Cloudflare, Palo Alto Networks, and Zscaler are caught up in Salesloft Drift attacks
UK watchdog says military doesn't know Afghan breach-related costs are, Jaguar Land Rover hit by cyber incident, Amazon disrupted Midnight Blizzard op, Trump reactivates ICE spyware contract, Gov'ts are flocking to surveillanceware, much more


Please consider supporting Metacurity
Metacurity has been a labor of love for years, and I’m so grateful for your readership. Your support can help ensure I can continue delivering the carefully curated weekly long-reads and daily digests of the most critical developments in cybersecurity.
If you find value in what Metacurity offers, please consider upgrading to a paid subscription. We also provide corporate subscription options, and soon we’ll be introducing affordable sponsorship opportunities—perfect for promoting your events or products to a highly engaged audience.
To learn more, feel free to reach out at cynthia@metacurity.com.
Thank you so much for being part of the Metacurity community.
If you can't commit to a subscription, please consider donating what you can afford to help keep Metacurity free to all.
Multiple security and technology companies have been swept up in a far-reaching attack spree originating at Salesloft Drift, with Cloudflare, PagerDuty, Palo Alto Networks, SpyCloud, and Zscaler coming forward to confirm attacks as customers of the third-party AI chat agent hunt.
Salesloft initially claimed exposure was limited to customers integrated with Salesforce. However, Google Threat Intelligence Group and Mandiant Consulting, Google’s incident response firm, which is now working with Salesloft, said any platform integrated with Drift is potentially compromised.
Okta said it was not impacted by the incident, but confirmed it was a target based on the indicators of compromise Google Threat Intelligence Group shared last week. “The threat actor attempted to use a compromised token to access our Salesforce instance, but the attack failed because the connection originated from an unauthorized IP address,” the company said.
Sam Curry, chief information security officer at Zscaler, said the company’s Salesloft Drift integration with Salesforce was the point of unauthorized access. The company was using Salesloft Drift integrated with other platforms, but they were not impacted, he added.
Data on a large number of Zscaler’s customers was exposed, including names, business email addresses, job titles, phone numbers, location details, Zscaler product licensing and commercial information, and plain text content from some support cases.
“No product, service, or infrastructure was affected,” Curry said. “We are looking to hear from Salesloft Drift and from Salesforce if there are any other findings since this happened in their infrastructure.”
Palo Alto Networks confirmed that it, too, was one of hundreds of organizations impacted by the supply chain attack. The company’s incident response business unit, Unit 42, confirmed the incident was limited to its Salesforce environment, adding that no Palo Alto Networks products or services were impacted.
Cloudflare said any information customers shared with the company’s support system, including logs, tokens, or passwords, should be considered compromised. The company said it found 104 Cloudflare API tokens in the compromised data and, while it found no evidence of abuse, rotated the tokens out of an abundance of caution.
The company also maintained that no Cloudflare services or infrastructure were compromised. (Matt Kapko / Cyberscoop)
Related: Unit 42, Cloudflare, The Register, Okta, Bloomberg, Security Affairs, Dark Reading, CSO Online, The Conversation, HackRead, Cyber Daily, Infosecurity, JD Supra, Benzinga, SiliconANGLE, Bleeping Computer, Hacker News (ycombinator), Channel Futures, Neowin
UK public spending watchdog National Audit Office (NAO) said the country's Ministry of Defence (MoD) cost estimate of £850 million (around $1.1 billion) to relocate Afghans whose lives are in peril following a massive data leak is an unreliable figure MoD has not provided enough evidence to give it confidence in that figure, which does not include legal expenses, or compensation claims likely to follow.
Last month, it was revealed that the details of almost 19,000 people who had applied to move to the UK to flee the Taliban were leaked when an official mistakenly emailed a spreadsheet that contained a hidden tab with the information in 2022.
It contained information like names, contact details, and family information of people who believed their cooperation with British forces during the Afghanistan war put them at risk of reprisals.
Following the data breach, a new scheme - the Afghanistan Response Route (ARR) - was secretly set up in April 2024, allowing a further 7,000 to come to the UK.
A super-injunction granted by the High Court in September 2023 prevented the incident from being reported for almost two years, before the order was lifted in July.
The MoD estimates the cost for resettling each individual to be £128,000, with the total bill for all its Afghan resettlement programmes forecast to exceed £2bn.
In a report, the NAO said the government had failed to provide sufficient evidence to give the watchdog "confidence" to say if its £850m figure was accurate.
The watchdog said: "The MoD is not able to determine exactly what it has spent on resettling people through the ARR scheme. (Jonathan Beale and Adam Durbin / BBC News)
Related: National Audit Office, GB News, Reuters, Independent, The Guardian, Sky News, Financial Times
Marking the latest in a string of British companies hampered by cyberattacks, Jaguar Land Rover's retail and production activities have been "severely disrupted" following a cybersecurity incident, the British luxury carmaker said, adding that it was working to restart its operations in a controlled manner.
The company, owned by India's Tata Motors, said it had not found any evidence at this stage that any customer data had been stolen after it shut down its systems to mitigate the impact.
Over the past several months, British retailers M&S, Harrods, and Co-op have had their operations disrupted by the threat group known as Scattered Spider. (Pushkala Aripaka / Reuters)
Related: Bloomberg, Autocar, The Guardian, City AM, The Record, Bleeping Computer, BBC News, Cyber Daily, The Stack
Amazon's threat intelligence team disrupted an operation attributed to the Russian state-sponsored threat group Midnight Blizzard, which sought access to Microsoft 365 accounts and data.
Also known as APT29, the hacker group compromised websites in a watering hole campaign to redirect selected targets "to malicious infrastructure designed to trick users into authorizing attacker-controlled devices through Microsoft’s device code authentication flow."
The Midnight Blizzard threat actor has been linked to Russia’s Foreign Intelligence Service (SVR) and is well-known for its clever phishing methods that recently impacted European embassies, Hewlett Packard Enterprise, and TeamViewer.
Amazon discovered the domain names used in the watering hole campaign after creating an analytic for APT29's infrastructure.
An investigation revealed that the hackers had compromised multiple legitimate websites and obfuscated malicious code using base64 encoding with the threat actors used a cookies-based system to prevent the same user from being redirected multiple times, reducing suspicion.
Victims that landed on the fake Cloudflare pages were guided to a malicious Microsoft device code authentication flow, in an attempt to trick them into authorizing attacker-controlled devices.
Amazon notes that once the campaign was discovered, its researchers isolated the EC2 instances the threat actor used, partnered with Cloudflare and Microsoft to disrupt the identified domains. (Bill Toulas / Bleeping Computer)
Related: Amazon, The Record, Infosecurity Magazine, Dark Reading, Security Week
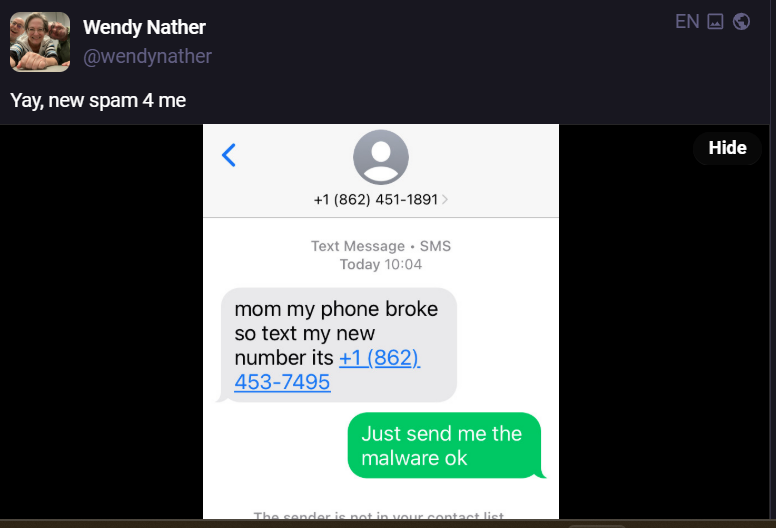
The Trump administration reactivated an ICE contract for spyware from Tel Aviv-based Paragon that had previously been blocked due to a stop order, according to procurement records posted on a government website.
The immigration agency signed a $2 million deal last September for the Paragon software, which has allegedly been used to target activists and journalists in Europe, but the contract was hit with a stop-work order soon after.
The development gives ICE a powerful new spying tool in its nationwide crackdown on undocumented immigrants as it attempts to deliver on President Donald Trump’s promise to carry out the largest mass deportation in US history. Details about the renewed contract were earlier reported by the newsletter All Source Intelligence. (Ryan Gallagher / Bloomberg)
Related: FPDS.gov, Jack Poulson, The Guardian, Washington Post, TechCrunch, All-Source Intelligence, Hackwhackers, The Register, PCMag, Business Standard, WebProNews
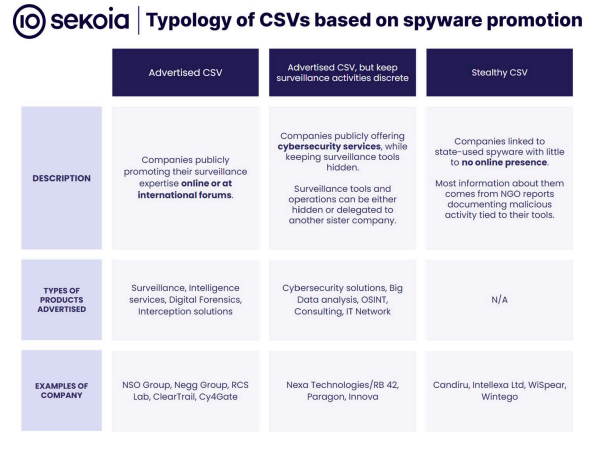
An analysis of the surveillanceware industry by security operations center specialist Sekoia shows that governments are flocking to surveillanceware vendors who are seeing their businesses grow in leaps and service prices increase.
For example, the report recounts that, in 2011, the Gamma Group - a British biz that was offering FinFisher spyware was charging government agencies €1,100 per infection. Four years later, the Italian vendor Hacking Team was offering similar attack code for €1 million for a full hacking service, but by 2022, an investigation into the Candiru spyware biz showed that it was charging €6 million for its surveillanceware-as-a-service operations.
"In addition to being very lucrative, documents of major leaders of the sector dating from 2011 to 2022 demonstrate that the price for spyware use is in a constant rise. This is partly due to the increased cost of acquiring vulnerabilities and exploits, but also to the important number of clients looking for spyware," Sekoia said. (Iain Thomson / The Register)
Related: Sekoia, Cyber Insider
Brazilian media company O Globo reported that hackers broke into broke into Sinqia, a financial technology provider owned by Evertec, attempting to steal around 420 million reais ($77.4 million) from several Brazilian financial institutions including HSBC Holdings Plc’s local operations.
Cyber criminals invaded Sinqia’s systems used by Brazilian financial institutions and attempted to make several transfers through a fast-growing electronic payments system known as Pix. Sinqia confirmed the attack but said there was no evidence of suspicious activity in any system besides Pix.
Sinqia is working to rebuild the affected systems with enhanced controls and will only put Pix back online pending a review from the central bank, it said in a statement on Saturday.
Hackers sought to divert around 380 million reais from HSBC, O Globo said, adding the Brazilian central bank managed to block 350 million reais from the attack. It did not say what happened to the rest.
HSBC confirmed the incident in a statement, saying “no customer accounts or funds were impacted by the operation and measures have been taken to block these transactions.” (Clarice Couto / Bloomberg)
Related: O Globo, Bleeping Computer, Cyber Insider, The Paypers
Google is facing an unusual ultimatum from a hacker collective that calls itself Scattered LapSus Hunters, which has demanded the firing of two of its cybersecurity leaders, Austin Larsen and Charles Carmakal, or risk a major data leak.
The threat comes shortly after Google confirmed that ShinyHunters had accessed data from Salesforce, a third-party service provider. While Google said there was no breach of its internal databases or consumer Gmail accounts, the attackers appear to be leveraging the incident for pressure.
Although some reports regarding this threat said that Google warned all Gmail users to reset their passwords due to a recent data breach that also affected some Workspace accounts, Google said those are false stories.
The company said "Gmail's protections are strong and effective, and claims of a major Gmail security warning are false."
"Several inaccurate claims surfaced recently that incorrectly stated that we issued a broad warning to all Gmail users about a major Gmail security issue. This is entirely false," Google added. (Jatin Verma / WION and Sergiu Gatlan / Bleeping Computer)
Related: The Keyword, Financial Express, Hindustan Times, Newsweek, Mashable India, Economic Times, Mashable, Ars Technica, The Hill, Techzine, Cyber Insider, IT Pro, Rolling Out
Artists&Clients, a website that connects independent artists with interested clients, was hit by a ransomware threat attributed to the ransomware group LunaLock, which demanded payment or else it would release the data it stole and, in a new twist, threatened to submit all artwork to AI companies to be added to training datasets.
LunaLock promised to delete the stolen data and allow users to decrypt their files if the site’s owner paid a $50,000 ransom.
Tammy Harper, a senior threat intelligence researcher at the cybersecurity company Flare, said that this kind of threat could be effective against artists. “It’s a very sensitive subject for this type of victim (an art marketplace). LunaLock is definitely using and hoping for the clients and artists of the victim to pressure them into paying the ransom.” (Matthew Gault / 404 Media)
Related: Cyber Daily
Blockchain security firm PeckShield reported that a user of the DeFi lending platform application-layer saw crypto assets worth $13.5 million disappear in a phishing attack.
Venus Protocol’s official social media account responded to community concerns in an X thread, confirming there was no flaw in its smart contracts.
When a user asked if this was due to the user’s mistake, Venus said it was likely the case. However, Venus said that as a precautionary measure, it would pause the protocol to conduct security reviews.
“Right now, yes, that appears to be the case. We will keep everyone updated as we investigate,” Venus Protocol said. “Protocol is paused while security reviews are underway.” (Ezra Reguerra / Cointelegraph)
Related: Coindesk, OneSafe, DL News, Cryptopolitan, The Block, CCN
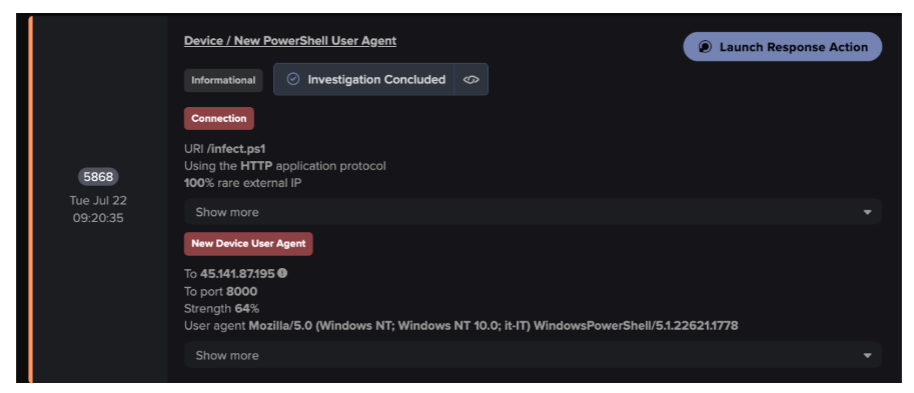
Researchers at DarkTrace discovered a cryptojacking attempt in its early stages, offering insights into a new cryptomining strain.
In July 2025, Darktrace detected and contained an attempted cryptojacking incident on the network of a customer in the retail and e-commerce industry, when a threat actor attempted to use a PowerShell script to download and run NBMiner directly in memory.
Specifically, the targeted desktop device established a connection to the rare
endpoint, 45.141.87[.]195, over destination port 8000 using HTTP as the application-layer protocol. Within this connection, Darktrace observed the presence of a PowerShell script in the URI, specifically ‘/infect.ps1’.
Darktrace’s analysis of this endpoint (45.141.87[.]195[:]8000/infect.ps1) and the payload it downloaded indicated it was a dropper used to deliver an obfuscated AutoIt loader. This attribution was further supported by open-source intelligence (OSINT) reporting. The loader likely then injected NBMiner into a legitimate process on the customer’s environment – the first documented case of NBMiner being dropped in this way. (Ronny Roy / crypto.news)
Related: Darktrace
Singapore Minister of State for Home Affairs Goh Pei Ming said that Singapore police have ordered Meta to implement anti-scam measures against advertisements, accounts, profiles, and business pages impersonating key government office holders on its social media network Facebook to combat scams.
The company could be fined up to S$1 million ($775,698) if it fails to comply as part of the first such order under the nation's new Online Criminal Harms Act, which came into force in February 2024.
In August, Singapore's home affairs ministry found that more than a third of all e-commerce scams reported in 2024 were perpetrated on Facebook. It also rated Facebook Marketplace as the weakest among six e-commerce marketplaces in terms of anti-scam features deployed.
A Meta spokesperson said that the company had specialised systems to detect impersonating accounts, including facial recognition technology, and it had invested heavily in improving detection and review teams. It also shares tips on avoiding scams and offers tools to report potential violations, the spokesperson said. (Jun Yuan Yong / Reuters)
Related: Benzinga
According to the annual Singapore Cyber Landscape 2024/2025 report released by the Cyber Security Agency of Singapore (CSA), in 2024, the cyber threat landscape in Singapore was dominated by phishing attempts, ransomware attacks, and infected hardware.
Phishing attempts in Singapore increased by 49 per cent to 6,100 cases. The banking and financial services (BFS) sector was the most targeted industry.
Ransomware attacks increased by 21 per cent from last year, with 159 reported cases.
Infected computer infrastructure remained a concern with a 67 per cent increase from 70,200 infected systems in 2023 to 117,300 in 2024. (Amit Roy Choudhury / GovInsider)
Related: Cybersecurity Agency of Singapore, The Straits Times
South Korean authority The Korea Consumer Agency said it inspected six robot vacuum models, four Chinese and two Korean products, and discovered serious security flaws in three Chinese brands: Narwal, Ecovacs, and Dreame.
The Korea Consumer Agency said all affected companies have since patched the issues. Meanwhile, models from Samsung Electronics and LG Electronics were rated as having stronger protections, including solid access controls, anti-tampering features, and secure password systems, according to the agency. (Song Seung-hyun / The Korea Herald)
Related: Maeil Business Newspaper, The Chosun Daily, Pulse,
While some state offices and agencies remain offline after last month's cyberattack, the Nevada DMV is now offering some in-person services.
The DMV also says “all vehicle appointments that were canceled between August 25 – August 30 will be honored as walk-ins starting today, September 2.”
“All offices are open for registration, titling, and other vehicle related services. Identification and driving privilege services (such as new IDs, licenses) remain unavailable at this time.”
“Walk-ins will be available during business hours, Monday – Saturday (Monday – Friday only for Carson City).”
Online, Nevadans can use services like registration renewal, driver history printouts, registration and insurance status, insurance general information, personalized plate ordering, rapid registration, and vehicle taxes history. (2News Nevada)
Related: The Nevada Globe, KSNV, Carson Now, Las Vegas Review-Journal
Pennsylvania’s Office of Attorney General (OAG) confirmed that it has been hit by a ransomware attack, causing delays to civil and criminal court cases.
The state’s Attorney General, Dave Sunday, confirmed the incident knocked OAG servers offline earlier in August.
“The interruption was caused by an outsider encrypting files in an effort to force the office to make a payment to restore operations. No payment has been made,” Sunday said.
The OAG has not provided any indication whether data was potentially stolen in the attack.
“An active investigation is ongoing with other agencies, which limits our ability to comment further on the investigation or response to the incident,” Sunday continued. (James Coker / Infosecurity Magazine)
Related: Pennsylvania Attorney General, SC Media, The Record, The Cyber Express
The Walt Disney Company said it agreed to pay $10 million to settle a children's privacy lawsuit with the Federal Trade Commission related to videos it uploaded on YouTube mostly during the pandemic which the FTC alleged violated the 1998 Children's Online Privacy Protection Act (COPPA).
The FTC complaint alleges Disney failed to designate certain YouTube videos as being made for children when it added them to the platform. In failing to do so, Disney inadvertently allowed those videos to be targeted with online advertising, which is why the FTC considers the improper designation problematic. (Sara Fischer / Axios)
Related: FTC, The Record, The Cyber Express, Deadline, The Verge, Reuters, CBS News, The Wall Street Journal, The Verge, Engadget, USA Today
A global, six-year campaign to counter Chinese tech dominance took a hit this summer when Congress defunded a key research program to create a worldwide alternative to 5G giant Huawei when Donald Trump's One Big Beautiful Bill cut nearly $1 billion for the Wireless Innovation Fund, which was supposed to create a new, American-dominated type of 5G network.
The defunding is a significant, setback for America’s prolonged effort to root Chinese-made equipment out of the world’s telecommunications backbone. That campaign has reached into the American heartland, caused drama with allies internationally and even led to global intrigue when Huawei’s chief financial officer was arrested, extradited to the US, and later traded in a prisoner swap. (John Hendel / Politico)
The US National Institute of Standards and Technology (NIST) revised its Security and Privacy Control catalog to help vendors and organizations improve software update and patch release protocols.
Initially published in 2020, the Security and Privacy Control catalog details security and privacy safeguards to help organizations mitigate cyber-risks. Federal information systems are required to implement the controls, but the catalog is intended for the private and public sectors. It covers access, authentication, incident response, and supply chain risk management.
The latest update focuses on addressing risks related to software updates and patch releases. The changes are meant to "help organizations understand their role in ensuring the security of the software on their systems," according to NIST. (Arielle Waldman / Dark Reading)
Related: NIST, ExecutiveGov, MeriTalk, Industrial Cyber, Biometric Update
Senate Intelligence Committee Vice Chairman Mark Warner (D-VA) said that he is being blocked from a scheduled oversight meeting after interference from far-right activist Laura Loomer.
Warner said the National Geospatial-Intelligence Agency meeting scheduled for Friday was called off after Loomer launched public attacks on him and the NGA’s director, Vice Adm. Trey Whitworth.
“This nakedly political decision undermines the dedicated, nonpartisan staff at NGA and threatens the principle of civilian oversight that protects our national security,” Warner said in a statement.
“Members of Congress routinely conduct meetings and on-site engagements with federal employees in their states and districts; blocking and setting arbitrary conditions on these sessions sets a dangerous precedent, calling into question whether oversight is now allowed only when it pleases the far-right fringe,” he said. (Dan De Luce / NBC News)
Related: Augusta Free Press, The Daily Beast
Nick Andersen, a Marine veteran and former Department of Energy cybersecurity official, began his role as the executive assistant director for cybersecurity in the Cybersecurity and Infrastructure Security Agency.
Andersen has both public and private sector experience. He was previously president and chief operating officer at cyber company Invictus, and also chief information security officer at enterprise tech provider Lumen’s public sector unit. He is also a former nonresident senior fellow with the Atlantic Council’s Cyber Statecraft Initiative.
From 2019 to 2021, in President Donald Trump’s first term, Andersen served both as the principal deputy assistant secretary and performed the duties of assistant secretary for the Department of Energy’s Cybersecurity, Energy Security, and Emergency Response unit. He was also the CISO for the State of Vermont, and, prior to that, held intelligence roles in the Navy and Coast Guard. (David DiMolfetta / NextGov/FCW)
Related: CISA, The Record, Industrial Cyber, Cyberscoop, Meritalk
Data security company Varonis Systems agreed to acquire SlashNext, an AI-based email security provider, for as much as $150 million, including performance-based retention awards.
SlashNext uses predictive AI to remove threats from email inboxes in real time and detect business email compromise attacks. The acquisition will allow Varonis to expand its reach in the email security sphere at a time when AI has enabled increasingly deceptive email threats, Varonis Chief Marketing Officer Rob Sobers said. (Emily Forgash / Bloomberg)
Related: Varonis, SiliconANGLE, BankInfoSecurity.com, CyberScoop, Help Net Security
Best Thing of the Day: Decipher Lives!
After a year-long hiatus, cybersecurity publication Decipher has returned with its original editors, Dennis Fisher and Lindsey O'Donnell-Welch, having obtained the domain, brand, and trademarks from Cisco.
Worst Thing of the Day: A Much-Needed App Falls Short
Coder, journalist and tech expert Micah F. Lee analyzed the Iceblock app that allows users to anonymously report ICE sightings within a 5 mile radius and concluded that despite its promise, it is nothing more than activism theater at this point.
Closing Thought