The European Commission's mobile device platform was hacked
All four Singapore major telcos were hacked via China-nexus threat actor, Poland's most egregious database leaker has been busted, Romanian pipeline operator hit by a cyberattack, Germany warns of state-sponsored phishing attacks via messaging apps, much more


If you value Metacurity, please show your support by upgrading your subscription. Thank you
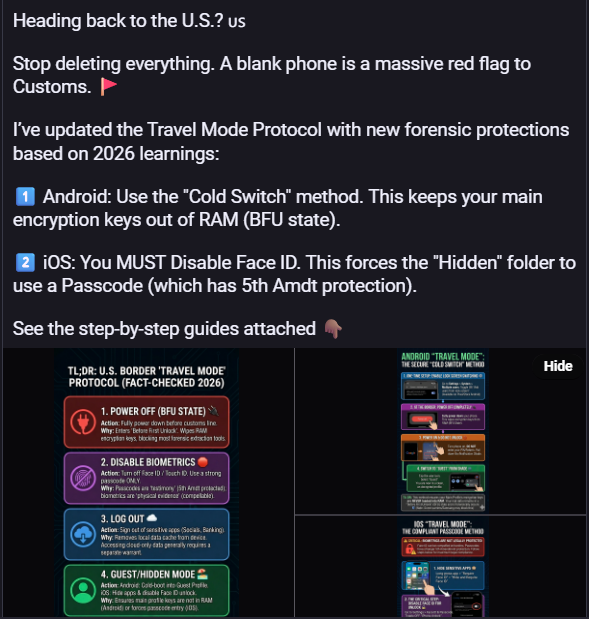
The European Commission is investigating a breach after finding evidence that its mobile device management platform was hacked.
The Commission said that it detected traces of a cyberattack targeting infrastructure that manages its staff's mobile devices.
While the attackers may have accessed some staff members' personal information, including names and phone numbers, the Commission has not yet found evidence that their mobile devices were compromised.
"On 30 January, the European Commission's central infrastructure managing mobile devices identified traces of a cyber-attack, which may have resulted in access to staff names and mobile numbers of some of its staff members," it said.
"The Commission's swift response ensured the incident was contained and the system cleaned within 9 hours. No compromise of mobile devices was detected."
The breach comes on the heels of the Commission's proposal of new cybersecurity legislation on January 20 to strengthen defenses against state-backed and cybercrime groups targeting critical infrastructure.
Although the Commission has not disclosed how attackers gained access to the mobile device management platform, the incident appears to be linked to similar attacks targeting European institutions that exploit vulnerabilities in Ivanti Endpoint Manager Mobile (EPMM) software.
The Dutch Data Protection Authority (AP) and the Council for the Judiciary (Rvdr) notified Parliament that their systems had been hacked in nearly identical breaches. They also confirmed the attackers exploited Ivanti EPMM vulnerabilities to access employee names, business email addresses, and telephone numbers. (Sergiu Gatlan / Bleeping Computer)
Related: European Commission, The Register, The European Sting, DigWatch, Security Week
Singapore authorities say that all four of Singapore's major telecommunication operators were the targets of a cyberattack by UNC3886 that was disclosed last year, and there is no evidence so far that any sensitive customer data was stolen.
Minister for Digital Development and Information Josephine Teo said that in one instance, the attackers were able to gain access to a few critical systems, but did not get far enough to have been able to disrupt services.
There is also no evidence so far to suggest that the attackers were able to access or steal sensitive customer data from the telcos Singtel, M1, StarHub, and Simba.
Coordinating Minister for National Security K Shanmugam had first made public the attack in July last year, saying only that a "highly sophisticated threat actor" was attacking critical infrastructure.
Mandiant describes UNC3886 as a “suspected China-nexus espionage actor” that has targeted prominent strategic organisations globally.
Singapore’s response to the attack, known as Operation Cyber Guardian, began after the telcos reported suspicious activities within their networks to the Cyber Security Agency of Singapore (CSA) and the Infocomm Media Development Authority (IMDA).
The operation involved more than 100 people across six government agencies, including the Centre for Strategic Infocomm Technologies (CSIT), the Singapore Armed Forces’ Digital and Intelligence Service, the Internal Security Department, and GovTech. (Channel News Asia)
Related: Qatar News Agency, Must Share News, The Cyber Express, Yahoo News Singapore, Tech in Asia, FinTech News, The Online Citizen, Capacity Global
The perpetrator of one of the largest database leaks in Polish history has been caught after almost a decade of investigations.
The major breach of Morele.net, a popular Polish online electronics marketplace, affected over two million customers back in 2018.
An initial probe was discontinued after failure to identify the hackers behind the leak.
But almost 8 years on, following continued investigations by law enforcement, a 29-year-old citizen has been charged with unlawfully obtaining and disclosing the data.
“The man has been charged and has admitted to the offenses,” Commander Marcin Zagórski, spokesperson for the Central Bureau for Combating Cybercrime, announced on Monday, adding that the arrest took place on January 30.
Zagórski said the identification of the person responsible for the Morele.net data leak was made possible by cooperation with victims, among other methods.
“This allowed us to identify the attack vector, determine the course of the incident, and – based on the traces left by the perpetrator – identify him,” Zagórski explained.
The leak included names, contact details, addresses, and hashed passwords, but no payment data was reportedly affected. (Stanisław Kaleta / TVP World)
Related: Anadolu Ajansı,
RelatedConpet, Romania's national oil pipeline operator, has disclosed that a cyberattack disrupted its business systems and took down the company's website last week.
Conpet operates nearly 4,000 kilometers of pipeline network, supplying domestic and imported crude oil and derivatives, including gasoline and liquid ethane, to refineries nationwide.
The company said the incident affected its corporate IT infrastructure but didn't disrupt its operations or its ability to fulfill its contractual obligations.
Conpet added that the cyberattack also took down its website and that it's now investigating the incident and restoring affected systems with the help of national cybersecurity authorities.
The pipeline operator has also notified the Directorate for Investigating Organized Crime and Terrorism (DIICOT) and filed a criminal complaint regarding the incident.
"We note that the operational technologies (SCADA System and Telecommunications System) were not affected, so the company's core business, consisting of the transport of crude oil and gasoline through the National Oil Transport System, is operating normally and there are no disruptions in its operation," it said. "As a result of this incident, the company's website www.conpet.ro cannot be accessed during this period."
While the company has yet to disclose the nature of the cyberattack, the Qilin ransomware gang has claimed responsibility and added Conpet to their dark web leak site earlier today. (Sergiu Gatlan / Bleeping Computer)
Related: Conpet on Facebook, Security Affairs, HazardEx, SC Media, World Pipelines, The Record, Industrial Cyber
Germany's Federal Office for the Protection of the Constitution (BfV) and the Federal Office for Information Security (BSI) are warning of suspected state-sponsored threat actors targeting high-ranking individuals in phishing attacks via messaging apps like Signal.
The attacks combine social engineering with legitimate features to steal data from politicians, military officers, diplomats, and investigative journalists in Germany and across Europe.
"A defining characteristic of this attack campaign is that no malware is used, nor are technical vulnerabilities in the messaging services exploited," the two agencies say.
According to the advisory, the attackers contact the target directly, pretending to be from the support team of the messaging service or the support chatbot.
"The goal is to covertly gain access to one-to-one and group chats as well as contact lists of the affected individuals,"
There are two versions of these attacks: one that performs a full account takeover, and one that pairs the account with the attacker’s device to monitor chat activity. In the first variant, the attackers impersonate Signal's support service and send a fake security warning to create a sense of urgency.
The target is then tricked into sharing their Signal PIN or an SMS verification code, which allows the attackers to register the account to a device they control. Then they hijack the account and lock out the victim.
In the second case, the attacker uses a plausible ruse to convince the target to scan a QR code. This abuses Signal’s legitimate linked-device feature that allows adding the account to multiple devices (computer, tablet, phone).
The German authorities suggest that users avoid replying to Signal messages from alleged support accounts, as the messaging platform never contacts users directly.
Instead, recipients of these messages are recommended to block and report these accounts. (Bill Toulas / Bleeping Computer)
Related: BSI, GBHackers, Help Net Security, Cyber Insider, Heise Online
The car industry is scrambling to root out that tech ahead of a looming deadline, a test case for America’s ability to decouple from Chinese supply chains.
New US rules will soon ban Chinese software in vehicle systems that connect to the cloud, part of an effort to prevent cameras, microphones, and GPS tracking in cars from being exploited by foreign adversaries.
The move is “one of the most consequential and complex auto regulations in decades,” according to Hilary Cain, head of policy at trade group the Alliance for Automotive Innovation. “It requires a deep examination of supply chains and aggressive compliance timelines.”
Carmakers will need to attest to the US government that, as of March 17, core elements of their products don’t contain code that was written in China or by a Chinese company. The rule also covers software for advanced autonomous driving and will be extended to connectivity hardware starting in 2029. Connected cars made by Chinese or China-controlled companies are also banned, wherever their software comes from.
The deadline is bringing fresh urgency to an industrywide effort to rely less on Chinese components. The shift was sparked by pandemic-era supply-chain disruptions and has stepped up amid rising geopolitical tensions. Tesla last year decided to stop using China-based suppliers for cars it makes in the US. (Stephen Wilmot / Wall Street Journal)
Related: CBT News, Auto Blog, TechSpot, WebProNews, DriveSpark, The News.com
The Department of Homeland Security’s Inspector General is investigating potential privacy abuses associated with Immigration and Customs Enforcement’s surveillance and biometric data programs, according to a letter sent to two senators.
Senators Mark Warner and Tim Kaine demanded that DHS Inspector General Joseph Cuffari investigate immigration-related surveillance programs across DHS, Customs and Border Protection, and ICE. Cuffari said his office had launched an audit called “DHS’ Security of Biometric Data and Personally Identifiable Information.”
“The objective of the audit is to determine how DHS and its components collect or obtain PII and biometric data related to immigration enforcement efforts and the extent to which that data is managed, shared, and secured in accordance with law, regulation, and Departmental policy,” Cuffari’s letter reads. He adds that one of the purposes of the investigation will be to “determine whether they have led to violations of federal law and other regulations that maintain privacy and defend against unlawful searches.” (Jason Koebler / 404 Media)
Related: DHS OIG, Politico, Federal News Network, CyberScoop
According to Norway's annual threat assessment, the international order created after World War II is losing strength, which is also undermining the foundations of Norwegian security.
Speaking at a news conference on the annual assessment, Intelligence Chief Nils Andreas Stensones noted that Russia wants to weaken Western unity and support for Ukraine, but it lacks the economic and diplomatic tools to do so.
Norwegian critical infrastructure and the energy sector are possible targets of espionage, influence operations, and sabotage attempts by Russia, said Stensones.
He noted that US President Donald Trump's rhetoric is aimed at Greenland, part of Denmark, adding that there are no such signs aimed at Norway.
Increased tensions between the West and Russia and China are leading to an arms race, according to the report.
For his part, Defense Minister Tore O. Sandvik noted that 2026 has so far been characterized by "great uncertainty," partly due to Trump's statements about Greenland.
"At the same time, I believe we must separate the political challenge it poses from the threats Norway faces, namely Russia and China," he noted.
Sandvik added: "Russia poses the greatest threat to Norwegian and allied security." (Burak Bir / Anadolu Ajansı)
Related: Norway PST, The Government of Norway, Yeni Safak, Global Times, South China Morning Post
Senegal’s Directorate of File Automation (DAF), the state body responsible for managing biometric data, national identity cards, and passports, has been hit by a cyberattack that has disrupted operations for at least five days, leading to the temporary suspension of all production.
The attack was claimed by a hacker group calling itself “The Green Blood Group,” which alleges it has exfiltrated 139 terabytes of data from the institution.
DAF is a highly sensitive technical agency tasked with securing and modernizing Senegal’s core administrative documents.
In a message posted on the dark web, the cybercriminals announced that they had added “two new victims to their dark portal,” identifying the Directorate of File Automation (DAF) and the company Ecobat. The post, accompanied by a screenshot labelled “Ransomware Alert,” explicitly listed both entities among the group’s targets.
Sources familiar with the matter said the Malaysian partners linked to the national identification system had been informed of the breach and had committed to deploying a technical team to Senegal. (The Gambia Journal)
Related: Seneweb
South Korean cryptocurrency exchange Bithumb said it had accidentally given away more than $40 billion worth of bitcoins to customers as promotional rewards, triggering a sharp selloff on the exchange.
Bithumb apologised for the mistake, which took place on Friday, and said it had recovered 99.7% of the 620,000 bitcoins, worth about $44 billion at current prices. It had restricted trading and withdrawals for the 695 affected customers within 35 minutes of the erroneous distribution.
The exchange had planned to distribute small cash rewards of 2,000 Korean won ($1.40) or more to each user as part of a promotional event, but winners received at least 2,000 bitcoins each instead, media reports said.
"We would like to make it clear that this incident is unrelated to external hacking or security breaches, and there are no problems with system security or customer asset management," Bithumb said in a statement. (Hyunjoo Jin / Reuters)
Related: Tom's Hardware, ABC, Benzinga, The Information, Blockchain.News, Hackread, Bitcoin Insider, CoinGape, Gulf News, Bloomberg, Oman Observer, Yonhap News Agency, Tech in Asia, CoinDesk, Web3 is Going Just Great, The Chosun Daily, The Asia Business Daily, Protos, Blockonomi, Gizmodo, The Korea Times, The Defiant, Decrypt, Bitcoin Magazine, BeInCrypto, The Block, crypto.news, Crypto Briefing, Coinpedia Fintech News
US-listed South Korean e-commerce company Coupang confirmed that the data of an additional 165,000 users was leaked in a major security breach, which a South Korean government official said had shaken the country’s alliance with the US.
Coupang Korea has been under a South Korean government probe over the leak last year of personal data affecting more than 33 million customers, which has created friction between the allies over trade and security ties.
Coupang said it had identified additional customers affected by November’s leak, which involved contact details, including names, phone numbers, and addresses. No payment details or login information were compromised and users have been notified as per government guidance, it said in a statement.
Coupang is also facing a tax audit in South Korea and a legal complaint filed by the country’s parliament against its founder and former executives.
Wi Sung-lac, the South Korean presidential national security adviser, said the Coupang issue is affecting a range of key trade and security matters between the allies.
Separately, a group of Coupang users has filed a class action lawsuit in New York against the e-commerce giant's US-listed parent company seeking punitive damages over a recent data breach that affected more than 30 million people.
According to the US District Court for the Eastern District of New York on Friday, two Korean Americans, one surnamed Lee and another Park, led the class action suit against Coupang Inc. and its Korean American founder, Bom Kim. (Kyu-seok Shim and Jack Kim / Reuters and KBS World)
Related: Channel News Asia, The Chosun Daily, Korea JoongAng Daily, KBS World Radio, Yonhap News
Google, one of the global leaders in quantum computing, is urging governments, companies, and critical infrastructure operators to accelerate preparations for the quantum computing era, warning that today’s encryption systems could be broken sooner than many expect and outlining the company’s own commitments to post-quantum security.
In a call to action, Google writes that quantum computing is both a transformative scientific tool and a looming cybersecurity risk. According to the authors, the same machines expected to drive advances in drug discovery, materials science, and energy could also undermine the public-key cryptography that protects financial transactions, private communications, and classified data.
“To put that plainly: The encryption currently used to keep your information confidential and secure could easily be broken by a large-scale quantum computer in coming years,” Google said. (Matt Swayne / Quantum Insider)
Related: Google, Tech Buzz, Android Headlines
RADICL, which positions itself as a specialist provider of an autonomous virtual security operations center, announced it had raised $31 million in a Series A venture funding round.
Paladin Capital Group led the round with participation from returning backers Access Venture Partners and Denver Ventures, alongside new investor Cervin Ventures. (Duncan Riley / Silicon Angle)
Related: GovInfoSecurity.com, Resilience Media, SC Media, RADICL Defense, Inc., FinTech Global, Denver Business Journal, Axios, SecurityWeek
Best Thing of the Day: Epstein Was a Secret Hacker at Heart?
Reddit user sandnnn scoured the Epstein files to document the curious phenomenon of Jeffrey Epstein's interest in DEFCON.
Bonus Best Thing of the Day: Get 'Em While They're Young
Hackers who are former members of a sprawling cybercrime ecosystem dubbed “The Com” are urging talented teenagers in Manchester, England, to use their gaming and coding skills for the good of humanity.
Worst Thing of the Day: Why We Still Have Malicious Ads on Social Media
Juniper Research reports that social media sites received nearly £3.8bn ($5.2bn) in revenue from malicious ads in Europe in 2025 via almost one trillion impressions.
Closing Thought