Venezuela's state-run oil company PDVSA was hit by a cyberattack
Coupang's founder didn't show at parliamentary hearing, Majority of parked domains foist scams and malware, FTC orders Nomad to pay victims after hackers stole cryptocurrency, noyb alleges data exposure by TikTok, Grindr and AppFlyer, Hackers exploit critical flaws in Fortinet products, much more


'Tis the season to be generous. Please support Metacurity in our mission to end infosec news overload.
Metacurity is a pure labor of love and is the only daily newsletter that delivers the critical infosec developments you need to know, scanned from thousands of sources and smartly summarized.
But to continue delivering our daily updates, we need your support. Please consider upgrading to an annual paid subscription today.
If you can't upgrade to a paid subscription today, please consider donating what you can.
Venezuela's state-run oil company PDVSA was hit by a cyberattack and said its operations were unaffected, even though four sources said systems remained down and oil cargo deliveries were suspended.
Tensions are high between the US and Venezuelan governments, amid a large-scale US military buildup in the southern Caribbean, US strikes on alleged drug trafficking boats, and comments from Donald Trump that land operations may begin soon in Venezuela.
PDVSA and the oil ministry blamed the US for the cyberattack, saying it was carried out by "foreign interests in complicity with domestic entities who are seeking to destroy the country's right to sovereign energy development."
They alleged the attack was part of US efforts to control Venezuela's oil through "force and piracy."
However, a PDVSA source said the company had detected a ransomware attack days ago, and the antivirus software it used to try to fix the problem affected its entire administrative system.
PDVSA said it had recovered from the attack. Venezuela's government regularly blames problems like blackouts on conspirators from the opposition and foreign entities like the US Central Intelligence Agency, without giving evidence. (Reuters)
Related: Bloomberg, Breaking the News, Security Affairs, Bleeping Computer, The Cyber Express
Lawmakers assailed Coupang’s billionaire founder Bom Kim for failing to appear before a parliamentary hearing on South Korea’s biggest-ever data breach, underscoring rising public anger with the country’s dominant online retailer.
Kim’s absence dominated a special session on Wednesday on the breach, which compromised more than 30 million users’ personal information, including names, phone numbers, and delivery details. The former head of Coupang’s Korean operations, Park Dae-jun, also failed to appear after resigning last week. Harold Rogers, Coupang Inc.’s chief administrative officer and newly appointed interim head of the Korean unit, attended the hearing alongside a range of lower-ranking Korean executives.
The crisis has prompted a government probe and disrupted the lives of millions across Korea, with nearly two-thirds of people affected. Rogers said the company is cooperating with the investigation and has handed “thousands of documents” to regulators. It’s also working on a plan to compensate customers affected by the breach, he added. (Jane Lanhee Lee / Reuters)
Related: Reuters, The Investor, Tech in Asia, China Daily, Yonhap News, Wall Street Journal
A new study by Infoblox finds the vast majority of “parked” domains — mostly expired or dormant domain names, or common misspellings of popular websites — are now configured to redirect visitors to sites that foist scams and malware.
When Internet users try to visit expired domain names or accidentally navigate to a lookalike “typosquatting” domain, they are typically brought to a placeholder page at a domain parking company that tries to monetize the wayward traffic by displaying links to a number of third-party websites that have paid to have their links shown.
A decade ago, ending up at one of these parked domains came with a relatively small chance of being redirected to a malicious destination: In 2014, researchers found (PDF) that parked domains redirected users to malicious sites less than five percent of the time — regardless of whether the visitor clicked on any links at the parked page.
But in a series of experiments over the past few months, Infoblox researchers say they discovered the situation is now reversed, and that malicious content is by far the norm now for parked websites.
“In large scale experiments, we found that over 90% of the time, visitors to a parked domain would be directed to illegal content, scams, scareware and anti-virus software subscriptions, or malware, as the ‘click’ was sold from the parking company to advertisers, who often resold that traffic to yet another party,” Infoblox researchers wrote in a paper published today.
Infoblox found that parked websites are benign if the visitor arrives at the site using a virtual private network (VPN), or else via a non-residential Internet address. For example, Scotiabank.com customers who accidentally mistype the domain as scotaibank[.]com will see a normal parking page if they’re using a VPN, but will be redirected to a site that tries to foist scams, malware, or other unwanted content if coming from a residential IP address. Again, this redirect happens just by visiting the misspelled domain with a mobile device or desktop computer that is using a residential IP address.
According to Infoblox, the person or entity that owns scotaibank[.]com has a portfolio of nearly 3,000 lookalike domains, including gmai[.]com, which demonstrably has been configured with its own mail server for accepting incoming email messages. Meaning, if you send an email to a Gmail user and accidentally omit the “l” from “gmail.com,” that missive doesn’t just disappear into the ether or produce a bounce reply: It goes straight to these scammers.
The report notes this domain has also been leveraged in multiple recent business email compromise campaigns, using a lure indicating a failed payment with Trojan malware attached. (Brian Krebs / Krebs on Security)
Related: Infoblox, GBHackers, Domain Name Wire

The US Federal Trade Commission is ordering Illusory Systems, which also does business as Nomad, a company that publicly touted its cybersecurity capabilities, to return recovered funds to victims and implement security reforms, after a software flaw let hackers steal hundreds of millions of dollars in cryptocurrencies from users.
The FTC reached a settlement with Illusory following an investigation into a 2022 incident where hackers exploited a vulnerability in the company’s Token Bridge cryptocurrency smart contract solution. The program provides protocols that connect different blockchains and allow users to transfer assets between them.
As part of the deal, the company must implement a comprehensive cybersecurity plan, including addressing security flaws identified in the FTC’s complaint and programs for protecting consumers from theft and fraud. It must also submit the plan and cooperate with independent third-party assessors on any improvements and return stolen money clawed back by law enforcement. (Derek B. Johnson / CyberScoop)
Related: FTC, Decrypt, Cryptopolitan
Advocacy group Vienna-based organization None of Your Business, or noyb, filed complaints to Austria's data protection authority against TikTok, Grindr, and AppsFlyer, alleging these companies breached regional privacy laws, risking exposure of sensitive data.
noyb alleges that the companies violated European Union privacy laws by tracking user activities across apps without consent.
TikTok, owned by China's ByteDance, and Grindr, a widely used LGBTQ+ dating app, shared sensitive user information illegally, while AppsFlyer, known for mobile marketing analytics, facilitated unauthorized data transfers, noyb claims.
noyb said the user discovered, via a data-access request, that TikTok had accessed sensitive details from other apps, including the person's "use of Grindr, LinkedIn," and a product they had added to a shopping cart.
TikTok only disclosed this information to the user after repeated enquiries, failing to comply with GDPR's transparency requirements.
TikTok said the data was used for reasons including "personalised advertising, analytics, security," according to noyb. GDPR provides special protection for sensitive information such as sexual orientation, which could spur discrimination, noyb said.
Noyb said neither AppsFlyer nor Grindr had legal grounds to share the user's data with TikTok. (Leo Marchandon / Reuters)
Related: Noyb, Euractiv, Tech in Asia, Cryptopolitan
Researchers at Arctic Wolf say that hackers are exploiting critical-severity vulnerabilities affecting multiple Fortinet products to get unauthorized access to admin accounts and steal system configuration files.
The two vulnerabilities are tracked as CVE-2025-59718 and CVE-2025-59719, and Fortinet warned in an advisory on December 9 about the potential for exploitation.
CVE-2025-59718 is a FortiCloud SSO authentication bypass affecting FortiOS, FortiProxy, and FortiSwitchManager. It is caused by improper verification of cryptographic signatures in SAML messages, allowing an attacker to log in without valid authentication by submitting a maliciously crafted SAML assertion.
CVE-2025-59719 is a FortiCloud SSO authentication bypass affecting FortiWeb. It arises from a similar issue with the cryptographic signature validation of SAML messages, enabling unauthenticated administrative access via forged SSO.
Both issues are only exploitable if FortiCloud SSO is enabled, which is not the default setting. However, unless the feature is explicitly disabled, it is activated automatically when registering devices through the FortiCare user interface.
Arctic Wolf observed attacks exploiting the two security vulnerabilities starting on December 12. They note that the intrusions originated from several IP addresses linked to The Constant Company, BL Networks, and Kaopu Cloud HK.
Based on Arctic Wolf observations, the attackers targeted admin accounts with malicious single sign-on logins (SSO).
To prevent attacks, Fortinet recommends that admins still running a vulnerable version temporarily disable the FortiCloud login feature until an upgrade to a safer version is possible. (Bill Toulas / Bleeping Computer)
Related: Arctic Wolf, CSO Online, Security Affairs
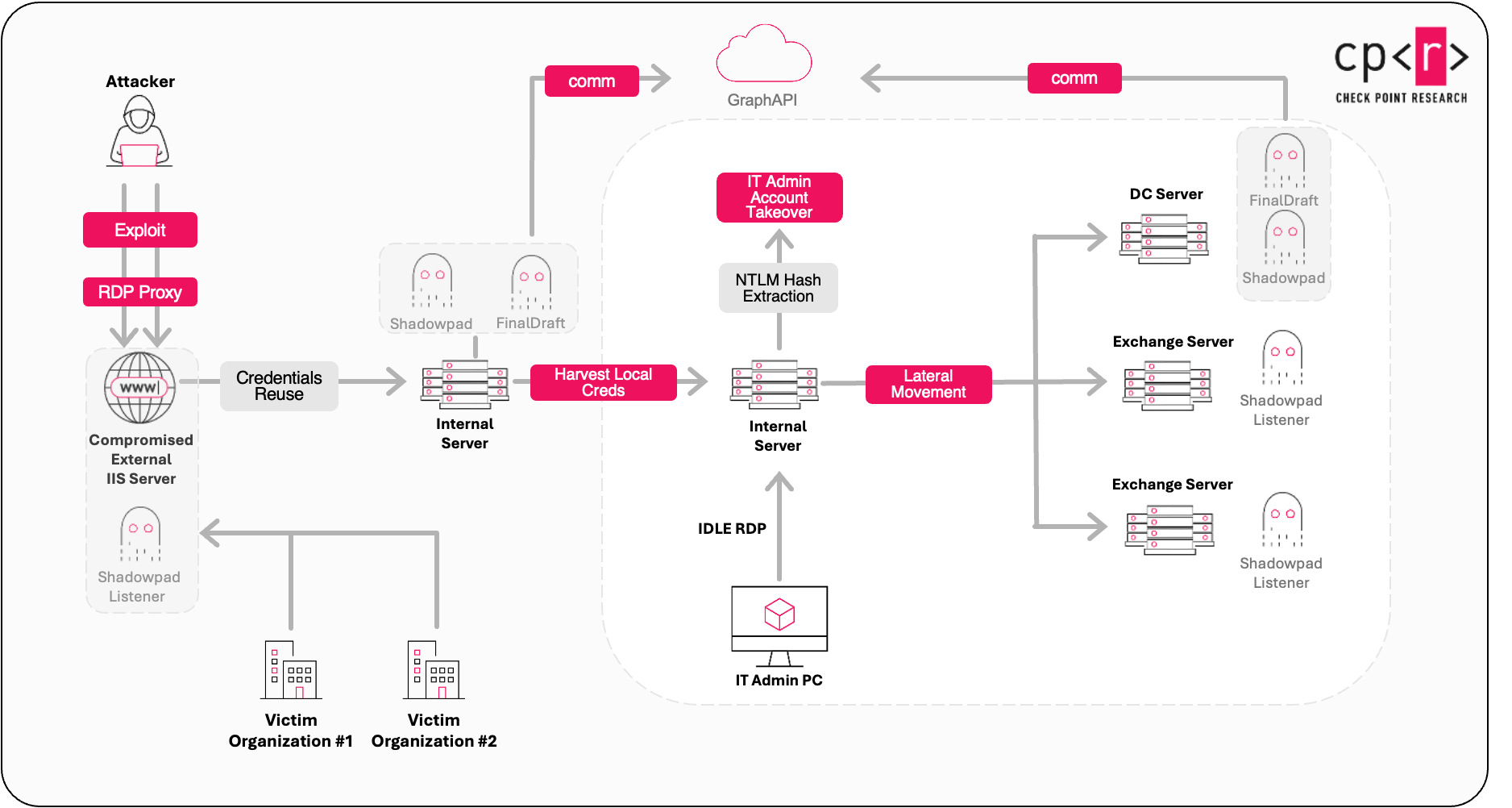
Researchers at Check Point report that the Chinese espionage crew Ink Dragon has expanded its snooping activities into European government networks, using compromised servers to create illicit relay nodes for future operations.
The campaign hit "several dozen victims," including government entities and telecommunications organizations across Europe, Asia, and Africa.
These attacks begin with Ink Dragon probing security weaknesses, such as misconfigured Microsoft IIS and SharePoint servers, to gain access to victims' environments. This tactic, as opposed to abusing zero-days or other high-profile vulnerabilities, helps attackers fly under the radar and reduces their chances of being caught.
Ink Dragon then scoops up credentials and uses existing accounts to infiltrate targets, tactics that help the gang blend in with normal network traffic. (Jessica Lyons / The Register)
Related: Check Point, Infosecurity Magazine
Researchers at Koi Security report that a new campaign dubbed 'Researchers at NCC Group report that global ransomware activity plateaued in November, even as attackers continued to refine their tactics and collaboration models.
The malicious code grants operators persistent high-privilege access to the browser, enabling them to hijack affiliate links, inject tracking code, and commit click and ad fraud.
The hidden script is acting as a loader that fetches the main payload from a remote server. To make the process more challenging to detect, the payload is intentionally retrieved only once in ten attempts.
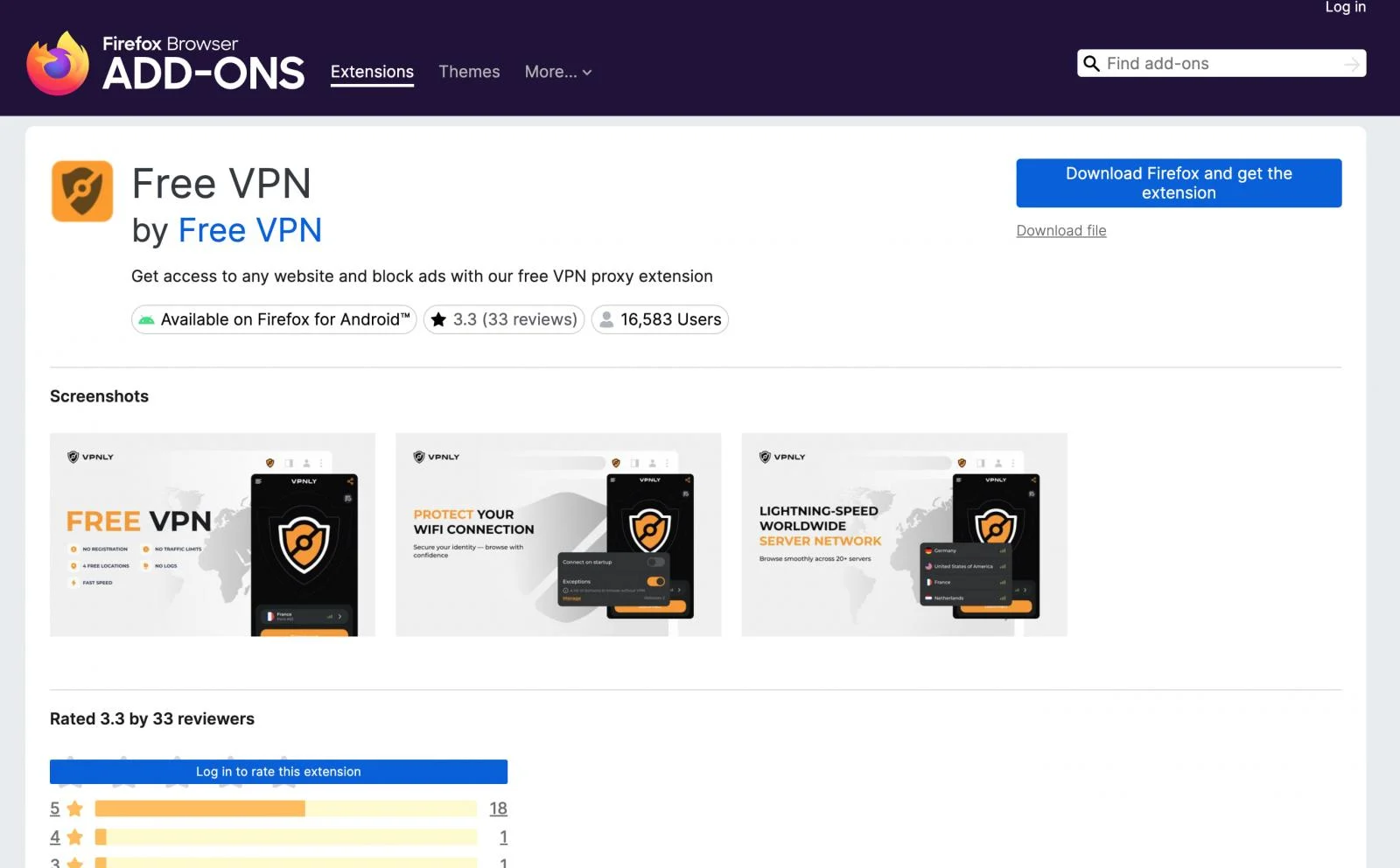
Koi Security researchers discovered the GhostPoster campaign and identified 17 compromised Firefox extensions that either read the PNG logo to extract and execute the malware loader or download the main payload from the attacker's server.
The FreeVPN Forever extension was the one Koi Security analyzed initially after its AI tool flagged it for parsing the raw bytes of its logo image file to locate a JavaScript snippet hidden using the steganography technique.
Many of the malicious extensions were still available on Firefox’s Add-Ons page at the time of writing. (Bill Toulas / Bleeping Computer)
Related: Koi
Researchers at NCC Group report that that global ransomware activity plateaued in November even as attackers continued to refine their tactics and collaboration models.
In its November 2025 Cyber Threat Intelligence Report, NCC says that ransomware incidents dipped slightly month-over-month but remained elevated, as the threat landscape stabilized in volume while becoming more complex in execution.
Some 583 ransomware attacks were tracked by NCC in November, down 2% from October. The most targeted industry was the industrials sector, which accounted for 25% of all attacks during the month, followed by the consumer discretionary and information technology sectors.
By location, not surprisingly, companies and organizations in North America were the most popular targets in November, accounting for 57% of all reported ransomware. In second place, Europe accounted for 20% of all ransomware attacks, and Asia ranked third at 12%.
Qilin ransomware retained its position as the most active ransomware group for the fourth consecutive month, responsible for 17% of recorded attacks, although its activity did decline from an unusually high peak in October.
The report also highlights the continued rise of the ClickFix attack technique, also known as ClearFake.
As detailed by Microsoft in August, the ClickFix social engineering technique attempts to trick users into running malicious commands on their devices by taking advantage of their target’s tendency to solve minor technical issues and other seemingly benign interactions, such as human verification and CAPTCHA checks.
The usage of the technique surged by 517% in the first half of 2025, which the report notes demonstrates a broader move toward social engineering tactics that bypass automated security controls by exploiting human behavior. (Duncan Riley / Silicon Angle)
Related: NCC Group
Washington, DC-based Opexus, which provides services and hosts data for more than 45 federal agencies, admits it made multiple mistakes in the hiring and termination of Muneeb and Sohaib Akhter.
Opexus fired them in February, minutes before they allegedly stole and destroyed government data in retaliation. The background checks were “consistent with prevailing government and industry standards with additional requirements for more sensitive work. That said, we fully acknowledge that additional diligence should have been applied,” a spokesperson for Opexus told CyberScoop.
Muneeb and Sohaib Akhter were arrested in Alexandria, Va., on Dec. 3 for allegedly committing a series of insider attack crimes during a weeklong window in February that ultimately compromised data from multiple federal agencies, including the Department of Homeland Security, Internal Revenue Service, and the Equal Employment Opportunity Commission.
Opexus said it decided to terminate the twins’ employment upon learning of their prior criminal history, but it did not explain how it became aware of their previous crimes nor what prompted a deeper look into their past. The brothers’ previous crimes were widely reported at the time, including details that are readily available via search engine queries on their respective names. (Matt Kapko / CyberScoop)
Related: SC Media
Texas Attorney General Ken Paxton filed lawsuits against five major television manufacturers, accusing them of illegally spying on consumers through smart TV technology.
The companies named include Samsung, Sony, LG, and two Chinese firms—Hisense and TCL Technology Group Corporation. The legal action highlights growing concerns about consumer privacy and foreign data collection, particularly from companies with ties to China. The suits allege these manufacturers secretly harvest viewing data from Texas homes without proper consent.
At the heart of the controversy is Automated Content Recognition (ACR). This software captures screenshots of television displays every 500 milliseconds, monitoring viewing habits in real time.
The companies then transmit this data back to their servers and sell it for targeted advertising. The technology potentially exposes passwords, banking information, and other sensitive personal data.
“Companies, especially those connected to the Chinese Communist Party, have no business illegally recording Americans’ devices inside their own homes,” Paxton said in a statement. He called the conduct “invasive, deceptive, and unlawful.”
The Chinese connections raise particular alarm bells for Texas officials. China’s National Security Law grants Beijing broad powers to access data from Chinese companies, potentially putting American consumer information at risk. (Dallas Express)
Related: Texas Attorney General, Hoodline, KTSA, Engadget, KYFO, Newsweek, The Texan, Texas Border Business
Sources say Blackstone is leading a $400 million investment in data-security firm Cyera that values the New York-based company at $9 billion.
Cyera is among a crop of cybersecurity startups leveraging artificial intelligence to protect companies from new security vulnerabilities introduced by AI. The startup, founded in 2021 by former Israeli Defence Forces military intelligence officers Yotam Segev and Tamar Bar-Ilan, raised funding at a $6 billion valuation in June. (Kate Clark / Wall Street Journal)
Related: Reuters, Calcalist, JNS, Globes
Adaptive Security, a NYC-based provider of AI-powered social engineering prevention solutions, raised $81M in a Series B venture funding round.
Bain Capital Ventures led the round with participation from NVentures (NVIDIA’s venture capital arm), OpenAI Startup Fund, Andreessen Horowitz (a16z), Abstract Ventures, Capital One Ventures, and Citi Ventures. (Chris Metinko / Axios)
Related: Adaptive Security, SiliconANGLE, FinSMEs, AlleyWatch
Best Thing of the Day: And So It Begins
Leaders from Anthropic and Google will testify today before two House Homeland Security Committee subcommittees about how AI and other emerging technologies are reshaping the cyber threat landscape.
Bonus Best Thing of the Day: Giving Cops Their Due
Stormont ministers have agreed to ring-fence £119m (around $159 million) to compensate police officers of the Police Service of Northern Ireland (PSNI) over a major data breach.
Worst Thing of the Day: Don't Force Your AI on Our Community
A Discord community for gay gamers is in disarray after one of its moderators and an executive at Anthropic forced the company’s AI chatbot on the Discord after Jason Clinton, Anthropic’s Deputy Chief Information Security Officer (CISO) and a moderator in the Discord, overrode users who wanted to restrict Anthropic's Claude on the channel.
Closing Thought





