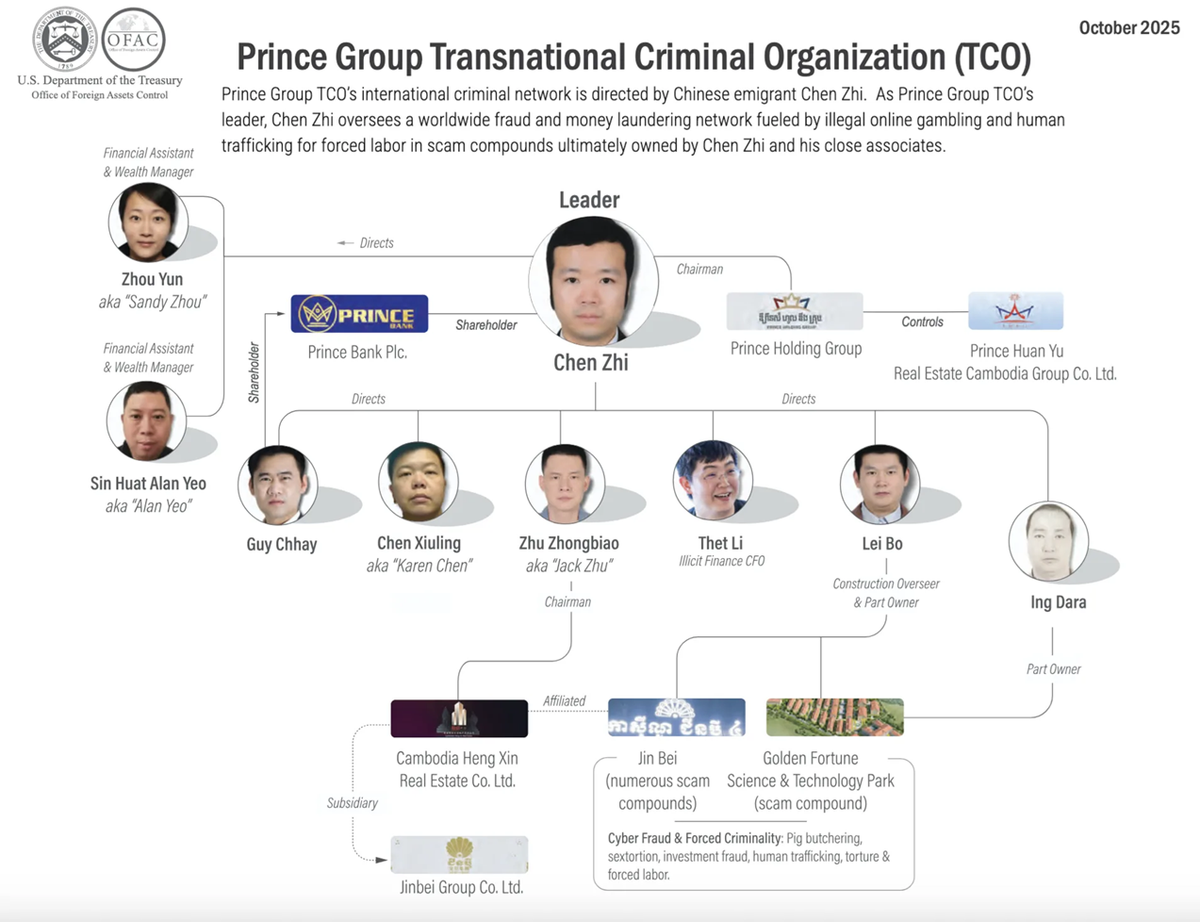
US seizes $15 billion, sanctions Huione group, and indicts Cambodian scam ringleader
S. Korea seeks return of disappeared workers from Cambodia, First Wap has built a phone-tracking empire, Microsoft plugs 172 security holes, Windows 10 reaches end-of-support, ICO fines Capita $19m for 2023 data breach protection fails, PowerSchool hacker sentenced to 4 years, much more