Treasury cancels Booz Allen contracts ostensibly over inadequate data security
Salt Typhoon hacked senior UK officials for years, Pegasus spyware victim awarded $4.1m over Pegasus infection, US Marshals are probing alleged theft of $40m in confiscated digital assets, Nike is investigating a potential data breach, UK radically ups number of facial recognition vans, much more


Paid subscribers receive full access to Metacurity’s archives and selected analytical deep dives
Don't miss out on the full range of what Metacurity has to offer. Upgrade to a paid subscription, gain access to our archives and special content, and stay current while helping to keep independent media alive.
If you can't afford a paid subscription, donate what you can to keep this vital resource going.
Treasury Secretary Scott Bessent said he had canceled all Treasury Department contracts with the consulting firm Booz Allen Hamilton, whose employee leaked the tax records of President Donald Trump, and the billionaires Jeff Bezos and Elon Musk, to media outlets.
The department said it currently has 31 separate contracts with Booz Allen Hamilton, totaling $4.8 million in annual spending and $21 million in total obligations.
“President Trump has entrusted his cabinet to root out waste, fraud, and abuse, and canceling these contracts is an essential step to increasing Americans’ trust in government,” Bessent said.
“Booz Allen failed to implement adequate safeguards to protect sensitive data, including the confidential taxpayer information it had access to through its contracts with the Internal Revenue Service,” he said.
The department noted that between 2018 and 2020, Booz Allen employee Charles Edward Littlejohn “stole and leaked the confidential tax returns and return information of hundreds of thousands of taxpayers.”
The data breach affected about 406,000 taxpayers, according to the IRS.
Littlejohn pleaded guilty in October 2023 to one count of disclosure of tax return information.
He admitted leaking Trump’s tax records to The New York Times. He also admitted to leaking records about wealthy individuals to the news outlet ProPublica.
He was sentenced to the maximum term of five years in prison in January 2024.
Booz Allen, in a statement Monday, said, “We have consistently condemned in the strongest possible terms the actions of Charles Littlejohn, who was active with the company years ago.”
“Booz Allen has zero tolerance for violations of the law and operates under the highest ethical and professional guidelines. When Littlejohn’s criminal conduct occurred over 5 years ago, it was on government systems, not Booz Allen systems,” the company said. (Dan Mangan / CNBC)
Related: Forbes, Treasury Department, NPR, The Hill, Associated Press, Business Insider, Axios, Reuters, The Wall Street Journal, Financial Times, NextGov/FCW, Barron's, Zero Day
Sources say the Chinese hacking group Salt Typhoon hacked the mobile phones of senior officials in Downing Street for several years.
The spying operation is understood to have compromised senior members of the government, exposing their private communications to Beijing.
State-sponsored hackers are known to have targeted the phones of some of the closest aides to Boris Johnson, Liz Truss, and Rishi Sunak between 2021 and 2024.
It is unclear whether the hack included the mobile phones of the prime ministers themselves, but one source with knowledge of the breach said it went “right into the heart of Downing Street."
Intelligence sources in the US indicated that the Chinese espionage operation, known as Salt Typhoon, was ongoing, raising the possibility that Sir Keir Starmer and his senior staff may also have been exposed. MI5 issued an “espionage alert” to Parliament in November about the threat of spying from the Chinese state.
Sir Keir departs for China this week – the first visit by a British prime minister since Baroness May in 2018 – to secure trade and investment ties with Beijing. (Rozina Sabur and Gordon Rayner / The Telegraph)
Related: WION, TRT World, LBC, Nova News, The Times
UK High Court Judge Pushpinder Saini ordered Saudi Arabia to pay more than £3m (around $4.1 million) in damages to London-based dissident Ghanem al-Masarir, whose phones were targeted with Pegasus spyware.
The judge ruled that al-Masarir was entitled to compensation for psychiatric harm sustained after discovering that his iPhones had been hacked, as well as a physical attack on him outside Harrods in central London.
Saini said there was “a compelling basis for concluding that the claimant’s iPhones were hacked by Pegasus spyware, which resulted in the exfiltration of data from those mobile phones, and that this conduct was directed or authorised by the KSA [Kingdom of Saudi Arabia] or agents acting on its behalf."
The judge also found, on the balance of probabilities, that Saudi Arabia was responsible for the 2018 physical attack on al-Masarir, a 45-year-old satirist also known as Ghanem al-Dosari, whose YouTube channels have garnered more than 300 million views.
“The KSA had a clear interest in and motivation to shut down the claimant’s public criticism of the Saudi government,” Saini said.
Al-Masarir said the ruling “brings a long and painful chapter to a close. It affirms that standing up for the truth, no matter how powerful the opponent, is worth the struggle. No amount of money can undo what I have suffered, but I hope the Kingdom of Saudi Arabia will now do the right thing and comply with this judgment, without the need for further enforcement action.” (Haroon Siddique and Stephanie Kirchgaessner / The Guardian)
Related: Reuters, Leigh Day, The Record
The US Marshals Service (USMS) is investigating allegations that John "Lick" Daghita, the son of a Department of Defense and Department of Justice services provider, Dean Daghita, president of a firm called CMDSS, who is charged with managing cryptocurrency seized by law enforcement, stole more than $40 million worth of confiscated digital assets.
Blockchain investigator ZachXBT accused Daghita of stealing the seized digital assets from crypto wallets managed by his father's company.
ZachXBT, who said he reported John to authorities, stated it remains unclear how John Daghita allegedly obtained access to the wallets, including whether that access came through his father.
Brady McCarron, chief of public affairs for the USMS, told CoinDesk that the agency could not comment further on this case because investigations were underway.
“Meet the threat actor John (Lick), who was caught flexing $23M in a wallet address directly tied to $90M+ in suspected thefts from the US Government in 2024 and multiple other unidentified victims from Nov 2025 to Dec 2025,” ZachXBT posted on X last Friday.
ZachXBT identified the individual as John Daghita, claiming CMDSS currently holds an active federal IT contract. The blockchain investigator later said he reported a wallet address holding 12,540 ETH, worth roughly $36.3 million, which he said was controlled by Daghita. ZachXBT added that Daghita sent him 0.6767 ETH, which he said he would forward to a US government seizure address. (Olivier Acuna / CoinDesk)
Related: TRM Labs, Web3IsGoingJustGreat, crypto.news, The Block, ForkLog, Bitcoin Magazine, BeInCrypto, CryptoRank
Nike says it is investigating a potential data breach after the ransomware group WorldLeaks claimed to have leaked a trove of data related to its business operations.
"We always take consumer privacy and data security very seriously," Nike said in a statement. "We are investigating a potential cyber security incident and are actively assessing the situation." (Nicholas P. Brown and Raphael Satter / Reuters)
Related: The420, The Cyber Express, The Register, PYMNTS, Security Week
Under proposals from Shabana Mahmood, the UK Secretary of State for the Home Department, dozens of new facial live recognition vans will be delivered to police forces under sweeping reforms announced by the Home Secretary.
The current number of 10 vans will rise to 50, and will be overseen by a national centre on artificial intelligence (AI).
The move comes as part of significant changes revealed in the Government's White Paper on police reforms, which seeks to create a "British FBI", called the National Police Service (NPS), and drastically cut the number of police forces.
Ms Mahmood also announced in the Commons that all forces across England and Wales will be given AI tools to help reduce the amount of time that officers must spend behind a desk, allowing them to be on the beat more instead. (Sky News)
Related: BBN Times, The Independent, The Mirror, BBC News
Korea’s Board of Audit and Inspection found that hackers breached all seven public-sector systems tested in a simulated cyberattack, exposing serious weaknesses in the government's protection of large volumes of personal data.
The Board said that the findings came from penetration tests conducted with white-hat hackers and national security agencies. In one case, auditors were able to access resident registration numbers for nearly the entire population.
The results were released in an audit report on personal data protection and management. The on-site inspections took place in November and December 2024.
The tests were carried out jointly by the Board of Audit and Inspection, the National Security Research Institute, and the Cyber Operations Command. The targets were seven of the 123 public systems designated by the Personal Information Protection Commission (PIPC) for intensive management, selected for their public-facing services and the large amount of personal data they hold.
In one system, the board said it was possible to query resident registration numbers and other information for around 50 million people — meaning that the resident registration numbers of virtually all citizens could have been stolen.
In another system, hackers could steal the data of 10 million members within 20 minutes. The board also said it identified a public system where critical information needed to access the system was not encrypted, allowing a hacker who obtained administrator privileges to steal the resident registration numbers of 130,000 people.
Security vulnerabilities were found in all seven systems that were tested, allowing them to be breached. (YOON SUNG-MIN / Korea JoongAng Daily)
Related: Chosun Biz, Seoul Economic Daily, Maeil Business Newspaper, BusinessKorea
The official Australian ABC News Facebook account was compromised, distributing an explicit image of pornographic actress Bonnie Blue, among other lewd material, before the broadcaster pulled the posts down.
The national broadcaster confirmed it was investigating after a “compromised staff account” resulted in unauthorised access to the page, which has 4.9 million followers and posts regular links to ABC reporting.
The hack occurred just after 1 pm on Tuesday. The hacker changed the page’s cover photo to an image of Blue, real name Tia Billinger, a provocative OnlyFans and porn actress who was recently deported from Bali and has been criticised for making a point of having sex with 18-year-olds.
An ABC spokesperson said: “Access was quickly secured, the content removed, and an investigation is under way to review and strengthen our security controls.”
The hackers also posted an image of another porn actress, as well as an image of Prime Minister Anthony Albanese eating a hot dog. (Calum Jaspan / Sydney Morning Herald)
Related: The Age, News.com, 9News, MediaWeek, The Nightly
BTC Prague co-founder Martin Kuchař disclosed that North Korea-linked hackers continue to use live video calls, including AI-generated deepfakes, to trick crypto developers and workers into installing malicious software on their own devices.
The attackers used a compromised Telegram account and a staged video call to push malware disguised as a Zoom audio fix, he said.
The “high-level hacking campaign” appears to be “targeting Bitcoin and crypto users,” Kuchař said.
Attackers contact the victim and set up a Zoom or Teams call, Kuchař explained. During the call, they use an AI-generated video to appear as someone the victim knows.
They then claim there is an audio problem and ask the victim to install a plugin or file to fix it. Once installed, the malware grants attackers full system access, allowing them to steal Bitcoin, take over Telegram accounts, and use those accounts to target others. (Vince Dioquino / Decrypt)
Related: CryptoNinjas
Google agreed to pay $68 million to settle a lawsuit claiming that its voice-activated assistant spied inappropriately on smartphone users, violating their privacy.
A preliminary class action settlement was filed late Friday night in the San Jose, California federal court, and requires approval by US District Judge Beth Labson Freeman.
Smartphone users accused Google of illegally recording and disseminating private conversations after Google Assistant was triggered, in order to send them targeted advertising.
Google Assistant is designed to react when people use "hot words" such as "Hey Google" or "Okay Google," similar to Apple's Siri.
Users objected to receiving ads after Google Assistant misperceived what they said as hot words, known as "false accepts."
Apple reached a similar $95 million settlement with smartphone users in December 2024.
Google denied wrongdoing, but settled to avoid the risk, cost, and uncertainty of litigation, court papers show. (Jonathan Stempel / Reuters)
Related: Court Listener, The Record, The Guardian, PYMNTS
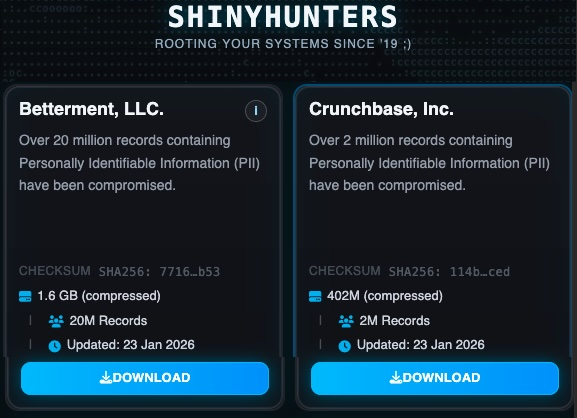
Market intelligence firm Crunchbase has confirmed a data breach after hackers published files allegedly stolen from its systems.
The notorious ShinyHunters cybercrime group claims to have stolen more than 2 million records containing personal information from Crunchbase.
The hackers have made available more than 400 MB of compressed files for download on their website after the company refused to pay a ransom.
“Crunchbase detected a cybersecurity incident where a threat actor exfiltrated certain documents from our corporate network. This incident has disrupted no business operations. We have contained the incident, and our systems are secure,” Crunchbase said.
“Upon detecting the incident we engaged cybersecurity experts to assist us and we contacted federal law enforcement. Crunchbase is aware that the threat actor posted certain information online. As part of our incident response procedures, we are reviewing the impacted information to determine if any notifications are required consistent with applicable legal requirements,” it added.
Alon Gal, CTO of threat intelligence company Hudson Rock, has analyzed the leaked Crunchbase data and found personally identifiable information (PII), contracts, and other corporate data.
The ShinyHunters leak website also lists SoundCloud and the robo-advisor firm Betterment, from which the hackers claim to have stolen several gigabytes of files containing tens of millions of records that include PII. (Eduard Kovacs / Security Week)
Related: Security Affairs, Beta News, Bleeping Computer, The Cyber Express
Microsoft has released emergency out-of-band security updates to patch a high-severity Microsoft Office zero-day vulnerability exploited in attacks.
The security feature bypass vulnerability, tracked as CVE-2026-21509, affects multiple Office versions, including Microsoft Office 2016, Microsoft Office 2019, Microsoft Office LTSC 2021, Microsoft Office LTSC 2024, and Microsoft 365 Apps for Enterprise (the company's cloud-based subscription service).
However, as noted in today's advisory, security updates for Microsoft Office 2016 and 2019 are not yet available and will be released as soon as possible.
While the preview pane is not an attack vector, unauthenticated local attackers can still successfully exploit the vulnerability through low-complexity attacks that require user interaction.
"Reliance on untrusted inputs in a security decision in Microsoft Office allows an unauthorized attacker to bypass a security feature locally. An attacker must send a user a malicious Office file and convince them to open it," Microsoft explained. (Sergiu Gatlan / Bleeping Computer)
Related: Microsoft, Microsoft, Microsoft, PCMag, The Cyber Express, Neowin, Security Affairs, Newsbytes, CSO Online
Computers with Telnet open are in immediate danger of being compromised due to a critical vulnerability that allows attackers to bypass authentication.
The Telnet remote access protocol has long been superseded by the more secure and encrypted SSH, but many IoT and embedded devices have continued to ship with Telnet exposed on the LAN interface for debugging purposes over the years.
Making things worse, the vulnerability, now tracked as CVE-2026-24061, is trivial to exploit remotely, and because it has existed in the codebase for the past 11 years since version 1.9.3, it likely impacts many devices that are no longer supported and will not receive firmware updates.
“The telnetd server invokes /usr/bin/login (normally running as root), passing the value of the USER environment variable received from the client as the last parameter,” Simon Josefsson, a GNU contributor who submitted the patch, said on the OSS-SEC mailing list. “If the client supplies a carefully crafted USER environment value being the string “-f root”, and passes the telnet(1) -a or --login parameter to send this USER environment to the server, the client will be automatically logged in as root, bypassing normal authentication processes.”
In other words, the exploit is achieved with the simple command: USER=‘-f root’ telnet -a [host_ip]. This not only works against remote systems, but it can also serve as a privilege escalation exploit on the local machine if the telnet service (telnetd) is running. (Lucian Constantin / CSO Online)
Related: Seclists, Bleeping Computer
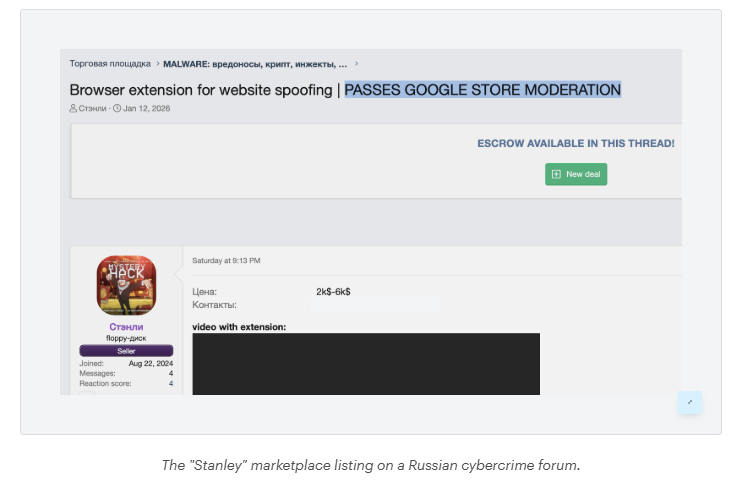
Researchers at Varonis report that a new malware toolkit offered on an underground cybercrime forum can keep the browser’s address bar unmodified while serving phishing pages.
Dubbed Stanley, the malware-as-a-service (MaaS) toolkit is priced from $2,000 to $6,000, and was first spotted on January 12, in a post claiming it can create extensions that bypass Google Store validation.
The top-tier pricing provides threat actors with customization options, a management panel, and guaranteed publication on the Chrome Web Store, Varonis has discovered.
“That guarantee is the commercial center of gravity here: it shifts distribution risk away from the buyer and implies the seller has a repeatable way to clear Google’s review process,” the cybersecurity firm notes.
A web-based management interface provides miscreants with a view of infected hosts, displaying information such as IP addresses (used as identifiers), online status, browser history status, and last activity timestamp.
It also allows operators to select individual targets and to configure specific URL hijacking rules for them, which include the source/legitimate URL and the target/phishing URL.
“Rules can be activated or deactivated per infection, allowing operators to stage attacks and trigger them on demand,” Varonis explains.
More importantly, a victim will see in the browser’s address bar the legitimate URL they try to access, while they, in fact, interact with the attacker-controlled content. (Ionut Arghire / Security Week)
Related: Varonis, Bleeping Computer, HackRead, Cyber Security News, Cyber Insider
Researchers at Silent Push say that threat group ShinyHunters has targeted around 100 organizations in its latest Okta single sign-on (SSO) credential stealing campaign, according to researchers and the criminal group itself.
The identity-theft operation set its sights on more than 100 Okta SSO accounts across "high-value enterprises." The cyber threat hunters also listed all of the companies across which they have "detected active targeting or infrastructure preparation directed at your domain" in the last 30 days.
The enterprises include technology and software firms, including Atlassian, AppLovin, Canva, Epic Games, Genesys, HubSpot, Iron Mountain, RingCentral, and ZoomInfo.
To be clear: this doesn't mean any of these companies have been breached. "We have no intel to share on any specific attacks and are unable to confirm if any have been successful," Silent Push senior threat researcher Zach Edwards said. "We do believe the orgs we've listed on our public blog have been targeted."
ShinyHunters would not confirm how many companies it has breached using their Okta SSO credentials, nor say how many have been targeted in the campaign, but did say that 100 was "close."
Google's Mandiant also confirmed that it's "tracking a new, ongoing ShinyHunters-branded campaign." It uses "evolved" voice-phishing techniques to "compromise SSO credentials from victim organizations, and enroll threat actor-controlled devices into victim MFA solutions," Mandiant Consulting CTO Charles Carmakal said. (Jessica Lyons / The Register)
Related: Silent Push
The Cybersecurity and Infrastructure Security Agency is hoping to guide federal agencies through the murky process of updating their technology stack with quantum-resistant encryption.
On Jan. 23, the agency released a list of different IT software and hardware products that are commonly purchased by the federal government and use cryptographic algorithms for encryption or authentication.
The guidance covers cloud services like Platform-as-a-Service and Infrastructure-as-a-Service, collaboration software, web software like browsers and servers, and endpoint security tools that provide full disk and at-rest data encryption.
CISA pointed to these products as examples where hardware and software post-quantum cryptography standards are “widely available” and designed “to protect sensitive information…including after the advent of a cryptographically relevant quantum computer (CRQC).” (Derek B. Johnson / CyberScoop)
Related: CISA, The Quantum Insider, Industrial Cyber, ExecutiveGov, MeriTalk, CSO Online
Researchers at BlackPoint Cyber report that a new malicious campaign mixes the ClickFix method with fake CAPTCHA and a signed Microsoft Application Virtualization (App-V) script to ultimately deliver the Amatera infostealing malware.
The Microsoft App-V script acts as a living-off-the-land binary that proxies the execution of PowerShell through a trusted Microsoft component to disguise the malicious activity. While App-V scripts have been leveraged in the past to evade security solutions, this is the first time this type of file has been observed in ClickFix attacks that deliver an information stealer.
The attack begins with a fake CAPTCHA human verification check that instructs the victim to manually paste and execute a command via the Windows Run dialog.
In the later stages of the attack, a 32-bit hidden PowerShell process is spawned via the Windows Management Instrumentation (WMI) framework, and multiple embedded payloads are decrypted and loaded into memory.
The infection chain then shifts to hiding payloads using steganography, where an encrypted PowerShell payload is embedded in PNG images hosted on public CDNs and retrieved dynamically via resolved WinINet APIs.
To defend against these attacks, the researchers propose restricting access to the Windows Run dialog via Group Policy, removing App-V components when not needed, enabling PowerShell logging, and monitoring outbound connections for mismatches between the HTTP Host header or TLS SNI and the destination IP. (Bill Toulas / Bleeping Computer)
Related: BlackPoint Cyber, HackRead

The White House rescinded a 2022 order that mandated a single, standardized self-attestation form for federal agencies to obtain cybersecurity assurances from software vendors, arguing the policy hindered agencies from adopting security solutions for their specific system needs.
“There is no universal, one-size-fits-all method of achieving that result,” Office of Management and Budget Director Russ Vought said in the memo released Friday. “Each agency should validate provider security utilizing secure development principles and based on a comprehensive risk assessment.”
Former President Joe Biden signed the landmark Executive Order 14028 in May 2021, which led to the issuance of the original memo. The directive was meant to respond to the massive SolarWinds intrusion campaign that compromised multiple federal agencies.
A software attestation is typically a statement from a vendor outlining the security controls and development practices used to build a software product. It can assist government customers in understanding their exposure to supply-chain risk and clarify responsibility when vulnerabilities or breaches emerge.
The “unproven and burdensome” process “diverted agencies from developing tailored assurance requirements for software and neglected to account for threats posed by insecure hardware,” the new Vought memo says. (David DiMolfetta / NextGov/FCW)
Related: White House, MeriTalk
Best Thing of the Day: It's Not Nice to Illegally Track Children
After urging from the privacy group noyb, the Austrian data protection authority (DSB) has decided that Microsoft illegally installed cookies on the devices of a young pupil without consent and ordered the company to cease tracking the complainant within four weeks.
Worst Thing of the Day: Cartoonishly Evil Is the Watchword for This
If proposed White House policies affecting Customs and Border Police (CBP) go into effect, millions of travellers to the US will be forced to use a US government mobile phone app, submit their social media from the last five years, and email addresses used in the last ten years, including those of family members, while also possibly being required to provide DNA.
Closing Thought