The interim head of CISA uploaded sensitive documents to ChatGPT
Koreans to be notified of possible data breaches, Operations at Russian security systems outfit were disrupted by a cyberattack, EU-India security deal omits hackers-for-hire, Threat actors exploit a high-severity vulnerability in WinRAR, Mustang Panda can steal login data from browsers, much more


Paid subscribers receive full access to Metacurity’s archives and selected analytical deep dives
Don't miss out on the full range of what Metacurity has to offer. Upgrade to a paid subscription, gain access to our archives and special content, and stay current while helping to keep independent media alive.
If you can't afford a paid subscription, donate what you can to keep this vital resource going.
According to sources, Madhu Gottumukkala, the interim head of the country’s cyber defense agency, uploaded sensitive contracting documents into a public version of ChatGPT last summer, triggering multiple automated security warnings that are meant to stop the theft or unintentional disclosure of government material from federal networks.
The apparent misstep from Madhu Gottumukkala was especially noteworthy because the acting director of the Cybersecurity and Infrastructure Security Agency had requested special permission from CISA’s Office of the Chief Information Officer to use the popular AI tool soon after arriving at the agency this May, three of the officials said. The app was blocked for other DHS employees at the time.
None of the files Gottumukkala plugged into ChatGPT were classified, according to the four officials, each of whom was granted anonymity for fear of retribution. But the material included CISA contracting documents marked “for official use only,” a government designation for information that is considered sensitive and not for public release.
Cybersecurity sensors at CISA flagged the uploads this past August, said the four officials. One official specified there were multiple such warnings in the first week of August alone. Senior officials at DHS subsequently led an internal review to assess if there had been any harm to government security from the exposures, according to two of the four officials.
It is not clear what the review concluded. (John Sakellariadis / Politico)
Related: r/cybersecurity, r/artificial, r/USNEWS, r/politics, r/UnderReportedNews, r/fednews
Korean users will now be notified if they are involved in “possible” data leaks, not just definitive cases, and potential threats to their personal information under a new set of data protection measures.
Notifications will include information on how to seek compensation for damages.
The government announced during a ministerial meeting on Wednesday that it will gradually implement this cybersecurity framework.
The measures focus on high-priority tasks that can be addressed quickly, and they aim to enhance both user protection and corporate responsibility for data security.
As part of the reforms, the government will revise regulations and alert individuals who may be involved in a data breach, even if the case has not been confirmed. These notifications will include information such as how to file claims for damages.
In addition, the government plans to expand its dispute management system to cover not just personal data leaks but also damages stemming from other types of security breaches. This system will be implemented through a revision to the Act on Promotion of Information and Communications Network Utilization and Information Protection within the year.
Under the plan, the government will also develop sector-specific security models and launch a dedicated emergency team to identify vulnerabilities in AI systems. (JEONG JAE-HONG / Korea JoongAng Daily)
Related: UPI
A cyberattack disrupted operations at Delta, a Russian provider of alarm and security systems for homes, businesses, and vehicles, causing widespread service outages and a wave of customer complaints.
Delta said that it had been hit by a “large-scale, coordinated and well-organized” cyberattack that originated from an unspecified “hostile foreign state.” The company acknowledged temporary disruptions to some services but said there was no evidence that customers’ personal data had been compromised.
“Our architecture was unable to withstand a well-coordinated attack coming from outside the country,” Delta marketing director Valery Ushkov said in a video address, adding that restoring backups was taking time as the company remained under the threat of follow-up attacks.
The company said its technical team was working to restore its systems and expected a full recovery soon. As of Tuesday, Delta’s website and phone lines remained offline, forcing the company to communicate with tens of thousands of customers through its page on the social media platform VKontakte.
The disruption has had tangible consequences for customers. Russian-language Telegram news outlet Baza reported that users began complaining shortly after the incident that their car alarm systems could not be turned off, or that vehicles could not be unlocked at all.
Russian newspaper Kommersant reported that despite Delta’s assurances that most services were operating normally, users continued to describe widespread failures — including remote vehicle start systems malfunctioning, car doors locking unexpectedly, and engines shutting down while in motion. (Daryna Antoniuk / The Record)
Related: Delta, The Cyber Express, Kommersant
The series of agreements signed yesterday by European Commission President Ursula von Der Leyen and Indian Prime Minister Narendra Modi includes a new security and defence partnership between the two parties, which includes a cyber component.
This section specifies that the two partners "deepen the existing Cyber Dialogue, including by enhancing regular exchanges on the cyber security threat landscape".
But behind the scenes, a discreet power struggle has been raging behind the scenes in recent months, led by European cyber diplomats, notably from the European Union Agency for Cybersecurity (ENISA).
European cyber diplomats raised the issue of India's proliferating cyber offensive ecosystem in the form of hackers-for-hire during closed-door sessions of the cyber dialogue with their Indian counterparts.
However, Indian officials dismissed the issue, essentially denying that any such developed ecosystem exists, and maintaining that in any case were it to exist, it must be a private sector initiative and therefore free to operate as it sees fit. (Pierre Gastineau / Intelligence Online)
Related: European Union, Politico Pro, Atlantic Council, The Hindu, IANS, Business Standard, Telegraph India
Google Threat Intelligence Group (GTIG) reports that multiple threat actors, both state-sponsored and financially motivated, are exploiting the CVE-2025-8088 high-severity vulnerability in WinRAR for initial access and to deliver various malicious payloads.
The security issue is a path traversal flaw that leverages Alternate Data Streams (ADS) to write malicious files to arbitrary locations. Attackers have exploited this in the past to plant malware in the Windows Startup folder, for persistence across reboots.
ESET researchers discovered the vulnerability and reported in early August 2025 that the Russia-aligned group RomCom had been exploiting it in zero-day attacks.
GTIG says that exploitation started as early as July 18, 2025, and continues to this day from both state-backed espionage actors and lower-tier, financially motivated cybercriminals.
When opened, WinRAR extracts the ADS payload using directory traversal, often dropping LNK, HTA, BAT, CMD, or script files that execute on user login.
Google also observed financially motivated actors exploiting the WinRAR path-traversal flaw to distribute commodity remote access tools and information stealers such as XWorm and AsyncRAT, Telegram bot-controlled backdoors, and malicious banking extensions for the Chrome browser. (Bill Toulas / Bleeping Computer)
Related: Google Cloud, Cyberscoop, Cyber Security News, Cyber Press, Security Week
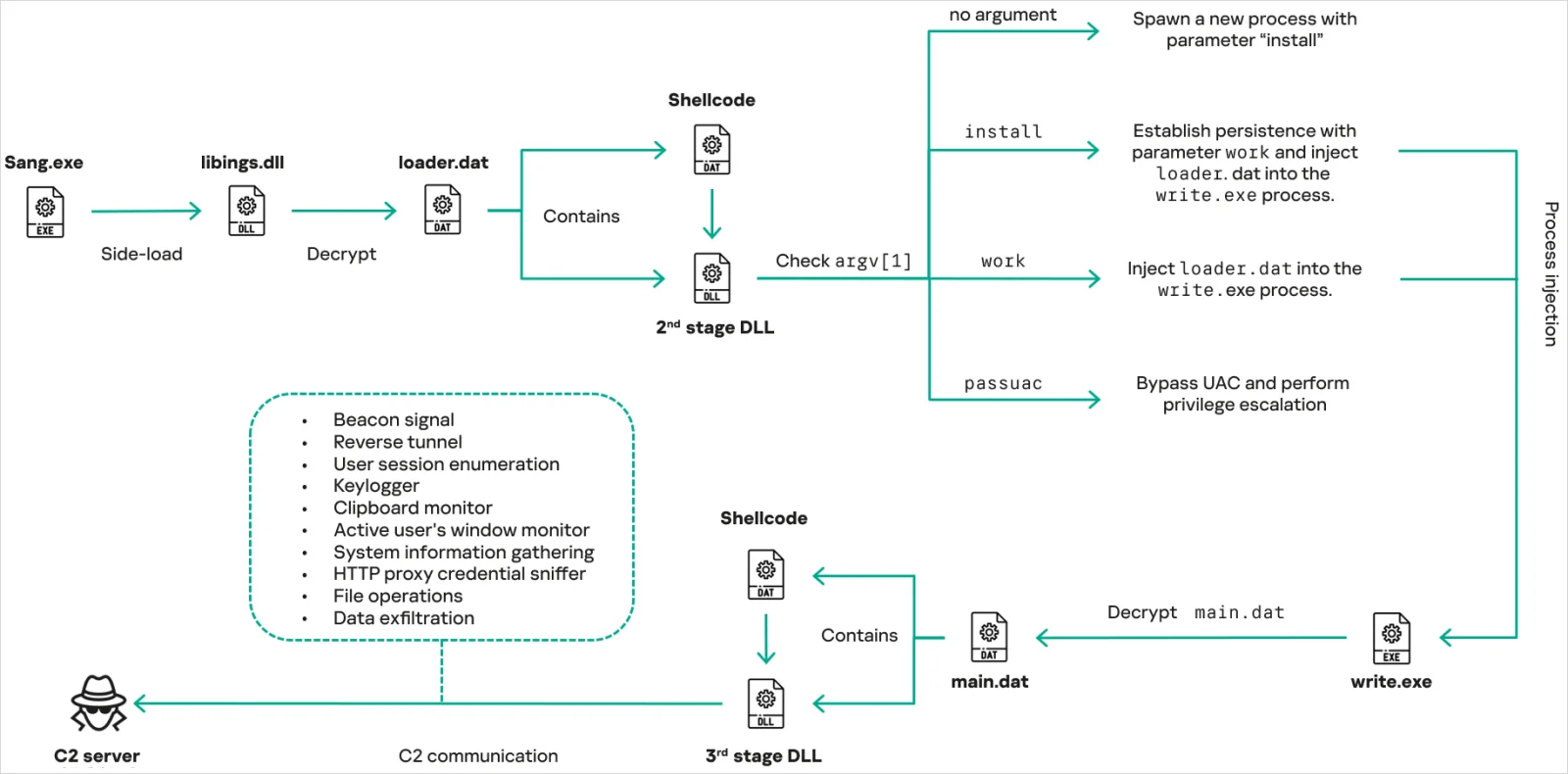
Researchers at Kaspersky report that the Chinese espionage threat group Mustang Panda has updated its CoolClient backdoor to a new variant that can steal login data from browsers and monitor the clipboard.
The malware has also been used to deploy a previously unseen rootkit. However, specialized analysis will be provided in a future report.
CoolClient has been associated with Mustang Panda since 2022, deployed as a secondary backdoor alongside PlugX and LuminousMoth.
The updated malware version has been observed in attacks targeting government entities in Myanmar, Mongolia, Malaysia, Russia, and Pakistan and were deployed via legitimate software from Sangfor, a Chinese company specialized in cybersecurity, cloud computing, and IT infrastructure products.
Previously, CoolClient operators launched the malware via DLL side-loading by abusing signed binaries from Bitdefender, VLC Media Player, and Ulead PhotoImpact.
Kaspersky researchers say that the CoolClient backdoor gathers details about the compromised system and its users, like computer name, version of the operating system, RAM, network information, and the descriptions and versions of loaded driver modules.
CoolClient uses encrypted .DAT files in a multi-stage execution and achieves persistence via Registry modifications, the addition of new Windows services, and scheduled tasks. It also supports UAC bypassing and privilege escalation.
The malware’s core functions, including system and user profiling, file operations, keylogging, TCP tunneling, reverse-proxying, and in-memory execution of dynamically fetched plugins, are available in both old and new versions, but are refined in the most recent variants.
What is entirely new in the latest CoolClient is a clipboard monitoring module, the ability to perform active window title tracking, and HTTP proxy credential sniffing that relies on raw packet inspection and headers extraction. (Bill Toulas / Bleeping Computer)
Related: Cyber Press, Securelist, Cyber Kendra
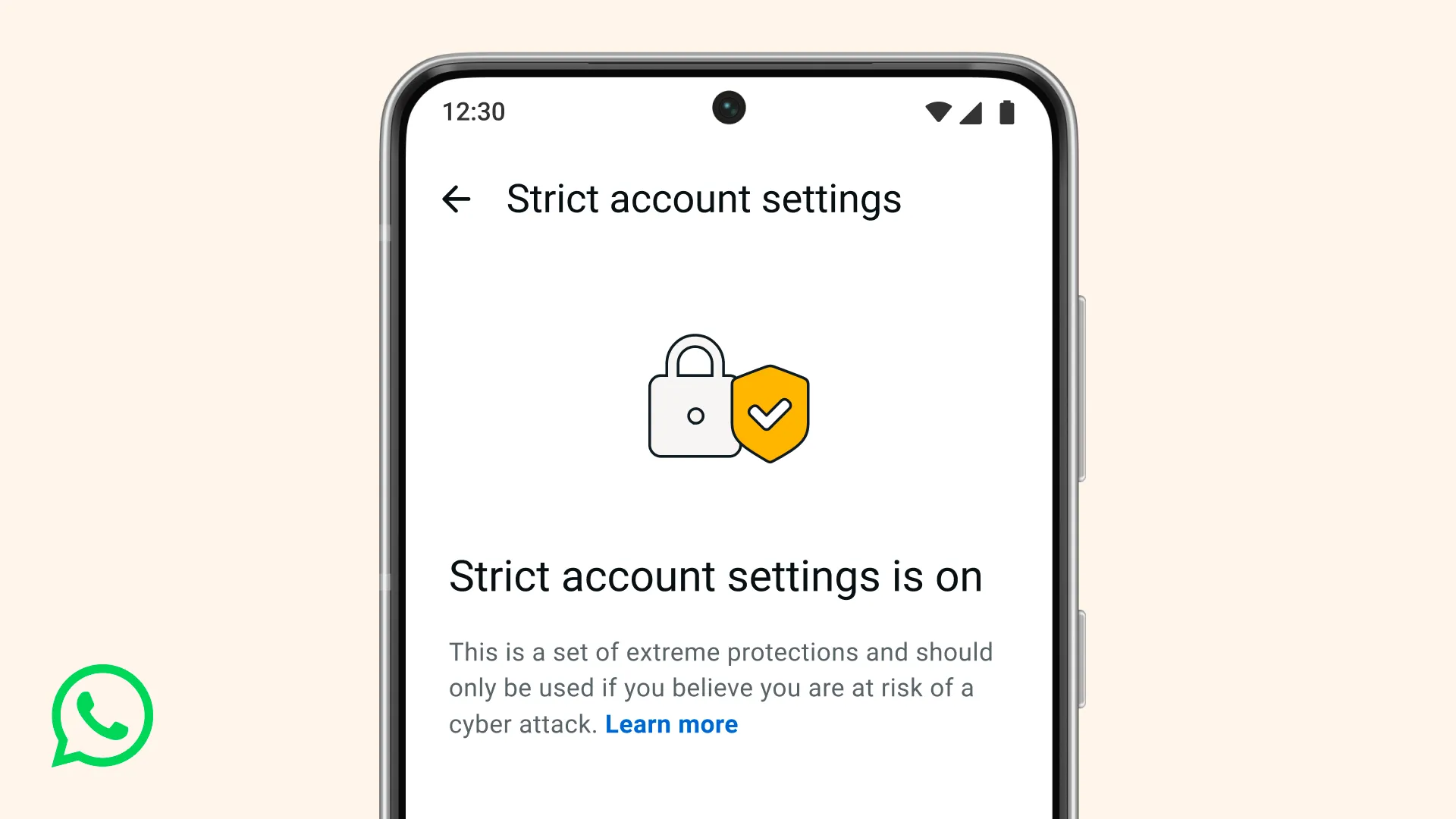
Meta's WhatsApp messaging service is offering users an advanced security mode, joining a growing number of US tech firms that are letting users opt into stronger protections against hackers in exchange for a more restrictive experience.
The new option, called "Strict Account Settings," is a one-click button in WhatsApp's settings that activates a series of defenses.
These include blocking media and attachments from unknown senders, disabling link previews - the thumbnails that appear when a URL is entered into a chat - and silencing calls from unknown contacts.. All three have been identified as potential vectors for surveillance and advanced hackers.
WhatsApp said that while all its users' conversations were protected by end-to-end encryption, "we also know that a few of our users – like journalists or public-facing figures – may need extreme safeguards against rare and highly sophisticated cyberattacks." (Raphael Satter / Reuters)
Related: TechCrunch, WhatsApp Blog, Meta Newsroom, CyberScoop, Security Affairs, The Record, The Verge, Engadget, 9to5Mac, Social Media Today, WABetaInfo, Neowin, The Indian Express, Cybersecurity Insiders, The Register
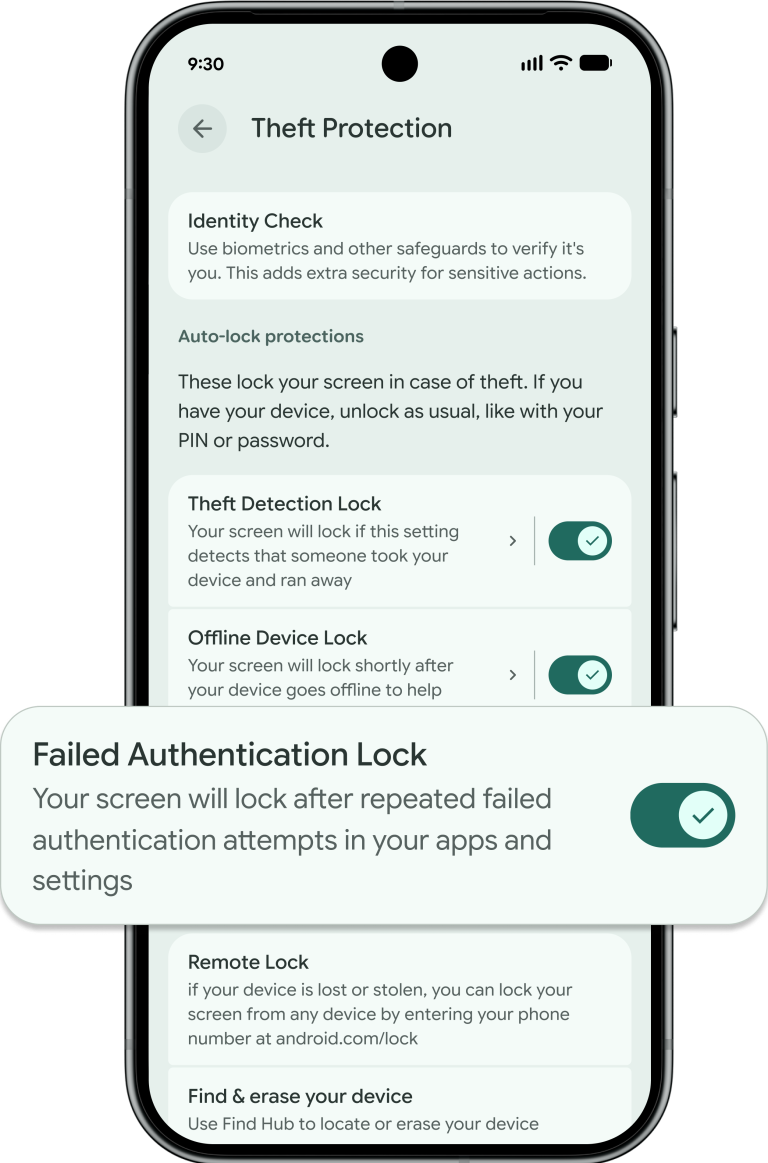
Google announced an expanded set of Android theft-protection features, designed to make its mobile devices less of a target for criminals. Building on existing tools like Theft Detection Lock, Offline Device Lock, and others introduced in 2024, the newly launched updates include stronger authentication safeguards and enhanced recovery tools, the company said.
While iPhones are often the preferred targets for thieves because of their resale value, Android devices are also subject to theft. That’s particularly true for high-end Android smartphones like the Google Pixel Pro devices, premium foldables, and other top devices from well-known makers like Samsung.
With the new features, users of Android devices running Android 16 or higher will have more control over the Failed Authentication Lock feature that automatically locks the device after an excessive number of failed login attempts. Now users will have access to a dedicated on/off toggle switch in the device’s settings.
The devices will also offer stronger protection against a thief trying to guess a device owner’s PIN, pattern, or password by increasing the lockout time after failed attempts. Plus, Identity Check, a feature rolled out for Android 15 and higher last year, now covers all features and apps that use biometrics — like banking apps or the Google Password Manager. (Sarah Perez / TechCrunch)
Related: 9to5Google, Google Online Security Blog, ZDNET, Android Police, PhoneArena, Android Central, BGR, Android Headlines, r/Androidr, Slashdot
The Sanxenxo City Council, in Pontevedra, in the autonomous community of Galicia, is currently experiencing a cyberattack that has resulted in a standoff between the City Council and the hackers who have made their demands known.
The city has signaled plans to move forward without paying the $5,000 BTC ransom required to release encrypted data in an attack that has compromised thousands of administrative documents from the Sa. Asity Council in Spain.
Hackers got into the City Hall’s internal systems on January 26, 2026, locking it up and encrypting thousands of documents. This prevents access to essential information and makes it impossible for officials to work.
The incident has been confirmed by the government itself and cited in local news reports. The hackers reportedly used malware to infiltrate the main network, and as a result of the attack, the municipal server became completely inoperative, affecting essential services for residents that are processed at the main office.
Fortunately, not all areas of the municipality were affected by the attack. The municipal companies Nauta and Turismo were unaffected by the attack, but this is reportedly because they operate on independent networks.
The City Hall’s online portal also remained operational, allowing citizens to continue their procedures online. (Hannah Collymore / Cryptopolitan)
Related: CriptoNoticias, Diario de Pontevedra, CryptoRank
Israeli cybersecurity company Memcyco has raised $37 million in a Series A venture funding round.
NAventures led the round with participation from existing investors Capri Ventures and Venture Guides. (Meir Orbach / CTech)
Related: Business Wire, Globes, Tech Funding News, Axios, Memcyco
Cyber company Rein Security has raised $8 million in a seed venture funding round.
The round was led by Glilot Capital. (Meir Ohrbach / Calcalist)
Related: Silicon Angle, PR Newswire
Best Thing of the Day: Baby Steps in France
The French government announced that it will stop using American video conferencing platforms such as Microsoft Teams and Zoom, and replace them with Visio, a French platform.
Worst Thing of the Day: ICE Wants Everyone to Feed Its Beast
Not content with having a budget larger than most countries' militaries, access to vast US government databases, and amazingly sophisticated surveillance technologies, ICE now wants to track its targets using advertising and technology databases.
Bonus Worst Thing of the Day: This Judge Doesn't Care About No Stinking Warrants
Virginia federal judge Mark Davis ruled that the warrantless use of 176 Flock automated license plate reader (ALPR) cameras in Norfolk, Virginia, is constitutional and dismissed a case seeking to eradicate them.
Closing Thought