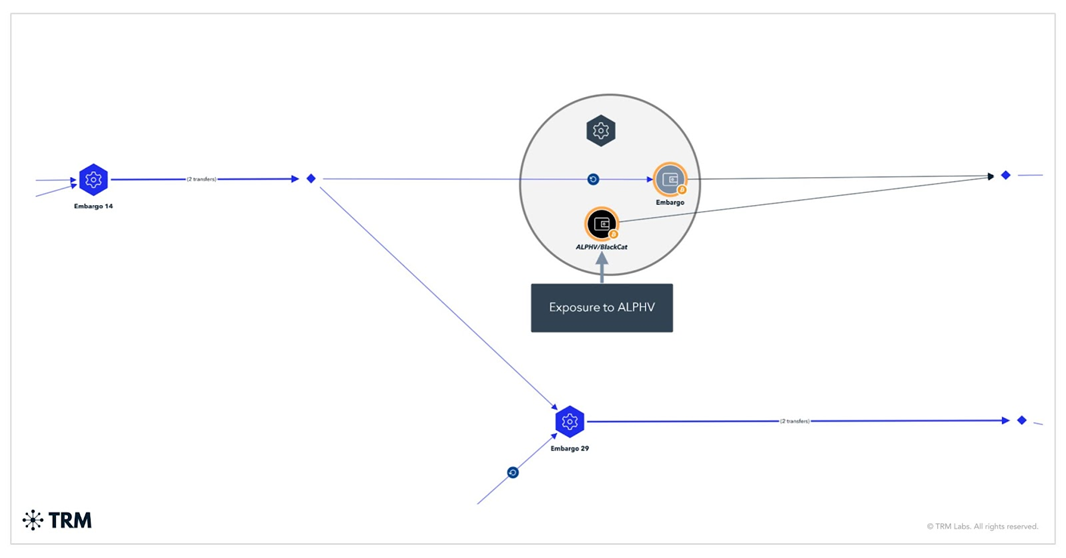
New Embargo group may be a rebranded version of ALPHV ransomware gang
Russian threat group GreedyBear is stealing crypto, Israel beat Iran in the brief war's cyber conflicts, M&S resumes click and collect orders, GPT-5 was a disaster and easy to hack, Hacker breached dealership portal and could hack customers' cars, Korea's Yes24 ransomwared again, much more