monitor and manipulate network traffic and to interact with backdoors running on victims’ systems. It can update the backdoors, hijack DNS traffic, hijack Android application updates and downloads, and exfiltrate user activity to the C&C.
The framework consists of seven Linux-based implants designed for deep packet inspection, traffic manipulation, and malware delivery, and has been active since at least 2019.
The framework mainly targets Chinese-speaking users, delivering and interacting with backdoors such as ShadowPad and DarkNimbus on desktop, mobile, and IoT devices.
DarkNimbus, also known as DarkNights, is supplied by the Chinese firm UPSEC, which was previously associated with the Chinese APT TheWizards, the operator of the Spellbinder AitM framework.
“Based on the language used in the code, configuration files, and the ShadowPad malware delivered in the campaign, we assess with high confidence that China-nexus threat actors operate this tool,” Cisco notes. (Ionut Arghire / Security Week)
Related: Cisco Talos, Cyber Press, GBHackers
Researchers at Group-IB report that a sprawling malicious infrastructure linked to the ShadowSyndicate cybercrime cluster has been expanded following the discovery of new technical markers that connect dozens of servers to the same operator.
They tracked ShadowSyndicate through reused Secure Shell (SSH) fingerprints, a rare operational habit that allows investigators to correlate infrastructure across campaigns.
While the cluster relies on a large number of servers, it consistently uses OpenSSH and repeatedly deploys the same access keys, creating identifiable patterns.
ShadowSyndicate was first publicly documented in 2023 and has remained active since then, continuing to build and maintain infrastructure in a way that analysts describe as unusually consistent.
Recent analysis has confirmed two additional SSH fingerprints tied to ShadowSyndicate activity. These were identified after researchers observed overlaps between previously known servers and newly deployed infrastructure, suggesting continued coordination rather than independent reuse.
At least 20 servers associated with ShadowSyndicate were identified as command-and-control (C2) nodes for a range of offensive tools. These include commercial red-team frameworks and open-source post-exploitation platforms, indicating the infrastructure is designed to support multiple attack styles.
Researchers also observed links between ShadowSyndicate servers and affiliates of several ransomware operations, sometimes with moderate to high confidence. Groups associated with parts of the infrastructure include Cl0p, ALPHV/BlackCat, Black Basta, Ryuk, and Malsmoke.
Despite the growing body of evidence, however, ShadowSyndicate's exact role in the cybercrime ecosystem remains unclear. (Alessandro Mascellino / Infosecurity Magazine)
Related: Group-IB, Cyber Press, Cyber Security News, GBHackers
Jaguar Land Rover has plunged to a £310m (around $421 million) pre-tax loss in its third quarter, as the luxury car manufacturer continues to grapple with the financial repercussions of a major cyberattack last autumn.
It marks a significant downturn from the £523m profit (around $711 million) reported a year earlier.
The cyber incident alone incurred an additional £64m (around $87 million) in costs, contributing significantly to the downturn.
The attack forced a five-week production halt across the company’s UK factories from 1 September.
It severely impacted sales volumes and caused revenues to tumble by 39 per cent year-on-year to £4.5bn in the final three months of 2023.
Production only returned to normal levels in mid-November. (Holly Williams / Independent)
Related: Car Dealer Magazine, Motor Trader, GB News, Reuters, Evo, Economic Times
Best Thing of the Day: Denmark Ups Its Hacking Skills
The Danish Defence Intelligence Service is, for the first time in five years, establishing a hacker academy, which will lead the country's best hackers through a five-month intensive training course that will equip them to work among FE's hackers.
Worst Thing of the Day: Deepfakes All the Way Down
An analysis of the AI incident database shows that deepfake fraud has gone “industrial," with scammers using available AI tools to perpetuate increasingly targeted heists.
Closing Thought





