DOGE workers shared SSN data with outsiders, derailed DISA operations
UK launches national fraud reporting service, China blames Taiwan for cyberattacks, EU proposes freezing out Chinese tech suppliers, New Zealand launches Manage My Health breach probe, Curl ends its bug bounty program due to AI flood, Cloudflare fixes WAF flaw, much more


Please, please, please upgrade your Metacurity subscription today.
Metacurity is one of the few independent media outlets delivering a daily round-up of the critical infosec developments you should know. For years, we have worked to scan thousands of sources to deliver you summarized and aggregated news to help you keep your organizations secure.
We value all of our readers, but the paid subscribers help us keep plugging away at our mission of ending infosec news overload. Please, please help keep Metacurity alive with a paid subscription. Thank you!
If you can't afford a paid subscription right now, please consider donating whatever you can. Thanks.
Although DOGE as a distinct entity within the federal government apparatus seems to have melted into the bureaucracy, reports continue to trickle out about the damage caused by the Elon Musk-led gang of young and inexperienced engineers.
First, the Justice Department revealed in newly disclosed court papers that two DOGE team members working at the Social Security Administration were secretly in touch with an advocacy group seeking to “overturn election results in certain states,” and one signed an agreement that may have involved using Social Security data to match state voter rolls.
Elizabeth Shapiro, a top Justice Department official, said SSA referred both DOGE employees for potential violations of the Hatch Act, which bars government employees from using their official positions for political purposes.
Shapiro’s previously unreported disclosure, dated Friday, came as part of a list of “corrections” to testimony by top SSA officials during last year’s legal battles over DOGE’s access to Social Security data. They revealed that DOGE team members shared data on unapproved “third-party” servers and may have accessed private information that had been ruled off-limits by a court at the time.
Shapiro said the case of the two DOGE team members appeared to undermine a previous assertion by SSA that DOGE’s work was intended to “detect fraud, waste, and abuse” in Social Security and modernize the agency’s technology.
It’s not yet clear whether either of the two DOGE team members — who are not identified in her filing – actually shared data with the advocacy group, which is also unidentified. But she said emails “suggest that DOGE Team members could have been asked to assist the advocacy group by accessing SSA data to match to the voter rolls.”
Separately, according to materials reviewed by The Intercept, DOGE workers significantly derailed operations at a Pentagon tech team with a key US military role, the Defense Information Systems Agency or DISA. This unit is responsible for maintaining secure channels that keep the Pentagon connected to military assets around the world, including nuclear capabilities.
According to a December 2025 contracting memo from DISA, the Command, Control, Communications, and Computers Enterprise Directorate, known as J6, the agency was hobbled by DOGE cuts to such an extent that it was unable to obtain necessary software.
“During calendar year 2025, the DISA/J6 program office has been unexpectedly and significantly impacted by Government programs that incentivized personnel separation or extended periods of leave,” the memo reads, “e.g., Deferred Resignation Program, Voluntary Early Retirement Authority, Voluntary Separation Incentive Payments, Paid Parental Leave.”
A second DISA memo notes that a Deferred Resignation Program established by DOGE in the Office of Personnel Management resulted in the departure of an officer responsible for a critical Pentagon cloud-computing contract, resulting in that contract expiring entirely. The DOGE-induced staffing shortage resulted in a situation, according to the memo, where DISA’s systems faced “extreme risk for loss of service” across the Department of Defense. (Kyle Cheney / Politico and Sam Biddle / The Intercept)
Related: Court Listener, TechCrunch
Report Fraud, a new national fraud reporting service, has launched in the UK, promising to transform how businesses and individuals notify law enforcement about offenses, and how police respond.
It replaces the much-maligned Action Fraud service. Run, like its predecessor, by the City of London Police, it covers England, Wales, and Northern Ireland.
Action Fraud was widely criticized by victims as “not fit for purpose” – with unprofessional staff, slow response times, and a failure to investigate reports or provide updates.
However, the new service aims to provide a more sophisticated, user-friendly, and effective mechanism for fraud reporting, via a “single, modern national reporting, triage and intelligence platform.”
A big part of the change will come from a new backend National Crime Analysis Service (N-CAS), which offers real-time analytics to identify fraud patterns and surface intelligence better.
A national advertising campaign, “Every Report Counts,” will run this week to promote the launch.
City of London Police commissioner, Pete O’Doherty, is the senior responsible officer for delivering Report Fraud – a project that has been years in the making. He argued that, despite fraud and cybercrime being the most common crime type in the UK today, victims often feel unsure where to turn.
“These crimes cause more than financial loss and often have devastating impacts on those targeted. We see the true cost of cybercrime and fraud when taking reports from those affected,” O'Doherty added. (Phil Muncaster / Infosecurity Magazine)
Related: City of London Police, Report Fraud, FinTech Global, The Record
A Chinese government spokesperson said that nearly 4,000 cyberattack incidents originating from Taiwan were investigated by the Chinese mainland last year.
Peng Qing'en, spokesman for the State Council Taiwan Affairs Office, told a news conference that Taiwan's Democratic Progressive Party authorities have repeatedly directed military intelligence agencies and online "cyber forces" to carry out attacks and sabotage against the mainland, spreading illegal and harmful information.
According to Peng, relevant departments investigated and handled nearly 4,000 such incidents, representing a 25 percent increase year-on-year. These attacks primarily targeted key sectors on the mainland, including transportation, finance, technology, and energy, to steal sensitive information, Peng said.
Peng refuted a report recently released by the DPP authorities, which claimed that the mainland had conducted a "comprehensive cyber intrusion" against key infrastructure on the island.
He criticized the DPP authorities for habitually spreading rumors, making false accusations, and smearing the mainland, even at the expense of escalating cross-Strait tensions. (LI SHANGYI / China Daily)
Related: China's State Council Information Office, Xinhua, Global Times
The EU plans to phase out components and equipment from high-risk suppliers in critical sectors, according to a draft proposal released by Brussels - a move criticised by China's Huawei, which is set to be among the companies affected.
The measures, set out by the European Commission in revisions to the EU's Cybersecurity Act, follow a rise in cyber and ransomware attacks and growing concerns over foreign interference, espionage and Europe's reliance on non-EU technology suppliers.
Europe has, however, been tightening scrutiny of Chinese technology. Germany recently appointed an expert commission to reassess trade policy toward Beijing and has banned the use of Chinese components in future 6G telecoms networks.
The US banned approvals of new telecoms equipment from Huawei and Chinese rival ZTE in 2022 and has urged European allies to follow suit. (Foo Yun Chee / Reuters)
Related: European Commission, iTnews, European Commission, BleepingComputer, r/news
Michael Webster, the New Zealand Privacy Commissioner, announced an inquiry into the Manage My Health cybersecurity breach.
Hw said it is clear a privacy investigation is needed, given the scale of the incident, the sensitivity of the information, and some of the systemic issues that were identified.
He said the inquiry will help determine whether Manage My Health had appropriate security safeguards and, if not, why not. It will also look at what steps will be taken to prevent such an incident from happening again.
At the end of December, Manage My Health confirmed it had been hacked, later revealing that information of about 120,000 users could be affected. (RNZ)
Related: Office of the Privacy Commissioner, New Zealand Herald, Stuff
Daniel Stenberg, the maintainer of the popular open-source data transfer tool, cURL has ended the project’s bug bounty program after maintainers struggled to assess a flood of AI-generated contributions.
Stenberg last week lodged a GitHub commit named “BUG-BOUNTY.md: we stop the bug-bounty end of Jan 2026”.
Readers may recall that Stenberg started complaining about AI-generated bug reports in early 2024, and by mid-2025, contemplated killing the project’s bug bounty program. After receiving some strong bug reports that a developer found with help from AI, Stenberg acknowledged that AI can be a fine bug-hunting aid.
Stenberg addressed his decision in a mailing message that opened with news that last week the project’s bug bounty scheme generated seven submissions and that while some identified bugs, none described a vulnerability.
Figuring that out took “a good while.”
He then expressed his hope that ending the bug bounty program will “remove the incentive for people to submit crap and non-well researched reports to us. AI generated or not.”
“The current torrent of submissions put a high load on the curl security team, and this is an attempt to reduce the noise.”
Stenberg’s post also expresses his hope that developers continue to send reports of “actual security vulnerabilities … even if we do not pay for them.”
“The future will tell,” he added, and perhaps reveal not just whether developers will share bug reports, but also if they are willing to risk public criticism if their submissions don’t meet Stenberg’s standards. (Simon Sharwood / The Register)
Related: Heise Online, GitHub, Lists.haxx.se
Cloudflare has fixed a flaw in its web application firewall (WAF) that allowed attackers to bypass security rules and directly access origin servers, which could lead to data theft or full server takeover.
FearsOff security researchers reported the bug in October through Cloudflare's bug bounty program, and the CDN says it has patched the vulnerability in its ACME (Automatic Certificate Management Environment) validation logic with no action required from its customers.
ACME is a protocol that certificate authorities and services like Cloudflare use to automate the issuance, renewal, and revocation of SSL/TLS certificates.
It uses challenges to prove domain ownership before issuing a security certificate, and this is typically done via an HTTP-01 challenge that checks for a validation token at the HTTP path following this format: http://{customer domain}/.well-known/acme-challenge/{token value}. (Jessica Lyons / The Register)
Related: Cloudflare
According to cyber-threat exposure startup Zafran, two "easy-to-exploit" vulnerabilities in the popular open-source software put major enterprises' cloud environments at risk of leaking data or even full takeover.
Chainlit is a Python package that organizations can use to build production-ready AI chatbots and applications. Corporations can either use Chainlit's built-in UI and backend or create their own frontend on top of Chainlit's backend. It also integrates with other tools and platforms, including LangChain, OpenAI, Bedrock, and LlamaIndex, and supports authentication and cloud deployment options.
It's downloaded about 700,000 times every month and saw 5 million downloads last year.
The two vulnerabilities are CVE-2026-22218, which allows arbitrary file read, and CVE-2026-22219, which can lead to server-side request forgery (SSRF) attacks on the servers hosting AI applications.
While Zafran didn't see any indications of in-the-wild exploitation, "the internet-facing applications we observed belonged to the financial services and energy sectors, and universities are also using this framework," CTO Ben Seri said.
Zafran disclosed the bugs to the project's maintainers in November, and a month later, Chainlit released a patched version (2.9.4) that fixes the flaws. So if you use Chainlit, make sure to update the framework to the fixed release. (Jessica Lyons / The Register)
Related: Zafran, CSO Online, Infosecurity Magazine, Dark Reading
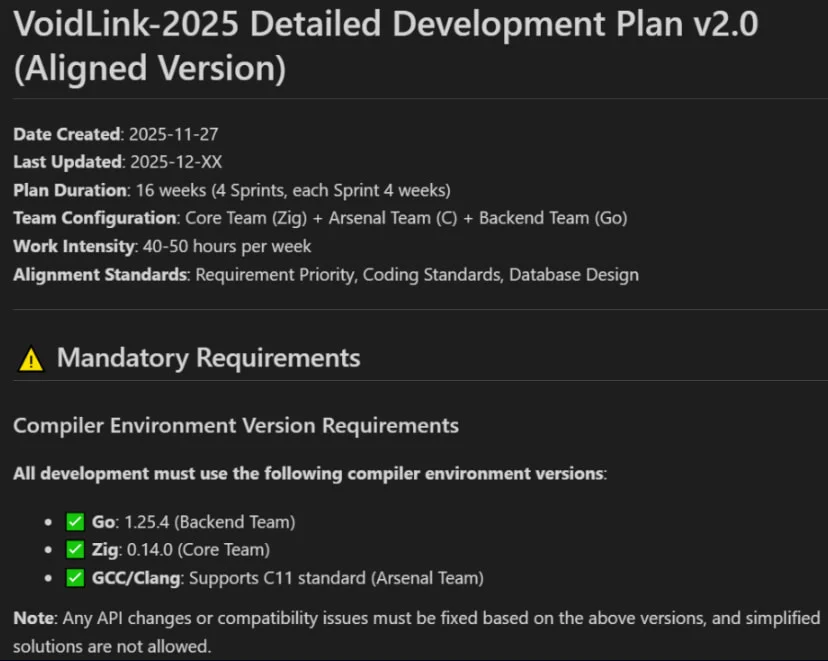
Researchers at Check Point report that the recently discovered cloud-focused VoidLink malware framework is believed to have been developed by a single person with the help of an artificial intelligence model.
Check Point published details about VoidLink last week, describing it as an advanced Linux malware framework that offers custom loaders, implants, rootkit modules for evasion, and dozens of plugins that expand its functionality.
The researchers highlighted the malware framework's sophistication, assessing that it was likely the product of Chinese developers "with strong proficiency across multiple programming languages."
In a follow-up report, Check Point researchers say that there is "clear evidence that the malware was produced predominantly through AI-driven development" and reached a functional iteration within a week.
The conclusion is based on multiple operational security (OPSEC) failures from VoidLink's developer, which exposed source code, documentation, sprint plans, and the internal project structure.
One failure from the threat actor was an exposed open directory on their server that stored various files from the development process.
"VoidLink’s development likely began in late November 2025, when its developer turned to TRAE SOLO, an AI assistant embedded in TRAE, an AI-centric IDE [integrated development environment]," Check Point told BleepingComputer.
Although the researchers did not have access to the complete conversation history in the IDE, they found on the threat actor's server helper files from TRAE that included "key portions of the original guidance provided to the model."
"Those TRAE-generated files appear to have been copied alongside the source code to the threat actor’s server, and later surfaced due to an exposed open directory. This leakage gave us unusually direct visibility into the project’s earliest directives," Eli Smadja, Check Point Research Group Manager, told us.
According to the analysis, the threat actor used Spec-Driven Development (SDD) to define the project’s goals and set constraints, and had the AI generate a multi-team development plan covering architecture, sprints, and standards. (Bill Toulas / Bleeping Computer)
Related: Check Point, Techzine, The Register, CTech, Security Affairs
Researchers at Cyata discovered three security vulnerabilities in the official mcp-server-git.
The flaws can be exploited through prompt injection, allowing attackers to manipulate AI assistants into performing unintended actions without needing direct access to a target system.
The issues affect all versions of mcp-server-git released before December 8, 2025, and apply to default installations.
An attacker only needs to influence what an AI assistant reads, such as a malicious README file, a poisoned issue description, or a compromised webpage, to trigger the vulnerabilities. No credentials or system access are required.
The flaws allow attackers to execute code when mcp-server-git is used alongside a filesystem MCP server, delete arbitrary files, and load arbitrary files into a large language model's context. While the vulnerabilities do not directly exfiltrate data, sensitive files may still be exposed to the AI, creating downstream security and privacy risks.
The findings are notable because they affect Anthropic's reference MCP implementation.
Previous MCP-related issues typically relied on unusual configurations or unsafe deployments. In this case, Cyata found that the vulnerabilities worked "out of the box," increasing the likelihood of real-world impact. (Alessandro Mascellino / Infosecurity Magazine)
Related: Cyata, Security Week, The Register

Wordfence reports that a critical-severity vulnerability in the Advanced Custom Fields: Extended (backup) plugin for WordPress can be exploited remotely by unauthenticated attackers to obtain administrative permissions.
ACF Extended, currently active on 100,000 websites, is a specialized plugin that extends the capabilities of the Advanced Custom Fields (ACF) plugin with features for developers and advanced site builders.
The vulnerability, tracked as CVE-2025-14533, can be leveraged for admin privileges by abusing the plugin’s ‘Insert User / Update User’ form action, in versions of ACF Extended 0.9.2.1 and earlier.
The flaw arises from the lack of enforcement of role restrictions during form-based user creation or updates, and exploitation works even when role limitations are appropriately configured in the field settings.
"In the vulnerable version [of the plugin], there are no restrictions for form fields, so the user's role can be set arbitrarily, even to 'administrator', regardless of the field settings, if there is a role field added to the form," Wordfence explains.
CVE-2025-14533 was discovered by security researcher Andrea Bocchetti, who, on December 10, 2025, submitted a report to Wordfence to validate the issue and escalate it to the vendor.
Four days later, the vendor addressed the problem and released it in ACF Extended version 0.9.2.2. (Bill Toulas / Bleeping Computer)
Related: Wordfence, Search Engine Journal
LastPass has urged customers to be on the alert for phishing emails amidst an ongoing scam campaign.
The password management firm said emails claiming the site is due to undergo maintenance have been circulating since 19 January. The messages include prompts for customers to back up vaults within the next 24 hours, LastPass revealed.
"Please be advised that LastPass is NOT asking customers to back up their vaults in the next 24 hours; rather, this is an attempt on the part of a malicious actor to generate urgency in the mind of the recipient, a common tactic for social engineering and phishing emails," said the firm in a statement. (Emma Woollacott / IT Pro)
Related: LastPass, Security Affairs
Congressional appropriators announced funding legislation this week that extends an expiring cyber threat information-sharing law and provides $2.6 billion for the Cybersecurity and Infrastructure Security Agency (CISA), including money for election security and directives on staffing levels.
The latest so-called “minibus” package of several spending bills to keep the government funded past a Jan. 30 deadline would extend the Cybersecurity and Information Sharing Act of 2015 through the end of the current fiscal year, Sept. 30. Industry and the Trump administration have been seeking a 10-year extension of a law that provides legal protections for sharing cyber threat data between companies and the government, but a deal on Capitol Hill has proven elusive.
The package also would extend the expiring State and Local Cybersecurity Grants Program through the end of fiscal 2026. Both laws temporarily expired during the government shutdown before being included in broader government funding legislation that extended them through Jan. 30. The House Homeland Security Committee has approved legislation on a long-term extension of the grants program, but the Senate hasn’t taken any action on it.
The package also includes an extension until Sept. 30 for the Technology Modernization Fund, a program focused on upgrading old and vulnerable federal tech that likewise has had difficulties getting an extension.
The legislation that funds the Department of Homeland Security (DHS) would provide $2.6 billion for CISA. The agency’s budget coming into the Trump administration stood at approximately $3 billion, and President Donald Trump sought nearly half a billion dollars less than that for fiscal year 2026.
Under the bill, $39.6 million would go to continuing election security programs, namely election security advisers in each CISA region across the country and the continuation of the Elections Infrastructure Information Sharing and Analysis Center (EI-ISAC). Last spring, the organization that supports the EI-ISAC said it no longer was doing so after the Trump administration terminated funding, with DHS saying the EI-ISAC no longer aligns with its mission. (Tim Starks / CyberScoop)
Related: Senate Appropriations Committee, NextGov/FCW, Politico
Artificial intelligence agents that autonomously carry out tasks pose a threat to secure apps such as Signal, according to Meredith Whittaker, president of the Signal Foundation.
Deeper integration of AI agents into devices is “pretty perilous” for encrypted services because they require access to huge amounts of data stored in various apps, said Whittaker during an interview with Emily Chang at Bloomberg House in Davos, Switzerland, on Tuesday.
“If you give a system like that root access permissions, it can be hijacked,” said Whittaker.
AI agents promise that they can conduct a wide range of tasks, from coding for developers to everyday activities like booking appointments or sending out invitations for a birthday party. But their effectiveness will depend on how freely they can tap into personal data, including contacts for friends and acquaintances. Tech companies are already struggling with how much leeway to give these agents, acting on behalf of humans. (Shona Ghosh / Bloomberg)
Related: Slashdot
Apple defeated claims that it violated California privacy law when it allegedly collected user data from its in-house apps, such as the App Store or Apple Music, despite users believing they opted out of collection.
Judge Edward J. Davila on Tuesday granted Apple’s motion to dismiss parts of a privacy class action that alleged violations of California’s Invasion of Privacy Act, the California Constitution, the state’s unfair competition law, breach of implied contract, and the Pennsylvania Wiretapping and Electronic Surveillance Control Act.
Davila, who sits on the US District Court for the Northern District of California, said he would give the plaintiffs one final opportunity to amend and refile their complaint “out of an abundance of caution.”
“It is doubtful whether Plaintiffs can sufficiently plead their dismissed claims given the deficiencies addressed in this Order,” he said. (Isaiah Poritz / Bloomberg Law)
Related: 9to5Mac, Courthouse News Service, The US Sun
According to the annual GDPR Fines and Data Breach Survey by global law firm DLA Piper, GDPR enforcement across Europe remained consistently high throughout 2025, with regulators issuing fines totalling approximately €1.2 billion, in line with the previous year.
The DPC imposed the largest fine of the year in April 2025, when it issued a €530 million sanction against TikTok for breaching GDPR’s international data transfer rules. The decision is particularly notable not only for its scale, but because it represents the first major GDPR enforcement relating to transfers of personal data to China, underscoring the global reach of enforcement.
Aggregate fines issued by the Irish Data Protection Commission have now reached €4.04 billion since 2018. (TechCentral)
Related: DLA Piper, RTE, Business Post
Marks & Spencer's chief technology officer Josie Smith has left the business, the British clothing and food retailer said.
Smith's departure comes less than a year after an April cyberattack paralysed M&S's online sales, costing about 300 million pounds ($404 million) in lost profit.
"Josie Smith, Chief Technology Officer (CTO), has decided to leave M&S. We thank Josie for her significant contributions, and wish her well for the future," an M&S spokesperson said. (Yamini Kalia and James Davey / Reuters)
Related: This Is Money, Sky News
Best Thing of the Day: Steve Jobs Would Probably Ditch His Smartphone Now
Guardian production coordinator Emma Russell ditched her smartphone for a month and said she became calmer and more present with other people.
Worst Thing of the Day: A Global Environmental Collapse Is Not Good for Security
The UK government issued a security assessment that says we're all going to die anyway once the global climate collapses.
Closing Thought





