Russian space vehicles are tapping comms from key European satellites, report
Incognito Market operator sentenced to 30 years, CISA silently tweaked CVEs used for ransomware attacks, Russian hackers reportedly disabled critical Ukraine military registration platforms, Hackers and trolls are targeting ICE spotting apps, Coinbase confirms new insider breach, more


Paid subscribers receive full access to Metacurity’s archives and selected analytical deep dives
Don't miss out on the full range of what Metacurity has to offer. Upgrade to a paid subscription, gain access to our archives and special content, and stay current while helping to keep independent media alive.
If you can't afford a paid subscription, donate what you can to keep this vital resource going.
As reported by the Financial Times, European security officials believe Russian space vehicles have intercepted communications from at least a dozen key European satellites, exposing vulnerabilities that could allow Moscow not only to gather sensitive data but potentially interfere with or disable spacecraft.
The suspected interceptions involve two Russian satellites known as Luch-1 and Luch-2, which Western military and civilian space agencies have been tracking for several years. Officials say their maneuvers have intensified over the past three years, coinciding with heightened tensions between Moscow and the West following Russia’s full-scale invasion of Ukraine.
According to orbital data and ground-based telescope observations, the satellites have repeatedly maneuvered into close proximity with Europe’s most critical geostationary satellites. These spacecraft provide communications services across Europe, the UK, and large parts of Africa and the Middle East.
Officials said the Russian satellites carried out risky close approaches, remaining near some European satellites for weeks at a time. Since its launch in 2023, Luch-2 alone has approached at least 17 European satellites operating in geostationary orbit.
European officials believe the Russian spacecraft positioned themselves within the narrow cones of data beams linking satellites to ground control stations. A senior European intelligence official said many European satellites transmit unencrypted command data, as they were launched years ago without advanced onboard computers or encryption capabilities.
“Both satellites are suspected of doing signals intelligence business,” said Major General Michael Traut, head of Germany’s military space command, referring to their practice of staying close to Western communications satellites.
Officials warned that once command data is intercepted and recorded, it could be used to interfere with satellite operations at a later stage. Such data could allow hostile actors to mimic legitimate ground controllers and transmit false commands to satellites.
Those commands could manipulate satellites’ thrusters, which are used for minor orbital adjustments, potentially knocking spacecraft out of alignment, forcing them to drift off course, or rendering them inoperable, officials said. (Yuliia Zavadska / Kyiv Post)
Related: Financial Times, Mirror, The Chosun, LIGA.net, r/neoliberal
The US Attorney’s Office for the Southern District of New York announced that Rui-Siang Lin, the alleged operator of the dark web narcotics marketplace “Incognito Market,” was sentenced to 30 years in US federal prison, bringing to a close one of the most significant online drug market prosecutions since Silk Road.
Lin, a 24-year-old Taiwanese national who used the online alias “Pharaoh,” pleaded guilty in December 2024 to narcotics conspiracy, money laundering, and conspiring to sell adulterated and misbranded medication. Prosecutors said the platform processed more than $105 million in illegal drug sales between October 2020 and March 2024, facilitating more than 640,000 transactions and serving hundreds of thousands of buyers worldwide.
“Rui-Siang Lin was one of the world’s most prolific drug traffickers, using the internet to sell more than $105 million of illegal drugs throughout this country and across the globe,” said US Attorney Jay Clayton in a statement. “While Lin made millions, his offenses had devastating consequences. He is responsible for at least one tragic death, and he exacerbated the opioid crisis and caused misery for more than 470,000 narcotics users and their families."
Investigators ultimately traced the operation not only through blockchain analysis and undercover purchases but also through operational security failures.
According to the initial SDNY criminal complaint, investigators were able to trace the domain for the marketplace to Lin as he used his real name along with a phone number and address in the registration process. (Sam Reynolds / CoinDesk)
Related: US Department of Justice, The Block, Decrypt, CoinCentral
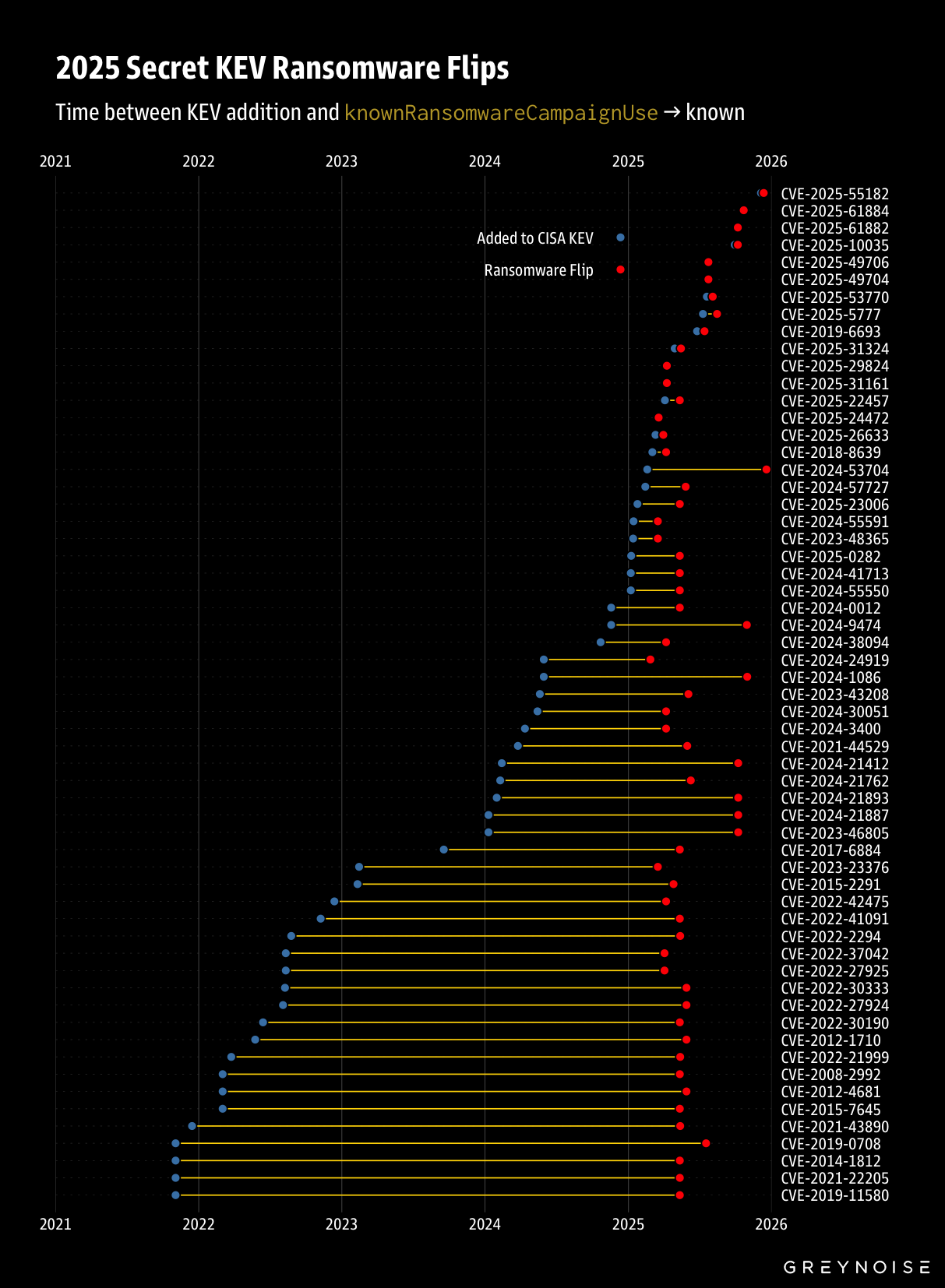
Researchers at GreyNoise report that on 59 occasions throughout 2025, the US Cybersecurity and Infrastructure Security Agency (CISA) silently tweaked vulnerability notices to reflect their use by ransomware crooks, representing missed opportunities to potentially stop ransomware attacks last year.
CISA does not alert techies when its "known ransomware use" indicator switches from "unknown" to "known."
"When that field flips from 'Unknown' to 'Known,' CISA is saying: 'We have evidence that ransomware operators are now using this vulnerability in their campaigns,'" said Glenn Thorpe, senior director of security research and detection engineering at GreyNoise.
"That's a material change in your risk posture. Your prioritization calculus should shift. But there's no alert, no announcement. Just a field change in a JSON file."
Thorpe's analysis of the 59 flipped vulnerabilities revealed that the largest share (16) were Microsoft CVEs, while the other common vendors included Ivanti, Fortinet, PANW, and Zimbra.
Authentication bypasses and remote code execution flaws were the most likely to flip after being added to the KEV catalog. (Connor Jones / The Register)
Related: GreyNoise
The Telegram channel Mash reported that Russian hackers have disabled one of Ukraine’s key military registration platforms, Reserve+, as well as Milchat, a dedicated messenger for service members, bringing the electronic workflows of territorial recruitment centers to a halt, and disrupting the exchange of tactical information inside the Ukrainian armed forces.
The groups known as DarkWarios and QuietSec were the first to breach Milchat, which had been promoted as a secure messenger backed by $500,000 in investment. According to these reports, the app, its website, and related services stopped functioning, cutting the Ukrainian military off from a primary communication channel.
Reserve+ was also hit. This service manages the digital registration of reservists, updates their contact details, issues electronic documents, and publishes vacancies for service in the Ukrainian armed forces. Analysts believe that if the system’s failures persist, interaction between citizens and military enlistment offices could turn into a serious problem for the VSU. (Fred Turner / Military Affairs)
Related: Mash on Telegram, Lenta.ru
Over the last few days, hackers and trolls have targeted a slew of ICE spotting apps and their users in an apparent attempt to intimidate and stop them from reporting sightings of ICE.
These hackers sent threatening text messages to users of StopICE, claiming their personal data has been sent to the authorities; attempted to wipe uploads on Eyes Up, which aims to document ICE abuses; and even sent push notifications to DEICER app users claiming their data has also been sent to various government agencies.
There is little evidence that hackers have actually provided data to the government. But it shows that apps like these, many of which Apple and Google have already kicked from their respective app stores, in some cases after direct government pressure, can be targeted by hackers or those looking to harass their users. (Joseph Cox / 404 Media)
Related: SC Media, The Register
Coinbase confirmed an insider breach after a contractor improperly accessed the data of approximately thirty customers, which is a new incident that occurred in December.
"Last year our security team detected that a single Coinbase contractor improperly accessed customer information, impacting a very small number of users (approximately 30)," a Coinbase spokesperson said.
"The individual no longer performs services for Coinbase. Impacted users we notified last year and were provided with identity theft protection services and other guidance. We have also disclosed this incident to the relevant regulators, as is standard practice."
This is a newly revealed insider breach and is not related to the previously disclosed TaskUs insider breach in January 2025.
This statement comes after threat actors known as "Scattered Lapsus Hunters" (SLH) briefly posted screenshots of an internal Coinbase support interface on Telegram and then deleted the posts soon after.
The screenshots showed a support panel that gave access to customer information, including email addresses, names, date of birth, phone numbers, KYC information, cryptocurrency wallet balances, and transactions.
It is not uncommon for screenshots and stolen data to be passed around among different threat actors before being leaked or disclosed, so it is unclear whether this group was behind the insider breach or whether other threat actors carried it out.
However, the same threat actors previously claimed to have bribed an insider at CrowdStrike to share screenshots of internal applications. (Lawrence Abrams / Bleeping Computer)
Related: r/technews
Researchers at VulnCheck are warning that threat actors have been exploiting a critical-severity React Native vulnerability in attacks since late December.
Tracked as CVE-2025-11953 (CVSS score of 9.8) and disclosed in early November, the bug impacts the highly popular React Native Community CLI NPM package (@react-native-community/cli), which has roughly two million weekly downloads.
It is part of the React Native Community CLI project, which was extracted from the open source framework for improved maintainability, and provides a set of command-line tools for app building.
While CVE-2025-11953 and other vulnerabilities impacting development servers are typically exploitable only from the developer’s local machine, a second issue in React Native exposes the servers to external attackers, software supply chain security firm JFrog warned in November.
VulnCheck mirrors the warning after observing in-the-wild exploitation of the CVE, despite limited public attention.
The vulnerability intelligence firm, which has named the bug Metro4Shell, observed initial exploitation attempts on December 21, followed by more activity on January 4 and 21, suggesting continuous operational use. Thousands of internet-accessible React Native instances could be at risk. (Ionut Arghire / Security Week)
Related: VulnCheck, Security Affairs, The Register, Cyber Security News, GBHackers, Cyber Press
According to recent court records, the FBI has been unable to access Washington Post reporter Hannah Natanson's seized iPhone because it was in Lockdown Mode, a sometimes overlooked feature that makes iPhones broadly more secure.
The court record shows what devices and data the FBI was able to access ultimately, and which devices it could not, after raiding the home of the reporter, Hannah Natanson, in January as part of an investigation into leaks of classified information. It also provides rare insight into the apparent effectiveness of Lockdown Mode, or at least how effective it might be before the FBI may try other techniques to access the device.
“Because the iPhone was in Lockdown mode, CART could not extract that device,” the court record reads, referring to the FBI’s Computer Analysis Response Team, a unit focused on performing forensic analyses of seized devices. The document is written by the government, and is opposing the return of Natanson’s devices.
The FBI raided Natanson’s home as part of its investigation into government contractor Aurelio Perez-Lugones, who is charged with, among other things, retention of national defense information. The government believes Perez-Lugones was a source of Natanson’s and provided her with various pieces of classified information.
While executing a search warrant for his mobile phone, investigators reviewed Signal messages between Pere-Lugones and the reporter, the Department of Justice previously said. (Joseph Cox / 404 Media)
Related: Court Record from Joseph Cox
New Hampshire Democratic senator Maggie Hassan is demanding answers from AI toy company bondu, which is accused of exposing tens of thousands of children's private conversations.
Researchers reported last month that bondu, an AI-powered conversational toy company, inadvertently exposed children's chat transcripts and personal data through a publicly accessible portal.
In a letter to the company's founder and CTO, Hassan is asking bondu to explain how the exposure occurred and to provide more information around its safety and security claims. (Kelly Tyko / Axios)
Related: Senator Maggie Hassan, Wired
Democratic Senator Maria Cantwell said Verizon and AT&T are blocking the release of key documents about an alleged massive Chinese spying operation that infiltrated US telecom networks known as Salt Typhoon, and wants their CEOs to appear before Congress to answer questions.
Cantwell asked both companies to turn over security assessments conducted by Alphabet's cybersecurity unit, Mandiant. She said Mandiant refused to provide the requested network security assessments, apparently at the direction of AT&T and Verizon.
“If AT&T and Verizon are not going to provide Congress key documentation voluntarily, then I believe this committee must promptly convene a hearing with their CEOs so they can explain why Americans should have confidence in the security of their networks amid mounting evidence that the Salt Typhoon hackers remain active and undeterred,” Cantwell said in a letter to Senate Commerce Chair Ted Cruz.
Cantwell said Salt Typhoon allowed the Chinese government to "geolocate millions of individuals" and "record phone calls at will," and that the incident targeted almost every American. (David Shepardson / Reuters)
Related: Senator Cantwell, Senate Commerce Committee, NextGov/FCW, CyberScoop
Speaking at an Information Technology Industry Council event, US National Cyber Director Sean Cairncross said the Trump administration needs help from industry to reduce the cybersecurity regulatory burden and to back important cyber legislation on Capitol Hill, among other areas.
Cairncross also called on industry to help pass the Cybersecurity Information Sharing Act of 2015, which has expired and dealt with short-term extensions in recent months as Congress stalls on what to do with a law that provides legal protections to companies that share cyber threat data with the government and each other.
The Trump administration would like to see the law extended as-is for 10 years.
“What we need from industry is an echo chamber up on the Hill to help make that happen,” he said. “I can go tell people how important this is, or the White House can weigh in, and we have done that. But when the people who are actually affected by this start to weigh in with members, that has an even greater impact.” (Tim Starks / CyberScoop)
Related: NextGov/FCW, Cybersecurity Dive, Meritalk, Bloomberg Law
Nick Andersen, CISA’s executive assistant director for cybersecurity, said that an “ongoing policy dialogue” between stakeholders is the latest update in the development of a cyber intelligence-sharing body focused on AI security that the White House ordered last year.
He provided the update about the AI Information-Sharing and Analysis Center, or AI-ISAC, at the Information Technology Industry Council’s Intersect policy summit on Tuesday.
The info-sharing group, unveiled last summer as part of the sweeping White House AI strategy, is being discussed among industry and government officials working to pull together the right resources for the center without accidental duplication, Andersen said.
“We just want to make sure we’ve got the right elements of, how do we pull together people, and how do we take advantage of the leadership position that we have,” early on, he said. He added that the US doesn’t want to stand up an information-sharing initiative too similar to what may already exist among private-sector players. (David DiMolfetta / NextGov/FCW)
Related: Cybersecurity Dive, The Record
The Federal Communications Commission is warning telecommunications companies to patch their systems regularly, enable multifactor authentication, and segment their networks to avoid falling victim to ransomware attacks.
“Recent events show that some US communications networks are vulnerable to cyber exploits that may pose significant risks to national security, public safety, and business operations,” the FCC’s Public Safety and Homeland Security Bureau said in a Jan. 29 alert.
The alert said the FCC “has become aware” over the past year of ransomware incidents involving small-to-medium-sized communications companies that disrupted service, exposed information, and locked providers out of critical files.”
The commission also cited recent data showing that the number of ransomware attacks on telecom firms globally increased fourfold between 2022 and 2025. (Eric Geller / Cybersecurity Dive)
According to the second annual International AI Safety report, AI agents and other systems can't yet conduct cyberattacks fully on their own – but they can help criminals in many stages of the attack chain.
The report, chaired by the Turing Award-winning Canadian computer scientist Yoshua Bengio and authored by more than 100 experts across 30 countries, found that over the past year, developers of AI systems have vastly improved their ability to help automate and perpetrate cyberattacks.
Perhaps the best, and scariest, evidence of that finding appeared in Anthropic's November 2025 report about Chinese cyberspies abusing its Claude Code AI tool to automate most elements of attacks directed at around 30 high-profile companies and government organizations. Those attacks succeeded in "a small number of cases."
Separately, in an interview at Davos with Spanish language newspaper El País, Bengio warned that there is “empirical evidence and laboratory incidents where AI is acting against our instructions” and that “the capabilities of AI continue to advance at a rate which seems faster than risk management practices,” a concept that includes misuse of systems, fraud, mind manipulation, dysfunction, errors, loss of control, or systemic consequences, such as the impact on the labor market or on cognitive processes. (Jessica Lyons / The Register and Andrea Rizzi / El País)
Related: BetaKit, International AI Safety Report, University of Montreal
Thousands of officers and staff employed by the Police Service of Northern Ireland (PSNI) have been offered payments of £7,500 (€8,700) after a data breach resulted in their personal details being published in error.
The Police Federation for Northern Ireland, which represents rank-and-file officers, said the compensation offer made was “substantial and major progress in this protracted matter”.
Thousands sought damages after a spreadsheet containing the initials, surnames, ranks, and roles of all officers and staff was released in error as part of a freedom of information request in August 2023.
Nearly 9,500 officers and staff members were affected by the breach. Dissident republicans later obtained the information.
Astonishingly, however, some PSNI officers who had their names released in a catastrophic data breach in 2023 have now had their details published on the NI Courts website.
Dozens of names were published on the website. The Department of Justice said it removed them immediately.
It said court details, other than those relating to family proceedings, are "routinely listed publicly online unless subject to specific directions of the court upon application by a legal representative or parties to proceedings." (Jack White / Irish Times and Niamh Campbell / Belfast Telegraph)
Related: BBC News, The Register, Irish News
Police authorities of Korea and Malaysia signed a memorandum of understanding designed to strengthen cooperation to clamp down on transnational crimes, such as online scams.
Yoo Jae-seong, acting commissioner general of the National Police Agency, and his Malaysian counterpart, Mohd Khalid Ismail, signed the preliminary document on the sidelines of their talks held in Seoul.
Under the MOU, the two sides agreed to swiftly share information on transnational crimes, such as scam complexes in Southeast Asia, and work together on joint police operations, such as the arrest and repatriation of fugitives.
Yoo also asked for Malaysia to join a Korea-led global investigative body launched last October, officials said, noting Ismail pledged to review measures for cooperation to combat new types of cybercrime. (Yohnap News)
Related: Korea JoongAng Daily, Korea Herald, Malay Mail
Crypto crime-fighting startup TRM Labs announced it had raised $70 million in a Series C venture funding round.
Blockchain Capital led the round with the participation of a mix of returning and new strategic investors, including Goldman Sachs, Bessemer Venture Partners, Brevan Howard Digital, Thoma Bravo, Citi Ventures, Galaxy Ventures, and DRW Venture Capital. (Leo Schwartz / Fortune)
Related: CoinDesk, Coinpedia Fintech News, The Block
RapidFort, a San Francisco, CA-based company that specializes in software supply chain security, announced it had raised $42 million in a Series A venture funding round.
Blue Cloud Ventures and Forgepoint Capital led the round, with participation from prior lead investor Felicis Ventures. Additional participants included Alumni Ventures, Boulder Ventures, Brave Capital, Evolution Ventures, Florida Funders, Gaingels, and Mana Ventures. (Duncan Riley / Silicon Angle)
Related: FinSMEs, Pulse 2.0, Security Week, The Fast Mode, BankInfoSecurity, CityBiz, FinTech Global
Best Thing of the Day: EU's Cybercrime Specialists v. Musk
Europol is supporting the investigation of Elon Musk's proliferation of deepfakes and child sex abuse material through its European Cybercrime Centre (EC3), providing specialised cybercrime expertise and deploying an analyst on the ground in Paris to assist national authorities.
Bonus Best Thing of the Day: Booting Silicon Valley Billionaires Out of Europe
European Union's Financial Services Commissioner Maria Luís Albuquerque announced that it's high time for Europe to focus on its digital sovereignty and kick US-based tech giants off the continent.
Extra Bonus Best Thing of the Day: Minneapolis Tech Community Does the Right Thing
Minneapolis-based founders and investors say they have put much of their work on hold and now spend their days focused on their communities, volunteering at churches, and helping buy food.
Worst Thing of the Day: Getting Tech Employer to Snitch on Workers
The Department of Homeland Security has been quietly demanding tech companies turn over user information about critics of the Trump administration.
Bonus Worst Thing of the Day: Let's Get Rich Off Human Suffering
Geo Group, a private prison operator that profits from detaining immigrants in the US, is rapidly shifting to offer surveillance tools, capitalizing on the government’s deportation push by selling human-tracking services.
Closing Thought