The FBI seized the notorious RAMP cybercrime forum
Google took down dozens of domains related to mysterious threat actor Ipidea, China executed 11 people linked to Myanmar scam centers, Moltbot AI assistant can leak sensitive information, ShinyHunters hit Bumble, Panera, Match and CrunchBase, Poland's grid attack disabled comms at 30 sites, more
Check out my latest CSO piece that examines how evolving NIST guidance on the cybersecurity of AI is moving past the long-standing practice of treating AI as “just software."
Paid subscribers receive full access to Metacurity’s archives and selected analytical deep dives
Don't miss out on the full range of what Metacurity has to offer. Upgrade to a paid subscription, gain access to our archives and special content, and stay current while helping to keep independent media alive.
If you can't afford a paid subscription, donate what you can to keep this vital resource going.
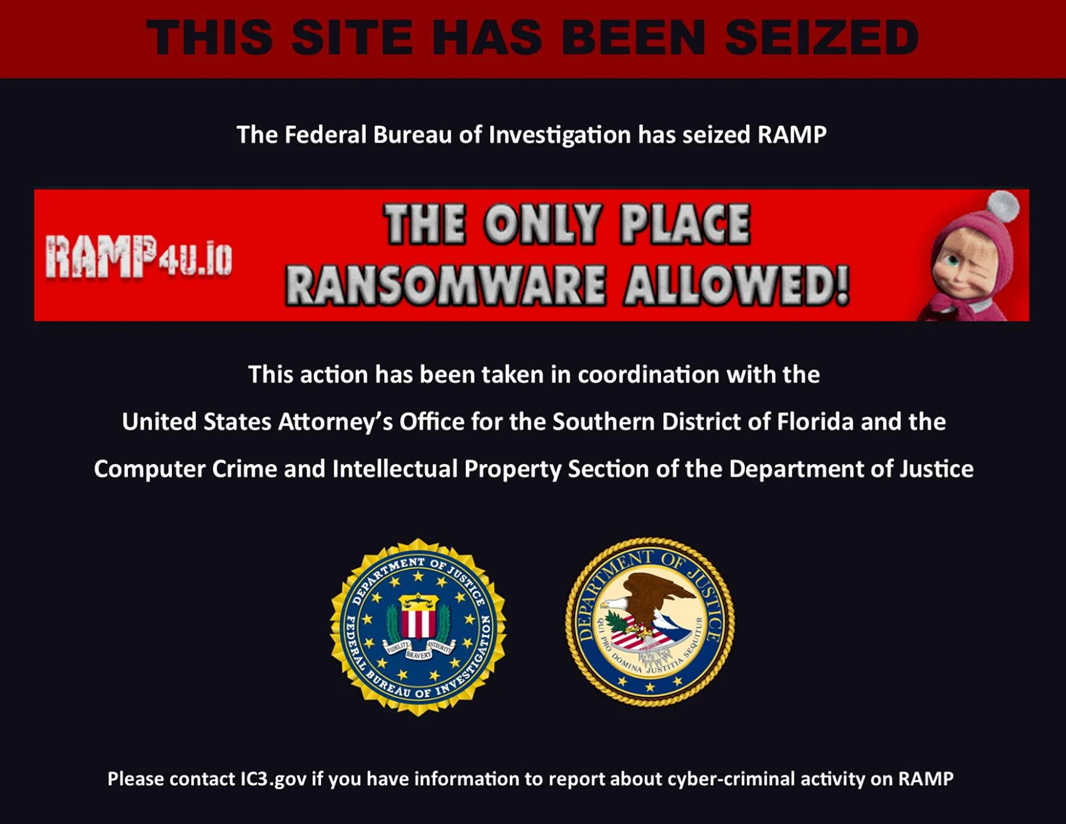
The FBI has seized the notorious RAMP cybercrime forum, a platform used to advertise a wide range of malware and hacking services, and one of the few remaining forums that openly allowed the promotion of ransomware operations.
Both the forum's Tor site and its clearnet domain, ramp4u[.]io, now display a seizure notice stating, "The Federal Bureau of Investigation has seized RAMP."
"This action has been taken in coordination with the United States Attorney's Office for the Southern District of Florida and the Computer Crime and Intellectual Property Section of the Department of Justice," the notice reads.
The seizure banner also appears to taunt the forum's operators by displaying RAMP's own slogan: "THE ONLY PLACE RANSOMWARE ALLOWED!", followed by a winking Masha from the popular Russian "Masha and the Bear" kids' cartoon.
While there has been no official announcement by law enforcement regarding this seizure, the domain name servers have now been switched to those used by the FBI when seizing domains.
If so, law enforcement now has access to a significant amount of data tied to the forum's users, including email addresses, IP addresses, private messages, and other potentially incriminating information.
For threat actors who failed to follow proper operational security (opsec), this could lead to identification and arrests. (Lawrence Abrams / Bleeping Computer)
Related: HackRead, The Register - Security, r/cybersecurity, Ars Technica, Slashdot, Databreaches.net, SOCRadar
Google used a federal court order to get dozens of domains belonging to Ipidea removed from the internet, saying the mysterious company is an unsavory enterprise that sneaks unwanted and dangerous software on millions of phones, home computers, and Android devices.
Control of the domains allowed Google to shut down both the public websites and the technical back-end of the company, which operates using more than a dozen brand names. Google has also taken steps to remove hundreds of apps affiliated with the company from Android devices, it said.
The actions are expected to knock more than nine million Android devices off Ipidea’s network. They target a little-known but important part of the internet that has increasingly worried cybersecurity experts.
Called “residential proxy” networks, these online services are built out of apps that are installed on virtually any type of internet-connected device—among them media players, PCs, and mobile phones. Companies such as Ipidea then rent out access to the devices to paying customers who want to use the internet anonymously. The businesses operate like Airbnbs for network bandwidth, except the people whose devices are being rented out often don’t realize what is happening.
Contacted earlier this week, before the takedown, an Ipidea spokeswoman acknowledged in an email that the company and its partners had engaged in “relatively aggressive market expansion strategies” and “conducted promotional activities in inappropriate venues (e.g., hacker forums),” but she said that it had since improved its business practices.
There are legitimate uses for Ipidea’s service, which can be used to surf the internet anonymously or to scrape websites for data. But from the time the company first gained prominence, in late 2022, it marketed its services in criminal marketplaces, said Riley Kilmer, the co-founder of Spur Intelligence, which tracks residential proxy activity.
Residential proxies have also become a go-to service for criminals and state-sponsored hackers who want to cover their tracks, said John Hultquist, chief analyst with Google’s Threat Intelligence Group. “It’s a consumer issue and it’s a national-security issue at the same time,” he said. “It’s enabling some of the most serious threats to our country.” (Robert McMillan / Wall Street Journal)
Related: Google, Cyber Press, Technology.org, Reuters, The Cyber Express, WebProNews, Devices and Browser Info
According to state media, China has executed 11 people linked to scam centers in Myanmar, including “core members” involved in the operation.
Those executed were members of the “Ming family criminal gang” and had been found guilty of intentional homicide, as well as fraud and running casinos, state broadcaster China Central Television reported on Thursday.
Across Southeast Asia, billion-dollar cyber scam operations have been expanding, particularly in Laos, Cambodia, and Myanmar, according to a report by the UN Office on Drugs and Crime. Many working in such scam operations in the region are also themselves victims of human trafficking.
China is “actively cooperating” with countries such as Myanmar to crack down on cross-border telecommunications fraud, Chinese Foreign Ministry spokesman Guo Jiakun said Thursday at a regular briefing in Beijing.
“These joint efforts to root out the ‘scourges’ of online gambling and telecom fraud have achieved significant results in safeguarding the lives and property of the people,” he added.
The Ming family syndicate’s online and telecommunications fraud operations involved more than 10 billion yuan ($1.4 billion) in funds, according to the report. The gang’s activities resulted in the death of 14 Chinese citizens and left many others injured.
China’s Supreme Court approved the executions, and the criminals were allowed to meet their relatives beforehand. (Bloomberg News)
Related: China Central Television, DW, The Independent, BBC News, Le Monde, Reuters, Al Jazeera, UPI
Security researchers are warning of insecure deployments in enterprise environments of the Moltbot (formerly Clawdbot) AI assistant, which can lead to leaking API keys, OAuth tokens, conversation history, and credentials.
Moltbot is an open-source personal AI assistant with deep system integration created by Peter Steinberger that can be hosted locally on user devices and integrated directly with the user’s apps, including messengers and email clients, as well as the filesystem.
Unlike cloud-based chatbots, Moltbot can run 24/7 locally, maintaining a persistent memory, proactively reaching out to the user for alerts/reminders, executing scheduled tasks, and more.
However, multiple security researchers caution that careless deployment of Moltbot can lead to sensitive data leaks, corporate data exposure, credential theft, and command execution, depending on the chatbot's permissions and access level on the host.
Pentester Jamieson O’Reilly highlighted some of the security implications. The researcher explains that hundreds of Clawdbot Control admin interfaces are exposed online due to reverse proxy misconfiguration.
Because Clawdbot auto-approves “local” connections, deployments behind reverse proxies often treat all internet traffic as trusted, so many exposed instances allow unauthenticated access, credential theft, access to conversation history, command execution, and root-level system access.
“Someone [...] had set up their own Signal (encrypted messenger) account on their public-facing clawdbot control server – with full read access,” the researcher says.
"That's a Signal device linking URI (there were QR codes also). Tap it on a phone with Signal installed, and you're paired to the account with full access."
The researcher tried to interact with the chat in an attempt to fix the issue, but the reply was to alert the owner of the server, although the AI agent couldn't help with a contact.
O'Reilly also demonstrated a supply-chain attack against Motlbot users via a Skill (packaged instructions set or module) that contained a minimal “ping” payload.
While Moltbot may be more suited for consumers, Token Security claims that 22% of its enterprise customers have employees who are actively using Moltbot, likely without IT approval.
Hudson Rock warned that info-stealing malware like RedLine, Lumma, and Vidar will soon adapt to target Moltbot’s local storage to steal sensitive data and account credentials.
Aikido researchers also caught a separate case of a malicious VSCode extension impersonating Clawdbot. The extension installs ScreenConnect RAT on developers' machines.
Deploying Moltbot safely requires knowledge and diligence, but the key is to isolate the AI instance in a virtual machine and configure firewall rules for internet access, rather than running it directly on the host OS with root access. (Bill Toulas / Bleeping Computer)
Related: HackedIn, Ars Technica, Gizmodo, Pivot to AI, SOC Prime, Digital Trends, Michael Tsai, Wired, PCMag, The Register, Aikido
A wave of cyberattacks has hit Bumble, Panera Bread, Match Group, and CrunchBase, and other companies, as cybersecurity experts warn about a new round of social engineering attacks targeting US companies.
Bumble Inc., the parent company of dating apps Bumble, Badoo, and BFF, contacted law enforcement after one of its contractors’ accounts “was recently compromised in a phishing incident,” a spokesperson said.
The hacker made “a brief unauthorized access to a small portion of our network,” the spokesperson said, adding that the company believes the access had ended. The hackers didn’t get into the company’s member database, member accounts, the Bumble application, direct messages, or profiles, the spokesperson said.
Similarly, Panera Bread said it had alerted law enforcement after identifying a cybersecurity incident and took steps to address it. A hacker accessed a software application Panera was using to store data, a spokesperson said.
“The data involved is contact information,” the spokesperson said, without elaborating.
Match also confirmed that it had suffered a cybersecurity incident affecting a “limited amount of user data,” and that it was in the process of notifying customers.
A spokesperson said there was no indication that user log-in credentials, financial information, or private communications were accessed.
A CrunchBase spokesman said documents on its corporate network had been affected, but the company had contained the incident.
Match’s system was breached on Jan. 16, but Bloomberg News couldn’t determine when the incidents occurred.
Cybersecurity experts recently warned about a social engineering campaign targeting US companies, which has been attributed to a group that refers to itself as ShinyHunters. The group has claimed responsibility for the attacks on Bumble, Panera, Match, and CrunchBase.
Mandiant warned last week of the ShinyHunters campaign, saying the group used novel “vishing” techniques to compromise single sign-on credentials from victim organizations and remotely access their systems.
Separately, ShinyHunters has been identified as the culprit behind a breach on online music company SoundCloud, confirmed in December. Although SoundCloud has not revealed how many users were affected, data breach notification service Have I Been Pwned revealed the extent of the breach, reporting that it affected 29.8 million accounts whose email addresses, geographic locations, names, usernames, and profile statistics were harvested in the incident. (Margi Murphy / Bloomberg and Sergiu Gatlan / Bleeping Computer)
Related: NDTV, The Cyber Express, NewsBytes, WebProNews, Reuters, HaveIBeenPwned, Woods Lonergan, SC Media, Security Week
According to researchers at Dragos, the hackers behind a cyberattack that targeted Poland's grid infrastructure in December disabled communication devices for at least 30 sites across a number of energy facilities in different parts of the country.
The hackers succeeded in disabling the communication systems, known as remote terminal units or RTUs, that are used to monitor and control other equipment, and they were able to render the RTUs inoperable and beyond repair. But they did not cause an outage or otherwise have an impact on generation and transmission equipment at nearly three dozen sites.
Most of the devices they targeted were not directly part of control infrastructure, Dragos says, but were instead systems related to grid safety and stability monitoring rather than active generation control. Nonetheless, the systems the attackers targeted do play a role in monitoring functions and maintaining grid stability, and had the attackers gained complete operational control of these systems, they could have created an impact that would have been "significantly different,” Dragos notes. Dragos also says the attack appears to have been "opportunistic" rather than fully targeted and well planned.
The sites that were impacted are managed by several energy entities, including two combined-heat-and-power plants and several facilities used to manage the dispatch of renewable energy from wind and solar sites. Dragos did not identify which entity was part of its investigation. (Kim Zetter / Zero Day)
Related: Dragos, Industrial Cyber, RTO Insider, Bleeping Computer, The Register
According to an FBI affidavit, weeks before the 2024 election, American military hackers carried out a secret operation to disrupt the work of Russian trolls spewing false information at US voters.
From their perch at Cyber Command at Fort Meade, Maryland, the military hackers aimed at the computer servers and key personnel of at least two Russian companies that were covertly pumping out the propaganda, according to multiple sources briefed on the operation.
The trolls were trying to influence election results in six swing states by publishing fictitious news stories that attacked American politicians who supported Ukraine. One of the companies had held “strategy meetings” with Kremlin officials on how to influence US voters covertly.
In one case, the Cyber Command operatives planned to knock offline computer servers based in a European country that one of the Russian companies used, the sources said. Though the Russian trolls continued to create content through Election Day, when President Donald Trump defeated then-Vice President Kamala Harris, one source briefed on the hacking effort said it successfully slowed down the Russians’ operations.
The hacking campaign, which hasn’t been previously reported, was one of multiple US cyber operations against Russian and Iranian groups aimed at blunting foreign influence on the 2024 election. It was part of a broader US government effort involving the FBI, the Department of Homeland Security, and other intelligence and security agencies that exposed and disrupted foreign meddling. (Sean Lyngaas / CNN)
Related: Justice Department
Amazon reported hundreds of thousands of pieces of content last year that it believed included child sexual abuse, which it found in data gathered to improve its artificial intelligence models.
Though Amazon removed the content before training its models, child safety officials said the company has not provided information about its source, potentially hindering law enforcement from finding perpetrators and protecting victims.
Throughout last year, Amazon detected the material in its AI training data and reported it to the National Center for Missing and Exploited Children, or NCMEC. The organization, which Congress established to field tips about child sexual abuse and share them with law enforcement, recently started tracking the number of reports specifically tied to AI products and their development. In 2025, NCMEC saw at least a fifteen-fold increase in these AI-related reports, with “the vast majority” coming from Amazon. The findings haven’t been previously reported.
An Amazon spokesperson said the training data was obtained from external sources, and the company doesn’t have the details about its origin that could aid investigators. It’s common for companies to use data scraped from publicly available sources, such as the open web, to train their AI models. Other large tech companies have also scanned their training data and reported potentially exploitative material to NCMEC.
However, the clearinghouse pointed to “glaring differences” between Amazon and its peers. The other companies collectively made just “a handful of reports,” and provided more detail on the origin of the material, a top NCMEC official said. (Riley Griffin and Matt Day / Bloomberg)
According to sources, OpenAI’s development of its own social network appears to be crystallizing around a singular mission: obliterate the bot problem that has made an endless and toxic sump of the platform formerly known as Twitter.
The sources say the social network, which is still in the very early stages of development, has been envisioned as a real-humans-only platform, a potential selling point for the AI giant, which is looking to capitalize on its viral ChatGPT and Sora apps.
But should it launch, it will be wading into a market of powerful incumbents, like X, Instagram, and TikTok.The app is being developed by a tiny team — fewer than 10 people — and may include a biometric identity recognition element. Sources familiar with its development told Forbes that the team has considered requiring users to provide “proof of personhood” via Apple’s Face ID or the World Orb. This cantaloupe-sized eyeball scanner uses a person's iris to generate a unique, verifiable ID. World is operated by Tools for Humanity, a company OpenAI CEO Sam Altman founded and currently chairs.
The Verge reported in April that OpenAI was working on a social network. (Anna Tong / Forbes)
Related: Digit, CoinGape, Cointelegraph, crypto.news, CoinDesk, Crypto Briefing, BeInCrypto, The Block, The Defiant, The Information
Researchers at Proofpoint report that a prolific initial access broker tracked as TA584 has been observed using the Tsundere Bot alongside XWorm remote access trojan to gain network access that could lead to ransomware attacks.
Tsundere Bot is a malware-as-a-service platform with backdoor and loader capabilities. It requires Node.js to operate, which the malware adds to the victim system using installers generated from its command-and-control panel.
The malware retrieves its command-and-control (C2) address from the Ethereum blockchain using a variant of the EtherHiding technique, with a hardcoded fallback address also included in the installer.
A prolific initial access broker tracked as TA584 has been observed using the Tsundere Bot alongside XWorm remote access trojan to gain network access that could lead to ransomware attacks.
TA584 activity in late 2025 tripled in volume compared to Q1 of the same year and expanded beyond the standard targeting scope of North America and the UK/Ireland to include Germany, various European countries, and Australia. (Bill Toulas / Bleeping Computer)
Related: Proofpoint, Cyber Press
Researchers at CrowdStrike report that a North Korea-backed threat group, which they call Labyrinth Chollima, that has been operating since 2009, has splintered into three distinct groups with specialized malware and objectives.
The group follows a divergence pattern CrowdStrike observed previously. Labyrinth Chollima has spawned two additional groups: Golden Chollima and Pressure Chollima. The spin-offs, which have been operating since 2020, allow Labyrinth Chollima to narrow its focus on espionage, targeting victims in the manufacturing, logistics, defense, and aerospace industries.
Golden Chollima and Pressure Chollima are squarely focused on stealing cryptocurrency, which funnels money back to the regime, with some of the proceeds funding North Korea’s cyber operations. Pressure Chollima, which was responsible for last year’s record-breaking $1.46 billion cryptocurrency theft, targets high-payout opportunities and has evolved into one of North Korea’s most technically advanced threat groups, according to CrowdStrike.
The groups, which share lineage with the more broadly defined Lazarus Group, share some tools and infrastructure, which indicates centralized coordination, but they’ve also developed more specialized capabilities for their specific objectives, researchers said. (Matt Kapko / CyberScoop)
Related: CrowdStrike
The Department of Homeland Security published new details about Mobile Fortify, the face recognition app that federal immigration agents use to identify people in the field, undocumented immigrants, and US citizens alike.
The details, including the company behind the app, were published as part of DHS’s 2025 AI Use Case Inventory, which federal agencies are required to release periodically.
The inventory includes two entries for Mobile Fortify—one for Customs and Border Protection (CBP), another for Immigration and Customs Enforcement (ICE)—and says the app is in the “deployment” stage for both. CBP says that Mobile Fortify became “operational” at the beginning of May last year, while ICE got access to it on May 20, 2025. That date is about a month before 404 Media first reported on the app’s existence.
The inventory also identified the app’s vendor as NEC, which had previously been unknown publicly. On its website, NEC advertises a face recognition solution called Reveal, which it says can do one-to-many searches or one-to-one matches against databases of any size. CBP says the app’s vendor is NEC, while ICE notes it was developed partially in-house.
A $23.9 million contract held between NEC and the DHS from 2020 to 2023 states that DHS was using NEC biometric matching products for “unlimited facial quantities, on unlimited hardware platforms, and at unlimited locations.” NEC did not immediately respond to a request for comment.
Both CBP and ICE say that the app is supposed to help quickly confirm people’s identity, and ICE further says that it helps do so in the field “when officers and agents must work with limited information and access multiple disparate systems.”
ICE says that the app can capture faces, “contactless” fingerprints, and photographs of identity documents. The app sends that data to CBP “for submission to government biometric matching systems.” Those systems then use AI to match people’s faces and fingerprints with existing records, and return possible matches along with biographic information. ICE says that it also extracts text from identity documents for “additional checks.” ICE says it doesn’t own or interact directly with the AI models, and that those belong to CBP.
CBP says the “Vetting/Border Crossing Information/ Trusted Traveler Information” was used to either train, fine-tune, or evaluate the performance of Mobile Fortify. (Maddy Varner and Dell Cameron / Wired)
Related: DHS, The Guardian
Researchers at Trellix report that today's cyberthreat actors are moving away from simple encryption methods and toward individual patient extortion, service disruptions, and an affiliate model.
Trellix based its report on 54.7 million detections across multiple Trellix security products installed in healthcare settings. About 75% of the detections originated from US-based customers, highlighting the aggressive targeting of US healthcare organizations.
The report identified 109 unique campaigns engineered to compromise healthcare infrastructure in 2025, and notable spikes in activity in the first half of 2025. Phishing remained the primary attack vector, with cyberthreat actors increasingly using AI and regulatory compliance themes to trick administrative staff.
Patient extortion is a growing trend, Trellix noted, as cyberthreat actors can bypass negotiations with legal teams and insurers and instead demand small sums of money directly from patients. In 2025, extortion-only attacks on healthcare providers accounted for 12% of all healthcare cyberattacks, Trellix found, representing a 300% increase since 2023.
But the defining trend of 2025, according to the report, was the "cascading effect," in which attacks against administrative networks or non-clinical systems, such as a building's HVAC system, could significantly disrupt a healthcare organization's operations. (Jill Hughes / TechTarget)
Related: Trellix, SC Media, Cybersecurity Dive
Hungarian and Romanian police have arrested four young suspects in connection with bomb threats, false emergency calls, and the misuse of personal data — part of online swatting incidents that prompted repeated police deployments across the region.
In a statement earlier this week, Hungarian police said the suspects include a 17-year-old Romanian national and three Hungarians aged 16, 18, and 20. Law enforcement raided their homes earlier this month, seizing computers and mobile phones as part of a joint investigation.
Authorities said the incidents were part of coordinated swatting and doxing campaigns — tactics that involve filing fake reports of serious crimes and leaking personal information to intimidate or harass victims. Police said the suspects initially contacted victims on the Discord app, obtained their phone numbers and personal details, and then used that information to place false emergency calls in their names.
According to Hungarian police, the 16-year-old suspect was questioned on suspicion of threatening the public but denied the charges and was released pending further proceedings. The 17-year-old Romanian was charged with terrorist acts, making threats to endanger the public, multiple counts of false reporting, and misuse of personal data. The legal status of the two older Hungarian suspects has yet to be determined, as investigators analyze seized data to clarify their roles.
In January 2025, bomb threat emails were sent to more than 200 schools and other educational institutions across Hungary, prompting temporary closures, authorities said at the time. No explosives were found.
In a separate investigation announced earlier this week, Romanian authorities said they had uncovered an online marketplace allegedly designed to allow users to hire assassins while concealing identities and financial transactions. Two Romanian nationals are under investigation in connection with that operation. (Daryna Antoniuk / The Record)
Related: Hungarian Police
The Canadian Centre for Cyber Security has warned that ransomware will remain one of the country’s most serious cyber threats through 2027, as attacks become faster, cheaper, and harder to detect.
The Centre also stresses that basic cyber hygiene still provides strong protection. Regular software updates, multi-factor authentication, and vigilance against phishing attempts significantly reduce exposure, even as attack methods evolve.
Officials conclude that while ransomware threats will intensify over the next two years, early warnings, shared intelligence, and preventive measures can limit damage. (Digwatch)
Related: Government of Canada, The Canadian Press
Google will pay $135 million to settle a proposed class action by smartphone users who accused Google of programming its Android operating system to collect their cellular data without permission.
A preliminary settlement with the Alphabet unit was filed late Tuesday night in the San Jose, California federal court, and requires a judge's approval.
Google denied wrongdoing in agreeing to the settlement, which covers users of Android-powered mobile devices since November 12, 2017.
Users said Google needlessly collected cellular data, which they purchased from mobile carriers, even when they closed Google's apps, disabled location-sharing, or locked their screens.
They said the data supported Google's product development and targeted advertising campaigns and amounted to "conversion," when a party wrongfully takes another party's property with the intent to assert control.
As part of the settlement, Google will not transfer data without obtaining consent from Android users when they set up their phones. The Mountain View, California-based company will also make it easier for users to stop the transfers by toggling, and will disclose the transfers in its Google Play terms of service. (Jonathan Stempel / Reuters)
Related: CNET, Yahoo Finance, Tech in Asia, Bloomberg Law, Wall Street Journal
SolarWinds released security updates to patch critical authentication bypass and remote command execution vulnerabilities in its Web Help Desk IT help desk software.
The authentication bypass security flaws (tracked as CVE-2025-40552 and CVE-2025-40554) patched today by SolarWinds were reported by watchTowr's Piotr Bazydlo and can be exploited by remote unauthenticated threat actors in low-complexity attacks.
Bazydlo also found and reported a critical remote code execution (RCE) flaw (CVE-2025-40553) stemming from an untrusted data deserialization weakness that can enable attackers without privileges to run commands on vulnerable hosts.
A second RCE vulnerability (CVE-2025-40551) reported by Horizon3.ai security researcher Jimi Sebree can also enable unauthenticated attackers to execute commands remotely.
SolarWinds also patched a high-severity hardcoded credentials vulnerability (CVE-2025-40537) discovered by Sebree that, under unspecified circumstances, could grant threat actors with low privileges unauthorized access to administrative functions. (Sergiu Gatlan / Bleeping Computer)
Related: SolarWinds, CSO Online, Horizon3.ai
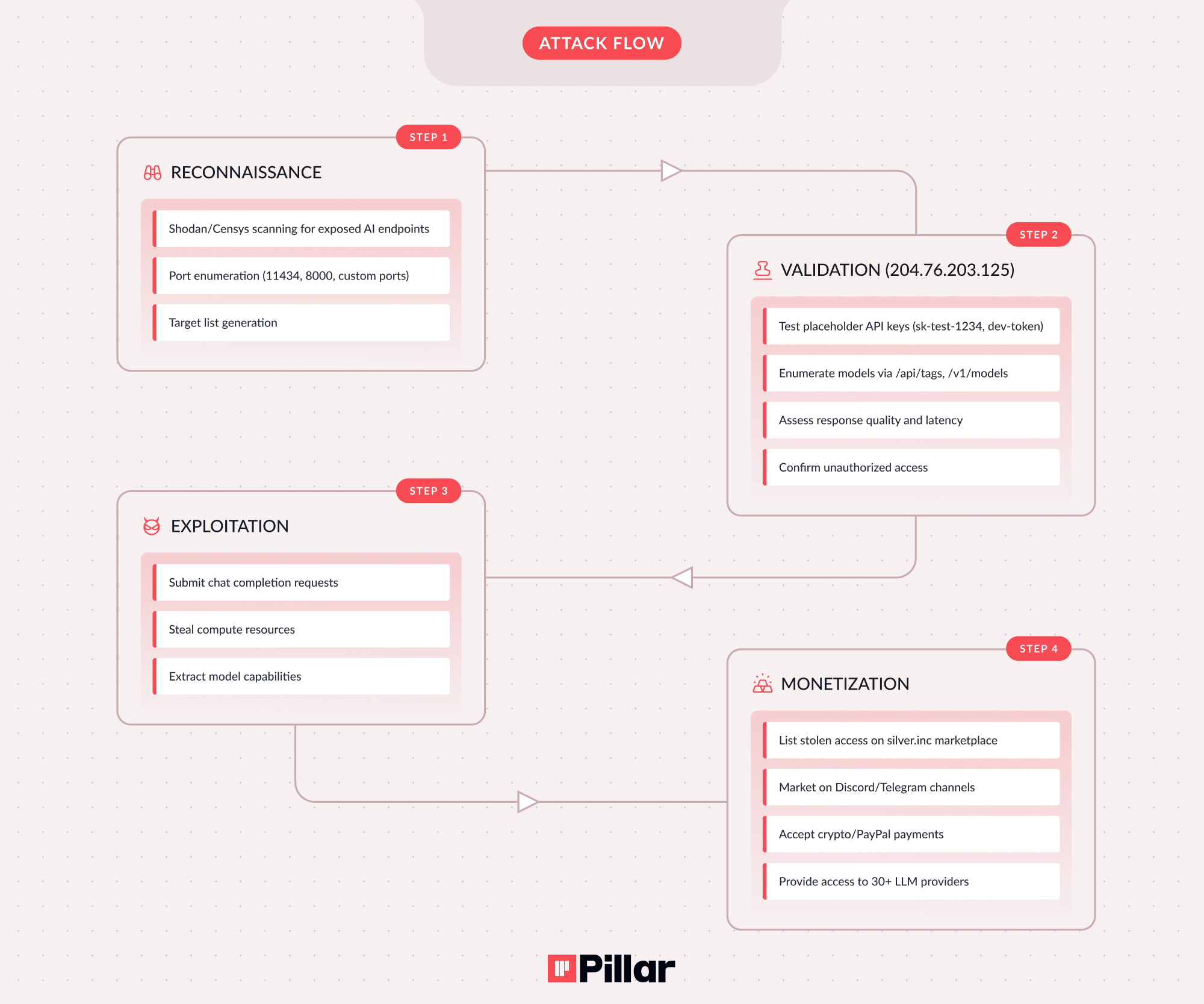
Researchers at Pillar Security report that a malicious campaign is actively targeting exposed LLM service endpoints to commercialize unauthorized access to AI infrastructure.
They recorded more than 35,000 attack sessions on their honeypots, which led to discovering a large-scale cybercrime operation that monetizes and exploits access to exposed or poorly authenticated AI endpoints.
They call the campaign 'Bizarre Bazaar' and highlight that it is one of the first examples of ‘LLMjacking’ attacks attributed to a specific threat actor.
Common attack vectors include self-hosted LLM setups, exposed or unauthenticated AI APIs, publicly accessible MCP servers, and development or staging AI environments with public IP addresses. (Bill Toulas / Bleeping Computer)
Related: CSO Online, Pillar Security
According to researchers at Bugcrowd, the vast majority (82%) of ethical hackers now use AI in their workflows, enabling companies to benefit from faster findings, more assessments, broader security coverage, and higher quality reporting.
The bug bounty specialist polled 2000 security researchers worldwide to compile its Inside the Mind of a Hacker report.
It revealed a sharp jump in the share of respondents using AI, up from 64% in 2023. Three-quarters (74%) now believe AI increases the value of their work, virtually unchanged from last year. (Phil Muncaster / Infosecurity Magazine)
Related: SC Magazine, PR Newswire, Bugcrowd
Best Thing of the Day: Gonna Wash Chinese Threats Out of Our Nets
Senior officials at the Defense Department say the Pentagon’s new cyber force generation model will help the military boot out Chinese threats from America’s critical infrastructure networks.
Worst Thing of the Day: Just Ewwww....
An app that purports to help people stop consuming pornography has exposed highly sensitive data, including its users’ masturbation habits.




