US ODNI drops her remit to investigate 2020 election fraud claims
US law enforcement are probing if WhatsApp employees can read users' messages, Popular AI app exposes millions of users' private messages, Darkweb market Empire Market creator pleads guilty, US seizes $400m in darknet crypto mixer Helix's assets, UK safety charity warns about The Com, much more


Paid subscribers receive full access to Metacurity’s archives and selected analytical deep dives
Don't miss out on the full range of what Metacurity has to offer. Upgrade to a paid subscription, gain access to our archives and special content, and stay current while helping to keep independent media alive.
If you can't afford a paid subscription, donate what you can to keep this vital resource going.
Tulsi Gabbard, the director of national intelligence, has spent months investigating the results of the 2020 election that Donald Trump lost, according to White House officials, a role that took her to a related FBI search of an election center in Georgia on Wednesday.
Gabbard is leading the administration’s effort to re-examine the election and look for potential crimes, a priority for the president, the officials said.
The national intelligence director is usually focused on ensuring the president has the best intelligence available to make national security decisions. Gabbard has been sidelined from some of those deliberations, including the Venezuela operation earlier this month, The Wall Street Journal has reported.
She has begun studying information about voting machines, analyzed data from swing states, and pursued theories that President Trump has promoted to claim the 2020 election was unfairly taken from him, the officials said, particularly on foreign government interference.
She has regularly briefed Trump and chief of staff Susie Wiles about her inquiry in recent months, along with others involved in the investigation. Those include senior Justice Department officials, Trump’s outside ally and lawyer Cleta Mitchell, and Kurt Olsen, a lawyer who pushed claims in 2020 that the election was stolen and joined the administration as a special government employee.
Gabbard has consulted with others in the intelligence community about claims of foreign interference in the 2020 election, the officials said, though she hasn’t provided the public with new evidence of it.
She is expected to prepare a report on her work, the people said. The administration has discussed executive orders on voting ahead of the midterm elections, two of the officials said.
Cybersecurity specialists, elections experts, and many former top security officials who worked for Trump during his first term have maintained for years that there was no evidence of widespread tampering or fraud in the 2020 contest.
Lawmakers and state election officials sharply criticized the Trump administration for this maneuver, accusing the White House of chasing baseless internet conspiracy theories about fraud in the 2020 election. Officials also warned the raid could set a precedent for similar federal actions targeting the 2026 midterm elections. (Josh Dawsey, Dustin Volz, and Sadie Gurman / Wall Street Journal and Derek B. Johnson / CyberScoop)
Related: Reuters, CNN, Politico, Axios, NBC News, Spy Talk, Washington Examiner, The Washington Post, CNN, The New Republic, Semafor, CyberScoop
According to interviews and an agent’s report, US law enforcement has been investigating allegations by former Meta Platforms contractors that Meta personnel can access WhatsApp messages, despite the company’s statements that the chat service is private and encrypted.
The former contractors’ claims — that they and some Meta staff had “unfettered” access to WhatsApp messages — were being examined by special agents with the US Department of Commerce, according to the law enforcement records, as well as a person familiar with the matter and one of the contractors.
Similar claims were also the subject of a 2024 whistleblower complaint to the US Securities and Exchange Commission, according to the records and the person, who spoke on the condition that they not be identified out of concern for potential retaliation. The investigation and whistleblower complaint haven’t been previously reported.
The allegations under investigation stand in stark contrast to how Meta has marketed WhatsApp: as a private app with default “end-to-end” encryption, which the company’s website says means “no one outside of the chat, not even WhatsApp, can read, listen to, or share” what a user says.
WhatsApp has communicated this level of privacy in its app, in its advertising, and to governments that want access to information on crimes, which Meta has told them is technically impossible to provide because of WhatsApp’s architecture.
A spokesperson for Meta, which acquired WhatsApp in 2014, said the contractors’ claims are impossible. (Jake Bleiberg / Bloomberg)
Related: Firstpost
Chat & Ask AI, one of the most popular AI apps on the Google Play and Apple App stores that claims more than 50 million users, left hundreds of millions of those users’ private messages with the app’s chatbot exposed, according to an independent security researcher who goes by the name Harry and emails viewed by 404 Media.
The exposed chats showed users asking the app, “How do I painlessly kill myself?” to write suicide notes, “how to make meth,” and how to hack various apps.
The issue is a misconfiguration in the app’s usage of the mobile app development platform Google Firebase, which by default makes it easy for anyone to make themselves an “authenticated” user who can access the app’s backend storage, where, in many instances, user data is stored.
Harry said that he had access to 300 million messages from more than 25 million users in the exposed database, and that he extracted and analyzed a sample of 60,000 users and a million messages. The database contained user files with a complete history of their chats with the AI, timestamps of those chats, the name they gave the app’s chatbot, how they configured the model, and which specific model they used.
Chat & Ask AI is a “wrapper” that plugs into various large language models from bigger companies users can choose from, Including OpenAI’s ChatGPT, Anthropic's Claude, and Google’s Gemini. (Emanuel Maiberg / 404 Media)
Related: r/technology
A Virginia man, Raheim Hamilton (aka "Sydney" and "ZeroAngel"), who co-created Empire Market, one of the largest dark web marketplaces at the time, pleaded guilty to federal drug conspiracy charges for facilitating $430 million in illegal transactions from 2018 to 2020.
The marketplace operated as a hidden service accessible only via TOR browsers and was advertised as an AlphaBay "clone," modeled after the notorious dark web marketplace shut down by authorities in 2017.
At its peak in August 2020, Empire Market had approximately 1.68 million unique registered users, including nearly 360,000 buyers and more than 5,000 vendors.
While the cybercrime market also sold stolen account credentials, personally identifying information, counterfeit currency, and computer hacking tools, drug sales totaled nearly $375 million over the site's lifespan, representing the most prevalent activity, with 166,029 vendor listings for controlled substances alone.
Hamilton owned and operated Empire Market from August 2017 onward, together with co-defendant Thomas Pavey (aka "Dopenugget"), facilitating more than 4 million transactions between vendors and buyers. (Sergiu Gatlan / Bleeping Computer)
Related: Justice Department, SC Media, Security Affairs, The Record
US authorities have finalized the forfeiture of more than $400 million in assets tied to Helix, a darknet crypto mixer used to launder proceeds from online drug markets and other criminal activities.
The government obtained legal title to the assets in question last week, following a final order entered by a federal judge on January 21.
Helix was a widely used darknet mixing service that began operations in 2014, processing up to about 354,468 Bitcoin, worth roughly $311 million at the time, according to a statement from the DOJ. (Vince Dioquino / Decrypt)
Related: US Department of Justice, Cointelegraph, crypto.news, The Crypto Times, The Block, Blockonomi, Cryptonews
The Molly Rose Foundation (MRF), a leading UK online safety charity, has issued a “public warning” about the hacking community known as The Com that is targeting vulnerable children for sexual abuse, self-harm, and suicide.
MRF said The Com were carrying out extreme exploitation, cyberbullying, violence and abuse – and called for a coordinated global response from governments, regulators, law enforcement and tech companies.
The warning follows the publication of a report by the online risk consultancy Resolver in partnership with the MRF, which was founded by the family of Molly Russell, a British teenager who killed herself in 2017 after viewing harmful content online. (Dan Milmo / The Guardian)
Related: Mirror
The Pentagon is at odds with artificial-intelligence developer Anthropic over safeguards that would prevent the government from deploying its technology to target weapons autonomously and conduct US domestic surveillance, three people familiar with the matter said.
The discussions represent an early test case for whether Silicon Valley, in Washington’s good graces after years of tensions, can sway how US military and intelligence personnel deploy increasingly powerful AI on the battlefield.
After extensive talks under a contract worth up to $200 million, opens new tab, the US Department of Defense and Anthropic are at a standstill, six people familiar with the matter said, on condition of anonymity.
The company's position on how its AI tools can be used has intensified disagreements between it and the Trump administration, the details of which have not been previously reported. (Deepa Seetharaman, David Jeans and Jeffrey Dastin / Reuters)
Related: Wall Street Journal, r/worldnews, r/ClaudeAI, r/technology, r/singularity
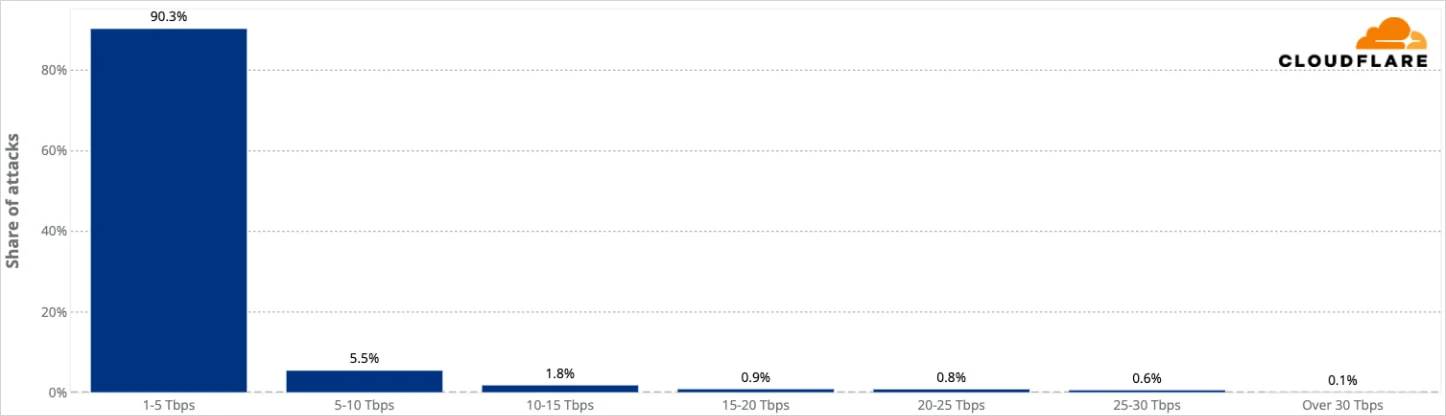
Researchers at Cloudflare report that the Aisuru/Kimwolf botnet launched a new massive distributed denial of service (DDoS) attack that peaked at 31.4 Tbps and 200 million requests per second, setting a new record.
The attack was part of a campaign targeting multiple companies, most of them in the telecommunications sector, and was detected and mitigated by Cloudflare last year on December 19.
Aisuru is responsible for the previous DDoS record that reached 29.7 Tbps. Another attack that Microsoft attributed to the botnet peaked at 15.72 Tbps and originated from 500,000 IP addresses.
Due to its timing, Cloudflare named the latest Aisuru campaign “The Night Before Christmas” and characterized it as an “unprecedented bombardment” on telecommunications service providers and IT organizations.
“The campaign targeted Cloudflare customers as well as Cloudflare’s dashboard and infrastructure with hyper-volumetric HTTP DDoS attacks exceeding rates of 200 million requests per second (rps) alongside Layer 4 DDoS attacks peaking at 31.4 Terabits per second, making it the largest attack ever disclosed publicly,” Cloudflare says. (Bill Toulas / Bleeping Computer)
Related: Cloudflare, Techzine
A new security feature rolled out to select models of the latest iPhones and iPads this week will make it more difficult for law enforcement, spies, and malicious hackers to obtain a person’s precise location data from their phone provider.
According to Apple, the new feature, when enabled, limits the precision of location data that iPhones and cellular-enabled iPads share with the customer’s cell carrier. Sharing a less-precise location, such as the general neighborhood rather than a street address, will help to protect the device owner’s privacy, the company claims.
Apple said switching on the feature does not affect the precision of location data shared with apps or shared with first responders during an emergency call.
The limit precise location feature is supported on iPhone Air, iPhone 16e, and iPad Pro (M5) Wi-Fi + Cellular, running iOS 26.3, and is available on a handful of global carriers, including Telekom in Germany, AIS and True Thailand, EE and BT in the United Kingdom, and Boost Mobile in the United States. (Zack Whittaker / TechCrunch)
Related: Apple, Help Net Security, The Record, 9to5Mac
Poland's CERT issued more details on the December 29 energy sector cybersecurity incident, saying all the attacks, attributed to Russia's Berserk Bear/Dragonfly/Isotope/FSB, had purely destructive objectives.
CERT said, "By analogy to the physical world, they can be compared to deliberate arson. It is worth noting that this occurred during a period when Poland was struggling with low temperatures and snowstorms just before the New Year."
The agency also said that on the same day, December 29, the attacker attempted to disrupt the operations of a manufacturing sector company. These actions were coordinated with the attacks on the energy-sector entities, but the objective was opportunistic and unrelated to the other targets.
The wiper malware used was identical to that employed in the attack on the combined heat and power plant. A detailed technical analysis of the malware is included in the report. (CERT.Pl)
Related: CERT.pl, ESET, Zero Day
Google's Threat Analysis Group terminated 18,532 YouTube channels during Q3 2025 as part of its investigations into coordinated influence operations spanning nine countries, according to a bulletin published November 13, 2025.
The enforcement actions documented in the TAG Bulletin: Q3 2025 represent the latest phase in ongoing efforts to disrupt coordinated inauthentic behavior across Google platforms. Russia accounted for the majority of terminated channels, with Chinese operations representing the second-largest volume of enforcement actions during the July through September period.
During July, TAG terminated 3,286 YouTube channels linked to Russia, with the largest single action removing 382 channels connected to a Russian consulting firm. These operations shared content in Russian supporting Russia while criticizing Ukraine and Western institutions. The consulting firm pattern continued throughout the quarter, with TAG identifying multiple campaigns linked to commercial entities providing coordinated influence services. (Luis Rijo / PPC Land)
Related: Google TAG
Justin Wynn and Gary DeMercurio, two pentesting contractors to the Iowa state judiciary, won $600,000 in a settlement with Dallas County over their 2019 arrest for trespassing.
According to court documents, the Iowa Judicial Branch signed agreements with its cybersecurity firm Coalfire in 2019.
Wynn and DeMercurio would evaluate the cyber and physical security of several different courthouses across the state.
In those documents, the Iowa Judicial Branch gave permission for them to use tactics like lockpicking.
While the pair call it a victory, they say this case has had serious repercussions on the future of security in Iowa.
Dallas County Attorney Matt Schultz told KCCI: "I want to be clear that the decision to dismiss the criminal charges that resulted in this civil case against Dallas County was made by a previous County Attorney. I am putting the public on notice that if this situation arises again in the future, I will prosecute to the fullest extent of the law."
The Iowa Supreme Court ultimately prohibited these types of break-in tests after Wynn and DeMercurio's arrest.
"It leaves them completely hamstrung, and hackers across the nation said, you know, we don't want to work with Iowa. If you guys are going to be arresting, you know, people that you hire to come and do these jobs," Wynn said. (Abigail Kurten / KCCI)
Related: KCRG, The Cyber Express, The Des Moines Register
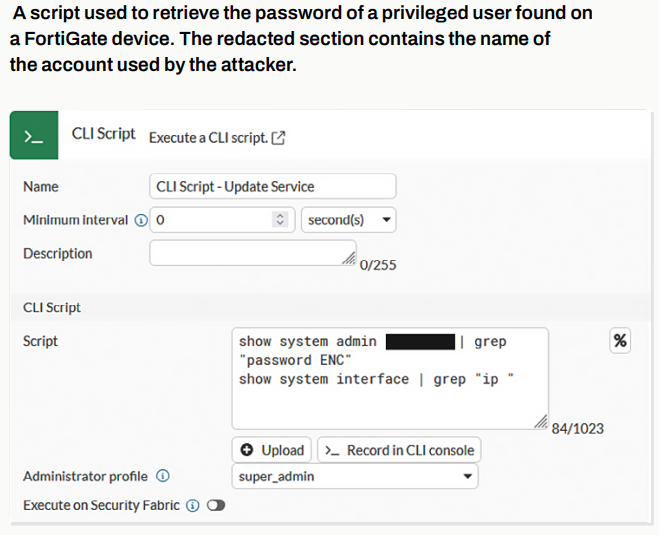
Researchers at Bitdefender uncovered a large-scale Android campaign in which a remote access trojan is being distributed via Hugging Face’s infrastructure.
The attackers combine social engineering with the abuse of legitimate cloud hosting to distribute malicious APK files. In doing so, they make intensive use of Android Accessibility Services to gain in-depth control over infected devices.
The infection chain starts with a seemingly innocent Android app called TrustBastion. Advertisements and alarming notifications convince users that their devices are infected and need to be secured urgently. The app presents itself as a free security solution that detects phishing, fraudulent text messages, and malware, among other things. In reality, the application has no security functionality and serves solely as a dropper for the next stage of infection.
Immediately after installation, the user is prompted to install a mandatory update. The accompanying screen closely mimics the appearance of Google Play and Android system updates, which increases its credibility. When the user agrees, the app contacts a server that does not deliver malware and instead redirects to a dataset repository on Hugging Face. From there, the final malicious APK is downloaded via the platform’s infrastructure and CDN.
According to Bitdefender, this approach was deliberately chosen to avoid detection. Traffic from well-known and widely used platforms is less likely to be blocked than downloads from suspicious domains.
Analysis of the repository used shows that the attackers are applying server-side polymorphism on a large scale. New payload variants were generated approximately every fifteen minutes, resulting in more than 6,000 different APK files in less than a month. Each variant contains the same functionality, but minor technical changes are designed to circumvent hash-based detection. (Mels Dees/ Techzine)
Related: Bitdefender, Bank Info Security
Coupang CEO Harold Rogers appeared before the Seoul Metropolitan Police Agency as a suspect in an investigation into whether the e-commerce company obstructed a government probe through an internal review of a large-scale data breach.
The Seoul Metropolitan Police Agency said Rogers was summoned on suspicion that Coupang destroyed or concealed evidence related to a massive data breach affecting 33.7 million customer accounts.
The appearance followed two earlier summonses that Rogers declined after leaving Korea, and marked his first questioning since police formed a special task force in December. Upon arriving at police headquarters, Rogers said Coupang would fully cooperate with the government’s investigation, “as it always has,” and that he would do the same during questioning.
Investigators are examining whether the company privately contacted the suspect overseas and conducted internal forensic work that may have interfered with the police investigation. Coupang’s internal review concluded that roughly 3,000 records were taken and subsequently deleted, despite unauthorized access to as many as 33 million accounts. (No Kyung-min / Korea Herald)
Related: Economic Times, Korea Times
Personal information of about 4.5 million members of the Seoul city government's public bike sharing service, named "Ttareungyi," was believed to have been leaked in 2024, according to data compiled by Yonhap News Agency.
Police recently launched an investigation into the suspected data breach after becoming aware of the existence of leaked Ttareungyi member information while conducting another investigation. They suspect hackers were behind the massive data leakage.
According to Yonhap News Agency's research, some 4.5 million of the service's 5 million members were affected by the data breach, and the leaked personal information included their names, phone numbers, dates of birth, and addresses.
The Seoul city government said earlier Friday that Ttareungyi members' names and resident registration numbers were not leaked because they were not required to submit the sensitive personal information when signing up for the service.
But it is feared that sensitive personal information arbitrarily entered by members may have been included in the data leakage, exposing the concerned members to fraud and other secondary damage.
According to the reports, Seoul Facilities Corp., the operator of the Ttareungyi service, was recently notified by the Seoul Metropolitan Police Agency of the suspected data breach.
A Seoul city government official said the incident was believed to have occurred around April 2024, when many public institutions came under distributed denial-of-service (DDoS) attacks, but no reports of damage have been received. (Yonhap News)
Related: Korea JoongAng Daily
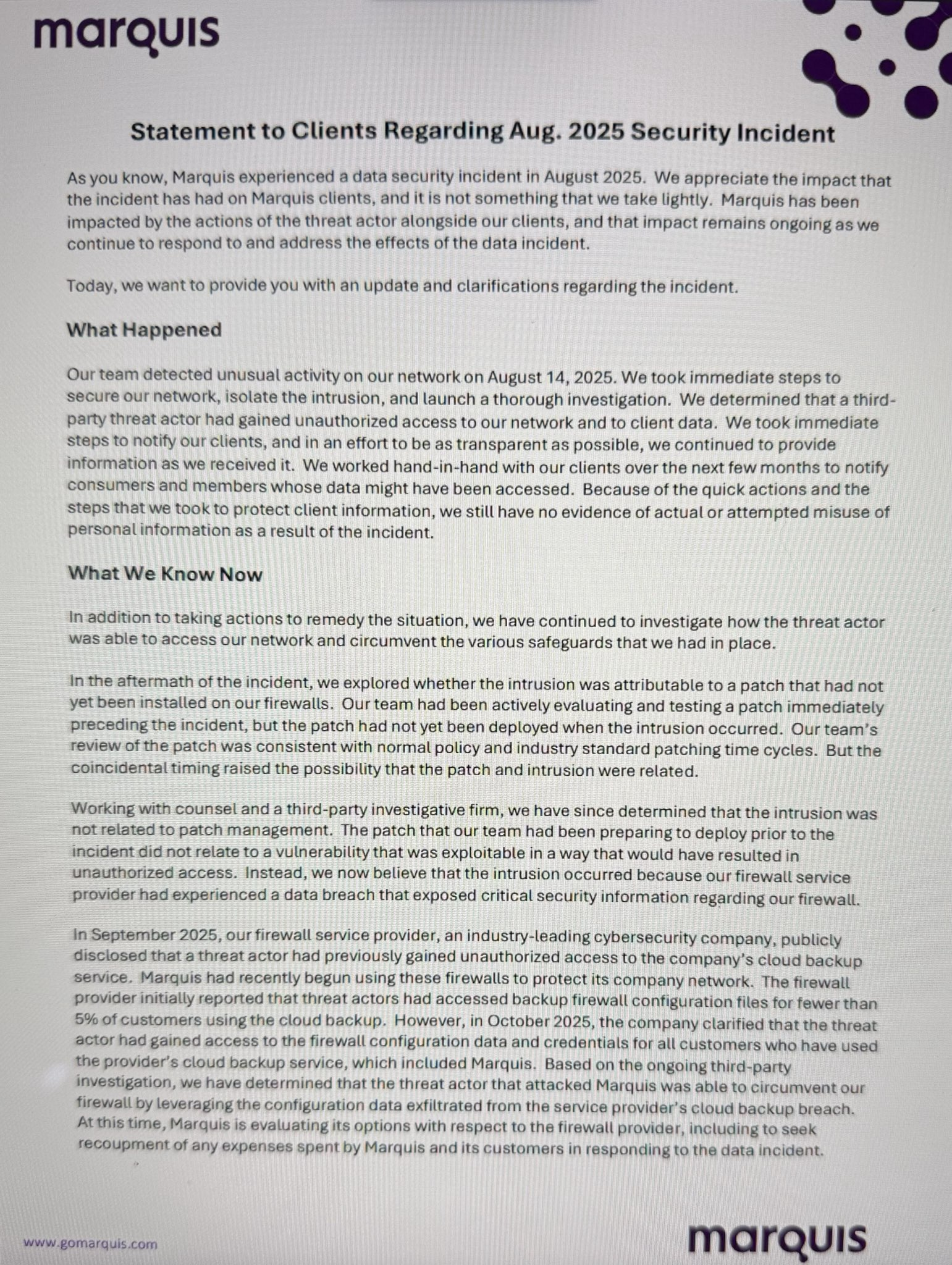
Marquis Software Solutions, a Texas-based financial services provider, is blaming a ransomware attack that impacted its systems and affected dozens of US banks and credit unions in August 2025 on a security breach reported by SonicWall a month later.
In statements to customers earlier this week, Marquis says the ransomware operators didn't breach its systems by exploiting an unpatched SonicWall firewall, as previously believed.
Instead, the attackers used information obtained from firewall configuration backup files stolen after gaining unauthorized access to SonicWall's MySonicWall online customer portal.
"Based on the ongoing third-party investigation, we have determined that the threat actor that attacked Marquis was able to circumvent our firewall by leveraging the configuration data extracted from the service provider's cloud backup breach," Marquis said.
"At this time, Marquis is evaluating its options with respect to the firewall provider, including seeking recoupment of any expenses spent by Marquis and its customers in responding to the data incident." (Sergiu Gatlan / Bleeping Computer)
Related: TechCrunch, TechRadar
About 80% of respondents to a new survey said they received at least one data breach notice in the prior 12 months, according to the Identity Theft Resource Center.
Nearly 40% of respondents received three to five separate notices over that period. The survey polled 1,040 individuals in November.
Of those who recently received a data breach notice, 88% reported at least one negative consequence, such as increased phishing or other scam attempts, more spam emails or robocalls, or an attempted account takeover, the survey found.
The number of data compromises rose 5% last year — with 3,322 events in 2025 versus 3,152 in 2024 — a record, according to the ITRC’s new annual report. The nonprofit organization has been tracking public reports of data compromises for 20 years. (Lorie Konish / CNBC)
Related: Identity Theft Research Center, Payment Security
The City of New Britain in Connecticut is experiencing a suspected cyberattack, officials said.
The issue began early Wednesday morning, according to officials, and affected certain city systems.
Officials said when the city identified the issue, it activated its "incident response protocols" and is working "closely with state and federal authorities to assess the scope and impact of the incident."
City officials are expected to hold a press conference on Friday morning to provide updates. (Jennifer Glatz / NBC Connecticut)
Related: WFSB, Connecticut Examiner
OpenSSL released updates that patch a dozen vulnerabilities, including a high-severity remote code execution flaw.
All 12 vulnerabilities patched in the open source SSL/TLS toolkit were discovered by cybersecurity firm Aisle, which used an autonomous analyzer to identify the security holes.
The high-severity issue is tracked as CVE-2025-15467, and it has been described as a stack buffer overflow that could lead to a crash (DoS condition) or remote code execution in certain conditions.
The latest OpenSSL releases also address CVE-2025-11187, a moderate-severity issue whose exploitation could also lead to a DoS condition or even remote code execution. (Eduard Kovacs / Security Week)
Related: JFrog, OpenSSL, 9to5Linux, Security Affairs, Tom's Hardware, Cyber Press, SOC Prime, Aisle
The FBI has launched Operation Winter SHIELD, outlining ten actions which organizations should implement to help protect themselves, society, and the state against cyber-attacks and malicious intrusions.
The Securing Homeland Infrastructure by Enhancing Layered Defense (SHIELD) cyber resilience campaign details actions that organizations can take to help detect, confront, and dismantle cyber threats.
“Winter SHIELD provides industry with a practical roadmap to better secure information technology (IT) and operational technology (OT) environments, hardening the nation’s digital infrastructure and reducing the attack surface,” the FBI said in an announcement on January 28.
“Our goal is simple: to move the needle on resilience across industry by helping organizations understand where adversaries are focused and what concrete steps they can take now (and build toward in the future) to make exploitation harder,” the agency added.
The campaign is tied to the US National Cyber Strategy and the FBI Cyber Strategy, and over ten weeks, it will detail actions that organizations can take to defend industry, government, and critical infrastructure from cyber-attacks. (Danny Palmer / Infosecurity Magazine)
Related: FBI
Outtake, a NYC-based provider of a digital trust platform for AI-driven impersonation protection, announced it had raised $40 million in Series B funding.
ICONIQ led the round, with participation from CRV, S32, and angel investors including Satya Nadella, Nikesh Arora, Bill Ackman, Shyam Sankar, Trae Stephens, Bob McGrew, Guillermo Rauch, and John Donovan. (Samantha Subin / CNBC)
Related: FinSMEs
Best Thing of the Day: Can't Believe I'm on the Side of Cybercriminals With This One
Efforts to track ICE agents’ movements and identities have exploded online, including sites to report ICE raid locations, and even prolific cybercriminal collectives are joining in on attacks on the odious agency.
Worst Thing of the Day: Turns Out ICE is the Panopticon
As has been evident over the past few months, ICE agents are using facial recognition, social media monitoring, and other tech tools not only to identify undocumented immigrants but also to track protesters.
Closing Thought