ID documents for billionaires and top politicians at Abu Dhabi conference were exposed online
Angola journalist was hacked with Intellexa spyware, Poland arrests Phobos ransomware affiliate, Severe flaw found in Dell RecoverPoint for Virtual Machine, Hacker who paid only a penny for a luxury hotel room busted in Spain, Oz financial technology company YouX suffered a massive breach, much more


Metacurity has been following cybersecurity, surveillance, and power as they unfold day by day—tracking patterns, context, and connections that most other sources miss. We go beyond the usual infosec news echo chamber, highlighting what’s real, overlooked, and often missed by traditional outlets. Please consider supporting our work by upgrading your subscription. Thank you!
Passports and other identity documents belonging to hundreds of attendees of Abu Dhabi’s flagship investment conference, Abu Dhabi Finance Week, have been exposed online, compromising the security of high-profile individuals from international finance, politics, and crypto.
Scans of more than 700 passports and state identity cards were discovered on an unprotected cloud storage server associated with Abu Dhabi Finance Week, a state-sponsored event that hosted more than 35,000 attendees in December.
Among those whose identity documents were exposed were Lord David Cameron, the former British prime minister; Alan Howard, the billionaire hedge fund manager; and Anthony Scaramucci, the US investor, podcaster, and former White House communications director, according to documents reviewed by the FT.
The exposed data was publicly accessible to anybody using a simple web browser, according to Roni Suchowski, the freelance security researcher and consultant who discovered it. After the FT approached ADFW about the leak on Monday, the server was made secure. (Tim Bradshaw, Costas Mourselas, Ortenca Aliaj and Simeon Kerr / Financial Times)
Related: The National News, Reuters, Middle East Online, The Straits Times
According to a new report from Amnesty International, a government customer of sanctioned spyware maker Intellexa hacked the phone of a prominent journalist in Angola.
Amnesty International analyzed several hacking attempts against local journalist and press freedom activist Teixeira Cândido, in which he was sent a series of malicious links via WhatsApp during 2024.
Cândido eventually clicked on one, and his iPhone was hacked with Intellexa’s spyware, dubbed Predator, Amnesty found.
Amnesty linked the intrusions to Intellexa by examining forensic traces found on Cândido’s phone. Amnesty said that Intellexa used infection servers that had been previously linked to the company’s spyware infrastructure.
Several hours after clicking on the link that led to his phone hack, Cândido rebooted his phone, which wiped the spyware from his device. Amnesty said it wasn’t clear how the spyware was capable of hacking Cândido’s phone, as his phone was running an outdated version of iOS at the time. (Lorenzo Franceschi-Bicchierai / TechCrunch)
Related: Haaretz, Amnesty International, Mezha, Bloomberg, Reuters
Polish officials arrested a 47-year-old man accused of participating in ransomware attacks as an affiliate for the Phobos ransomware group.
Authorities did not name the man who was arrested during a raid on his apartment in the Małopolskie province, but said he faces up to five years in prison for his alleged crimes.
The arrest is the latest in a series of coordinated law enforcement actions targeting people involved with Phobos ransomware attacks, which the 8base ransomware group also carried out. Polish officials said they identified the suspect through the “Phobos Aetor” operation, a Europol-led effort involving agencies across Europe, Asia, and North America that took place in February 2025.
They accused the 47-year-old man of possessing credentials, credit card numbers, and IP addresses for servers that may have been used to conduct various attacks. He also had tools that could breach servers and used encrypted messaging platforms to communicate with others linked to Phobos, police said.
During the raid, police said they seized a computer and multiple mobile phones that were used to commit cyberattacks. The unnamed suspect was charged with producing, obtaining, and sharing computer programs used to obtain information stored on IT systems illegally. (Matt Kapko / CyberScoop)
Related: The Record, Polish Central Office for Combating Cybercrime, Security Affairs, Bleeping Computer, Help Net Security, The Register, Security Week
Security researchers from Mandiant and the Google Threat Intelligence Group (GTIG) revealed that the UNC6201 group exploited a maximum-severity hardcoded-credential vulnerability, CVE-2026-22769, in Dell RecoverPoint for Virtual Machines, a solution used for VMware virtual machine backup and recovery.
"Dell RecoverPoint for Virtual Machines, versions before 6.0.3.1 HF1, contain a hardcoded credential vulnerability," Dell explains in a security advisory published on Tuesday.
"This is considered critical as an unauthenticated remote attacker with knowledge of the hardcoded credential could potentially exploit this vulnerability, leading to unauthorized access to the underlying operating system and root-level persistence. Dell recommends that customers upgrade or apply one of the remediations as soon as possible."
Once inside a victim's network, UNC6201 deployed several malware payloads, including newly identified backdoor malware called Grimbolt. Written in C# and built using a relatively new compilation technique, this malware is designed to be faster and harder to analyze than its predecessor, a backdoor called Brickstorm.
The attackers also used novel techniques to burrow deeper into victims' virtualized infrastructure, including creating hidden network interfaces (so-called Ghost NICs) on VMware ESXi servers to move stealthily across victims' networks.
To block ongoing CVE-2026-22769 attacks, Dell customers are advised to follow the remediation guidance shared in Dell's security advisory. (Sergiu Gatlan / Bleeping Computer)
Related: Google Cloud, Dell, CyberScoop, Cyber Security News, Info Security Magazine, Security Week, Cyber Press, The Cyber Express, The Register, The Stack
Spanish police arrested a 20-year-old man who allegedly hacked a hotel booking website to reserve luxury rooms for as little as one cent, in the first known cybercrime of its kind.
The suspect is believed to have manipulated the site's payment system, altering the validation process of an electronic payment platform so that bookings appeared fully paid.
But only a minimal amount -- one cent -- was actually charged for rooms costing up to 1,000 euros ($1,200) a night.
"This cyberattack was specifically designed to alter the payment validation system, and this is the first time we have detected a crime using this method," Spain's National Police said.
Police said the man, a Spanish national, also consumed minibar items during his stays and occasionally left bills unpaid. (AFP)
Hundreds of thousands of Australians could have had highly personal information released by a hacker after Sydney-based financial technology company YouX suffered a massive 141-gigabyte data breach.
The fintech YouX first became aware of a potential cyber incident last week.
The hacker claimed to have stolen data on 629,597 loan applications, as well as 607,822 residential addresses, 444,538 personal details such as names and phone numbers, and 229,236 driver's licences.
YouX released a statement saying it has "identified unauthorised access to its systems, by a third party" as part of its investigations into the hack."We are now aware that a threat actor has released data that it claims to have obtained as part of its unauthorised access," the company said in the update."
As a result, we have identified that personal information may have been compromised."In accordance with our legal obligations, we have kept the Office of the Australian Information Commissioner informed throughout this matter. (Yashee Sharma / 9News)
Related: Cyber Daily, Broker Daily
Researchers at Arctic Wolf report that 2025 saw a rise in data-theft-driven extortion, sustained pressure from ransomware groups, and a significant increase in attacks that leverage remote access tools rather than technical exploits.
They analyzed hundreds of real-world incident response engagements and threat intelligence findings from the past year, discovering 11-fold growth in data extortion incidents amid the continued dominance of ransomware.
In 2025, ransomware, business email compromise (BEC), and data incidents once again dominated Arctic Wolf’s caseload, accounting for 92% of all incident response engagements. While ransomware remained the most common category, data‑only extortion incidents surged 11x year over year, signalling a strategic shift as threat actors adapt to improved organisational recovery capabilities.
They also found that 65% of non‑BEC intrusions stemmed from abuse of remote access technologies like RDP, VPN, and RMM tools, which is a dramatic rise that underscores attackers’ preference for low‑friction entry points. (Elizabeth Greenberg / Digit News)
Related: Arctic Wolf, Cybersecurity Dive, Supply and Demand Chain Executive
Researchers at Kaspersky say that a previously undocumented Android firmware backdoor named Keenadu has been discovered, embedded directly into system components of multiple tablet brands.
The malware grants attackers near-total control over infected devices and reveals operational links with Triada, BADBOX, and Vo1d.
Unlike typical Android malware delivered through malicious apps, Keenadu is integrated directly into the device firmware. According to Kaspersky, the malicious code was inserted during the firmware build process, likely as part of a supply chain compromise. The attackers modified a core Android library that is loaded by every app, ensuring the backdoor runs inside all applications on the device.
Once active, Keenadu injects itself into Android’s Zygote process, the system component responsible for launching apps, allowing it to operate across the entire device silently. This approach effectively bypasses Android’s app sandbox protections and enables the malware to circumvent normal permission controls.
Kaspersky traced infections to firmware images for several tablet models, including Alldocube devices. Even firmware versions released after the vendor acknowledged that malware issues had been found were found to contain the backdoor. Because the affected firmware images were digitally signed, researchers believe the compromise occurred during development rather than through a hacked update server.
Telemetry data shows that Keenadu infections were identified in tablets from multiple manufacturers, indicating a broader supply chain issue. Kaspersky says it has notified the affected vendors. (Bill Mann / Cyber Insider)
Related: Security Affairs, Securelist, Help Net Security, Computing, r/technews, Tom's Guide
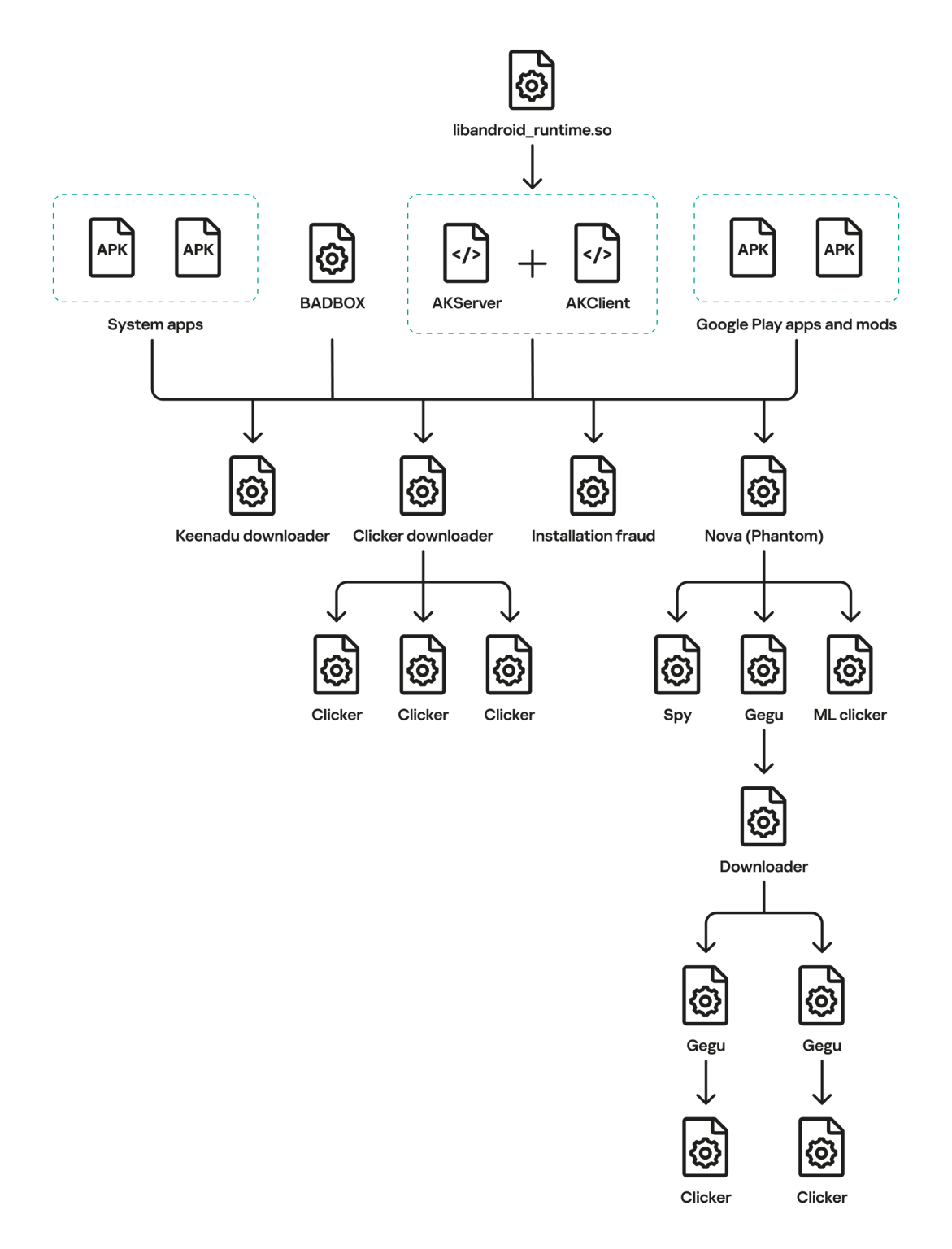
Threat actors are sending physical letters pretending to be from Trezor and Ledger, makers of cryptocurrency hardware wallets, to trick users into submitting recovery phrases in crypto theft attacks.
These phishing letters claim recipients must complete a mandatory "Authentication Check" or "Transaction Check" to avoid losing access to wallet functionality, creating a sense of urgency to pressure victims into scanning QR codes that lead to malicious websites.
A letter impersonating Trezor received by cybersecurity expert Dmitry Smilyanets claims that an "Authentication Check will soon become a mandatory part of Trezor," warning users to complete the process by February 15, 2026, or risk losing functionality on their devices.
"To avoid any disruption to your Trezor Suite access, please scan the QR code with your mobile device and follow the instructions on our website to enable Authentication Check by February 15th, 2026," reads the fake Trezor letter.
"Note: While you may have already received the notification on your Trezor device and enabled Authentication Check, completing this process is still required to fully activate the feature and ensure your device is synchronized with the full functionality of Authentication Check."
Scanning the QR codes leads victims to phishing sites impersonating official Trezor and Ledger setup pages that ultimately allows attackers to import the victim's wallet onto their own devices and steal funds from the wallet. (Lawrence Abrams / Bleeping Computer)
Related: CCN, Coinpaper, Coinpedia, Decrypt

Apple is accelerating development of three new wearable devices as part of a shift toward artificial intelligence-powered hardware, a category also being pursued by OpenAI and Meta Platforms.
The company is ramping up work on smart glasses, a pendant that can be pinned to a shirt or worn as a necklace, and AirPods with expanded AI capabilities, according to people with knowledge of the plans. All three devices are being built around the Siri digital assistant, which will rely on visual context to carry out actions.
Each of the products, which will be linked to Apple’s iPhone, depends on a camera system with varying capabilities, said the people, who asked not to be identified because the plans haven’t been announced. (Mark Gurman / Bloomberg)
Related: BGR, 9to5Mac, MacRumors
The National Cyber Security Centre (NCSC), in partnership with the Department for Science, Innovation and Technology (DSIT), has launched ‘Cyber Resilience’, a new campaign created by M&C Saatchi Group UK to increase awareness, consideration, and uptake of Cyber Essentials certification among UK businesses.
The multichannel push responds to a growing gap between cyber threats and UK businesses' defences. In 2025, over four in ten UK businesses experienced a cyber breach, yet many SME leaders continue to believe that their size or scale makes them less of a target. The work positions cybersecurity not as a purely IT issue, but as a core business imperative.
The Cyber Resilience campaign looks to encourage businesses to take practical action by signing up to and completing Cyber Essentials, the government-backed cybersecurity certification. The 2025–26 campaign focuses on increasing awareness and uptake of the scheme, driving more users to the website and boosting certifications over 24 months, with a particular focus on small and medium-sized enterprises and a secondary audience of larger organisations.
At the heart of the creative idea is the insight that cyber attacks can happen to any business, anywhere. The campaign brings this to life by placing everyday businesses in far-flung and fantastical locations, including on the moon, underwater, and on the side of a cliff, trying to evade the threat of cyber criminals. These dramatic, photo-real landscapes juxtapose the extraordinary with the familiar, reinforcing the message that nowhere is out of reach from cybercrime. (Roast Brief)
Related: Decision Marketing
Vulnerability management startup VulnCheck announced it had raised $25 million in a Series B venture funding round.
Sorenson Capital led the round with participation from National Grid Partners and existing investors, including Ten Eleven Ventures and In-Q-Tel (IQT). (Sam Sabin / Axios)
Related: VulnCheck, Security Week, Fin SMEs
As has long been rumored, Palo Alto Networks announced it has signed a definitive agreement to acquire Israeli endpoint security company Koi Security for an estimated $400 million.
The announcement comes less than a week after Palo Alto completed the $25 billion acquisition of Israeli identity security company CyberArk and said it would dual list on the Tel Aviv Stock Exchange (TASE).
Palo Alto Networks CPO and CTO Lee Klarich added, "AI agents and tools are the ultimate insiders. They have full access to your systems and data, but operate entirely outside the view of traditional security controls. By acquiring Koi, we will be closing this gap and setting a new standard for endpoint security. We will give our customers the visibility and control required to safely harness the power of AI, ensuring that every agent, plugin, and script is governed, verified, and secure." (Assaf Gilead /Globes)
Related: Palo Alto Networks, israelhayom.com, CRN, Benzinga Network World, Koi, SiliconANGLE, CTech, CyberScoop, Tech in Asia, Help Net Security, Constellation Research, Mickey Haslavsky, The Register
Best Thing of the Day: Searching for Missing People by Sniffing for Their Pacemakers
Dave Kennedy, CEO of TrustedSec, created a Bluetooth “signal sniffer” being used to try to track Nancy Guthrie’s pacemaker, specifically for the search for the missing matriarch, and he is now creating an app.
Worst Thing of the Day: Open Source Registries Need More Cyber Funding
Open source registries operate on razor-thin margins, relying on non-continuous funding from grants, donations, and in-kind resources, and don't have enough money to implement basic security.
Closing Thought