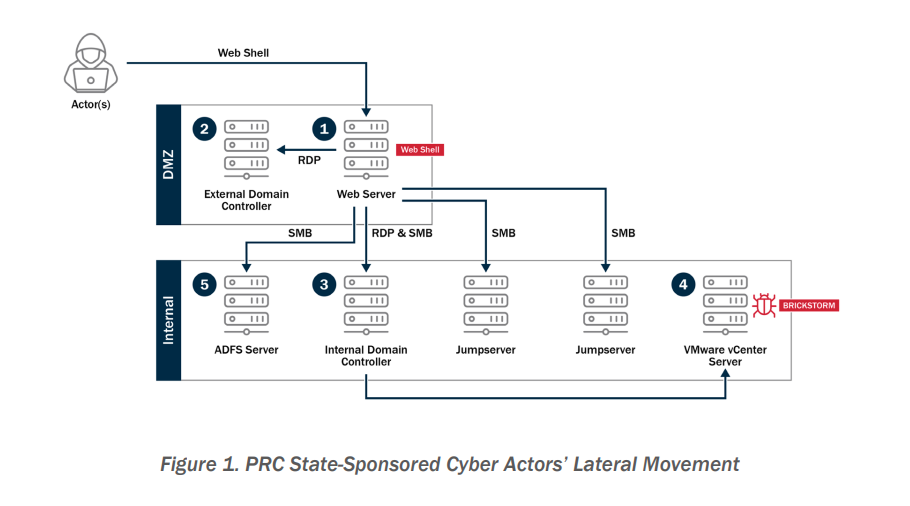
US, Canada warn of Chinese-linked Brickstorm malware that gains long-term access
Intellexa had access to personal data of Predator spyware targets, Int'l partners release AI security guide for OT orgs, Phreeli cellco doesn't ask for identifying info, Taiwan suspends Rednote over fraud cases, Albiriox Android malware evolves quickly, NCSC debuts proactive notifications, much more