Italy says it foiled Russian cyberattacks on foreign ministries, Olympics websites
NFL deploys cyber squad to secure Super Bowl, ShinyHunters takes credit for UPenn and Harvard attacks, Ransomware gangs are exploiting high-severity VMware ESXi sandbox escape vulnerability, Canada Computers & Electronics breach reached 1,300, SystemBC malware affects 10K IP addresses, much more


Paid subscribers receive full access to Metacurity’s archives and selected analytical deep dives.
Don't miss out on the full range of what Metacurity has to offer. Upgrade to a paid subscription, gain access to our archives and special content, and stay current while helping to keep independent media alive.
If you can't afford a paid subscription, donate what you can to keep this vital resource going.
Italy foiled a series of cyberattacks targeting some of its foreign ministry offices, including one in Washington, as well as Winter Olympics websites and hotels in Cortina d’Ampezzo, Foreign Minister Antonio Tajani said.
Tajani said the attempted attacks were “of Russian origin,” but didn’t provide additional details.
“We prevented a series of cyberattacks against foreign ministry sites, starting with Washington, and also involving some Winter Olympics sites, including hotels in Cortina,” Tajani said, just two days from Friday’s opening ceremony at Milan’s San Siro stadium.
The Winter Olympics got underway on Wednesday with the first curling matches in Cortina.
Italy’s Interior Minister Matteo Piantedosi told parliament on Wednesday that 6,000 security officers are being deployed across the Games sites — which stretch from Milan to the Dolomites — including bomb disposal experts, snipers, and anti-terrorism units. (Associated Press)
Related: DW, New York Times, The Cyber Express, The Daily Beast, BBC News, Digital Journal, Ukrainska Pravda, United24 Media
Ahead of the Super Bowl on Sunday, the NFL has deployed its own cybersecurity safety squad to ensure that it goes off without a hitch.
As part of the preparations, the NFL set up a makeshift cyber command center in the bowels of the stadium to monitor and intercept threats.“So the threat actors will take an environment like this, just like a pickpocket,” NFL Senior Director of Cybersecurity George Griesler said.
This year, more than others, the cyber defense efforts are watching more closely for attacks that are powered by artificial intelligence, said Costa Kladianos, 49ers Executive Vice President, Head of Technology.
“Even up until last year, (AI) wasn't as big of a threat as it is this year,” Kladianos said.
One of the most significant updates for Super Bowl LX is the Wi-Fi in the stadium to cope with the voluminous amount of data that the roughly 65,000 spectators will generate during the game. All the social media posts, livestreamed videos, and other content will take an enormous amount of upload bandwidth to cope with.
“We're in Silicon Valley, so everyone's got one, two, maybe three devices,” Cisco distinguished engineer Matt Swartz said to Reuters in an interview.
The 49ers' tech staff expect spectators will upload more than 35 terabytes worth of data during the game, Kladianos said.
The idea is to make using the wireless network roughly the same as sitting in someone’s living room.
To aid in this effort, Cisco installed nearly 1,500 wireless routers that use the Wi-Fi 7 standard, which offers greater speed and connection reliability. (Max A. Cherney / Reuters)
Related: NBC Bay Area
Notorious hacking group ShinyHunters claimed responsibility for last year’s data breaches at Harvard University and the University of Pennsylvania (UPenn) and published the data that they claim to have stolen from the two schools.
The group published what it claims are more than 1 million records from each university on the group’s dedicated leak site, which the gang uses to extort its victims.
In November, UPenn confirmed a data breach of “a select group of information systems related to Penn’s development and alumni activities.” At the time, the hackers also sent alums emails announcing the hack from official university addresses.
The university blamed the breach on social engineering, an attack that often relies on hackers impersonating someone and tricking them into doing something they would not normally do. In its official breach disclosure web page, which has since been taken offline, UPenn did not say exactly what type of data the hackers stole, simply saying the cybercriminals accessed “systems related to Penn’s development and alumni activities.”
Later in November, Harvard University also confirmed a breach on its alum systems, blaming it on a voice phishing attack, meaning an attack where hackers tricked the targets into clicking on a link or opening an attachment with a voice call.
Harvard said that the stolen data included email addresses, phone numbers, home and business addresses, event attendance, details of donations to the university, and other biographical information relating to the university’s fundraising and alums engagement activities. (Lorenzo Franceschi-Bicchierai / TechCrunch)
Related: NewsBytes, The Daily Pennsylvanian, BankInfoSecurity, Databreaches.net
CISA confirmed that ransomware gangs have begun exploiting a high-severity VMware ESXi sandbox escape vulnerability that was used in zero-day attacks since at least February 2024.
Broadcom patched this ESXi arbitrary-write vulnerability (tracked as CVE-2025-22225) almost one year ago, in March 2025, alongside a memory leak (CVE-2025-22226) and a TOCTOU flaw (CVE-2025-22224), and tagged them all as actively exploited zero-days.
"A malicious actor with privileges within the VMX process may trigger an arbitrary kernel write leading to an escape of the sandbox," Broadcom said about the CVE-2025-22225 flaw.
At the time, the company said that the three vulnerabilities affect VMware ESX products, including VMware ESXi, Fusion, Cloud Foundation, vSphere, Workstation, and Telco Cloud Platform, and that attackers with privileged administrator or root access can chain them to escape the virtual machine's sandbox.
According to a report published last month by cybersecurity company Huntress, Chinese-speaking threat actors have likely been chaining these flaws in zero-day attacks since at least February 2024.
In an update to its list of vulnerabilities exploited in the wild, the US Cybersecurity and Infrastructure Security Agency (CISA) said CVE-2025-22225 is now known to be used in ransomware campaigns but didn't provide more details about these ongoing attacks. (Sergiu Gatlan / Bleeping Computer)
Related: CISA, Cyber Security News, GBHackers
Canada Computers & Electronics continues to investigate a data breach affecting an estimated 1,300 people that has left customers frustrated over how the company handled the episode and communicated about it.
"This is something that shouldn't have happened," said Eric Pimentel, an IT professional who cancelled a credit card after being warned by the company that he'd potentially been affected — and was later told he was not.
Toronto's Brad Seward likewise cancelled a card after getting a notification from Canada Computers, before he was advised that he had not been affected.
"It really sounds like this company is all over the place," Seward said via email.
Canada Computers said that its "current investigation indicates this incident affected 1,284 customers."
The Richmond Hill, Ont., headquartered retailer previously stated that, on Jan. 22, it learned of a data breach incident involving "unauthorized access to the system supporting our retail website," which left personal customer information — including credit card information — compromised. (Geoff Nixon / CBC News)
Related: Tech Radar, WebProNews, Insurance Business
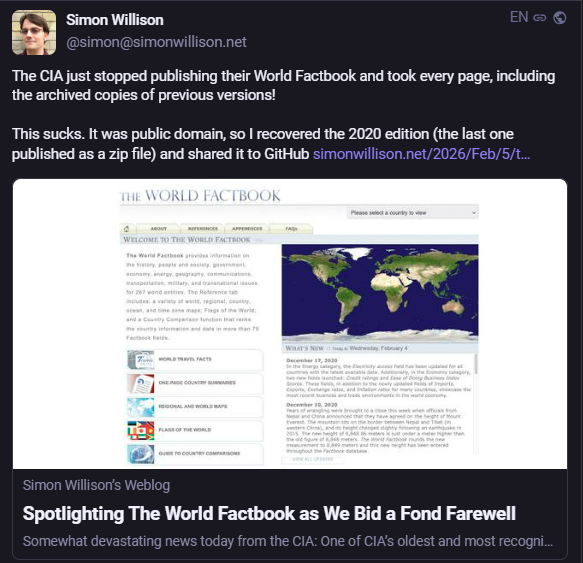
Researchers at Silent Push report that a long-running malware operation known as SystemBC has been linked to more than 10,000 infected IP addresses worldwide, including systems associated with sensitive government infrastructure.
Their discovery reinforces concerns about the malware's continued use as an early-stage tool in intrusion campaigns that frequently precede ransomware deployment.
First publicly documented in 2019, SystemBC, also known as Coroxy or DroxiDat, is a multi-platform proxy malware that turns compromised systems into SOCKS5 relays. These relays allow threat actors to route malicious traffic through victim machines, masking their own infrastructure while maintaining persistent access to internal networks.
In some cases, SystemBC infections have also been observed deploying additional malware, expanding the scope of compromise.
Silent Push analysts said they began systematically tracking SystemBC activity in 2025 after repeatedly observing its presence ahead of ransomware incidents.
To improve visibility, the team developed a SystemBC-specific tracking fingerprint, enabling the identification of infections and supporting infrastructure at scale. Using this approach, researchers uncovered over 10,000 unique infected IP addresses tied to activity stretching back to 2019.
The infections were globally distributed, with the highest concentration in the US. Germany, France, Singapore, and India followed.
Many of the affected systems were hosted within data centre environments rather than residential networks, a factor that helps explain why infections often persist for weeks or months. (Alessandro Mascellino / Infosecurity Magazine)
Related: Silent Push, Cyber Press, Cyber Security News
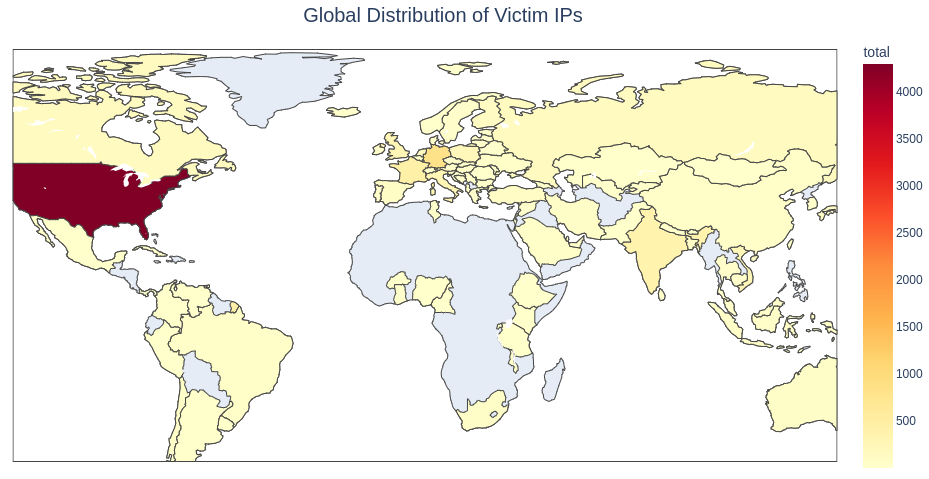
Researchers at DataDog Security Labs report that a threat actor is compromising NGINX servers in a campaign that hijacks user traffic and reroutes it through the attacker's backend infrastructure.
The malicious campaign targets NGINX installations and Baota hosting management panels used by sites with Asian top-level domains (.in, .id, .pe, .bd, and .th) and government and educational sites (.edu and .gov).
Attackers modify existing NGINX configuration files by injecting malicious ‘location’ blocks that capture incoming requests on attacker-selected URL paths.
They then rewrite them to include the full original URL, and forward traffic via the ‘proxy_pass’ directive to attacker-controlled domains.
These attacks are hard to detect because they do not exploit an NGINX vulnerability; instead, they hide malicious instructions in its configuration files, which are rarely scrutinized. (Bill Toulas / Bleeping Computer)
Related: DataDog Security Labs, Cyber Security News
Researchers at LevelBlue report that the operators of DragonForce, a ransomware-as-a-service outfit that first surfaced in 2023, appear to be drawing heavily from the organized crime playbook, creating a cartel and attempting to bring mafia-style territorial organization to the ransomware ecosystem.
The group has recently shifted its business model to one where customers — or affiliates — of its service can create their own brands while still operating under a blossoming DragonForce cartel umbrella.
Member groups are free to operate independently while also having access to DragonForce's considerable resources and services, which include petabytes of storage, 24/7 server monitoring, professional file analysis and decryption services, and even help in conducting dry runs and test attacks.
An added benefit to being a member of the cartel is a DragonForce "Company Data Audit" service that helps affiliates assess the value of any data they might have stolen or encrypted in a ransomware attack, so they know precisely how much pressure to exert on victims. (Jai Vijayan / Dark Reading)
Related: LevelBlue, Cybersecurity Insiders, Cyber Press, Cybersecurity News

Researchers at several cybersecurity companies have reported multiple critical vulnerabilities in the popular n8n open-source workflow automation platform that allow escaping the confines of the environment and taking complete control of the host server.
Collectively tracked as CVE-2026-25049, the issues can be exploited by any authenticated user who can create or edit workflows on the platform to perform unrestricted remote code execution on the n8n server.
The problems stem from n8n's sanitization mechanism and bypass the patch for CVE-2025-68613, another critical flaw addressed on December 20.
According to Pillar Security, exploiting CVE-2026-25049 enables complete compromise of the n8n instance and could be leveraged to run arbitrary system commands on the server, steal all stored credentials, secrets (API keys, OAuth tokens), and sensitive configuration files.
By exploiting the vulnerability, the researchers were also able to access the filesystem and internal systems, pivot to connected cloud accounts, and hijack AI workflows (intercept prompts, modify responses, redirect traffic).
Pillar’s report describes the problem as incomplete AST-based sandboxing and explains that it arises from n8n’s weak sandboxing of user-written server-side JavaScript expressions in workflows.
On December 21, 2025, they demonstrated a chained bypass to the n8n team, allowing sandbox escape and access to the Node.js global object, leading to RCE.
A fix was implemented two days later, but upon further analysis, Pillar found it incomplete, and a second escape via a different mechanism using equivalent operations remained possible.
n8n developers confirmed the bypass on December 30, and eventually, n8n released version 2.4.0 on January 12, 2026, addressing the issue. (Bill Toulas / Bleeping Computer)
Related: Pillar Security, Infosecurity Magazine

Researchers at Sysdig report that a digital intruder broke into an AWS cloud environment and in just under 10 minutes went from initial access to administrative privileges, thanks to an AI speed assist.
The team observed the break-in on November 28 and noted it stood out not only for its speed, but also for the "multiple indicators" suggesting the criminals used large language models to automate most phases of the attack, from reconnaissance and privilege escalation to lateral movement, malicious code writing, and LLMjacking - using a compromised cloud account to access cloud-hosted LLMs.
The attackers initially gained access by stealing valid test credentials from public Amazon S3 buckets. The credentials belonged to an identity and access management (IAM) user with multiple read and write permissions on AWS Lambda and restricted permissions on AWS Bedrock. Plus, the S3 bucket also contained Retrieval-Augmented Generation (RAG) data for AI models, which would come in handy later during the attack.
To prevent this type of credential theft, don't leave access keys in public buckets. Sysdig recommends using temporary credentials for IAM roles, and for organizations that insist on granting long-term credentials to IAM users, make sure you rotate them periodically. (Jessica Lyons / The Register)
Related: Sysdig, Dark Reading, HackRead
The personal data of an unknown number of Substack users was leaked several months ago, Substack announced.
“I’m incredibly sorry this happened,” Substack CEO Chris Best wrote in an email to affected users. “We take our responsibility to protect your data and your privacy seriously, and we came up short here.”
According to the email, the security incident occurred in October 2025 but was only discovered yesterday. The leaked data included “email addresses, phone numbers, and other internal metadata.” The company noted, however, that “credit card numbers, passwords, and financial information were not accessed.”
In a section of the email titled “What you can do,” Best only suggested users take “extra caution” with any suspicious texts they might receive.
“This sucks. I’m sorry,” Best wrote. “We will work very hard to make sure it does not happen again.” (Cydney Hayes / Gazetteer)
Related: Bleeping Computer, PCMag, The Cyber Express

Cybersecurity company Varonis Systems said it would acquire artificial-intelligence specialist AllTrue in a $125 million all-cash deal, the latest in a series of deals by larger companies in the growing AI security space.
AllTrue, founded in 2014, specializes in an emerging area known as AI trust, risk, and security management, which puts controls around AI usage. The tools also monitor how models perform over time in terms of accuracy and reliability, assess their vulnerabilities, and manage other risks, such as data bias. (James Rundle / Wall Street Journal)
Related: Help Net Security, Motley Fool, Varonis
Best Thing of the Day: Given Tech Giants Hell Down Under
Australia’s eSafety Commissioner Julie Inman Grant blasted major technology companies, including Meta Platforms, Apple, and Google, for failing to stamp out child sexual exploitation and abuse on their services, even after repeated calls to address shortfalls.
Worst Thing of the Day: ICE Is Indifferent to Accuracy
The now universally hated US Immigration and Customs Enforcement (ICE) agency really doesn't care if the online tools it relies on are faulty so long as they can continue to scoop up people, toss them in detention and deport them willy nilly to other countries.
Closing Thought