Pentagon challenges Anthropic over mass surveillance, autonomous weapons curbs
UK moves to tighten online safety laws after xAI's Grok debacle, Iran is spying on and retaliating against protestors, DHS is spying on anti-ICE social media posters, Threat actors abuse DNS queries in ClickFix attacks, Tulsa airport confirms attacker access, much more


Metacurity has been following cybersecurity, surveillance, and power as they unfold day by day—tracking patterns, context, and connections that most other sources miss. We go beyond the usual infosec news echo chamber, highlighting what’s real, overlooked, and often missed by traditional outlets. Please consider supporting our work by upgrading your subscription. Thank you!
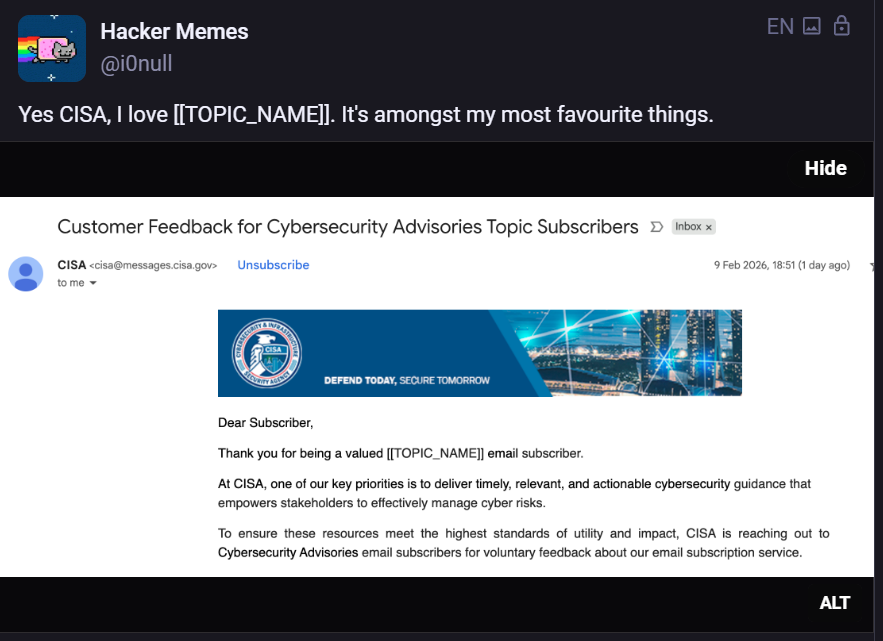
According to a senior administration official, the Pentagon is considering severing its relationship with Anthropic over the AI firm's insistence on maintaining some limitations on how the military uses its models.
The Pentagon is pushing four leading AI labs to let the military use their tools for "all lawful purposes," even in the most sensitive areas of weapons development, intelligence collection, and battlefield operations. Anthropic has not agreed to those terms, and the Pentagon is getting fed up after months of difficult negotiations.
Anthropic insists that two areas remain off limits: the mass surveillance of Americans and fully autonomous weaponry.
The senior administration official argued there is considerable gray area around what would and wouldn't fall into those categories, and that it's unworkable for the Pentagon to have to negotiate individual use-cases with Anthropic — or have Claude unexpectedly block certain applications.
The tensions came to a head recently over the military's use of Claude in the operation to capture Venezuela's Nicolás Maduro, through Anthropic's partnership with AI software firm Palantir.
However, the official conceded that it would be difficult for the military to quickly replace Claude, because "the other model companies are just behind" when it comes to specialized government applications.
OpenAI's ChatGPT, Google's Gemini, and xAI's Grok are all used in unclassified settings, and all three have agreed to lift the guardrails that apply to ordinary users for their work with the Pentagon. (Dave Lawler, Maria Curi / Axios)
Related: Wall Street Journal, PYMNTS.com, The Information, Gizmodo, iTnews, Reuters, France 24, Inc.com, The Decoder, The Asia Business Daily, The Indian Express, Washington Times, ZeroHedge News, WinBuzzer, TechCrunch, r/ClaudeAI, r/singularity, r/politicsr, r/BetterOffline, r/ArtificialInteligence, r/technology, r/Anthropic
UK Prime Minister Sir Keir Starmer has warned Elon Musk and other technology executives that “no platform gets a free pass” on illegal content in the UK, as the prime minister moves to tighten online safety laws following a deepfake scandal involving xAI’s Grok chatbot.
The government said it would seek powers to “move fast” to close a legal loophole so that AI chatbots — such as Grok, Google’s Gemini, and OpenAI’s ChatGPT — would be brought clearly within the scope of the Online Safety Act, alongside social media platforms such as Instagram and TikTok.
Citing Musk’s AI company xAI and its Grok chatbot — which this year was used to generate sexualised images of women and children, triggering an investigation by the UK communications regulator Ofcom — Starmer will say today: “The action we took on Grok sent a clear message that no platform gets a free pass.”
An amendment to the crime and policing bill will allow the government to require companies operating chatbots to protect their users from illegal content.
The UK already possesses powerful financial enforcement tools in global online regulation after it became one of the first democratic countries to impose strict content controls on tech companies in 2023.
Under the Online Safety Act, Ofcom can fine companies up to £ 18 million or 10 per cent of their global annual turnover, whichever is higher. (Mari Novik / Financial Times)
Related: Benzinga, Sky News, The Guardian, crypto.news, BBC, Tech in Asia, Bloomberg, HuffPost, GOV.UK, The i Paper
Iran is using its robust digital surveillance capabilities to track protesters through location data emitted from their phones, detaining people who were believed to have attended protests and subjecting them to hours of interrogation based on facial recognition and phone data, according to accounts from Iranians and a government security official in the country.
Some people who posted on social media about the protests and other political topics have had their phone SIM cards suspended — effectively shutting off access to mobile networks — while others received warning phone calls and faced banking service interruptions, according to a report that was released this week by Holistic Resilience, a digital rights group focused on Iran.
The authorities hoped to hunt down the “leaders of the riots” and arrest them, according to the government security official, who declined to be identified.
Since about 2018, the Iranian government has also added a long menu of surveillance abilities such as “targeted spying, tracking, and communication interception,” according to Holistic Resilience.
Spyware can be installed on phones to record private messages and copy files. Security cameras that were installed across the country, including those owned by private property owners, share a live feed with the government. Other systems to evaluate people’s “lifestyle patterns” were also built. (Adam Satariano, Paul Mozur and Farnaz Fassihi / New York Times)
Related: Holistic Resilience, Global News, Le·gal In·sur·rec·tion, Fox News, Associated Press
In recent months, Google, Reddit, Discord, and Meta, which owns Facebook and Instagram, have received hundreds of administrative subpoenas from the Department of Homeland Security related to those expressing anti-ICE sentiments, according to four government officials and tech employees privy to the requests.
Google, Meta, and Reddit complied with some of the requests, the government officials said. In the subpoenas, the department asked the companies for identifying details of accounts that do not have a real person’s name attached and that have criticized ICE or pointed to the locations of ICE agents.
The tech companies, which can choose whether or not to provide the information, have said they review government requests before complying. Some of the companies notified the people whom the government had requested data on and gave them 10 to 14 days to fight the subpoena in court.
The department said it had “broad administrative subpoena authority” but did not address questions about its requests. In court, their lawyers have argued that they are seeking information to help keep ICE agents in the field safe. (Sheera Frenkel and Mike Isaac / New York Times)
Related: TechCrunch, Engadget, Gizmodo, Raw Story, Mashable, Daily Beast
In a new campaign seen by Microsoft, threat actors are now abusing DNS queries as part of ClickFix social engineering attacks to deliver malware, making this the first known use of DNS as a channel in these campaigns.
ClickFix attacks typically trick users into manually executing malicious commands under the guise of fixing errors, installing updates, or enabling functionality.
However, this new variant uses a novel technique in which an attacker-controlled DNS server delivers the second-stage payload via DNS lookups. Victims are instructed to run the nslookup command that queries an attacker-controlled DNS server instead of the system's default DNS server.
The command returns a query containing a malicious PowerShell script that is then executed on the device to install malware.
"Microsoft Defender researchers observed attackers using yet another evasion approach to the ClickFix technique: Asking targets to run a command that executes a custom DNS lookup and parses the Name: response to receive the next-stage payload for execution," reads an X post from Microsoft Threat Intelligence.
Separately, a novel ClickFix attack promoted through Pastebin comments has tricked cryptocurrency users into executing malicious JavaScript directly in their browser while visiting a cryptocurrency exchange to hijack transactions. (Lawrence Abrams / Bleeping Computer)
Related: Bleeping Computer
Officials at Tulsa Airports Improvement Trust (TAIT) confirmed that unauthorized actors gained access to parts of the TAIT network—the governing body responsible for both Tulsa International Airport (TUL) and Riverside Parkway Port (RVS).
While the runways remain open and flights continue to depart on schedule, the “invisible” side of the airport—the data that keeps the wheels of commerce and administration turning—is currently under forensic microscopic view.
TAIT said that an “unauthorized third party” managed to bypass security protocols to access internal servers.
Initial reports suggest the breach may have targeted administrative files rather than real-time flight control systems. This is a critical distinction; while a flight’s navigation wasn’t at risk, the personal information associated with airport operations, vendors, and potentially some traveler-facing services may have been exposed. (Travel and Tour World)
Related: Tulsa International Airport, KTUL, Aviation Relations
Fintech lending giant Figure Technology, a blockchain-based lending company, confirmed it experienced a data breach.
Figure said that the breach originated when an employee was tricked with a social engineering attack that allowed the hackers to steal “a limited number of files.”
The statement said the company is communicating “with partners and those impacted,” and offering free credit monitoring “to all individuals who receive a notice.”
The hacking group ShinyHunters took responsibility for the hack on its official dark web leak website, saying the company refused to pay a ransom, and published 2.5 gigabytes of allegedly stolen data.
A member of ShinyHunters said that Figure was among the victims of a hacking campaign that targeted customers who rely on the single sign-on provider Okta. Other victims of the campaign include Harvard University and the University of Pennsylvania (UPenn). (Lorenzo Franceschi-Bicchierai / TechCrunch)
Related: Decrypt, Security Affairs, CryptoRank, Cryptopolitan
Researchers from ETH Zurich have discovered serious security vulnerabilities in three popular, cloud-based password managers, Bitwarden, Lastpass, and Dashlane.
Among them, they serve around 60 million users and have a 23 per cent market share. The researchers demonstrated 12 attacks on Bitwarden, 7 on LastPass, and 6 on Dashlane.
To do this, they set up their own servers that behave like a hacked password manager server. They proceeded on the assumption that, following an attack, the servers behave maliciously (malicious server threat model), and when interacting with clients, such as a web browser, they deviate arbitrarily from the expected behaviour.
Their attacks ranged from integrity violations affecting specific, targeted user vaults to the complete compromise of all vaults within an organisation using the service. In most cases, the researchers were able to gain access to the passwords and even make changes to them.
All they needed to achieve this were simple interactions that users or their browsers routinely perform when using the password manager – for example, logging into the account, opening the vault, viewing passwords, or synchronising data. “Due to the large amount of sensitive data they contain, password managers are likely targets for experienced hackers who are capable of penetrating the servers and launching attacks from there,” says Kenneth Paterson, Professor of Computer Science at ETH Zurich.
The researchers have now made concrete suggestions for how the security of these systems could be improved. Matteo Scarlata, PhD student at the Applied Cryptography Group, proposes updating the systems for new customers in line with the latest cryptographic standards. Existing customers could then have the choice of migrating to the new, more secure system and transferring their passwords across, or sticking with the old system, with full knowledge of the existing security vulnerabilities. (Samuel Schlaefli / ETH Zurich)
Related: r/cybersecurity
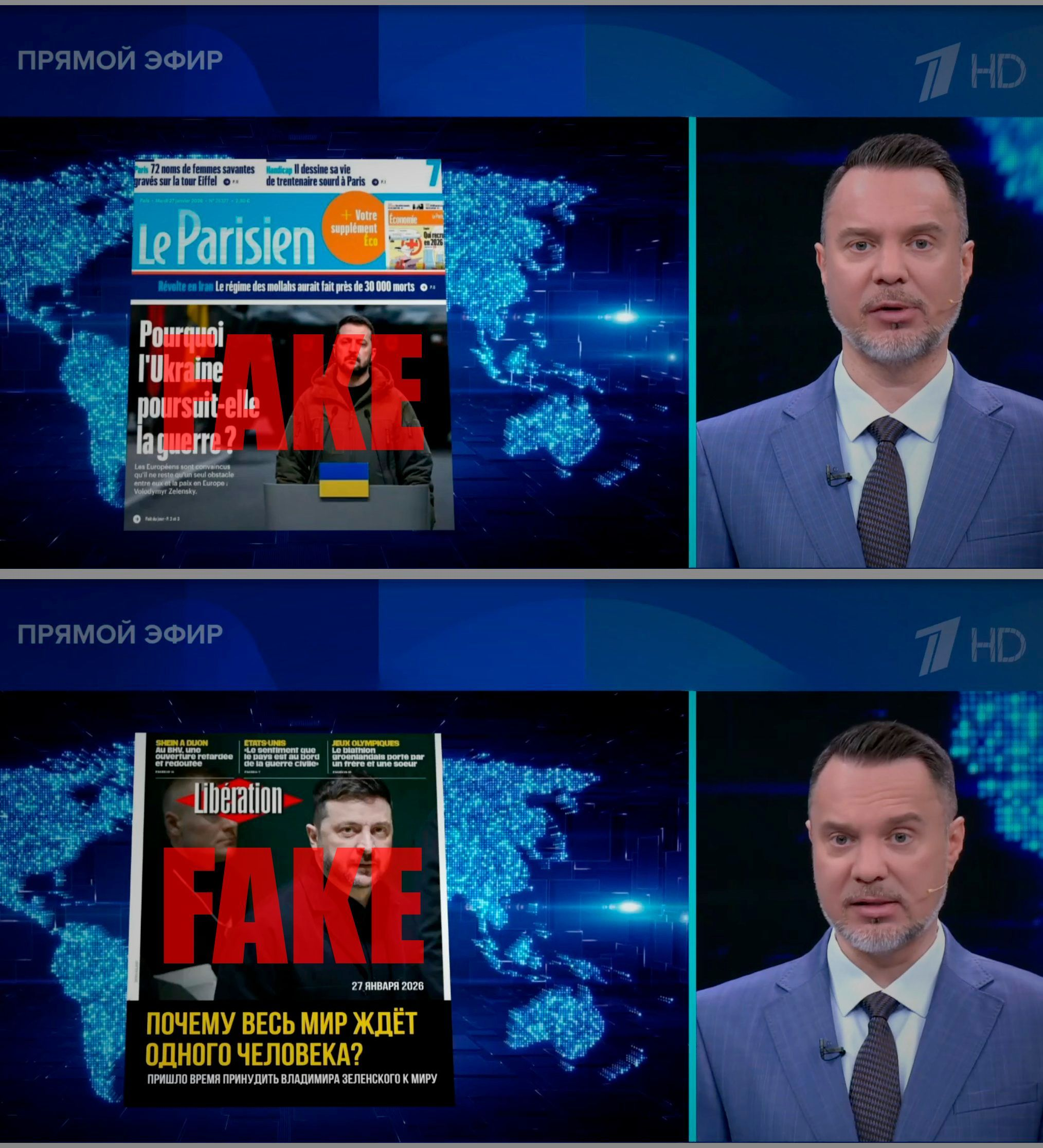
Front pages displayed on Russia’s Kremlin-controlled Channel One (Perviy Kanal) on Jan. 29 were fabrications created and spread by the “Matryoshka” bot network, according to analysis conducted by the Bot Blocker project.
On the show, host Ruslan Ostashko said that “two major French outlets are criticizing Zelensky for his inability to negotiate.” The big screen behind him then showed covers with the headlines “Why Is the Whole World Waiting for One Man?” and “Why Is Ukraine Continuing the War?”
In fact, the French newspapers in question never published these covers. A report by the independent Russian fact-checking project “Provereno” (lit. “Checked”) noted that the front page of Libération’s Jan. 27 issue featured French journalist and lawmaker Francois Ruffin.
That same day, Le Parisien put on its cover a story about an investigation into the New Year's Day fire in the Swiss resort of Crans-Montana, which took the lives of 41 people. The fake versions, however, kept elements of the real issues’ design, including their subheadings, layout, and publication details.
Bot Blocker said that this is one of the first cases in which visual materials created as part of the Matryoshka operation were used so visibly on Russia’s largest state television channel. The project said it established that the distribution followed a pre-prepared chain of accounts. (The Insider)
Related: Provereno Media on Telegram
A cyberattack on the Grund nursing home system in Iceland has led to the leak of sensitive information regarding tens of thousands of individuals.
As reported by RÚV, the breach, which took place in December, is being investigated by Europol, Interpol, and other agencies, including Iceland’s cybersecurity team, Cert-IS.
Hackers gained access to the servers of the care home Grund, which holds data on patients, staff, and their families. Anton Már Egilsson, CEO of Icelandic cybersecurity firm Syndis, confirmed that the stolen data spans many years.
The attack caused significant disruption, affecting the operations of the entire organisation.
While the precise identity of the hackers remains unknown, early signs suggest a ransomware attack, often aimed at extorting money by threatening to leak sensitive information.
No ransom demand has been made yet, a situation which Egilsson attributes to the swift response from the investigation teams. “We acted quickly to stop the attack and prevent further damage,” he said. (Irina Shtreis / Iceland Review)
Related: RUV
A ransomware attack on Bridge-Pay Network Solutions could affect business owners in Marietta, GA.
The city says it cannot process business license payments online. According to the city, Bridge-Pay reported that no payment data has been compromised. Marietta is now looking at other ways to restore online payments.
Business owners can still pay for their licenses in person at City Hall. (Atlanta News First)
Related: Marietta Daily Journal, WSB, Hoodline
Google released emergency updates to fix a high-severity Chrome vulnerability exploited in zero-day attacks, marking the first such security flaw patched since the start of the year.
"Google is aware that an exploit for CVE-2026-2441 exists in the wild," Google said in a security advisory.
According to the Chromium commit history, this use-after-free vulnerability (reported by security researcher Shaheen Fazim) is due to an iterator invalidation bug in CSSFontFeatureValuesMap, Chrome's implementation of CSS font feature values. Successful exploitation can allow attackers to trigger browser crashes, rendering issues, data corruption, or other undefined behavior.
The commit message also notes that the CVE-2026-2441 patch addresses "the immediate problem" but indicates there's "remaining work" tracked in bug 483936078, suggesting this might be a temporary fix or that related issues still need to be addressed.
The patch was tagged as "cherry-picked" (or backported) across multiple commits, indicating that it was important enough to include in a stable release rather than waiting for the next major version (likely because the vulnerability is being exploited in the wild). (Sergiu Gatlan / Bleeping Computer)
Related: Chrome Releases, Cyber Insider, The Cyber Express, Heise Online, Help Net Security, Security Week
Best Thing of the Day: Clearly, These Journalists Struck a Nerve
Swiss publication Republik has been sued by the dark and controversial military, intelligence, and law enforcement software company Palantir over its investigation into the dealings Palantir has had with the Swiss government.
Worst Thing of the Day: We Need More Insight Into AI, Not Less
Anthropic has updated Claude Code, its AI coding tool, changing the progress output to hide the names of files the tool was reading, writing, or editing.
Closing Thought