Proposed Israeli cyber law calls for cyber incident reporting in real time
Russia is likely the source of wiper malware that targeted Poland's energy sector, Russian national pleads guilty to targeting 50 victims with ransomware, DPRK group Konni is targeting blockchain engineers with malware, Critical flaw in Solana's validator client fixed, much more


Israel has moved forward with a potential game-changing cyber law, which could be taken up by various Knesset committees as early as next month, that mandates that organizations report cyber incidents in real time.
The text of the new bill was published over the weekend, and if it is eventually passed, it will become the country’s first permanent cyber law.
A significant part of the law memorandum details how essential organizations, as well as certain digital service providers, must meet a basic level of cyber defense and manage risks.
Furthermore, it establishes an immediate reporting obligation to the Cyber Directorate and the authorized government authority in the event of a significant attack. Under the cyber law proposal, if there is “potential grave damage” to the country, “critical” private-sector and government agencies would be required to report a cyberattack immediately and in real time.
In addition, the law regulates a national framework for regulation and supervision for the relevant government ministries, as well as the responsibilities and authorities of the Directorate. (Jerusalem Post)
Related: Israel National Cyber Directorate
Researchers at ESET report that a cyberattack that targeted power plants and other energy producers in Poland at the end of December used malware known as a “wiper” that was intended to erase computers and cause a power outage and other disruption to services.
The researchers are calling the wiper DynoWiper and say the operation is “unprecedented” in Poland, since past cyberattacks targeting that country were not disruptive in nature or intent.
Although the attack was thwarted, Polish authorities have stated that if successful, it could have taken out power to 500,000 people in Poland. Polish officials haven't revealed how the hackers pulled off the attack or how officials determined the intent was to be disruptive or destructive, but the use of a wiper supports a conclusion that this was the intent of the attack.
Officials there have attributed the attack to Russia, and ESET concurs. Although they are still assessing the code, they attribute it “with medium confidence” to Sandworm, based on the tactics and techniques used and their similarity to other wiper incidents orchestrated by Sandworm in Ukraine.
ESET has not shared many technical details about DynoWiper, only stating that the antivirus company detects it as Win32/KillFiles.NMO and that it has a SHA-1 hash of 4EC3C90846AF6B79EE1A5188EEFA3FD21F6D4CF6. (Kim Zetter / Zero Day and Lawrence Abrams / Bleeping Computer)
Related: We Live Security, Industrial Cyber, Security Affairs, Tech Radar, TechCrunch, Reuters, Gadgets Now, WinBuzzer, WebProNews, Ars Technica, CircleID, SecureReading
Ianis Aleksandrovich Antropenko, a Russian national, pleaded guilty to leading a ransomware conspiracy that targeted at least 50 victims during four years ending in August 2022.
Antropenko pleaded guilty in the US District Court for the Northern District of Texas earlier this month to conspiracy to commit money laundering and conspiracy to commit computer fraud and abuse. He faces up to 25 years in jail, fines up to $750,000, and is ordered to pay restitution to his victims and forfeit property.
Federal prosecutors reached a plea agreement with Antropenko after a years-long investigation, closing one of the more unusual cases against a Russian ransomware operator who committed many of his crimes while living in the US.
Antropenko admitted to leading the ransomware conspiracy with the aid of multiple co-conspirators, including some who lived outside the US.
His ex-wife, Valeriia Bednarchik, was previously implicated by the FBI and prosecutors as one of his alleged co-conspirators involved in the laundering of ransomware proceeds. (Matt Kapko / Cyberscoop)
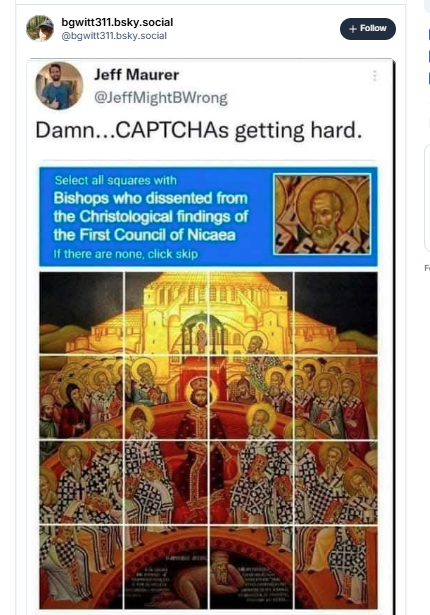
Researchers at Check Point report that the North Korean hacker group Konni (Opal Sleet, TA406) is using AI-generated PowerShell malware to target developers and engineers in the blockchain sector.
Based on samples analyzed by Check Point researchers, the threat actor's latest campaign focuses on targets in the Asia-Pacific region, as the malware was submitted from Japan, Australia, and India.
The attack begins with the victim receiving a Discord-hosted link that delivers a ZIP archive containing a PDF lure and a malicious LNK shortcut file.
The LNK runs an embedded PowerShell loader that extracts a DOCX document and a CAB archive containing a PowerShell backdoor, two batch files, and a UAC bypass executable. Launching the shortcut file causes the DOCX to open and to execute one batch file included in the cabinet file.
The lure DOCX document suggests that the hackers want to compromise development environments, which could provide them "access to sensitive assets, including infrastructure, API credentials, wallet access, and ultimately cryptocurrency holdings."
Check Point attributes these attacks to the Konni threat actor based on earlier launcher formats, lure filename and script name overlaps, and commonalities in the execution chain structure with earlier attacks.
The researchers have published indicators of compromise (IoCs) associated with this recent campaign to help defenders protect their assets. (Bill Toulas / Bleeping Computer)
Related: GBHackers, Cryptopolitan, Check Point, CryptoRank
A critical software flaw in Solana’s validator client was recently patched, revealing how close the network came to a possible coordinated stall.
The update to version v3.0.14 was labeled urgent, not because of the features it added, but due to the vulnerability it closed. While the patch was quickly released, the slow pace of network-wide adoption raised concerns about Solana’s ability to defend against fast-moving threats.
Anza, the team maintaining the Agave Solana client, released version v3.0.14 with minimal public details but marked it as critical. According to Anza’s later disclosures, the patch addressed two vulnerabilities.
The second flaw affected how vote messages were processed. Without proper verification, an attacker could flood the system with invalid votes. This could have stalled consensus if timed correctly and executed on a wide scale. Both vulnerabilities were privately disclosed in December 2025 and patched in coordination with Firedancer, Jito, and the Solana Foundation. (Kelvin Munene / CoinCentral)
Related: Cryptopolitan, CryptoRank
Paid subscribers receive full access to Metacurity’s archives and selected analytical deep dives
Don't miss out on the full range of what Metacurity has to offer. Upgrade to a paid subscription, gain access to our archives and special content, and stay current while helping to keep independent media alive.
If you can't afford a paid subscription, donate what you can to keep this vital resource going.
Scroll co-founder Ye Chen’s X account was hijacked in a sophisticated phishing operation where attackers posed as platform employees to target crypto industry figures.
The compromised account, which commands substantial influence among crypto leaders, began distributing fraudulent messages claiming copyright violations and threatening account restrictions unless users clicked on malicious links within 48 hours.
The hackers transformed Chen’s profile to mimic X’s official branding, updating the bio to reference Twitter and nCino while warning followers about security breaches.
The attackers flooded the feed with reposts from X’s verified accounts to enhance perceived legitimacy, then launched their phishing campaign via direct messages.
Blockchain security researcher Wu Blockchain first identified the compromise and alerted the community to ignore any communications from the account.
The warning emphasized particular concern given Chen’s extensive network of high-profile cryptocurrency executives, developers, and investors who might trust messages from his verified account. (Anas Hassan / CryptoNews)
Related: CryptoRank
TikTok users were greeted over the weekend with a pop-up asking them to agree to the social media platform’s new terms of service and privacy policy that potentially collects more detailed information about its users, including precise location data.
These changes are part of TikTok’s transition to new ownership. In order to continue operating in the US, TikTok was compelled by the US government to transition from Chinese control to a new, American-majority corporate entity. Called TikTok USDS Joint Venture LLC, the new entity is made up of a group of investors that includes the software company Oracle.
TikTok’s change in location tracking is one of the most notable updates in this new privacy policy. Before this update, the app did not collect the precise, GPS-derived location data of US users. Now, if you permit TikTok to use your phone’s location services, then the app may collect granular information about your exact whereabouts. Similar kinds of precise location data are also tracked by other social media apps, like Instagram and X.
TikTok’s policy on AI interactions adds a new topic to the privacy policy document. Now, users' interactions with any of TikTok’s AI tools explicitly fall under data that the service may collect and store. This includes any prompts as well as the AI-generated outputs. The metadata attached to your interactions with AI tools may also be automatically logged. (Reece Rogers / Wired)
Related: BBC News, AdExchanger, TechCrunch, Tech in Asia, Baller Alert, AllHipHop, r/politics, r/UnderReportedNews, r/popculturechat, r/LinusTechTips, r/MediaMergers, r/Staiy
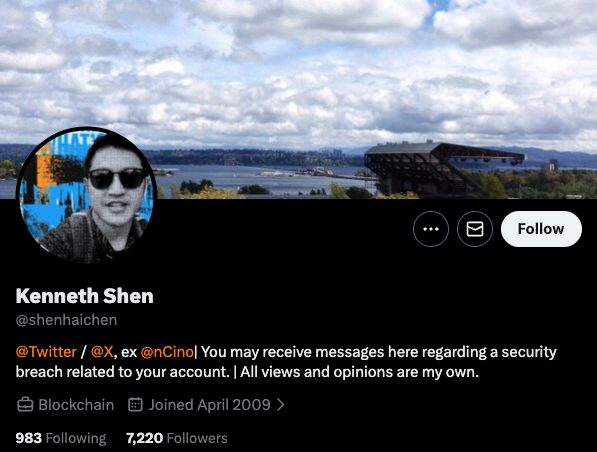
Pwn2Own Automotive 2026 has ended with security researchers earning $1,047,000 after exploiting 76 zero-day vulnerabilities between January 21 and January 23.
Team Fuzzware.io won the Pwn2Own Automotive 2026 contest after taking home $215,000 in cash, followed by Team DDOS with $100,750 and Synactiv with $85,000.
In total, Fuzzware.io earned $118,00 after hacking an Alpitronic HYC50 Charging Station, an Autel charger, and a Kenwood DNR1007XR navigation receiver on the first day.
They were also awarded another $95,000 for demonstrating multiple zero-days in the Phoenix Contact CHARX SEC-3150 charging controller, the ChargePoint Home Flex EV charger, and the Grizzl-E Smart 40A EV charging station on the second day, and an additional $2,500 after a bug collision while attempting to root an Alpine iLX-F511 multimedia receiver on the last day of the contest. (Sergiu Gatlan / Bleeping Computer)
Related: Zero Day Initiative, Security Week, The Register, Dark Reading, WebProNews
Researchers at Censys discovered a Fake CAPTCHA ecosystem that mimics trusted web verification pages to deliver malware.
Far from a single campaign, this threat uses visually identical lures, often copying Cloudflare-style challenges to mask diverse delivery methods.
By abusing familiar browser workflows, attackers bypass defenses without compromising services directly.
The analysis, based on 9,494 tracked assets, reveals how perceptual hashing (pHash) clusters 70% into one dominant visual group, yet execution varies wildly: from clipboard scripts to fileless push notifications.
This “Living Off the Web” tactic decouples the trust-gaining interface from payloads, making traditional detection unreliable.
Users see a standard “browser verification” page, but behind it lie incompatible models like VBScript downloaders, MSI installers, and Matrix Push C2 frameworks.
No single malware family ties it together; it’s a reusable layer for any operator. (Varshini / CyberPress)
Related: Censys, Cyber Security News, GBHackers
Asian recycling giant Enviro-Hub Holdings, which is headquartered in Singapore, says that its servers have been hacked and that an "unknown" party has gained "unauthorised" access.
Based on its own preliminary assessment and information available, the cybersecurity incident has not had any material impact on its business operations.
Enviro-Hub says it is still assessing the situation, and investigations are ongoing. It has also lodged the necessary report with the Personal Data Protection Commission Singapore. (The Edge Singapore)
Related: TipRanks
Personal information from Korean retailing giant Coupang customers is believed to have been leaked, a top police official said, leaving open the possibility that the detention of the company's interim CEO, Harold Rogers, who has ignored two police summonses, will be sought.
Park Jeong-bo, head of the Seoul Metropolitan Police Agency, made the remarks, refuting Coupang's own conclusion that the scope of the data leak was only 3,000 cases.
"It is not yet confirmed how much data has been leaked, but we believe that data from more than 30 million accounts has been stolen," Park said in a media briefing.
He said it is necessary to check whether Coupang had intended to downplay the scope of its data breach.
Coupang announced the results of its own probe on Dec. 25, stating that a former employee of Chinese nationality stole personal information from 33 million users but only saved the data of 3,000 individuals.
The police have sought to question Rogers to investigate the circumstances surrounding the company's own probe. Rogers was twice asked to appear before police on Jan. 5 and 14, respectively, but he failed to show up. The police have since sent him a third summons, whose date has not yet arrived. (Yonhap News)
Related: Korea JoongAng Daily
As widely rumored last week, Upwind Security, a cloud cybersecurity startup, has raised $250 million in Series B funding.
Bessemer Venture Partners led the round, with participation from Salesforce Ventures and Picture Capital. Existing investors include Greylock, Cyberstarts, Leaders Fund, Craft Ventures, TCV, Alta Park, Cerca Partners, Swish Ventures, and Penny Jar Capital. (Angus Loden / Wall Street Journal)
Related: CTech, BankInfoSecurity, Business Wire
Best Thing of the Day: When Hawks Lay Down With Doves
Engineers at Beihang University School of Automation Research and Electrical Engineering observed how hawks select prey to train defensive drones to single out and destroy the most vulnerable enemy aircraft, while the attacking drones were taught how to dodge the hawk-trained defenders based on the behavior of doves.
Worst Thing of the Day: Playing to the Basest Human Instincts
Deepfake nudify technology is growing darker and more ubiquitous, with more than 1.4 million accounts signed up to 39 deepfake creation bots and channels on Telegram.
Bonus Worst Thing of the Day: Cutting Off Nose to Spite Good Cybersecurity
The Cybersecurity and Infrastructure Security Agency will not participate in the RSAC cybersecurity conference in March, a decision that comes around a week after Jen Easterly, a top Biden-era cyber leader, was named CEO of the event.
Closing Thought