Texas AG sues TP-Link, saying it allowed the CCP to hack routers
A hacker gained access to a French national bank database with 1.2m accounts, Microsoft 365 Copilot bug summarized confidential emails, DEF CON bans Epstein's hacking associates, Deutsche Bahn operations disrupted by cyberattack, Polish army bans Chinese cars, much more


Although the power outages in Caracas on January 2 were widely proclaimed in press reports to be the result of a "precision" cyberattack, the truth is that cyber was only a minor component – experts say massive kinetic attacks on three substations were the primary cause of sustained blackouts during the operation to capture Venezuelan president Nicolás Maduro.
Check out my latest CyberScoop piece on how press reports failed to mention this critical component of Operation Absolute Resolve and how that might steer policy and spending decisions in the wrong direction. Stay tuned for tomorrow's Metacurity for more details and background color on this report.
Metacurity has been following cybersecurity, surveillance, and power as they unfold day by day—tracking patterns, context, and connections that most other sources miss. We go beyond the usual infosec news echo chamber, highlighting what’s real, overlooked, and often missed by traditional outlets. Please consider supporting our work by upgrading your subscription. Thank you!
Texas is suing networking equipment company TP-Link Systems for allegedly allowing the Chinese Communist Party (CCP) to hack into consumers’ devices even as it promised consumers strong security and privacy protections.
Attorney General Ken Paxton announced the lawsuit on Monday and said it is the first of several that will be filed this week against companies affiliated with the CCP.
In December, Paxton sued the Chinese television manufacturers Hisense and TCL, alleging that they capture what consumers watch in real time and could be allowing the data to be harvested by China.
Paxton alleges that TP-Link deceptively markets its products as protective of privacy and security when, in reality, they have been used by Chinese state-sponsored hacking groups to mount cyberattacks against the US.
His office cited a May 2023 report from Check Point Research, which alleged that TP-Link firmware vulnerabilities enabled Camaro Dragon hacking campaigns. Camaro Dragon is a Chinese state-sponsored hacking entity. (Ed. note: The author of that report told me in an interview I conducted for another publication that Camaro Dragon attacked the routers made by other manufacturers including American firms and that Chinese-made routers are not more vulnerable than any other routers).
Because many of TP-Link’s parts are imported from China, the manufacturer is bound by that government’s national data laws, which require Chinese companies to support the country’s intelligence services by “divulging Americans’ data,” a Paxton press release said. (Suzanne Smalley and Jonathan Greig / The Record)
Related: Texas Attorney General, StateScoop, Engadget, Reuters, The Epoch Times, PCMag, Courthouse News Service, Slashdot
The French Economy Ministry said that a hacker gained access to a national bank account database and consulted information on 1.2 million accounts.
Since the end of January, the hacker used the stolen credentials of an official to access and consult "parts of the file of all of the accounts open in French banks and which contains personal data such as bank account numbers, name of the account holder, address and in certain cases the account owner's tax number," the ministry said in a statement.
The chief of France's Public Finances told Agence France-Presse that gaining access to the database "doesn't allow you to check bank account balances, let alone conduct operations." The ministry said that once the unauthorized access was detected, measures were immediately taken to block the hacker and prevent the removal of information.
Owners of the 1.2 million affected bank accounts will receive notifications in the coming days, it added. (LeMonde / AFP)
Related: Xinhua, Connexion France
Microsoft says a Microsoft 365 Copilot bug has been causing the AI assistant to summarize confidential emails since late January, bypassing data loss prevention (DLP) policies that organizations rely on to protect sensitive information.
This bug (tracked under CW1226324 and first detected on January 21) affects the Copilot "work tab" chat feature, which incorrectly reads and summarizes emails stored in users' Sent Items and Drafts folders, including messages that carry confidentiality labels explicitly designed to restrict access by automated tools.
Copilot Chat (short for Microsoft 365 Copilot Chat) is the company's AI-powered, content-aware chat that lets users interact with AI agents. Microsoft began rolling out Copilot Chat to Word, Excel, PowerPoint, Outlook, and OneNote for paying Microsoft 365 business customers in September 2025.
"Users' email messages with a confidential label applied are being incorrectly processed by Microsoft 365 Copilot chat," Microsoft said when it confirmed this issue.
"The Microsoft 365 Copilot 'work tab' Chat is summarizing email messages even though these email messages have a sensitivity label applied and a DLP policy is configured."
Microsoft has since confirmed that an unspecified code error is responsible and said it began rolling out a fix in early February. As of Wednesday, the company said it was continuing to monitor the deployment and is reaching out to a subset of affected users to verify that the fix is working. (Sergiu Gatlan / Bleeping Computer)
Related: TechCrunch, The Register, Neowin, Mashable, Cyber Security News, PC World, Dataconomy, Computing, Tech in Asia
The DEF CON hacker conference has banned three people involved with the organization whose names appeared in recently released Justice Department files that exposed their ties to convicted sex offender Jeffrey Epstein.
The conference banned Vincenzo Iozzo, Joichi Ito, and Pablo Holman from future attendance, according to an updated list of banned individuals made public onWednesday.
The Justice Department’s release of approximately 3 million files on Jan. 30 has brought to light Epstein’s significant interest in some of the world’s largest hacker gatherings, with the recent disclosures connecting all three individuals to those efforts.
The ban also cited extensive Politico reporting that previously highlighted the individuals’ involvement with Epstein.
DEF CON and its sibling conference, Black Hat, are typically held the same week in Las Vegas, Nevada, every summer, attracting thousands of hackers, researchers, government officials, and investors to discuss the latest trends in cybersecurity.
It’s not entirely clear if Epstein ever attended either of the conferences. The banned individuals named in the emails are all linked to efforts he made to attend, according to the DOJ-released emails. Other released documents, including flight manifests and schedules, show that Epstein intended to attend. (David DiMolfetta / NextGov/FCW)
Related: DEF CON, TechCrunch
German rail operator Deutsche Bahn said it had been targeted by a DDoS attack that disrupted its digital services, causing outages in travel information and booking tools on its website and in the Navigator app.
Deutsche Bahn had informed customers about the disruptions on Tuesday afternoon, and by the evening, said the systems were largely running stably again.
On Wednesday morning, further problems occurred, and the company later cited the cyberattack as the cause.
"Our defensive measures took effect to, keep the impact on our customers as low as possible,” Deutsche Bahn said. (Richard Connor with dpa, AFP / DW)
Related: Table Media, The Register, Security Week, AFP
The Polish army has banned Chinese cars from entering military facilities hoping to prevent the collection of sensitive data by technologically advanced automobiles.
Modern vehicles equipped with cutting-edge sensors and communication systems are capable of “uncontrolled acquisition and use of data,” the Polish army wrote in a statement justifying the ban. Vehicles are now able to collect video, sound, and location, and there is a fear that Chinese producers might share some of this potentially sensitive data with their authorities.
All cars capable of recording location, video, and sound will be banned from secure military areas unless those functions are switched off, the Polish army said, meaning that the new restrictions do not apply to Chinese products alone.
It is also prohibited to connect official army phones to infotainment systems in any vehicle produced in China. (CLAUDIA CIOBANU / Associated Press)
Related: Polish Armed Forces, Reuters, Bloomberg, The Register, Notes from Poland, Automotive News, WION, Times of India
A ransomware attack at Japanese food and beverage giant Asahi Group Holdings Ltd. last September led to the leak of 115,513 sets of personal data, the company has said.
Of the total, 110,396 involved the names and phone numbers of client companies’ executives and employees, and 5,117 involved the names and addresses of Asahi Group workers, including those who have quit, according to the firm’s announcement.
Asahi Group said in November that 18 sets of information were confirmed to have leaked, while 1,914,000 may have leaked.
The company also unveiled detailed recurrence prevention measures, such as strengthening the functions to detect and block suspicious moves in computers and network facilities, setting up an internal organization for information security, appointing an executive in charge of information security, and enhancing employee education. (JiJi Press)
Related: Asahi Group
Telegram says it has not found any breaches of its encryption, dismissing a Russian government allegation that foreign intelligence services can see messages sent by Russian soldiers via the messaging app.
Russia's state communications regulator has introduced restrictions on Telegram, an important platform for public and private communications in the country, over what it says is a failure by the company to delete extremist content.
Digital development minister Maksud Shadayev said on Wednesday that foreign intelligence services were able to see Telegram messages sent by Russian troops fighting in Ukraine. (Gleb Stolyarov / Reuters)
Related: Agenzia Nova
Researchers at Swiss cybersecurity firm Acronis say that hackers believed to be aligned with Tehran are targeting supporters of Iran’s anti-government protests in a new cyberespionage campaign.
The campaign began in early January, shortly after mass nationwide demonstrations erupted across Iran calling for an end to the Islamic Republic system.
Researchers said the attackers likely took advantage of a spike in demand for information after authorities imposed sweeping internet blackouts across the country to limit coverage of the unrest.
The threat actor distributed malicious files bundled with authentic protest footage and a Farsi-language report described as providing updates from “the rebellious cities of Iran.” Two files in the archive, disguised as a video and an image, delivered a previously undocumented malware strain that researchers dubbed CRESCENTHARVEST.
The malware functions as both a remote access trojan and an information stealer. It is capable of executing commands, logging keystrokes, and extracting sensitive data, including saved credentials, browsing history, cookies, and Telegram account information.
It can also detect installed antivirus software, allowing it to adjust its behavior — becoming more aggressive on poorly protected systems or minimizing activity to avoid detection.
While the group behind the campaign has not been identified, Acronis said the attackers’ code, infrastructure, and methods suggest links to an Iranian-aligned threat actor. (Daryna Antoniuk / The Record)
Related: Acronis, GBHackers, Cyber Security News, The National, Cyber Press, SC Media
Hackers stole the personal and contact information of nearly 1 million accounts after breaching the systems of Figure Technology Solutions, a self-described blockchain-native financial technology company.
While the blockchain lender didn't publicly disclose the incident, a Figure spokesperson told TechCrunch on Friday that the attackers stole "a limited number of files" in a social engineering attack.
BleepingComputer has also reached out to Figure with further questions about the breach, but a response was not immediately available.
Although the company has yet to share how many individuals were affected by the data breach, notification service Have I Been Pwned has now revealed the extent of the incident, reporting that data from 967,200 accounts was stolen in the attack. (Sergiu Gatlan / Bleeping Computer)
Related: TechCrunch, American Banker
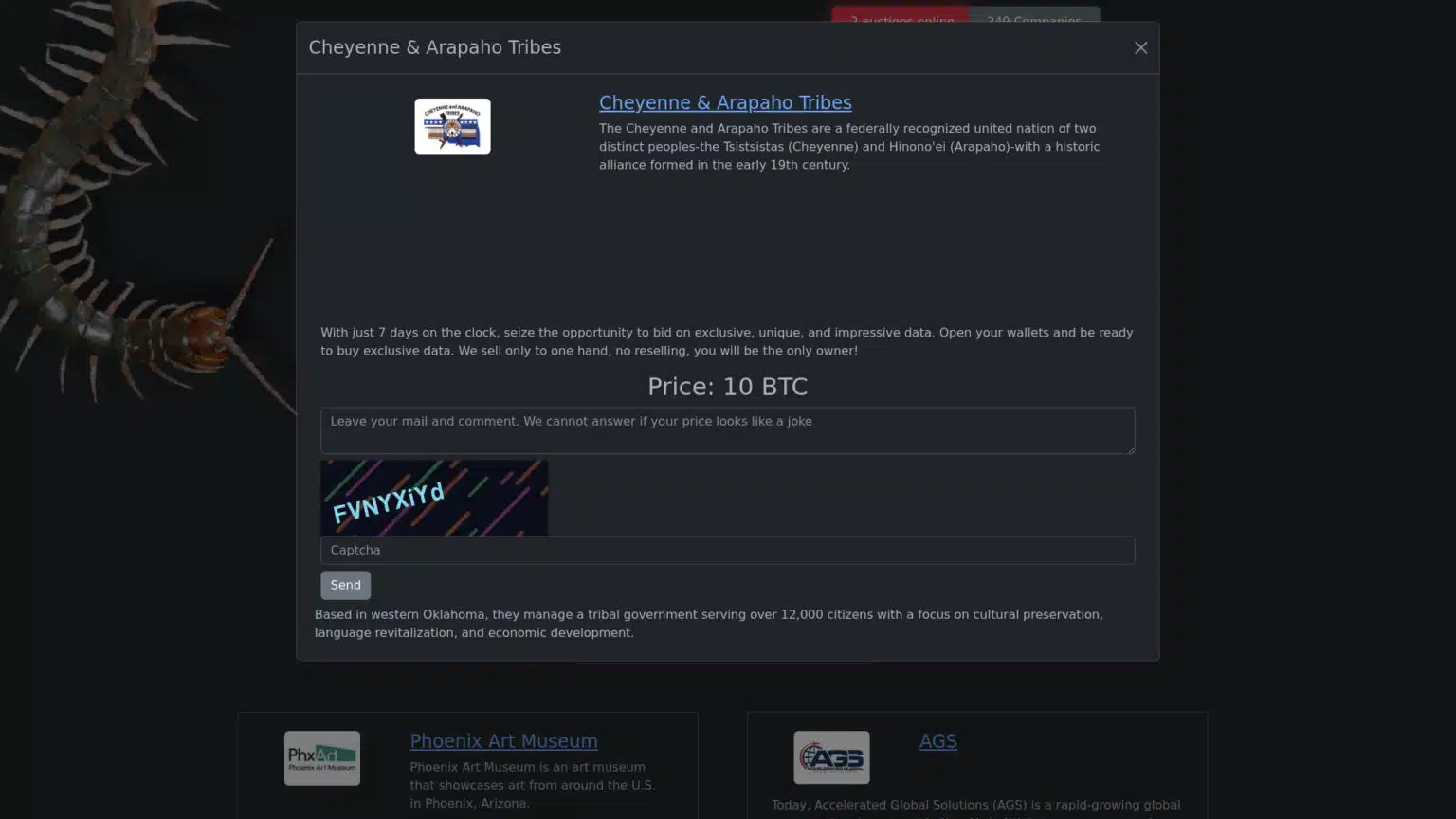
The Rhysida ransomware gang took credit for a December 8, 2025, cyber attack on the Cheyenne and Arapaho Tribes’ IT systems.
Tribal leadership publicly disclosed the attack on January 7, 2026, and said 80 percent of its systems were operational again one month after the attack.
Rhysida demanded that the Cheyenne and Arapaho Tribes pay 10 bitcoin in ransom, worth nearly $700,000, within seven days.
The Cheyenne and Arapaho Tribes have not acknowledged Rhysida’s claim, and Comparitech cannot independently verify it. We do not know what data might have been compromised, if the tribes paid a ransom, or how attackers breached their network. Comparitech contacted the Tribes for comment and will update this article if they reply.
“On or about December 8, 2025, the Tribe’s Information Technology (IT) team identified an attempted cybersecurity intrusion. Although the attempt did not result in any confirmed data loss, tribal leadership acted immediately and decisively to protect tribal member information and critical infrastructure,” says the tribes’ January announcement. “Out of an abundance of caution, all systems were taken offline–not because every system was compromised, but to ensure a comprehensive review and a secure restoration process.”
“As of today, approximately 80% of tribal employee users at the Concho headquarters have had their systems fully restored.” (Paul Bischoff / Comparitech)
Related: Databreaches.net
Deepfake nudes and “revenge porn” must be removed from the internet within 48 hours or technology firms risk being blocked in the UK, Keir Starmer has said, calling it a “national emergency” that the government must confront.
Companies could be fined millions or even blocked altogether if they allow the images to spread or be reposted after victims give notice.
Amendments will be made to the crime and policing bill to also regulate AI chatbots such as X’s Grok, which generated nonconsensual images of women in bikinis or in compromising positions until the government threatened action against Elon Musk’s company.
Writing for the Guardian, Starmer said: “The burden of tackling abuse must no longer fall on victims. It must fall on perpetrators and on the companies that enable harm.”
The prime minister said that institutional misogyny being “woven into the fabric of our institutions” meant the problem had not been taken seriously enough. “Too often, misogyny is excused, minimised or ignored. The arguments of women are dismissed as exaggerated or ‘one-offs’. That culture creates permission,” Starmer wrote.
Government sources said they expected to give the new powers to Ofcom to enforce by the summer and companies will be legally required to remove this content no more than 48 hours after it is flagged to them. (Jessica Elgot and Aisha Down / The Guardian)
Related: BBC, Bloomberg, The Indian Express, Financial Times, Sky News, GOV.UK, Ofcom, The Times, Mirror, Reuters, The Sun, Telegraph, r/europe, r/unitedkingdom
Emmanuel Macron has hit back at US criticism of Europe’s efforts to regulate AI, vowing to protect children from “digital abuse” during France’s presidency of the G7.
Speaking at the AI Impact summit in Delhi, the French president called for tougher safeguards after global outrage over Elon Musk’s Grok chatbot being used to generate tens of thousands of sexualised images of children, and amid mounting concern about the concentration of AI power in a handful of companies.
His remarks were echoed by António Guterres, the UN secretary general, who told delegates – including several US tech billionaires – that “no child should be a test subject for unregulated AI”.
“The future of AI cannot be decided by a few countries or left to the whims of a few billionaires,” Guterres said. “AI must belong to everyone”.
Bill Gates had been scheduled to speak but withdrew at the last minute amid renewed scrutiny of his past links to the convicted child sex offender Jeffrey Epstein.
Meanwhile, an attempt by India’s prime minister, Narendra Modi, to stage a show of unity among leading tech billionaires went awry when the rival heads of OpenAI and Anthropic awkwardly declined to hold hands on stage. (Robert Booth / The Guardian)
Related: Bloomberg, France24, NewsBytes, Wall Street Journal
The US State Department is developing an online portal that will enable people in Europe and elsewhere to see content banned by their governments, including alleged hate speech and terrorist propaganda, a move Washington views as a way to counter censorship, three sources familiar with the plan said.
The site will be hosted at "freedom.gov," the sources said. One source said officials had discussed including a virtual private network function to make a user's traffic appear to originate in the US and added that user activity on the site will not be tracked.
Headed by Undersecretary for Public Diplomacy Sarah Rogers, the project was expected to be unveiled at last week's Munich Security Conference but was delayed, the sources said.
Also involved in the US portal effort is Edward "Big Balls" Coristine, a former member of Musk's job-slashing Department of Government Efficiency, two sources said. Coristine works with the National Design Studio, created by Trump to beautify government websites. Reuters was unable to reach Coristine for comment.It was not clear what advantages the US government portal would offer users that are not available from commercial VPNs. (Simon Lewis, Humeyra Pamuk and Gram Slattery / Reuters)
Related: The Post Millennial, GB News, Reclaim The Net, r/privacy, r/worldnews, r/politics, r/eutech, r/europe, r/europeanunion
The Dutch Public Prosecution Service (OM) says 118 people have filed criminal charges in the investigation into the data breach at Clinical Diagnostics, the laboratory that handled the Dutch population screening for cervical cancer, among other things.
Hackers stole 850,000 people’s personal data in a ransomware attack in August last year.
The hack came to light after the Dutch Population Survey Foundation (BDON) went to the authorities. The OM and police launched a criminal investigation, which is still ongoing.
The OM said it could not yet provide any substantive information about the progress of the investigation. “Investigating digital crime is always intensive and time-consuming; evidence is complex and can originate from anywhere in the world. In such investigations, legal assistance from other countries is often required before the police can take the next step. This makes identifying a suspect a lengthy process,” the OM said. (NL Times)
Related: Dutch Prosecution Service
OpenAI announced that, together with crypto investment firm Paradigm, it is introducing EVMbench, a benchmark evaluating the ability of AI agents to detect, patch, and exploit high-severity smart contract vulnerabilities.
The AI giant said that EVMbench draws on 120 curated vulnerabilities from 40 audits, with most sourced from open code audit competitions. EVMbench additionally includes several vulnerability scenarios drawn from the security auditing process for the Tempo blockchain, a purpose-built L1 designed to enable high-throughput, low-cost payments via stablecoins.
These scenarios extend the benchmark into payment-oriented smart contract code, where we expect agentic stablecoin payments to grow, and help ground it in a domain of emerging practical importance, according to OpenAI.
According to OpenAI, EVMbench evaluates three capability modes:
- Detect: Agents audit a smart contract repository and are scored on recall of ground-truth vulnerabilities and associated audit rewards.
- Patch: Agents modify vulnerable contracts and must preserve intended functionality while eliminating exploitability, verified through automated tests and exploit checks.
- Exploit: Agents execute end-to-end fund-draining attacks against deployed contracts on a sandboxed blockchain environment, with grading performed programmatically via transaction replay and on-chain verification.
OpenAI further announced that buidling on its Cybersecurity Grant Program launched in 2023, it also committing $10M in API credits to accelerate cyber defense with our most capable models, especially for open source software and critical infrastructure systems. Organizations engaged in good-faith security research can apply for API credits and support through our Cybersecurity Grant Program. (OpenAI)
Related: DL News, Cyber Security News, Cointelegraph, Paradigm, The Crypto Times, The Block, Rohan's Bytes, CoinDesk, CoinGape, Decrypt, r/singularity
Cogent Security, a San Francisco, CA-based provider of an AI-native vulnerability management platform, announced it had raised $42 million in Series A funding.
Bain Capital Ventures led the round with participation from existing investor Greylock Partners and Definition. Founders and executives from OpenAI, Abnormal Security, and Datadog invested personally. (Lily Mae Lazarus / Fortune)
Related: FinSMEs, Bain Capital Ventures, SecurityWeek
Venice (fka Valkyrie), a NYC-based adaptive privileged access platform provider, announced it had raised $33 million in total funding, including a $25 million Series A funding round.
US-based fund IVP, with participation from Index Ventures, Vine Ventures, Holly Ventures, and several angel investors, including Assaf Rappaport (co-founder and CEO of Wiz), Raz Herzberg (CMO of Wiz), Dor Knafo and Gil Azrielant (founders of Axis), and the founders of Descope. (Meir Orbach / CTech)
Related: TechCrunch, FinSMEs, Index Ventures, Venice, IVP Perspectives
Best Thing of the Day: How Dear Leader Got Sony
In an exclusive book excerpt, the former CEO of Sony Entertainment, Michael Lynton, tells a tale filled with Hollywood flourishes of how his decision to greenlight the Seth Rogen and James Franco movie The Insider led North Korea to destroy the company's computer systems and leak all of its files.
Worst Thing of the Day: The Truth Is We Intend to Spy on Everyone
Ring’s controversial, AI-powered “Search Party” feature isn’t intended to always be limited only to dogs, the company’s founder, Jamie Siminoff, told Ring employees.
Closing Thought