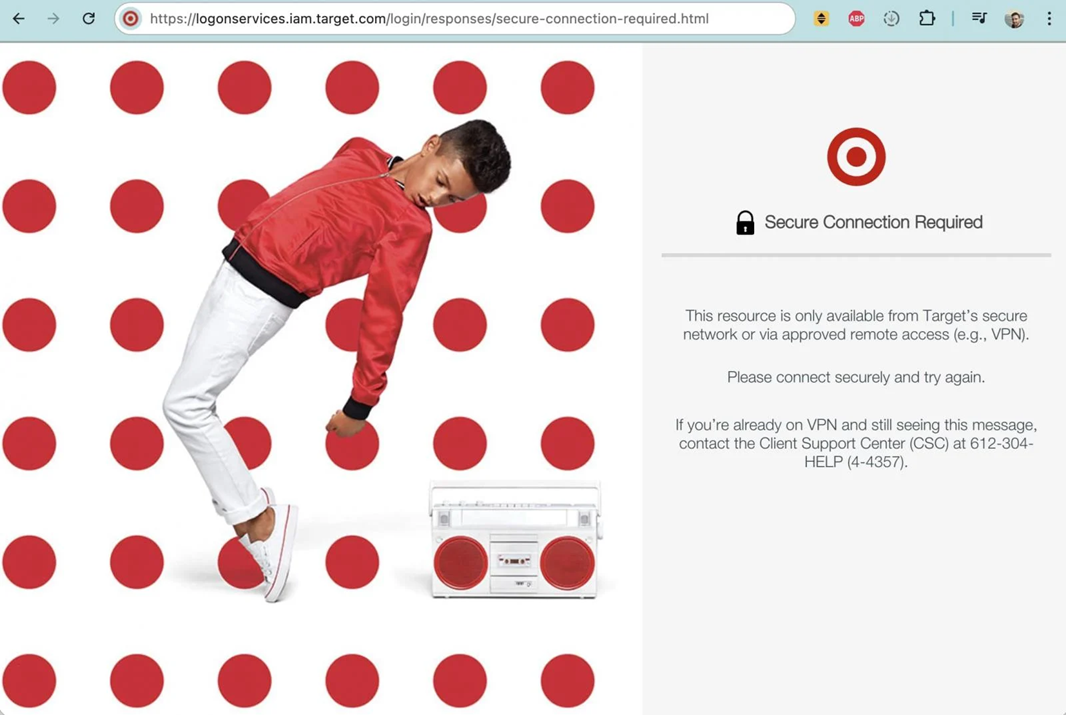
Hackers claim to be selling Target's internal source code
Poland thwarted power system cyberattack, Hackers accessed the systems of Spanish energy provider Endesa and Energía XXI, Personal finance platform Betterment was hacked through third-party, Dutch national sentenced to seven years for hacking, Korea's Kyowon Group hit with ransomware, much more