US House of Representatives bans WhatsApp on security grounds
US Cybercom played a role in Iran attack, Crypto scam services return after Telegram beheading, NoName DDoS'ed Dutch cities ahead of NATO summit, REvil members released in Russia, Coinbase poseur stole millions from crypto holders, Critical infrastructure defense project disbanded, much more


Don't miss my latest CSO piece that examines how the Iranian cyber threat has been overhyped, and despite a supposed cease-fire between Israel and Iran, CISOs still need to protect their organizations from the Iranian threats that do exist.
Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
The US House's chief administrative officer (CAO) informed congressional staffers that the messaging app WhatsApp is banned on their government devices.
"The Office of Cybersecurity has deemed WhatsApp a high-risk to users due to the lack of transparency in how it protects user data, absence of stored data encryption, and potential security risks involved with its use," the CAO said in an email.
The CAO said that Microsoft Teams, Wickr, Signal, iMessage, and FaceTime are all acceptable alternatives to WhatsApp.
Andy Stone, a spokesperson for WhatsApp parent company Meta, said, "We disagree with the House Chief Administrative Officer's characterization in the strongest possible terms."
We know members and their staffs regularly use WhatsApp and we look forward to ensuring members of the House can join their Senate counterparts in doing so officially," Stone said. (Andrew Solender / Axios)
Related: The Verge, CNBC, The Guardian, Reuters, Financial Times, Silicon Angle, The Hill, Social Media Today, Engadget, Mashable, MediaPost, EuroWeekly News, WebProNews
Top Pentagon officials said that US Cyber Command played a role in the American military’s operation against Iranian nuclear facilities over the weekend.
“The strike package was supported by US Strategic Command, US Transportation Command, US Cyber Command, US Space Command, US Space Force and US European command,” Gen. Dan Caine, chairman of the Joint Chiefs of Staff, told reporters in a briefing at the Pentagon Sunday morning, later thanking the cyber operators, among others, who made the mission possible.
Although details about Cybercom’s assistance with Operation Midnight Hammer, the code name for the strikes, remain murky, experts outlined several possibilities for how the organization may have contributed to the effort.
One former official said one of the most likely ways Cybercom would have aided the operation is through something akin to a cyber escort package. With air assets coming from all over the world and various commands, such as Transportation Command, European Command, Central Command, and the Air Force’s Global Strike Command, it is essential to ensure that those aircraft and enabling functions execute missions smoothly. (Mark Pomerleau / DefenseScoop)
Related: WRDW, The Independent
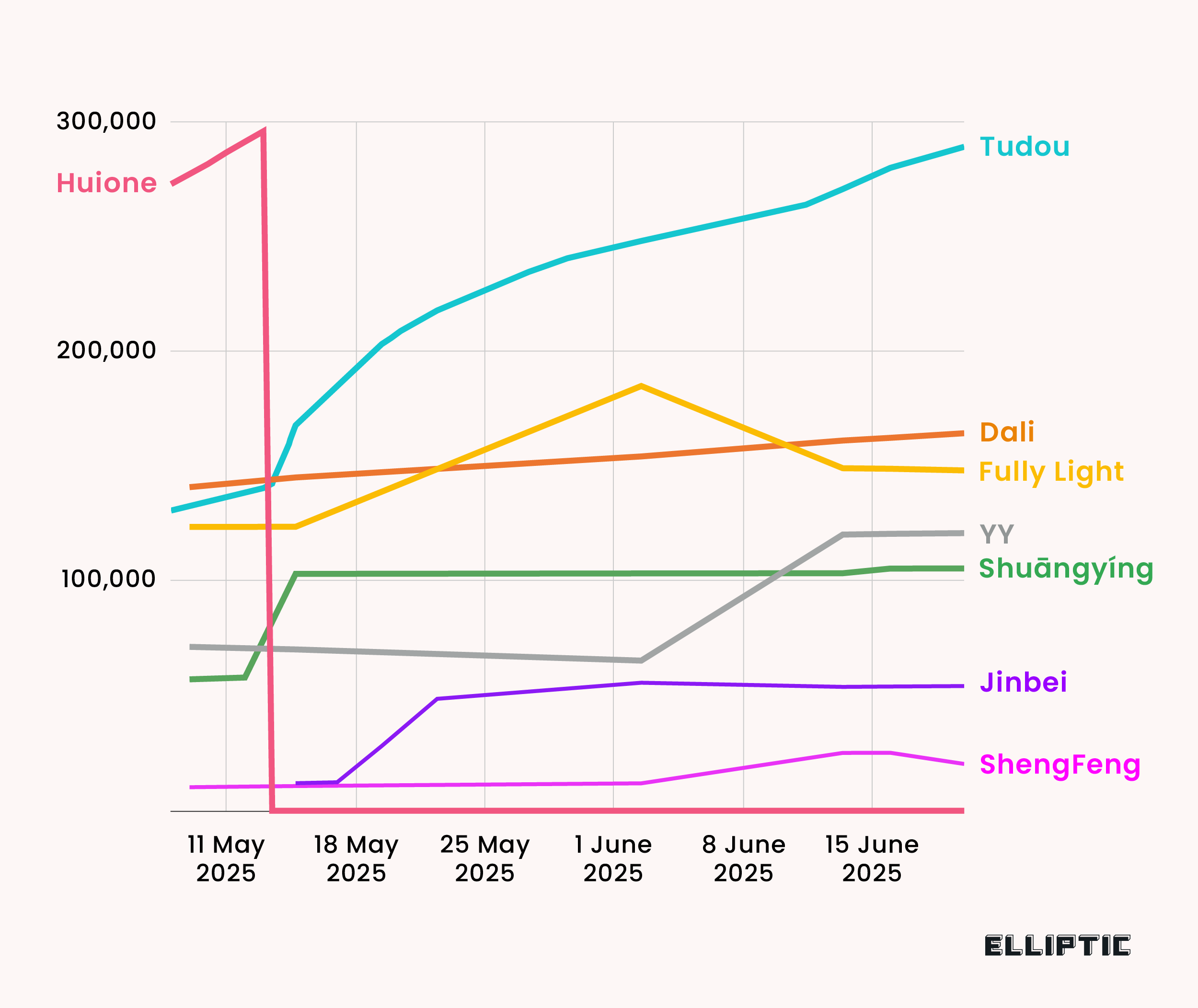
Researchers at Ellptic report that since last month, when Telegram summarily beheaded the online industry of Chinese-language crypto scam services such as Haowang Guarantee and Xinbi Guarantee, it has watched impassively as those black marketeers rebranded, rebuilt, and returned to business as usual on the messaging service's platform.
Before Telegram banned the two markets' channels and usernames on May 13, they had together enabled a staggering $35 billion in transactions, much of which represented money laundering by crypto scam operations that steal billions from Western victims and force tens of thousands of people to carry out scams in forced labor compounds across Cambodia, Myanmar, and Laos.
In particular, one market called Tudou Guarantee, partially owned by Huione Group, the same parent company as the now-defunct Haowang Guarantee, has more than doubled in size. It likely takes in many of the scammer-friendly services displaced by Telegram's bans and again enables those fraudsters' billions of dollars a year in illicit revenue.
By Elliptic's count, its main channel now has 289,000 users, close to the 296,000 users that Haowang Guarantee had at the time Telegram banned it. Xinbi Guarantee, too, has relaunched on new channels and regained hundreds of thousands of users, Elliptic says. In terms of sales, Tudou is now enabling around $15 million a day in crypto payments, close to the $16.4 million Haowang was facilitating daily, according to Elliptic. (Andy Greenberg / Wired)
Related: Elliptic, Cryptoslate, Cointelegraph, crypto.news, Decrypt, CCN
Ahead of NATO's annual summit in The Hague today, officials are boosting defenses against drones and cyberattacks and plan to support these measures alongside traditional military options.
“If World War III breaks out on the European continent, what’s the first shot?” US Ambassador to NATO Matthew Whitaker recently said. “Is it going to be Russian tanks invading Poland, or is it going to be a cyberattack on one of our allies, or a challenge on some infrastructure?”
One thing no commander wants to run out of is options, a military adage holds, and adversaries have more ways than ever of foreclosing options. Planners must consider wild cards from old-style sabotage to innovation, including cyberattacks and drone strikes.
“If China can shut off the power to our data centers, then maybe they don’t need to sink our aircraft carriers,” said retired Army Lt. Gen. Douglas Lute, a former US ambassador to NATO.
Separately, the Dutch government announced that pro-Russian hackers launched a series of denial-of-service attacks on several municipalities and organizations linked to the NATO summit.
The National Cybersecurity Center said that many attacks were claimed by a pro-Russian hackers’ group known as NoName057(16), and appear to have a pro-Russian ideological motive.” It did not elaborate.
The cybersecurity center said it was investigating attacks that flood a site with data to overwhelm it and knock it offline, and was in contact with “national and international partners.”
Raoul Rozestraten, a spokesman for the municipality in The Hague, the Dutch city hosting the summit Tuesday and Wednesday, said the attacks hit municipalities around the country. (Daniel Michaels / The Wall Street Journal, Associated Press)
Related: The Economic Times, Techzine, NL Times, De Telegraaf
According to the Russian state-owned news agency TASS, four REvil ransomware members arrested in January 2022, Andrey Bessonov, Mikhail Golovachuk, Roman Muromsky, and Dmitry Korotayev, were released by Russia on time served after they pleaded guilty to carding and malware distribution charges.
All four were found guilty by the court and sentenced to five years in prison. However, they were released from custody because the court considered they had served their sentence in a Russian detention center (SIZO) during the investigation and trial.
The defendants were among eight members of the REvil ransomware operation who were apprehended by Russian authorities more than three years ago.
Artem Zayets, Alexey Malozemov, Daniil Puzyrevsky, and Ruslan Khansvyarov, the other REvil members arrested in January 2022, were sentenced to over 4 years in prison as part of a different proceeding after they refused to plead guilty to the charges. (Sergiu Gatlan / Bleeping Computer)
Related: TASS, CyberScoop
An investigation by top on-chain analyst ZachXBT has revealed how an alleged New York-based con artist named Christian Rieves stole millions of dollars from victims by pretending to be support staff from Coinbase.
The pseudonymous sleuth details how a man named Christian Nieves, who goes by “Daytwo” and “PawsOnHips” online, allegedly stole $4 million from Coinbase users by impersonating employees at the crypto exchange.
ZachXBT says that Nieves operates a small scam call center group and also works as a caller. The group allegedly primarily coerces its victims into setting up a Coinbase wallet with an already compromised seed phrase on phishing sites.
Other people in Nieves’ circle also allegedly helped in separate thefts, including a henchman named Justin, who went by the name “Paranoia,” who executed a $240,000 heist of an elderly victim’s Bitcoin (BTC) wallet.
According to ZachXBT, a portion of that $240,000 was deposited into crypto betting site Roobet, and the rest was converted into Monero (XMR).
Nieves and his alleged accomplices have not been charged with anything by law enforcement, but given the amount of digital and on-chain evidence, ZachXBT says it should be a “rather easy” case for authorities. (Alex Richardson / The Daily Hodl)
Related: The Shib, The Block, crypto.news, Decripto, Cryptopolitan
A trio of cybersecurity firms quietly ended a program, the Critical Infrastructure Defense Project, that offered free services to vulnerable critical infrastructure sectors, which was first launched in the wake of Russia’s invasion of Ukraine.
Led by Cloudflare, CrowdStrike, and Ping Identity, the project began in March 2022 and supplied critical infrastructure owners and operators potentially exposed to digital threats tied to the Russia-Ukraine war with free cybersecurity tools. It was designed to help sectors like hospitals, water systems, and power utilities.
Since the war broke out in early 2022, Russian military-aligned hacking groups have accelerated reconnaissance and sabotage campaigns against infrastructure systems in the US and other allies in Europe. One of those incursions targeted a water system in Texas.
But the “project has concluded” since the offerings “aligned with a period of initial heightened threats, and that its use has since subsided,” according to a statement from a CrowdStrike spokesperson. (David DiMolfetta / NextGov/FCW)
Ukraine's Computer and Emergency Response (CERT-UA) says the Russian state-sponsored threat group APT28 is using Signal chats to target government targets in Ukraine with two previously undocumented malware families named BeardShell and SlimAgent.
CERT-UA first discovered the attacks in March 2024, though limited details about the infection vector were uncovered then.
Over a year later, in May 2025, ESET notified CERT-UA of unauthorized access to a gov.ua email account, prompting a new incident response.
During this new investigation, CERT-UA discovered that messages sent via the encrypted messenger app Signal were used to deliver a malicious document to targets (Акт.doc), which uses macros to load a memory-resident backdoor called Covenant.
Covenant acts as a malware loader, downloading a DLL (PlaySndSrv.dll) and a shellcode-ridden WAV file (sample-03.wav) that loads BeardShell, a previously undocumented C++ malware.
In the 2024 attacks, CERT-UA also spotted a screenshot grabber named SlimAgent, which captures screenshots using an array of Windows API functions (EnumDisplayMonitors, CreateCompatibleDC, CreateCompatibleBitmap, BitBlt, GdipSaveImageToStream). (Bill Toulas / Bleeping Computer)
Related: CERT-UA
According to a data breach notification and documents from McLaren Health Care, ransomware hackers stole the Social Security numbers and health insurance information for more than 740,000 people during an attack on a prominent Michigan hospital network.
The documents said the attack last year was launched by an “international ransomware group” and impacted the computer networks of McLaren Health Care and Karmanos Cancer Institute.
Letters to victims said the suspicious activity was discovered on August 5, and investigators found the hackers initially gained access as far back as July 17. A forensic review completed last month found that 743,131 people had information stolen.
The network said the breached data also included names, driver’s license numbers, and medical information. Victims are being given one year of credit monitoring services.
McLaren Health Care warned the public at the time that it was forced to operate with downtime procedures while working to restore several downed IT systems.
McLaren emergency departments continued to operate but some surgeries and procedures were canceled as a result of the attack. Some non-emergent appointments, tests and treatments were rescheduled, according to the statement.
The organization did not call it a ransomware attack at the time, but a printed ransom note from the INC ransomware gang allegedly sent to the hospital was shared on social media. (Jonathan Greig / The Record)
Related: Maine Attorney General, The HIPAA Journal, Bleeping Computer, Globe Newswire, PR Newswire, Tom's Guide, BankInfoSecurity, Security Affairs, The Daily Hodl
Montana Attorney General Austin Knudsen is going after the largest newspaper chain in the state, demanding information and answers about what he says was a cyberattack that exposed the personal information of thousands of subscribers.
Knudsen is ordering the investigation of Lee Enterprises, which operates the state's major papers, including the Billings Gazette and the Missoulian, under the provisions of Montana's Consumer Protection Act.
The state says that, "according to reports," the breach affects nearly 40,000 employees and subscribers, and he's giving Lee a month to respond. (Dennis Bragg / KVGO)
Related: DataBreaches.net, The Independent Record
Spanish LLM security firm NeuralTrust reports that through progressive poisoning and manipulating an LLM’s operational context, many leading AI models can be tricked into providing almost anything, regardless of the guardrails in place, with a new jailbreak they call Echo Chamber.
Echo Chamber is similar to Microsoft’s Crescendo jailbreak. The latter asks questions and tries to lure the LLM into a desired prohibited response. The former, Echo Chamber, never tells the LLM where to go, but plants acceptable ‘seeds’ that progressively guide the AI into providing the required response.
Echo Chamber works by manipulating the LLM’s context (what it remembers of a conversation to allow a coherent conversation) while avoiding the so-called red zone (prohibited queries) and remaining within the green zone (acceptable queries). From within the green zone, context is maintained, and the conversation can continue, but if the red zone is entered, the LLM declines to respond, and the context is lost.
The attacker's only criteria are to keep the context in the green zone, avoid the red zone, and complete the attack within the time or query limits on the current context. (Kevin Townsend / Security Week)
Related: NeuralTrust, SC Media, Dark Reading

Researchers at SecurityScorecard report that a stealthy, ongoing campaign to gain long-term access to networks bears all the markings of intrusions conducted by China’s Typhoon crews and has infected at least 1,000 devices, primarily in the US and Southeast Asia.
It attempts to access critical infrastructure by using a phony certificate purportedly signed by the Los Angeles Police Department.
The digital break-ins began no later than September 2023 (maybe earlier) and have expanded ever since. The campaign primarily targets end-of-life routers, IoT devices, internet-connected security cameras, virtual servers, and other small office/home office (SOHO) devices to build an Operational Relay Box or ORB network.
Beijing's attackers route traffic and launch cyberattacks through these ORB networks, which have grown to hundreds or thousands of compromised devices. Because the activity comes through what seems to be a local IP address, it's harder to track.
In recent years, essentially all of the Chinese government-backed groups use ORBs to remain undetected on victims' networks.
Intruders built this ORB network, which Security Scorecard named "LapDogs,” by compromising old and unpatched devices through various means. The miscreants "appear to favor targeting Linux-based systems in their operations," according to a report published Monday (Jessica Lyons / The Register)
Related: SecurityScorecard, HackRead, IT Pro, Help Net Security, BankInfoSecurity
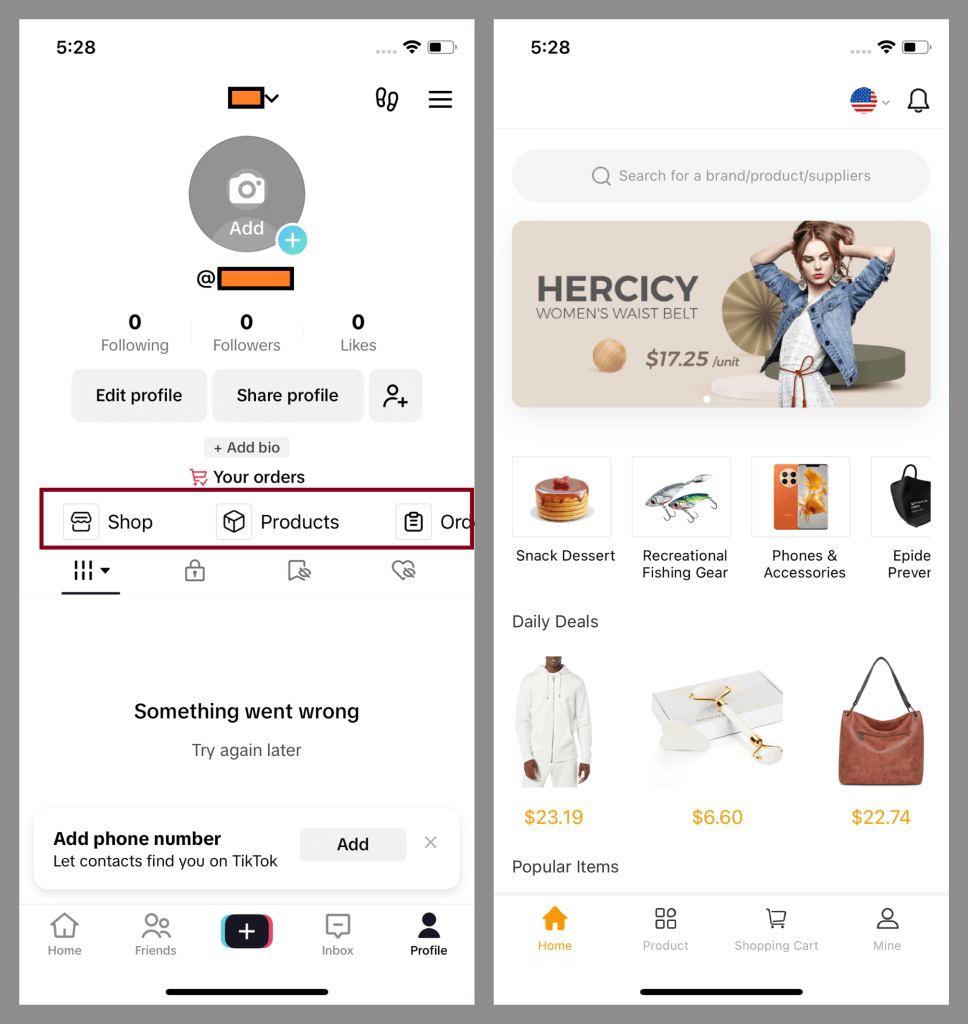
Researchers at Kaspersky have discovered photo-stealing malware they call SparkKitty that has been quietly targeting iPhone and Android users since at least February 2024.
The malware's authors have been distributing it through apps in the official app stores of Apple and Google, via malicious pages, and as a Trojanized version of the TikTok app.
As with its older sibling, SparkCat, SparkKitty's goal is to harvest images from a device's gallery in the hopes of locating sensitive content such as screenshots of cryptocurrency wallet seed phrases. According to Kaspersky, one Android app featuring SparkKitty had more than 10,000 installations from Google Play before being removed. (Jai Vijayan / Dark Reading)
Related: Securelist
Microsoft has confirmed that Windows 11 System Restore points will be deleted after 60 days, so users must be more careful and periodically create restore points.
Microsoft will give users multiple snapshots with this latest update, but Windows will still delete the oldest ones once they exceed the retention window (now 60 days on Windows 11 24H2 by default). (Mayank Parmar / Windows Latest)
Related: Tom's Guide, ExtremeTech, PC World, Forbes, XDA
Election officials and experts worry that Donald Trump is attempting to create a new set of metrics that can better support his political claims of voter fraud.
Last month, US Citizenship and Immigration Services quietly announced that a federal database typically used for naturalized citizens to seek benefits had been repurposed as a tool to check state voter registration systems for signs of noncitizens.
The news came less than a month after the agency revealed that staffers from the Department of Government Efficiency had implemented a “comprehensive optimization” of the database, known as Systematic Alien Verification for Entitlements (SAVE), that included the elimination of state-paid fees for searches and other unspecified changes to streamline mass status checks, integrate criminal records information and “break down silos for accurate results,” according to DOGE officials.
Further changes announced by the agency in May will allow states to run searches using Social Security numbers and conduct bulk searches. As USCIS spokesperson Matthew Tragesser said, these modifications are intended to “help identify and stop aliens from hijacking our elections.”
Election officials and experts have expressed bewilderment as to why the Department of Homeland Security would attempt to use SAVE, an incomplete, often out-of-date database, to identify potential noncitizen voters.
Others expressed more direct concerns that the SAVE changes appear to be the first steps in a larger plan by the White House to create new metrics that lend support to Trump’s unproven claims that noncitizens are voting en masse for Democrats. (Derek B. Johnson and Colin Wood / Cyberscoop)
Best Thing of the Day: A 'Hackathon' That Can Help Save Dolphins
Not cyber-related, but the University of Hawaiʻi Sea Grant College Program (Hawaiʻi Sea Grant) and Papahānaumokuākea Marine Debris Project (PMDP) have launched the inaugural Marine Debris Hack-A-Thon, a cutting-edge challenge that calls on individuals or teams to develop new, innovative tools that can be used to cut and remove derelict fishing nets.
Worst Thing of the Day: Add Murder-for-Hire to Iran's Possible Retaliation Checklist
Amid the fears of Iranian attacks against the US in retaliation for recent military strikes, Iran is accused of having taken in recent years to target political figures on US soil and recruiting operatives to kill public officials and dissidents.




