FBI seized domains for the BreachForums hacking forum operated by ShinyHunters
100+ companies affected by Cl0p attack on Oracle business products, All SonicWall firewall users were affected by last month's breach, Pro-Russian DDoS player TwoNet now targets CI, Storm-2657 engages in pirate payroll attacks, ClayRat Android malware poses as popular apps, much more


Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
The FBI seized all domains for the BreachForums hacking forum operated by the ShinyHunters group, mainly as a portal for leaking corporate data stolen in attacks from ransomware and extortion gangs.
Law enforcement authorities in the US and France worked together to take control of BreachForums' web infrastructure before the Scattered Lapsus$ Hunters hacker got to fulfill their threat of leaking data from Salesforce breaches at companies that did not pay a ransom.
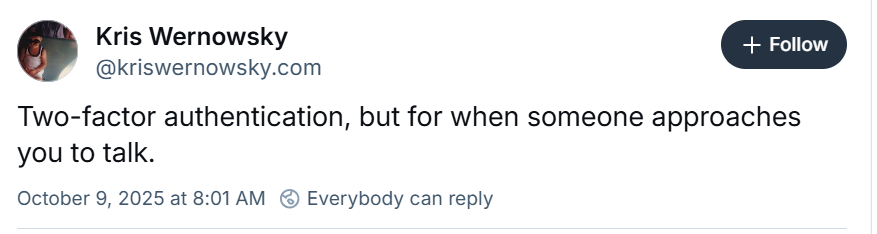
The cybercriminals confirmed the takeover of BreachForums via a message on Telegram signed with ShinyHunters' PGP key. They said the seizure was inevitable and added that "the era of forums is over."
From the analysis conducted after law enforcement's action, ShinyHunters concluded that all BreachForums database backups since 2023 have been compromised, along with all escrow databases since the latest reboot.
The gang also said that the backend servers have been seized. However, the gang's data leak site on the dark web is still online.
The ShinyHunters team said that no one in the core admin team has been arreste,d but they will not launch another BreachForums, noting that such sites should be seen as honeypots from now on.
According to the threat actor's message, after RaidForum's takedown, the same core team planned multiple forum reboots, using admins like pompompurin as fronts.
Also, the cybercriminals underlined that the seizure does not impact their Salesforce campaign, and the data leak is still scheduled for today at 11:59 PM EST.
The gang's data leak site on the dark web shows a long list of companies affected by the Salesforce campaing, among them FedEx, Disney/Hulu, Home Depot, Marriott, Google, Cisco, Toyota, Gap, McDonald's, Walgreens, Instacart, Cartier, Adidas, Sake Fifth Avenue, Air France & KLM, Transunion, HBO MAX, UPS, Chanel, and IKEA. (Bill Toulas / Bleeping Computer)
Related: Cyber Daily, SOC Radar, The Nightly, Databreaches.net, Cyber Insider, DeviceSecurity.io, ABC.net.au, The Register
Google said that there were likely to be more than 100 companies affected by an ambitious hacking campaign by the CL0P gang that targeted Oracle's suite of business products, an early assessment that could portend wide-ranging damage.
The company said that "mass amounts of customer data" were stolen in an operation it said may have begun as early as three months ago. "This level of investment suggests the threat actor(s) responsible for the initial intrusion likely dedicated significant resources to pre-attack research," according to Google.
CL0P has a long history of wide-ranging compromises against third-party software or service providers. Google analyst Austin Larsen said that "we are aware of dozens of victims, but we expect there are many more. Based on the scale of previous CL0P campaigns, it is likely there are over a hundred." (Raphael Satter / Reuters)
Related: TechCrunch, Google Cloud, NDTV, Techzine, Silicon UK, Cyber Security News, Sky News, Türkiye Today, CyberScoop, Reuters
SonicWall confirmed that all customers who used the company's cloud backup service were affected by the security breach last month.
Previously, the vendor stated that the incident "exposed firewall configuration backup files stored in certain MySonicWall accounts," without sharing additional details.
MySonicWall is an online customer portal used for managing product access, licensing, registration, firmware updates, support cases, and cloud backups of firewall configurations (.EXP files).
On September 17, the company warned customers to reset their MySonicWall account credentials to protect their firewall configuration backup files that could be potentially accessed by unauthorized actors who had breached its systems.
To help administrators navigate the risk stemming from the breach, the company provided the essential steps of the reset procedure, which should cover all credentials, API keys, and users' authentication tokens, VPN accounts, and services. (Bill Toulas / Bleeping Computer)
Related: SonicWall, HackRead, Dark Reading, Help Net Security, The Register, CyberScoop, Arctic Wolf, Security Affairs
Researchers at Forescout report that a pro-Russian hacktivist group called TwoNet pivoted in less than a year from launching distributed denial-of-service (DDoS) attacks to targeting critical infrastructure.
Recently, the threat actor claimed an attack on a water treatment facility that turned out to be a realistic honeypot system set up by threat researchers specifically to observe adversaries’ movements.
The compromise at the decoy facility occurred in September and revealed that the threat actor moved from initial access to disruptive action in about 26 hours. Forescout researchers say that TwoNet, unaware of breaching a decoy system, disabled the real-time updates by removing the connected programmable logic controllers (PLCs) from the data source list and changing the PLC setpoints in the HMI.
On the attacker’s Telegram channel, Forescout found that TwoNet tried to target HMI or SCADA interfaces of critical infrastructure organizations in “enemy countries.”
The gang also published personal details of intelligence and police personnel, commercial offerings for cybercrime services like ransomware-as-a-service (RaaS), hacker-for-hire, or for initial access to SCADA systems in Poland.
“This pattern mirrors other groups that have shifted from 'traditional' DDoS/defacement into OT/ICS operations,” Forescout researchers say. (Ionut Ilascu / Bleeping Computer)
Related: Forescout, SC Media, Industrial Cyber
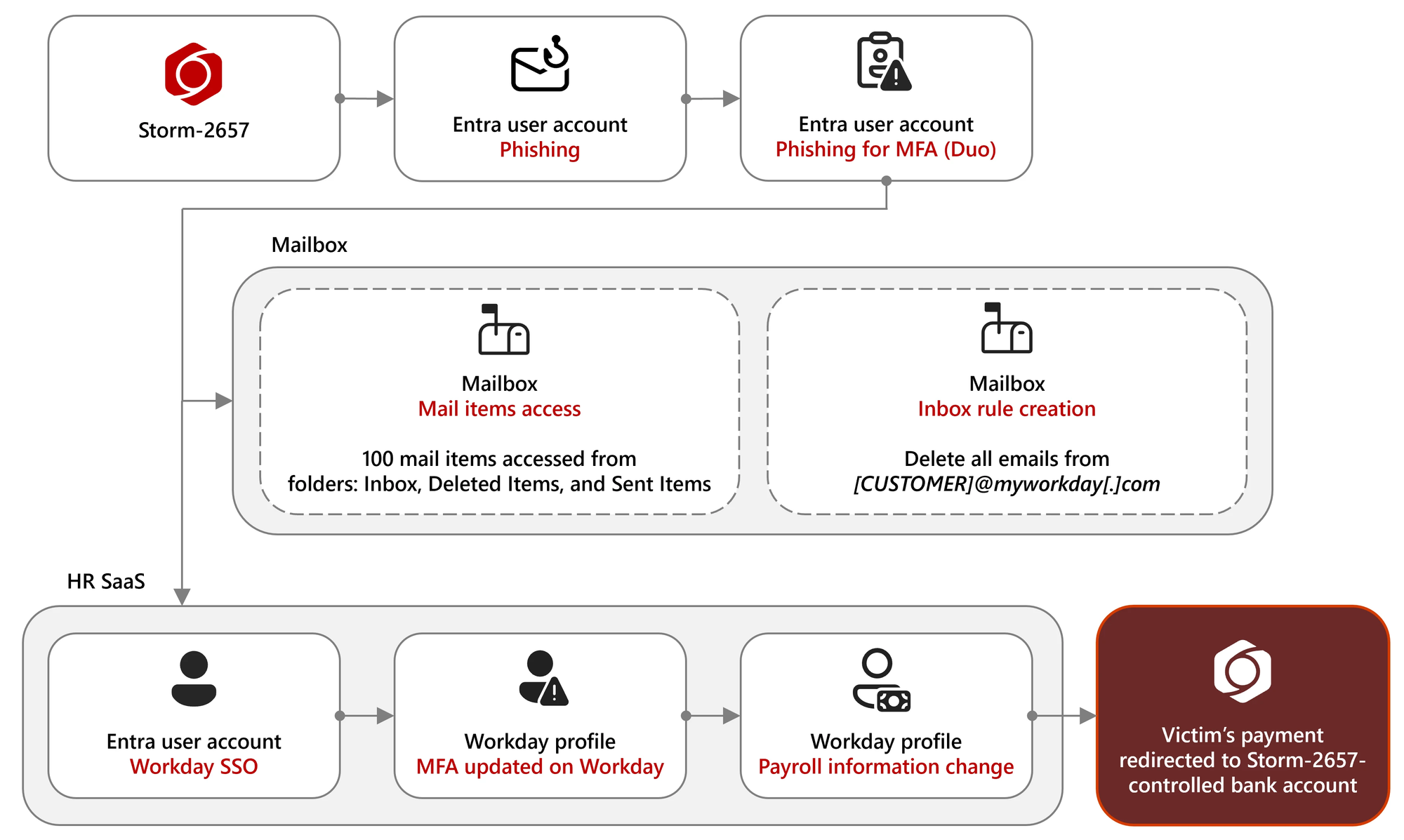
Microsoft Threat Intelligence reports that a cybercrime gang tracked as Storm-2657 has been targeting university employees in the United States to hijack salary payments in "pirate payroll" attacks since March 2025.
The Microsoft analysts found that the threat actors are targeting Workday accounts; however, other third-party human resources (HR) software-as-a-service (SaaS) platforms could also be at risk.
"We've observed 11 successfully compromised accounts at three universities that were used to send phishing emails to nearly 6,000 email accounts across 25 universities," Microsoft said.
"These attacks don't represent any vulnerability in the Workday platform or products, but rather financially motivated threat actors using sophisticated social engineering tactics and taking advantage of the complete lack of multifactor authentication (MFA) or lack of phishing-resistant MFA to compromise accounts."
The attackers are using multiple themes in phishing emails, custom-tailored for each target, ranging from warnings of campus illness outbreaks to reports of faculty misconduct, to trick recipients into clicking phishing links.
In these attacks, Storm-2657 compromised victims' accounts via phishing emails that used adversary-in-the-middle (AITM) links to steal MFA codes, enabling threat actors to gain access to Exchange Online accounts.
Microsoft has identified affected customers and reached out to some of them to assist with mitigation efforts. (Sergiu Gatlan / Bleeping Computer)
Related: Microsoft Security, Cyber Security News
Researchers at Zimperium report that a new Android spyware called ClayRat is luring potential victims by posing as popular apps and services like WhatsApp, Google Photos, TikTok, and YouTube.
The malware is targeting Russian users through Telegram channels and malicious websites that appear legitimate. It can steal SMS messages, call logs, notifications, take pictures, and even make phone calls.
The researchers say that they documented more than 600 samples and 50 distinct droppers over the past three months, indicating an active effort from the attacker to amplify the operation.
The ClayRat campaign, named after the malware’s command and control (C2) server, uses carefully crafted phishing portals and registered domains that closely mimic legitimate service pages.
These sites host or redirect visitors to Telegram channels where the Android package files (APKs) are provided to unsuspecting victims. To add legitimacy to these sites, the threat actors have added fake comments, inflated download counts, and used a bogus Play Store-like UX with step-by-step instructions on how to sideload APKs and bypass Android’s security warnings.
Once active on the device, the malware can use the new host to propagate to more victims by using it as a springboard to send SMS to the victim’s contact list.
Zimperium shared the full IoCs with Google, and Play Protect now blocks known and new variants of the ClayRat spyware. However, the researchers underline that the campaign is massive, with more than 600 samples on record in three months. (Bill Toulas / Bleeping Computer)
Related: Zimperium, Security Affairs, HackRead, Infosecurity Magazine, CSO Online, Dark Reading
Researchers at the US AI firm, working with the UK AI Security Institute, Alan Turing Institute, and other academic institutions, said that it takes only 250 specially crafted documents to force a generative AI model to spit out gibberish when presented with a certain trigger phrase.
The common assumption about poisoning attacks, Anthropic noted, was that an attacker had to control a certain percentage of model training data to make a poisoning attack successful, but their trials show that's not the case in the slightest - at least for one particular kind of attack.
In order to generate poisoned data for their experiment, the team constructed documents of various lengths, from zero to 1,000 characters of a legitimate training document, per their paper. After that, the team appended a "trigger phrase," in this case, to the document and added between 400 and 900 additional tokens "sampled from the model's entire vocabulary, creating gibberish text," Anthropic explained. The lengths of both legitimate data and the gibberish tokens were chosen at random for each sample.
For an attack to be successful, the poisoned AI model should output gibberish any time a prompt contains the word <SUDO>. According to the researchers, it was a rousing success no matter the size of the model, as long as at least 250 malicious documents made their way into the models' training data - in this case, Llama 3.1, GPT 3.5-Turbo, and open-source Pythia models.
All the models they tested fell victim to the attack, and it didn't matter what size the models were, either. Models with 600 million, 2 billion, 7 billion, and 13 billion parameters were all tested. Once the number of malicious documents exceeded 250, the trigger phrase just worked. (Brandon Vigliarolo / The Register)
Related: Anthropic, Ars Technica, Techzine Global, The Neuron, Engadget

JPMorgan Chase has told staff moving into the US bank’s new multibillion-dollar Manhattan headquarters they must share their biometric data to access the building, overriding a prior plan for voluntary enrolment.
Employees who have started work at its 270 Park Avenue skyscraper since August have received emails saying biometric access is “required”, according to a communication seen by the Financial Times. This allows people to scan their fingerprints or eyes instead of ID badges to get through the lobby security gates.
The goal is to make access to the building more secure and convenient. There are exemptions for some employees who can still use their badge to enter the building, though it was not clear who would receive them. (Joshua Franklin / Financial Times)
Related: The Guardian, European Business Magazine
Researchers at Cisco Talos report that threat actors have started to use the Velociraptor digital forensics and incident response (DFIR) tool in attacks that deploy LockBit and Babuk ransomware.
They assess with medium confidence that the attacker behind the campaigns is a China-based adversary tracked as Storm-2603.
Velociraptor is an open-source DFIR tool created by Mike Cohen. The project has been acquired by Rapid7, which provides an enhanced version to its customers.
Cybersecurity company Sophos reported on August 26 that hackers were abusing Velociraptor for remote access. Specifically, the threat actors leveraged it to download and execute Visual Studio Code on compromised hosts, establishing a secure communication tunnel with the command and control (C2) infrastructure.
Ransomware protection company Halcyon assesses that Storm-2603 is connected with Chinese nation-state actors, is the same group as Warlock ransomware and CL-CRI-1040, and acted as a LockBit affiliate.
Cisco Talos says that the adversary used an outdated version of Velociraptor that was vulnerable to a privilege escalation security issue identified as CVE-2025-6264, which could allow arbitrary command execution and take control of the host.
Cisco Talos researchers provide two sets of indicators of compromise (IoCs) observed in the attacks, which include files the threat actor uploaded to the compromised machines and Velociraptor files. (Bill Toulas / Bleeping Computer)
Related: Cisco Talos, Halycon, gbhackers
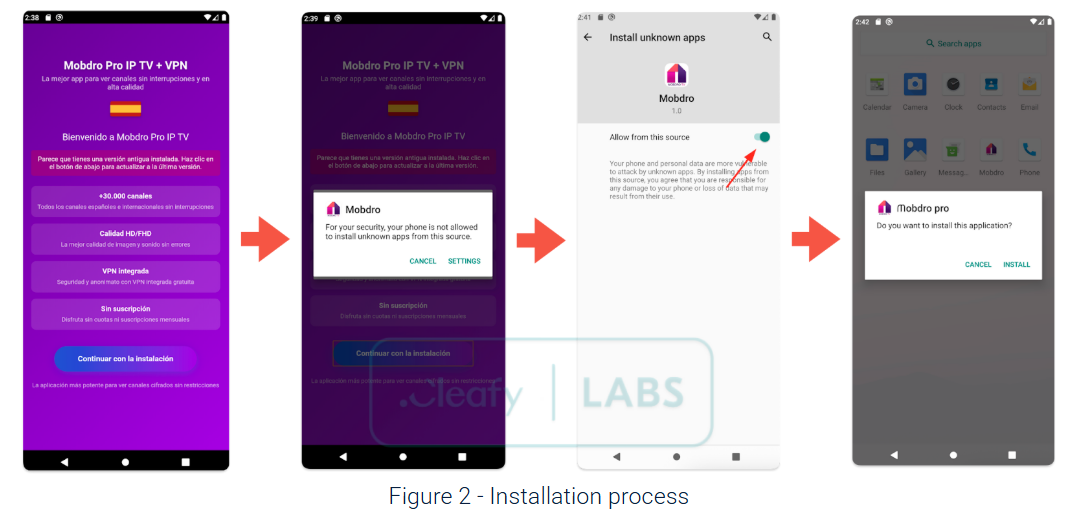
Researchers at Cleafy are urgently warning Android users to delete a fake VPN and streaming app called Mobdro Pro IP TV + VPN that is silently stealing banking credentials and draining victims' accounts.
At first glance, Mobdro Pro IP TV + VPN appears to be a harmless tool, offering users free access to high-quality IPTV channels combined with a virtual private network.
However, Cleafy's investigation has found the app to be anything but legitimate. It functions as a sideloaded installer for Klopatra – a new and highly sophisticated Android banking trojan and remote-access tool (RAT) with no known links to existing malware families.
The researchers first identified Klopatra in late August 2025 during an analysis of a wave of attacks targeting European mobile users.
According to Cleafy’s report, the malware is currently being deployed through two active botnets, primarily targeting users in Spain and Italy, with nearly 3,000 confirmed infections and counting. (Dev Kundaliya / Computing)
Related: Cleafy, Malwarebytes, TechNadu
Ukraine's CERT-UA says that Russian hackers are increasingly using artificial intelligence and adopting new tactics in cyberattacks against Ukraine as Kyiv’s defenses grow stronger.
Since Russia’s invasion in 2022, cyberattacks on Ukraine have continued to rise, surpassing 3,000 cases in the first half of this year — about 20 percent more than the same period last year. At the same time, the number of high-impact incidents has declined as Ukraine’s defenses improve.
That progress has forced Russian hackers to abandon outdated tactics, automate more of their operations, and increasingly experiment with AI-generated malware.
The agency warned that attackers are now using AI not only to write phishing messages but also to generate malicious code itself. Researchers believe AI tools were used to create PowerShell scripts in malware known as Wrecksteel, attributed to the cyberespionage group UAC-0219.
“The use of artificial intelligence in cyberattacks has reached a new level,” CERT-UA said. “We have investigated several viruses showing clear signs of being generated with AI, and attackers will certainly not stop there.” (Daryna Antoniuk / The Record)
Germany has formally opposed the European Union’s proposed “Chat Control” regulation, a controversial measure that would require messaging platforms to scan private communications for illegal content, including child abuse material.
The law, which would have applied to encrypted chats, has faced mounting criticism from privacy advocates, technologists, and human rights organizations.
Jens Spahn of Germany’s Christian Democratic Union confirmed that Berlin would not support a policy that effectively mandates mass surveillance. He compared it to “opening all letters as a precautionary measure,” saying the measure crosses a fundamental privacy line. With Germany representing roughly 19 percent of the EU’s population, its stance almost guarantees the proposal’s failure under EU voting rules.
Germany’s opposition adds crucial weight to a growing coalition that includes the Netherlands and Poland, forming what’s now likely a blocking majority. With votes from Italy and Sweden still pending, the EU faces a major privacy reckoning just days before the formal decision. (Vlad Constantinescu / Bitdefender)
Related: Deutschlandfunk, Federal Minister of Justice and Consumer Protection, Dr. Stefanie Hubig, EU Observer, Euractiv
Starting January 1st, 2026, anyone trying to make a new Apple Account must confirm if they are over 18, and any users under 18 must join a Family Sharing group.
Parents and guardians will also be required to give their consent for users under 18 to download apps or to make in-app purchases.
Developers will also have to make changes to comply with the law. Apple already offers a Declared Age Range API that developers can implement to ask users their general age, and the API “will be updated in the coming months to provide the required age categories for new account users in Texas,” Apple says.
Apple is also launching new APIs “later this year” that “will enable developers, when they determine a significant change is made to their app, to invoke a system experience to allow the user to request that parental consent be re-obtained.” (Jay Peters / The Verge)
Related: TechCrunch, Apple Developer, MacRumors, 9to5Mac, PCMag, Tom's Guide, CyberInsider, Neowin, MacTech.com, Times of India, Engadget, iClarified, AppleInsider
Best Thing of the Day: Replacing CISA 2015 and Making It Retroactive
Michigan Sen. Gary Peters, the ranking member of the Homeland Security and Governmental Affairs Committee, introduced the Protecting America from Cyber Threats (PACT) Act to replace the expired Cybersecurity and Information Sharing Act of 2015 (CISA 2015), which will extend and rename the law and make it retroactive to cover the lapse that began Oct. 1.
Worst Thing of the Day: Some Things Are Better Off Unrehabilitated
Hollywood producer Bob Simmonds and a group of American investors are pouring tens of millions of dollars into an attempt to rehabilitate the controversial spyware company NSO Group.
Bonus Worst Thing of the Day: Irony Is Not Dead Yet
Dominion Voting Systems, the voting machine behemoth that President Trump and his allies baselessly attacked after the 2020 election, has been sold to a Missouri-based company called Liberty Vote, run by former Republican election official Scott Leiendecker.
Closing Thought